Cybercriminals Exploit Cheap VPS to Launch SaaS Hijacking Attacks – HackRead
Published on: 2025-08-25
Intelligence Report: Cybercriminals Exploit Cheap VPS to Launch SaaS Hijacking Attacks – HackRead
1. BLUF (Bottom Line Up Front)
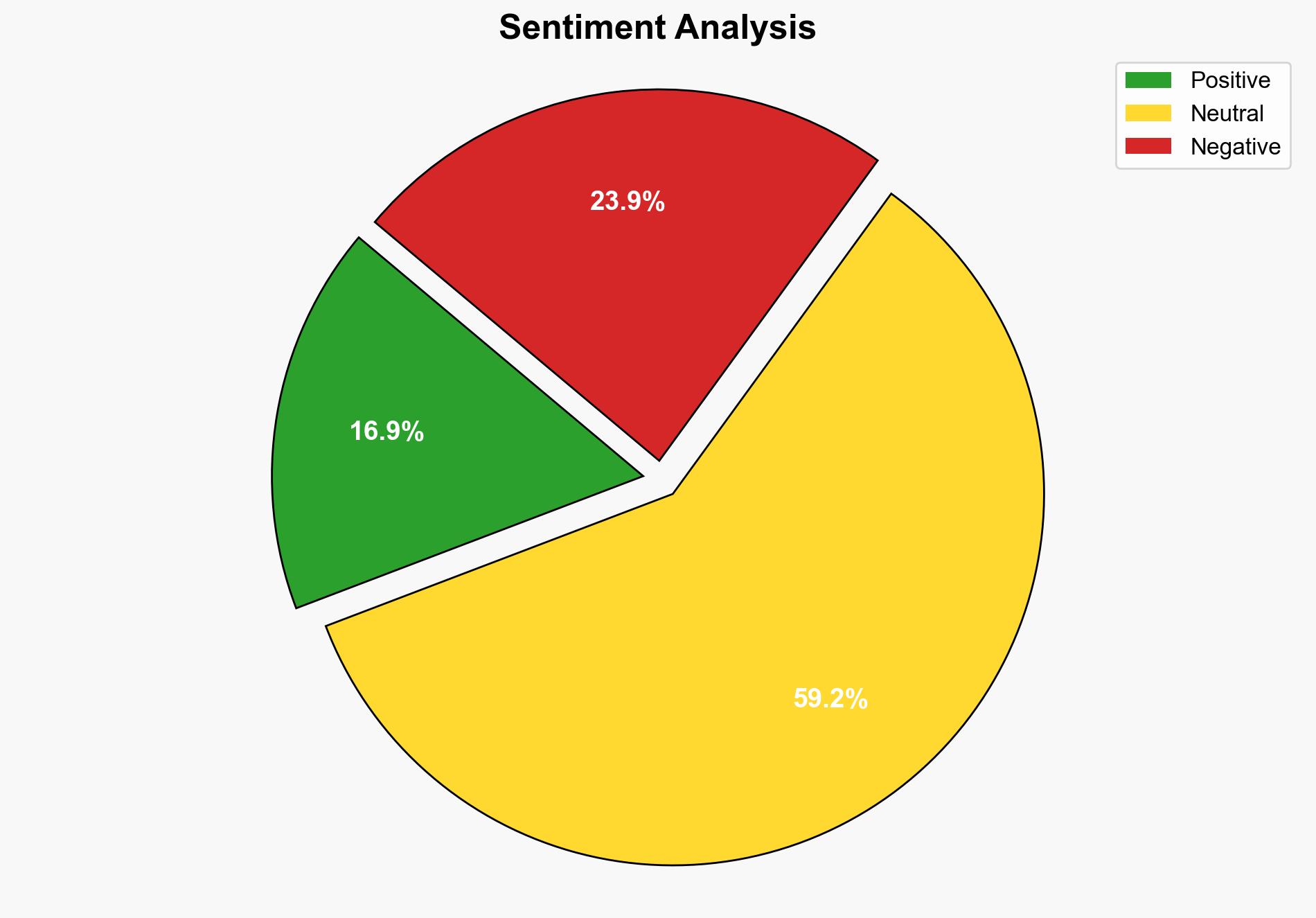
The most supported hypothesis is that cybercriminals are leveraging cheap virtual private servers (VPS) to conduct sophisticated SaaS hijacking attacks, exploiting these platforms to bypass traditional security measures. This is supported by evidence of increased malicious activity and the use of stealth tactics to maintain access. Confidence in this hypothesis is moderate due to the reliance on specific provider data and the potential for alternative explanations. Recommended action includes enhancing detection systems to identify unusual login patterns and strengthening multi-factor authentication (MFA) protocols.
2. Competing Hypotheses
1. **Hypothesis A**: Cybercriminals are primarily using cheap VPS services to conduct SaaS hijacking attacks, exploiting these platforms to bypass security measures effectively.
