Cybercriminals launch fraudulent website to market RAT disguised as legitimate RMM software
Published on: 2026-02-20
AI-powered OSINT brief from verified open sources. Automated NLP signal extraction with human verification. See our Methodology and Why WorldWideWatchers.
Intelligence Report: Criminals create business website to sell RAT disguised as RMM tool
1. BLUF (Bottom Line Up Front)
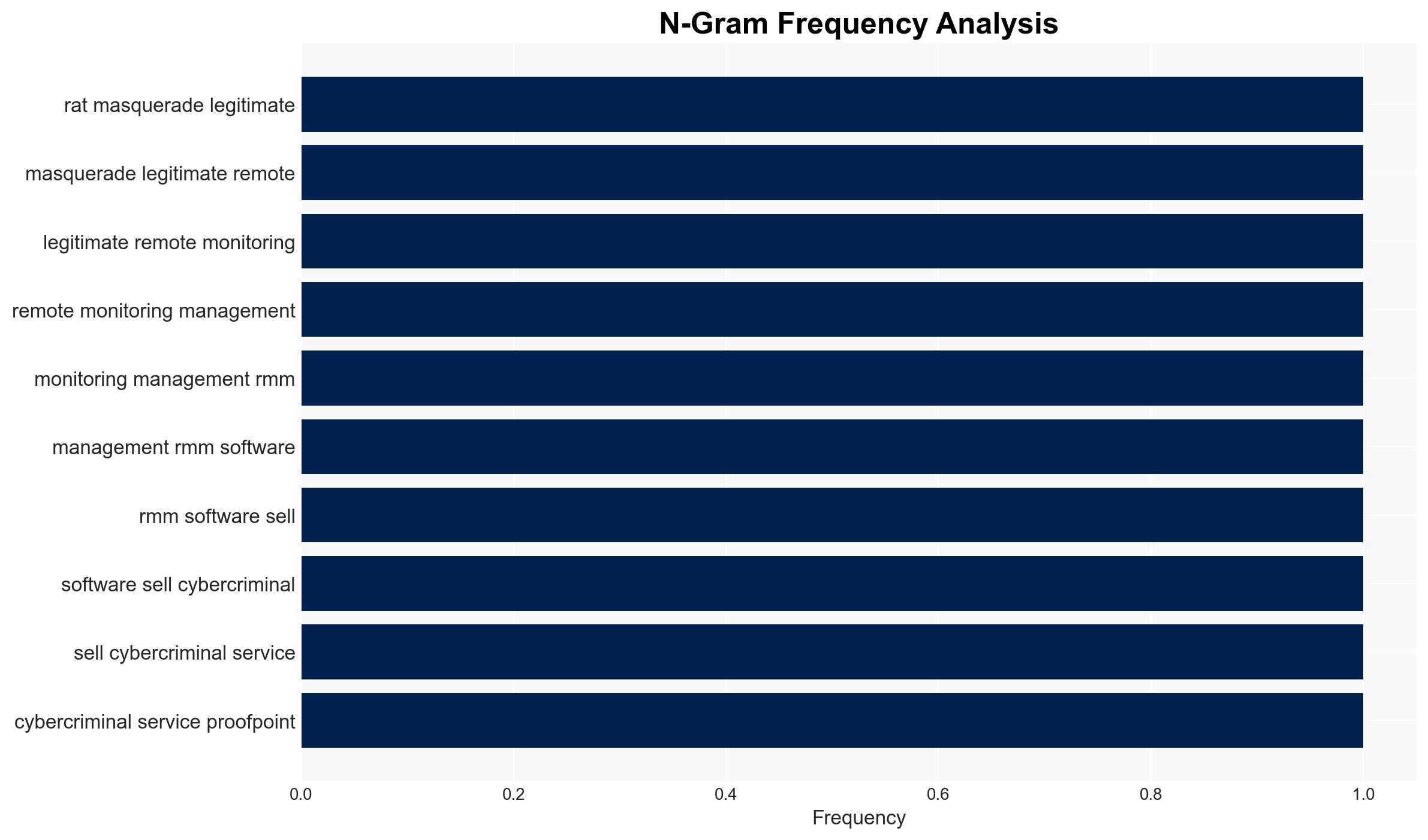
The discovery of a Remote Access Trojan (RAT) marketed as a legitimate Remote Monitoring and Management (RMM) tool, TrustConnect, represents a sophisticated cyber threat leveraging deceptive business practices. The operation exploits legitimate digital certificates to evade detection, posing significant risks to cybersecurity. This development primarily affects organizations using RMM tools and highlights vulnerabilities in certificate validation processes. Overall, there is moderate confidence in the assessment due to the complexity and scale of the operation.
