Cybercriminal abuse of large language models – Talosintelligence.com
Published on: 2025-06-25
Intelligence Report: Cybercriminal Abuse of Large Language Models – Talosintelligence.com
1. BLUF (Bottom Line Up Front)
Cybercriminals are increasingly exploiting large language models (LLMs) to enhance their attack capabilities, posing significant threats to cybersecurity. This report identifies key vulnerabilities and recommends strategic measures to mitigate these risks. Structured analytic techniques (SATs) have been employed to ensure a comprehensive and unbiased analysis.
2. Detailed Analysis
The following structured analytic techniques have been applied to ensure methodological consistency:
Adversarial Threat Simulation
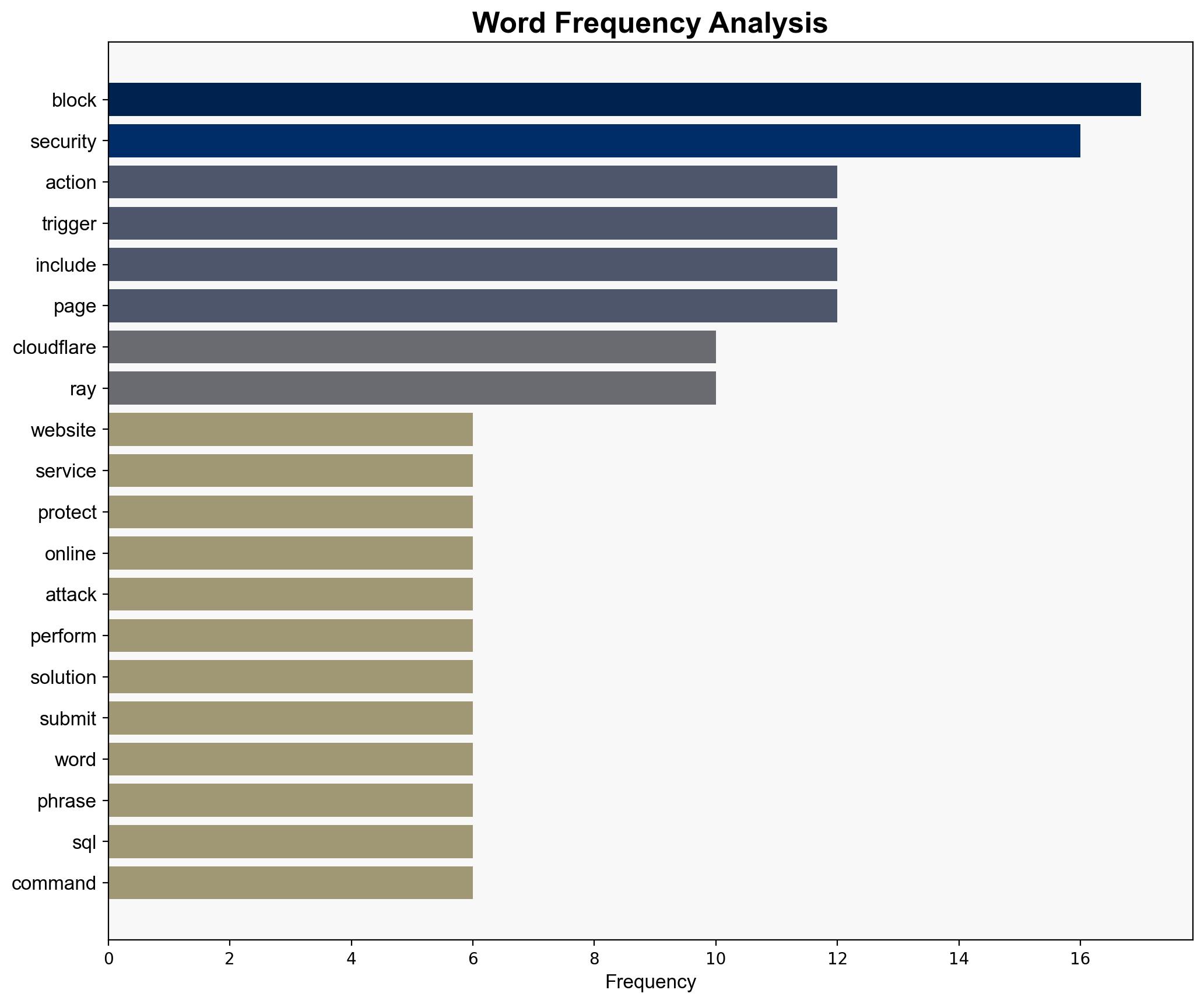
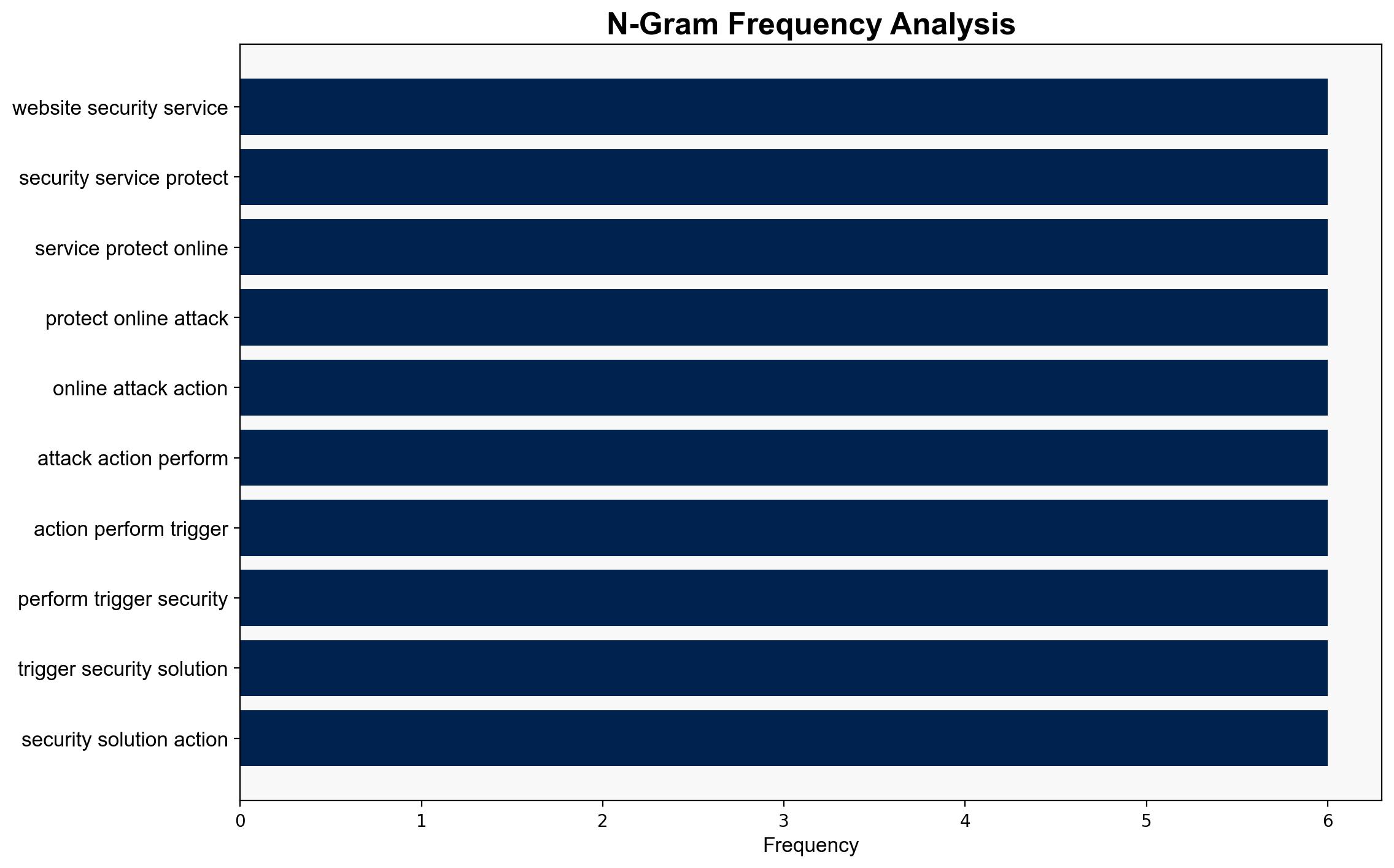
Simulations indicate that cyber adversaries are leveraging LLMs to automate phishing attacks, generate malicious code, and bypass security protocols. These models can mimic human-like interactions, making detection challenging.