2. **Hypothesis B**: The observed increase in SaaS hijacking attacks is due to a broader trend of cybercriminals adopting more sophisticated tactics, with cheap VPS usage being just one of several methods employed.
Using ACH 2.0, Hypothesis A is better supported by the specific evidence of increased activity linked to VPS providers like Hyonix and the detailed tactics described, such as creating subtle email rules. Hypothesis B lacks direct evidence linking it to the observed incidents.
3. Key Assumptions and Red Flags
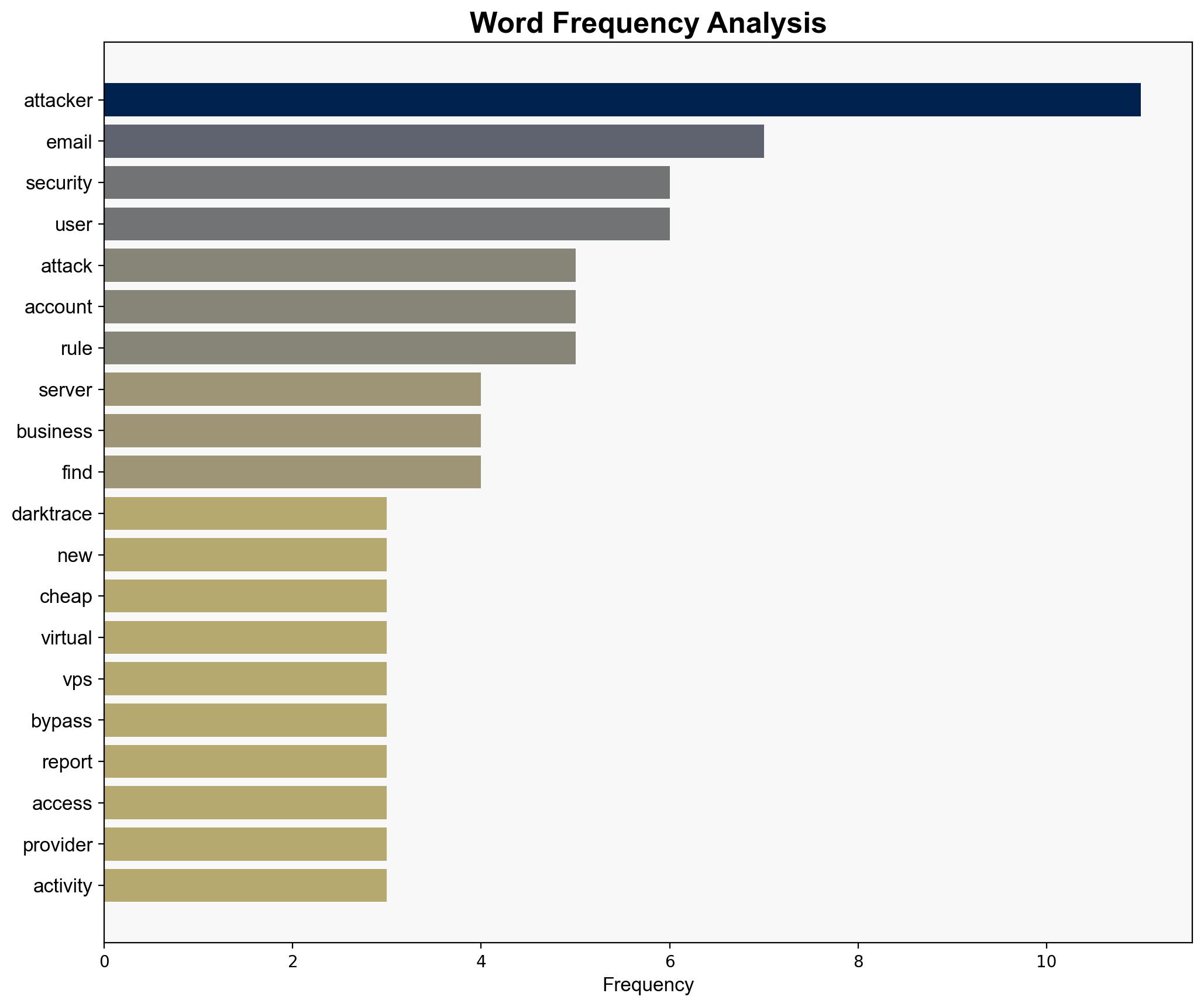
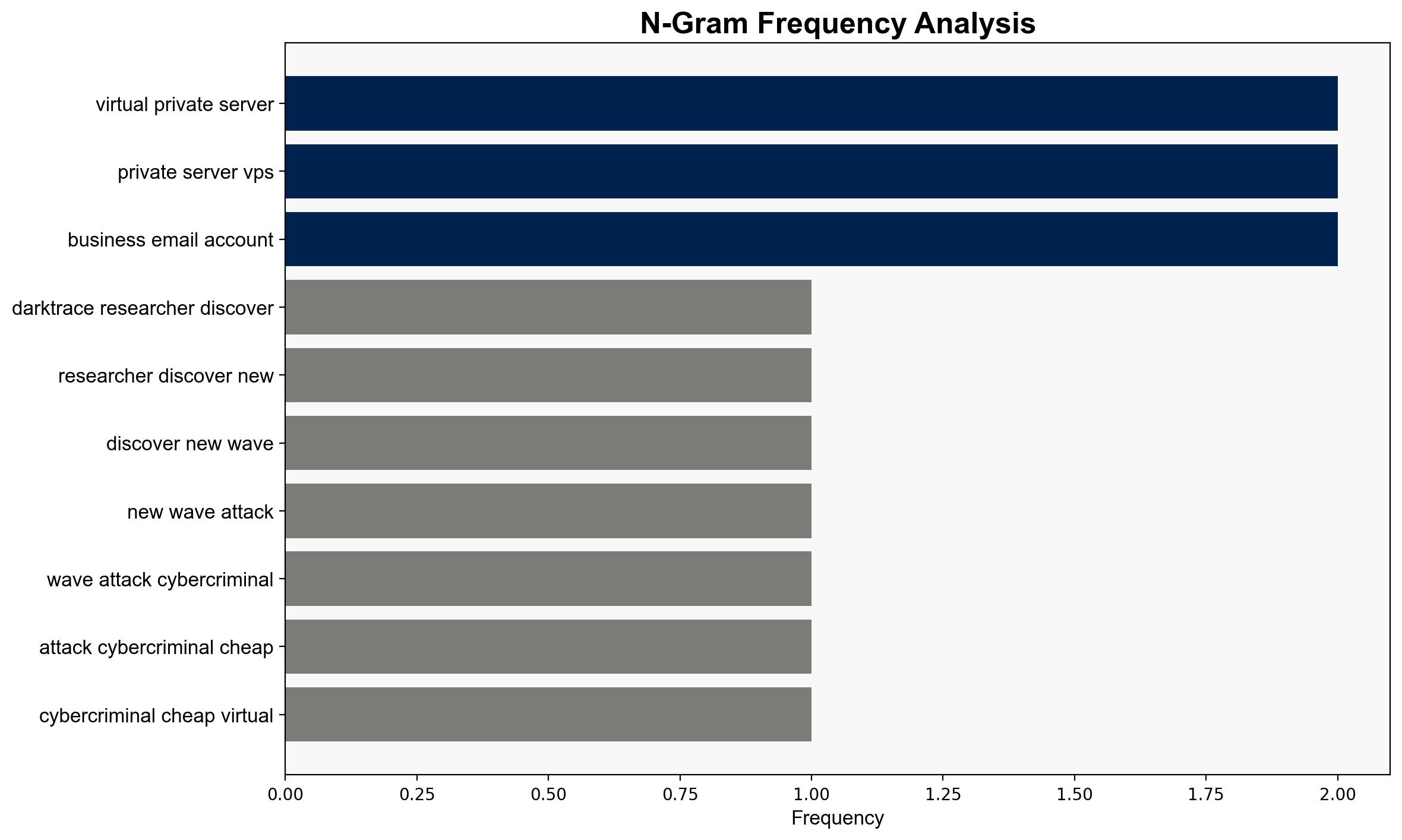
– **Assumptions**: It is assumed that the data from Darktrace accurately represents a broader trend and that the tactics described are unique to the use of cheap VPS services.
– **Red Flags**: The reliance on data from specific providers like Hyonix may not represent the entire landscape. There is also a potential bias in attributing the attacks solely to VPS usage without considering other factors.
– **Blind Spots**: The report does not address potential countermeasures already in place or the role of other service providers in facilitating these attacks.
4. Implications and Strategic Risks
The exploitation of cheap VPS services for SaaS hijacking poses significant risks to business email systems, potentially leading to data breaches and financial losses. This trend could escalate if not addressed, with cybercriminals refining their methods and targeting more organizations. The economic impact could be substantial, affecting trust in cloud services and increasing cybersecurity costs.
5. Recommendations and Outlook
- Enhance detection systems to monitor for unusual login patterns and implement stronger MFA protocols.
- Conduct regular security audits to identify vulnerabilities in email systems.
- Scenario Projections:
- Best Case: Organizations quickly adapt to new threats, reducing the success rate of such attacks.
- Worst Case: Cybercriminals continue to exploit these vulnerabilities, leading to widespread data breaches.
- Most Likely: A gradual increase in attacks with organizations slowly improving defenses.
6. Key Individuals and Entities
– Jason Soroko
– Hyonix
– Mevspace
– Hivelocity
7. Thematic Tags
national security threats, cybersecurity, counter-terrorism, regional focus