2. Competing Hypotheses
- Hypothesis A: The TrustConnect operation is primarily a financially motivated cybercrime scheme targeting businesses through deceptive marketing and credential abuse. Supporting evidence includes the use of a legitimate-looking business website and EV certificates to enhance credibility. However, uncertainties remain regarding the full extent of the operation’s reach and its potential connections to broader cybercrime networks.
- Hypothesis B: TrustConnect could be part of a larger state-sponsored cyber-espionage campaign disguised as a criminal enterprise to gather intelligence from targeted organizations. While the sophistication of the operation supports this hypothesis, there is a lack of direct evidence linking it to state actors. The primary focus on financial transactions and cryptocurrency payments suggests a criminal rather than state-sponsored motive.
- Assessment: Hypothesis A is currently better supported due to the financial structure of the operation and the use of common cybercrime tactics. Indicators such as the pricing model and cryptocurrency payments align more closely with financially motivated cybercrime. Future intelligence on the operation’s targets and any geopolitical connections could shift this assessment.
3. Key Assumptions and Red Flags
- Assumptions: The operation is primarily financially motivated; the use of EV certificates is intended to bypass security measures; the primary targets are businesses using RMM tools.
- Information Gaps: The identities of the individuals behind TrustConnect; the full scope of affected organizations; potential links to larger cybercrime or espionage networks.
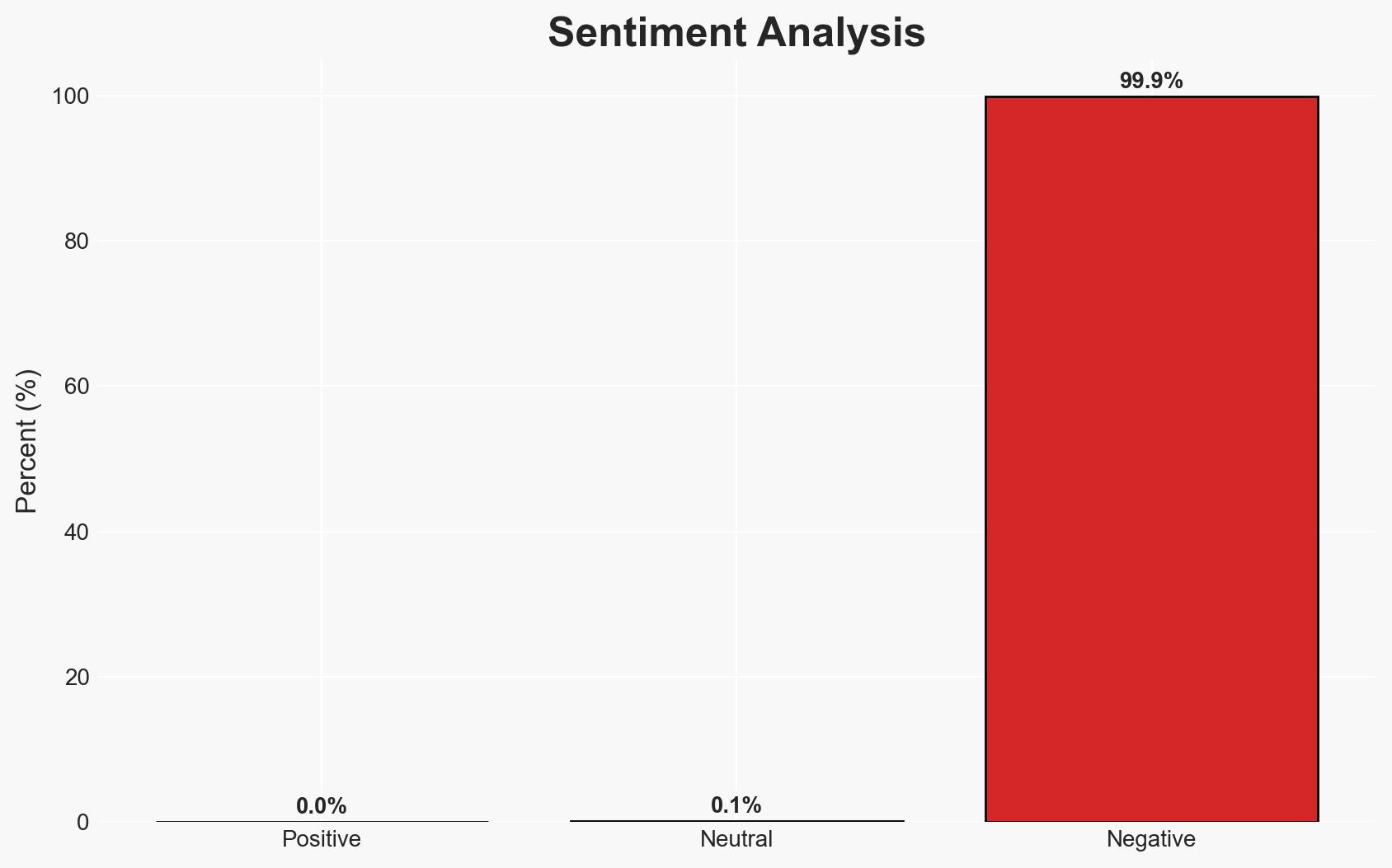
