Cyberattacks Threaten U.S. Water Systems: Senate Hearing Reveals Critical Vulnerabilities and Foreign Targeti…
Published on: 2026-02-06
AI-powered OSINT brief from verified open sources. Automated NLP signal extraction with human verification. See our Methodology and Why WorldWideWatchers.
Intelligence Report: Clear and present danger Cyber siege on Americas water supply exposed
1. BLUF (Bottom Line Up Front)
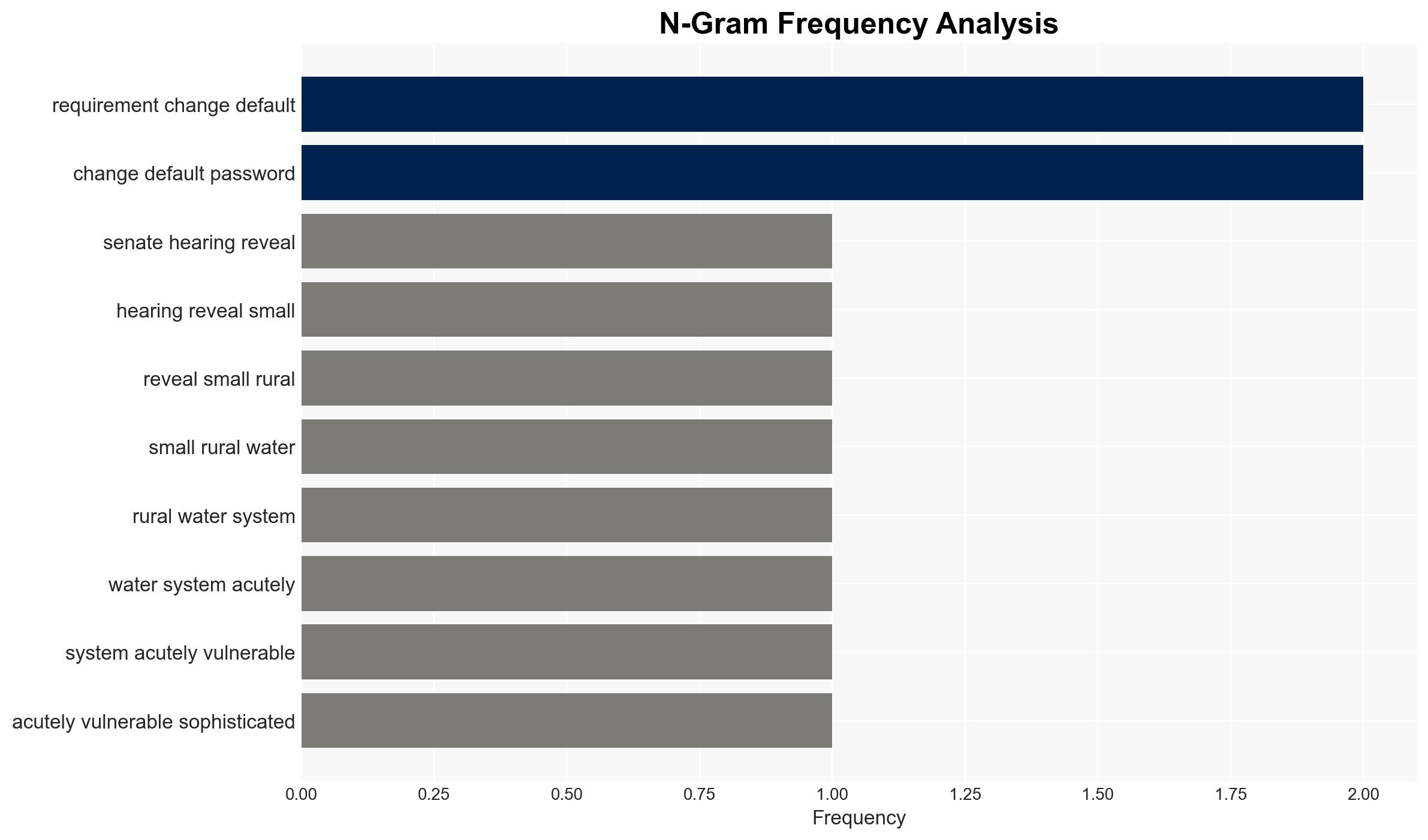
The U.S. water infrastructure, particularly small and rural systems, is critically vulnerable to cyberattacks from nation-state actors, posing a significant threat to public health and safety. The most likely hypothesis is that these vulnerabilities will continue to be exploited, potentially leading to disruptions in water supply and public trust. This assessment is made with moderate confidence, given the current evidence of ongoing cyber intrusions and resource constraints in these systems.