Indicators Development
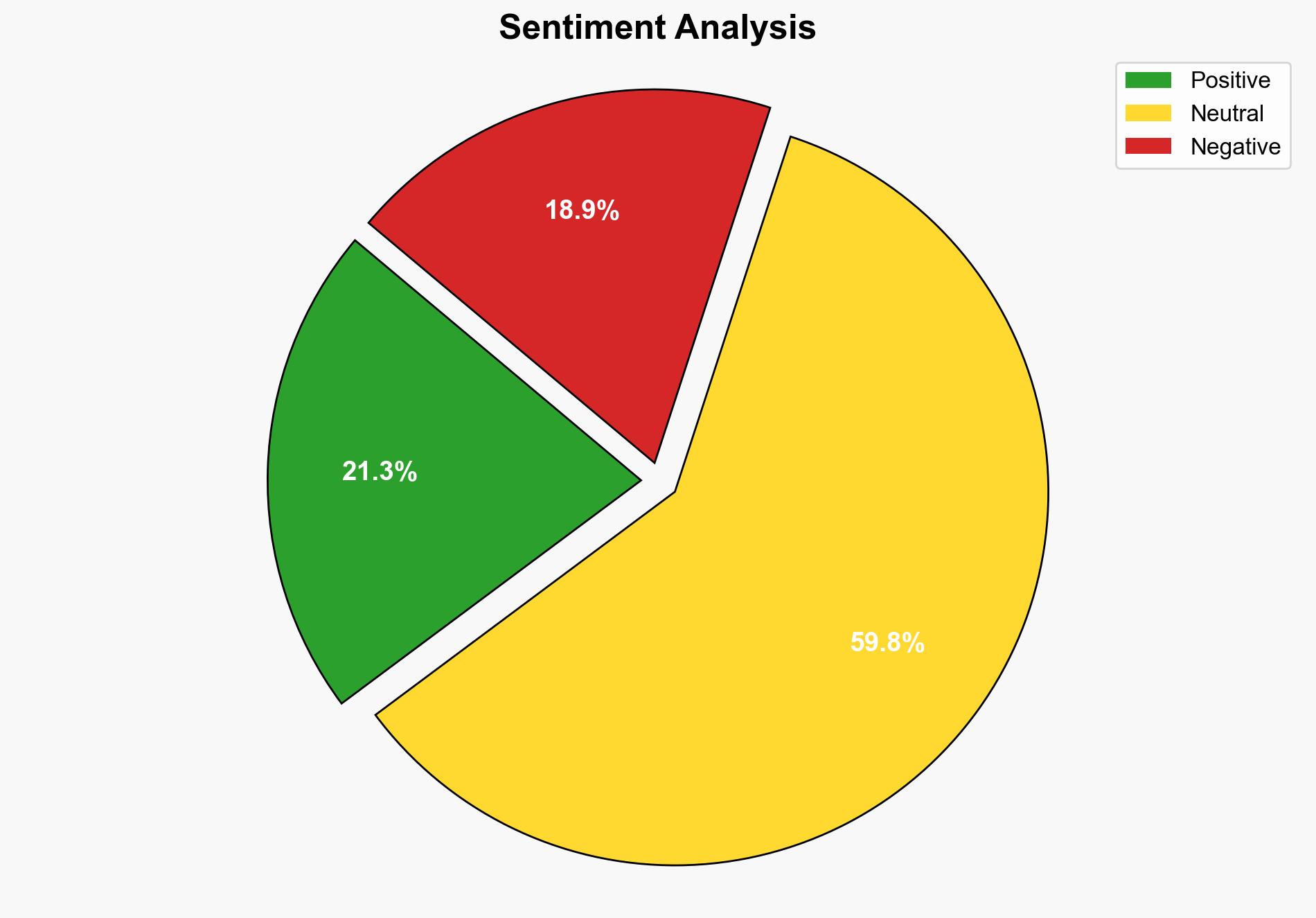
Key indicators of LLM abuse include unusual patterns in network traffic, increased phishing attempts with sophisticated language, and anomalies in user behavior analytics. Continuous monitoring is essential for early detection.
Bayesian Scenario Modeling
Probabilistic models predict a high likelihood of increased LLM-driven attacks in the next 6-12 months. Scenarios suggest that without intervention, these attacks could evolve into more complex and targeted operations.
3. Implications and Strategic Risks
The misuse of LLMs by cybercriminals could lead to widespread data breaches, financial losses, and erosion of public trust in digital systems. The potential for cross-domain impacts, such as economic disruptions and compromised national security, is significant.
4. Recommendations and Outlook
- Enhance cybersecurity frameworks to include AI-specific threat detection and response capabilities.
- Invest in research to develop countermeasures against LLM-driven attacks.
- Best Case: Successful implementation of AI defenses reduces attack frequency and impact.
- Worst Case: Failure to adapt leads to increased cyber incidents and systemic vulnerabilities.
- Most Likely: Gradual improvement in defenses with ongoing challenges from evolving threats.
5. Key Individuals and Entities
No specific individuals are identified in this report. The focus remains on the broader threat landscape and systemic vulnerabilities.
6. Thematic Tags
national security threats, cybersecurity, artificial intelligence, cybercrime, technological vulnerabilities