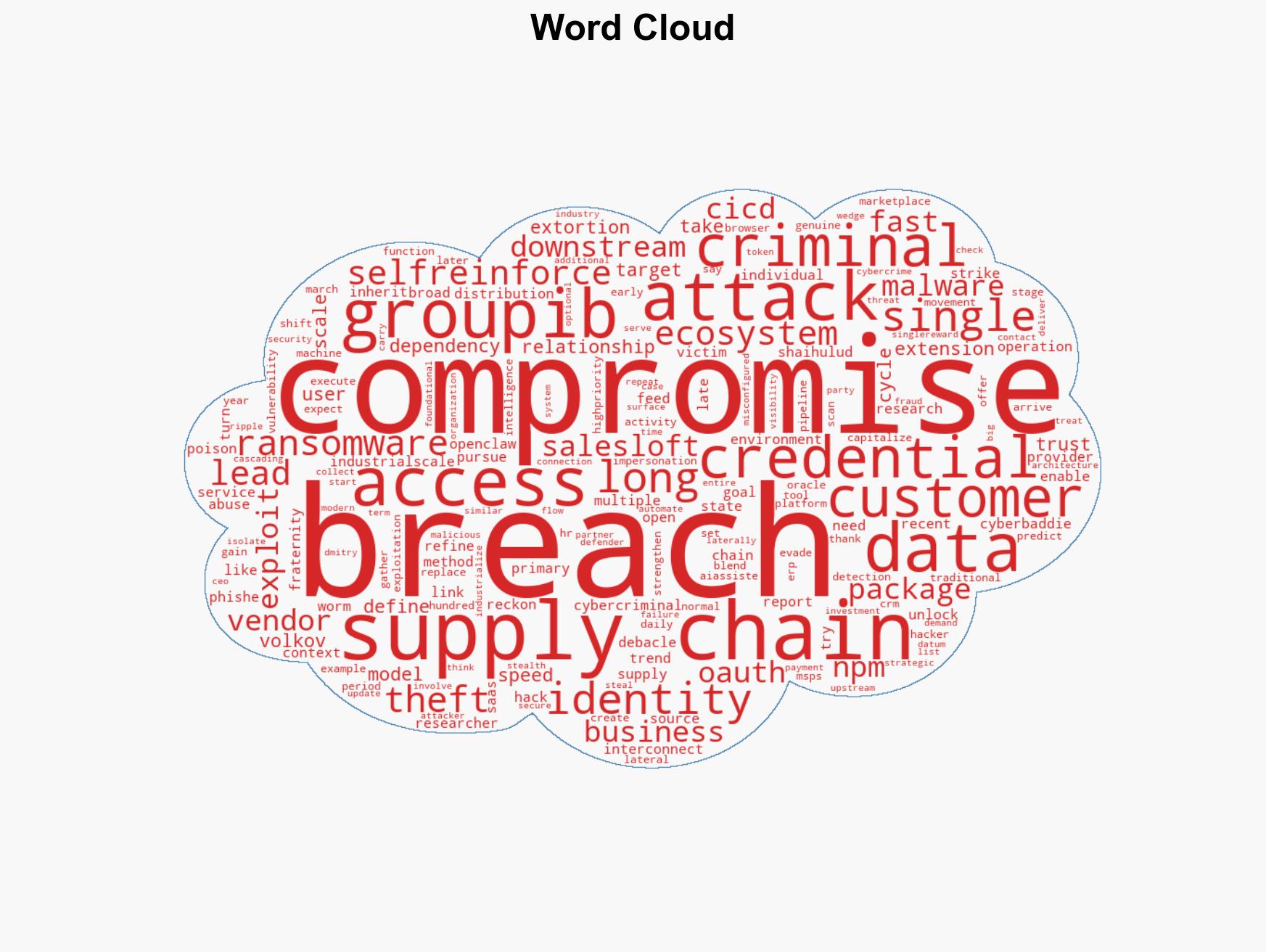
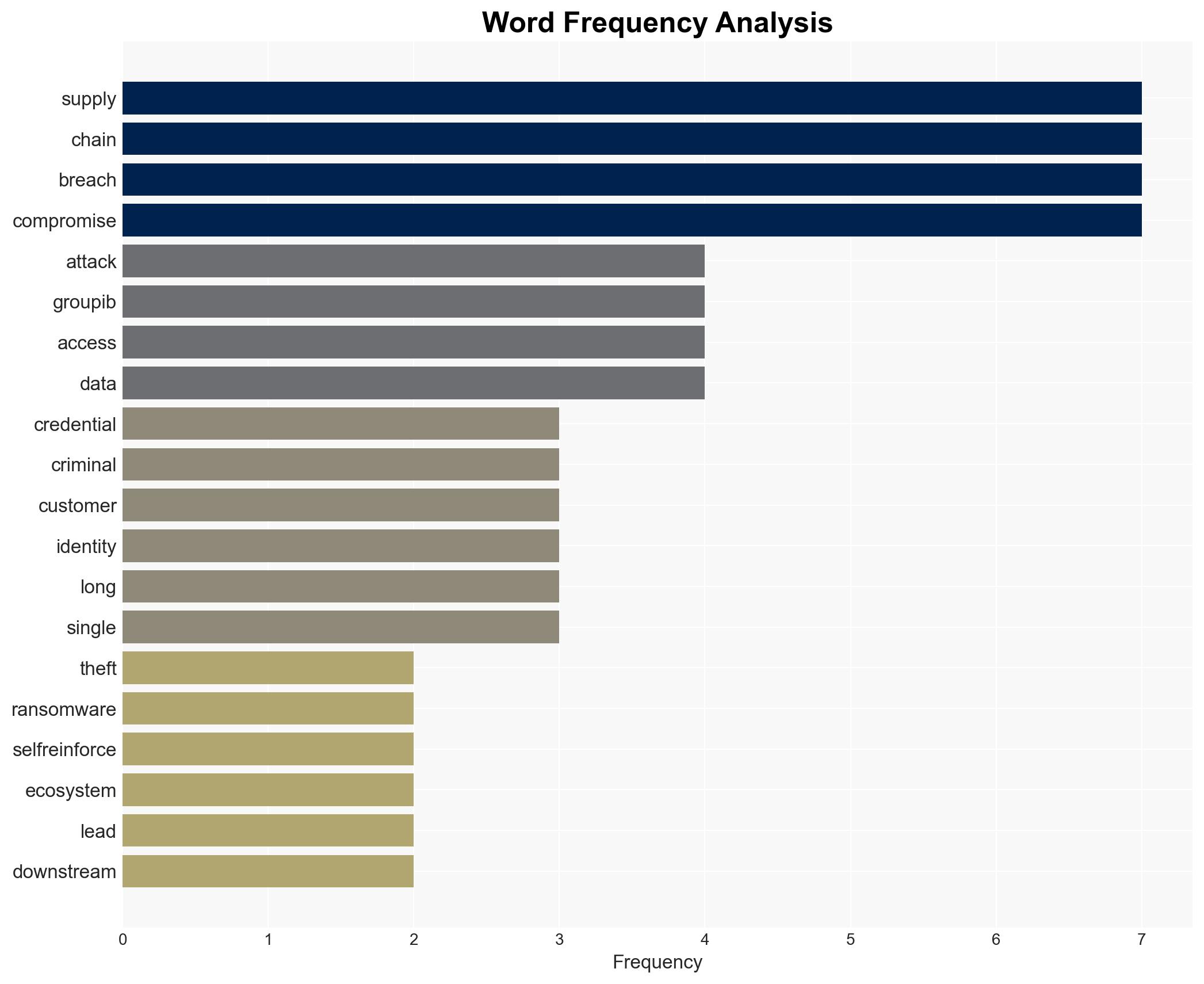
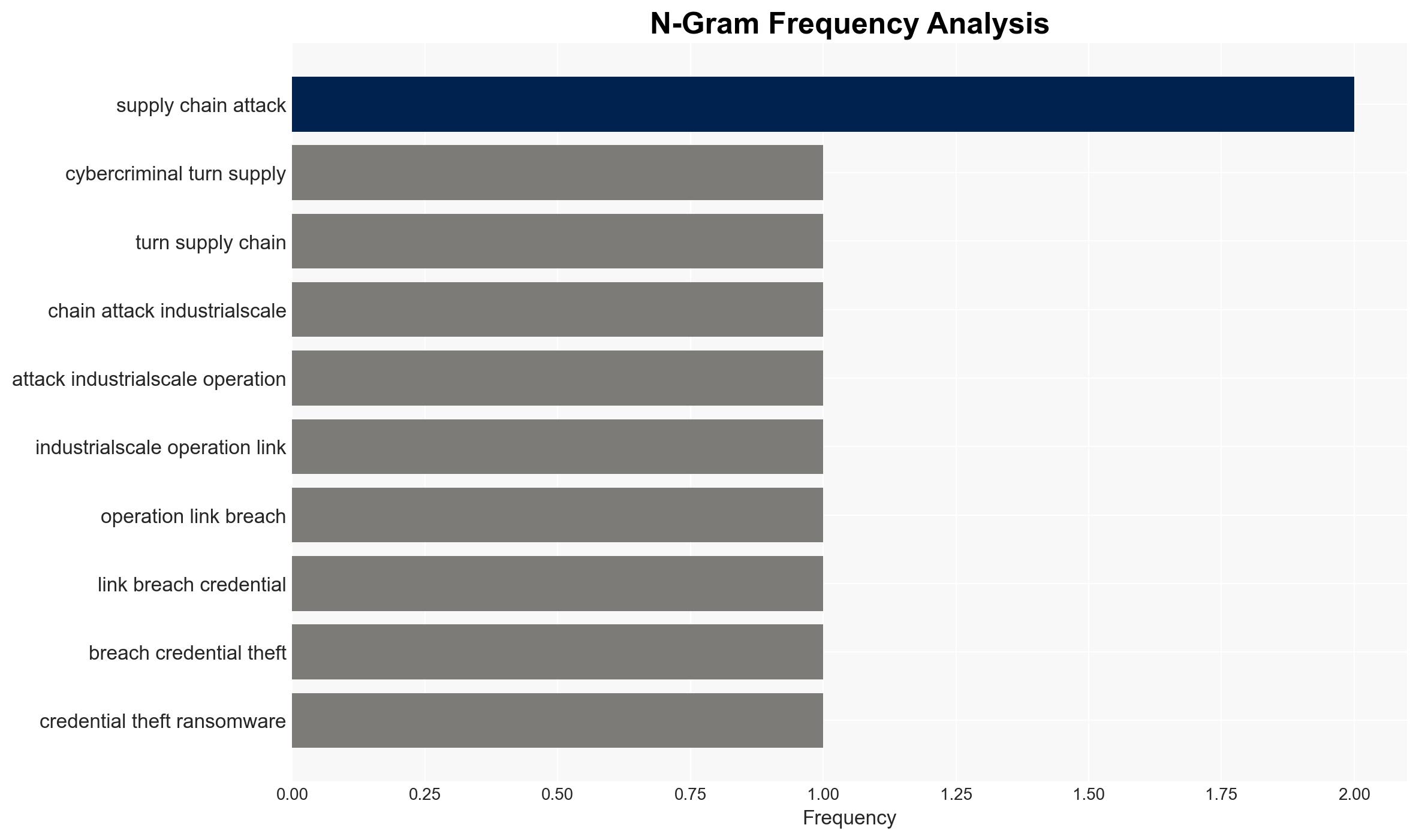
Cybercriminals exploit supply chain vulnerabilities to create a self-sustaining cybercrime ecosystem
Published on: 2026-02-12
AI-powered OSINT brief from verified open sources. Automated NLP signal extraction with human verification. See our Methodology and Why WorldWideWatchers.