2. Competing Hypotheses
- Hypothesis A: Nation-state actors are actively targeting U.S. water infrastructure to cause disruption and erode public confidence. This is supported by evidence of past cyber intrusions attributed to Iran, Russia, and China, and the strategic importance of water systems. Key uncertainties include the full extent of current intrusions and the specific motivations behind each attack.
- Hypothesis B: The vulnerabilities in U.S. water infrastructure are primarily due to systemic underfunding and lack of cybersecurity resources, rather than targeted nation-state campaigns. While resource constraints are evident, this hypothesis is less supported by the direct attribution of attacks to foreign actors.
- Assessment: Hypothesis A is currently better supported due to the attribution of attacks to specific nation-state actors and their strategic objectives. Indicators that could shift this judgment include evidence of increased domestic cyber incidents unrelated to foreign actors.
3. Key Assumptions and Red Flags
- Assumptions: Nation-state actors have the capability and intent to target U.S. water infrastructure; small and rural water systems lack adequate cybersecurity defenses; cyber intrusions will continue to escalate without intervention.
- Information Gaps: Detailed intelligence on the specific methods and tools used by adversaries; comprehensive data on all water systems’ cybersecurity postures.
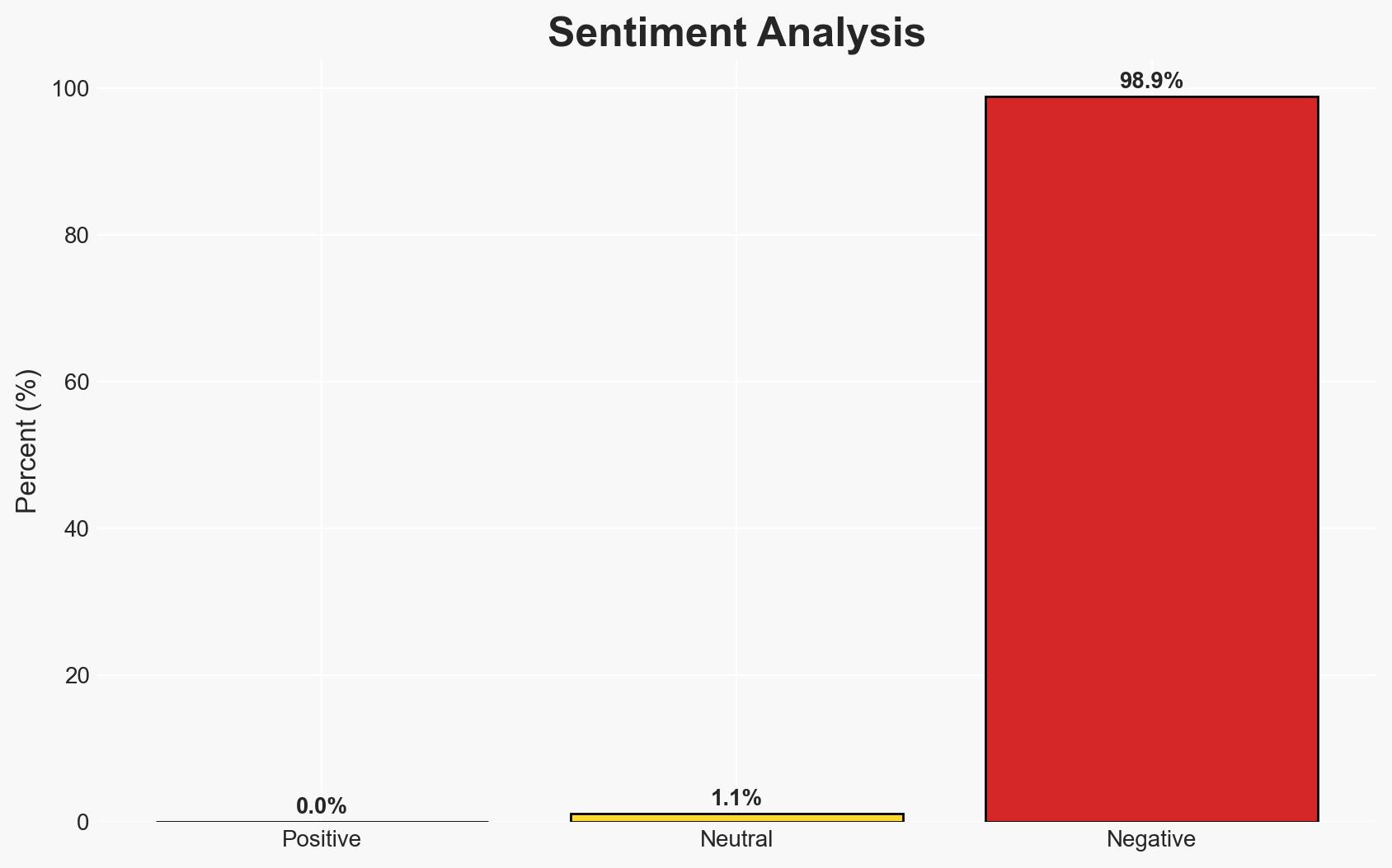
- Bias & Deception Risks: Potential confirmation bias in attributing all cyber incidents to foreign actors; risk of adversaries using false-flag operations to obscure true origins.