- Bias & Deception Risks: Potential cognitive bias towards viewing the operation as purely criminal; source bias from relying on a single research entity; possible deception by threat actors to mask true intentions.
4. Implications and Strategic Risks
The TrustConnect operation could lead to increased scrutiny of digital certificate issuance processes and highlight vulnerabilities in cybersecurity defenses. Over time, similar tactics may be adopted by other threat actors, increasing the overall threat landscape.
- Political / Geopolitical: Potential for increased international cooperation on cybercrime prevention and digital certificate regulation.
- Security / Counter-Terrorism: Heightened threat environment for organizations relying on RMM tools, necessitating improved security protocols.
- Cyber / Information Space: Increased risk of similar operations exploiting digital certificates; potential for widespread data breaches.
- Economic / Social: Potential financial losses for affected businesses; erosion of trust in digital certificates and RMM tools.
5. Recommendations and Outlook
- Immediate Actions (0–30 days): Monitor for indicators of TrustConnect activity; collaborate with certificate authorities to identify and revoke fraudulent certificates; increase awareness among potential targets.
- Medium-Term Posture (1–12 months): Develop partnerships with cybersecurity firms for threat intelligence sharing; enhance digital certificate validation processes; invest in cybersecurity training for organizations.
- Scenario Outlook:
- Best: Successful disruption of TrustConnect leads to improved cybersecurity measures and reduced threat levels.
- Worst: Proliferation of similar operations overwhelms cybersecurity defenses, leading to widespread data breaches.
- Most-Likely: Continued evolution of cybercrime tactics with incremental improvements in cybersecurity responses.