Intelligence Report: Supply chain attacks now fuel a ‘self-reinforcing’ cybercrime economy
1. BLUF (Bottom Line Up Front)
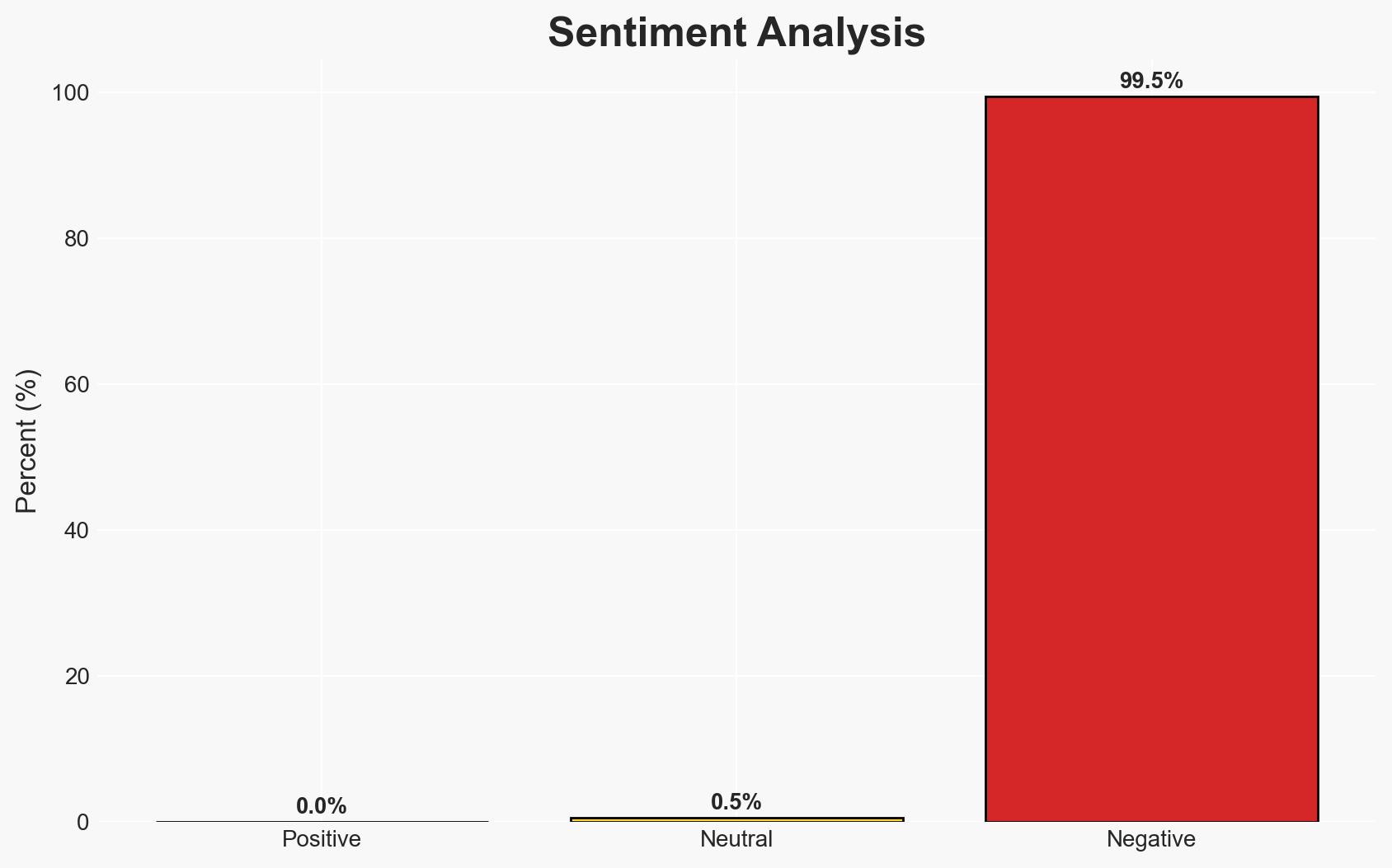
Cybercriminals are increasingly leveraging supply chain attacks to create a self-reinforcing cybercrime ecosystem, affecting a wide range of industries. This strategy involves interconnected breaches that exploit inherited access to victims’ customers, leading to cascading failures of trust. The most likely hypothesis is that these attacks will continue to grow in scale and sophistication, driven by AI-assisted tools. Overall confidence in this judgment is moderate.