4. Implications and Strategic Risks
The ongoing cyber threats to U.S. water infrastructure could lead to significant disruptions in public services and erode trust in government capabilities. Over time, this could exacerbate geopolitical tensions and increase the likelihood of retaliatory actions.
- Political / Geopolitical: Potential escalation in cyber warfare tactics and diplomatic tensions with implicated nations.
- Security / Counter-Terrorism: Increased vulnerability to hybrid warfare tactics targeting critical infrastructure.
- Cyber / Information Space: Heightened need for cybersecurity enhancements and public awareness campaigns.
- Economic / Social: Possible economic impacts from water service disruptions; social unrest due to loss of trust in public utilities.
5. Recommendations and Outlook
- Immediate Actions (0–30 days): Conduct rapid cybersecurity audits of vulnerable water systems; enhance monitoring and incident response capabilities.
- Medium-Term Posture (1–12 months): Develop partnerships with private cybersecurity firms; increase federal funding for cybersecurity improvements in critical infrastructure.
- Scenario Outlook:
- Best: Successful mitigation of vulnerabilities and reduction in cyber incidents.
- Worst: Major disruption in water supply leading to public health crises.
- Most-Likely: Continued low-level cyber intrusions with periodic disruptions.
6. Key Individuals and Entities
- Matt Odermann, National Rural Water Association
- Not clearly identifiable from open sources in this snippet.