6. Key Individuals and Entities
- TrustConnect Software PTY LTD (alleged entity)
- Proofpoint (research entity)
- Level RMM (affected vendor)
- Certificate authorities (involved in certificate issuance and revocation)
7. Thematic Tags
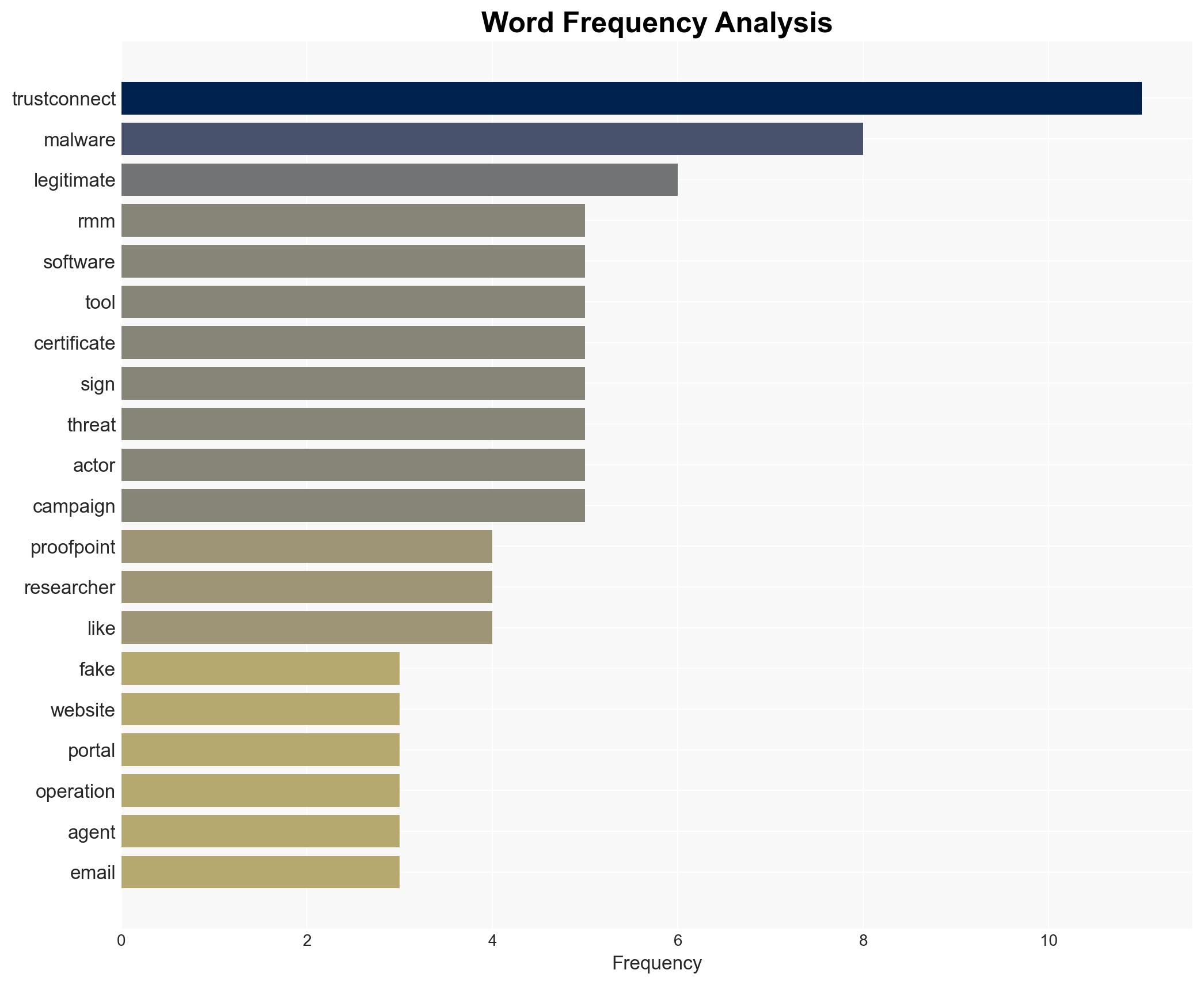
cybersecurity, digital certificates, cybercrime, remote access trojan, deception tactics, financial motivation, threat intelligence
Structured Analytic Techniques Applied
- Adversarial Threat Simulation: Model and simulate actions of cyber adversaries to anticipate vulnerabilities and improve resilience.
- Indicators Development: Detect and monitor behavioral or technical anomalies across systems for early threat detection.
- Bayesian Scenario Modeling: Quantify uncertainty and predict cyberattack pathways using probabilistic inference.
Explore more:
Cybersecurity Briefs ·
Daily Summary ·
Support us