2. Competing Hypotheses
- Hypothesis A: Cybercriminals are industrializing supply chain attacks to maximize impact and efficiency, using AI tools to enhance speed and stealth. This is supported by evidence of interconnected breaches and the prediction of increased AI use. Key uncertainties include the extent of AI tool deployment and potential countermeasures.
- Hypothesis B: The observed increase in supply chain attacks is a temporary trend driven by current vulnerabilities and may decline as organizations improve their defenses. This is contradicted by the ongoing development of sophisticated attack methods and the inherent complexity of securing supply chains.
- Assessment: Hypothesis A is currently better supported due to the systematic nature of the attacks and the strategic use of AI tools. Indicators that could shift this judgment include significant advancements in defensive technologies or a decrease in attack frequency.
3. Key Assumptions and Red Flags
- Assumptions: Cybercriminals will continue to prioritize supply chain attacks; AI tools will enhance the effectiveness of these attacks; organizations’ defenses will not rapidly evolve to counter these threats.
- Information Gaps: Detailed data on the specific AI tools used by cybercriminals; comprehensive statistics on the frequency and impact of supply chain attacks.
- Bias & Deception Risks: Potential bias in reporting from cybersecurity firms with vested interests; possible deception by cybercriminals to mislead attribution efforts.
4. Implications and Strategic Risks
The evolution of supply chain attacks into a self-reinforcing ecosystem poses significant risks across multiple domains. If unchecked, these attacks could destabilize trust in digital infrastructures and lead to widespread economic and operational disruptions.
- Political / Geopolitical: Potential for increased tensions between nations over cyber attribution and response strategies.
- Security / Counter-Terrorism: Heightened threat environment as cybercriminals exploit vulnerabilities in critical infrastructure supply chains.
- Cyber / Information Space: Increased complexity in defending against multi-stage attacks that blend into normal business operations.
- Economic / Social: Potential for significant economic losses and erosion of trust in digital commerce and services.
5. Recommendations and Outlook
- Immediate Actions (0–30 days): Enhance monitoring of supply chain partners; conduct vulnerability assessments; increase awareness and training on supply chain security.
- Medium-Term Posture (1–12 months): Develop partnerships for information sharing; invest in AI-driven defensive technologies; strengthen regulatory frameworks for supply chain security.
- Scenario Outlook:
- Best: Significant reduction in attacks due to improved defenses and international cooperation.
- Worst: Escalation of attacks leading to widespread economic and operational disruptions.
- Most-Likely: Continued increase in attack sophistication and frequency, with gradual improvements in defenses.
6. Key Individuals and Entities
- Group-IB (Cybersecurity firm)
- Dmitry Volkov (Group-IB CEO)
- Salesloft (Impacted entity)
- Oracle (Impacted entity)
- Not clearly identifiable from open sources in this snippet.
7. Thematic Tags
cybersecurity, supply chain attacks, cybercrime, AI tools, digital trust, ransomware, data breaches
Structured Analytic Techniques Applied
- Adversarial Threat Simulation: Model and simulate actions of cyber adversaries to anticipate vulnerabilities and improve resilience.
- Indicators Development: Detect and monitor behavioral or technical anomalies across systems for early threat detection.
- Bayesian Scenario Modeling: Quantify uncertainty and predict cyberattack pathways using probabilistic inference.
Explore more:
Cybersecurity Briefs ·
Daily Summary ·
Support us