7. Thematic Tags
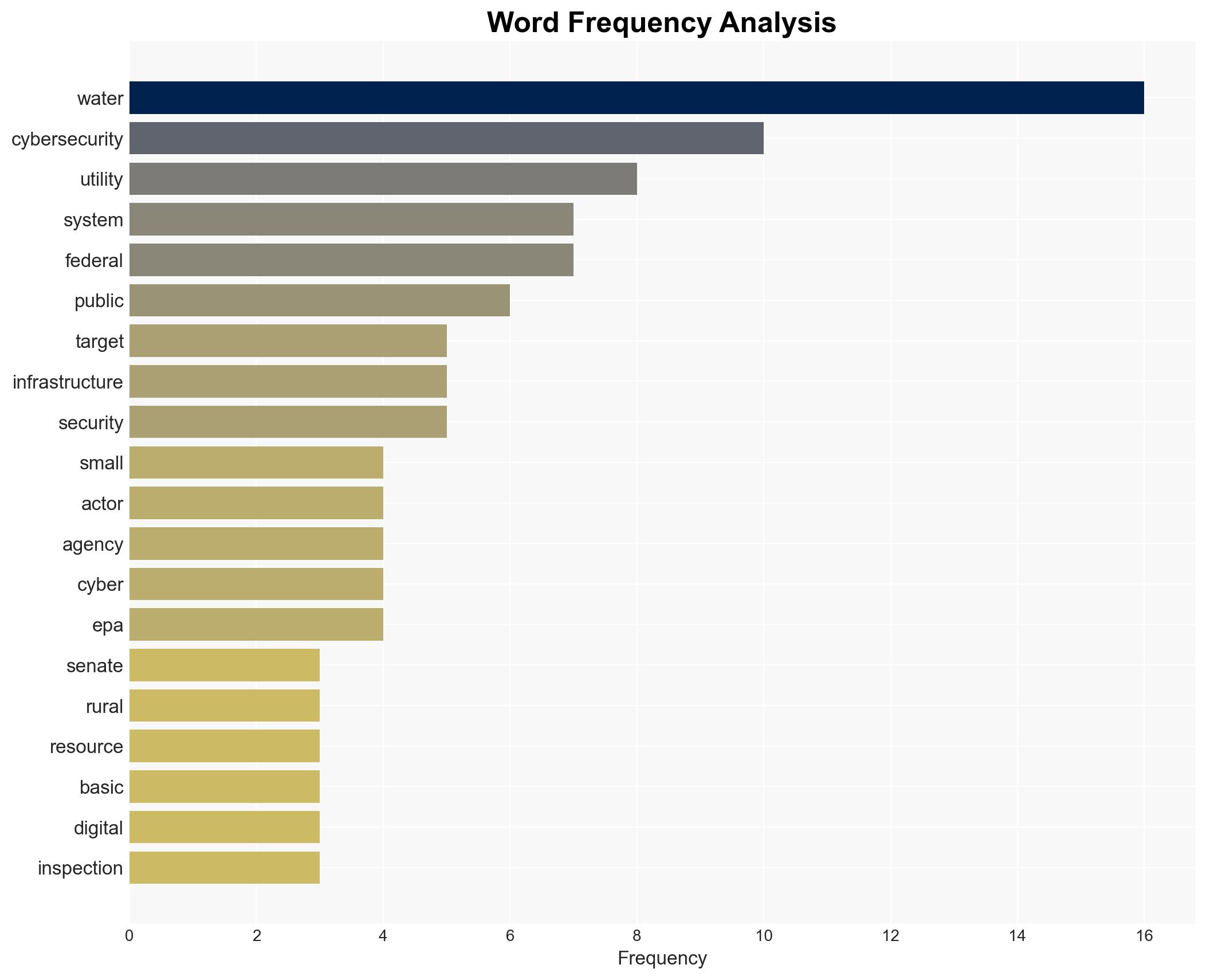
cybersecurity, critical infrastructure, nation-state actors, water systems, public safety, geopolitical tensions, asymmetric warfare
Structured Analytic Techniques Applied
- Adversarial Threat Simulation: Model hostile behavior to identify vulnerabilities.
- Indicators Development: Detect and monitor behavioral or technical anomalies across systems for early threat detection.
- Bayesian Scenario Modeling: Quantify uncertainty and predict cyberattack pathways using probabilistic inference.
- Network Influence Mapping: Map influence relationships to assess actor impact.
Explore more:
Cybersecurity Briefs ·
Daily Summary ·
Support us