Cybercriminals Leverage React2Shell to Redirect Web Traffic Through Compromised NGINX Servers
Published on: 2026-02-05
AI-powered OSINT brief from verified open sources. Automated NLP signal extraction with human verification. See our Methodology and Why WorldWideWatchers.
Intelligence Report: Hackers Exploit React2Shell to Hijack Web Traffic via Compromised NGINX Servers
1. BLUF (Bottom Line Up Front)
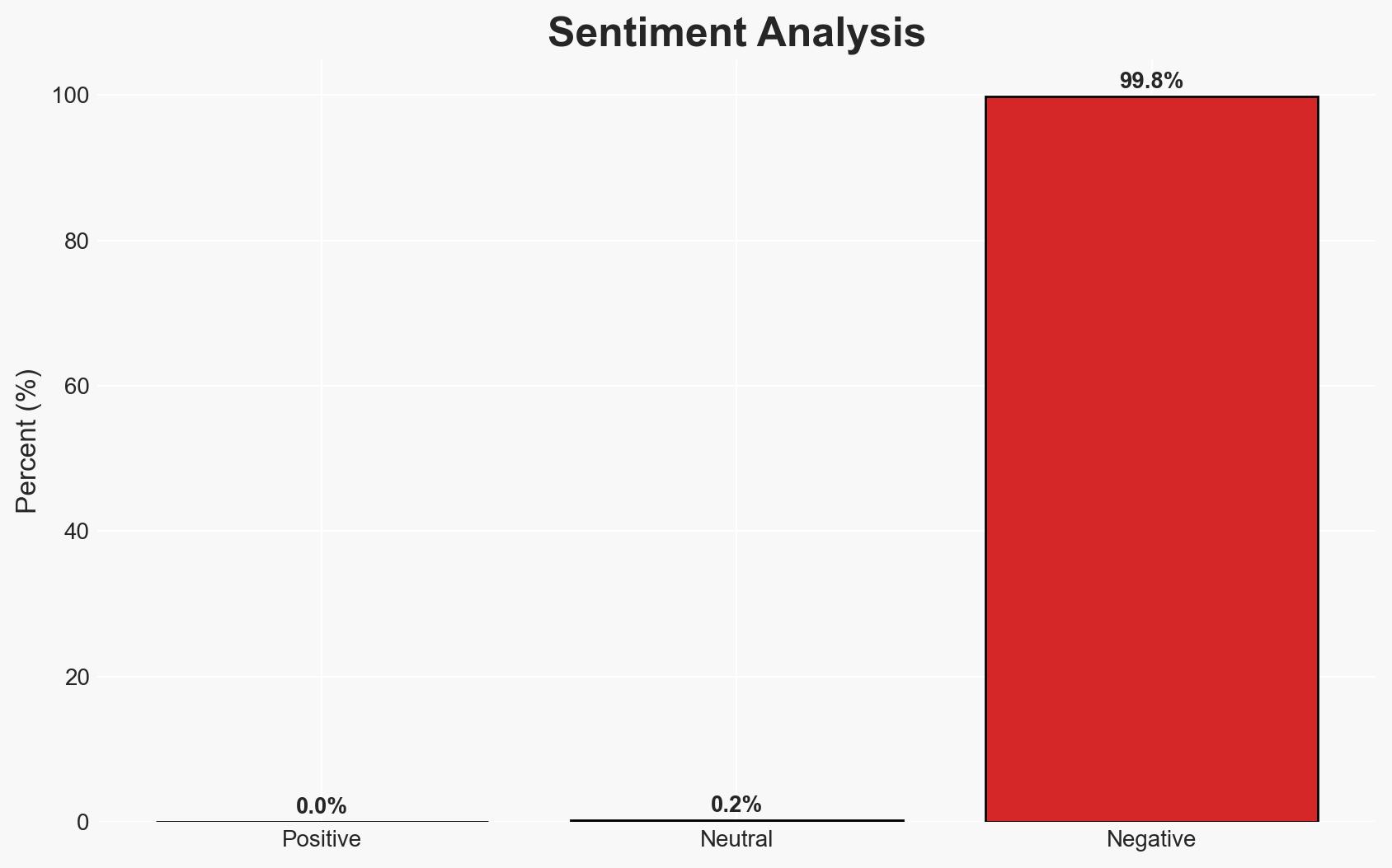
Hackers are exploiting the React2Shell vulnerability to hijack web traffic through compromised NGINX servers, primarily targeting Asian and government domains. This campaign involves sophisticated multi-stage toolkits to maintain persistence and control over web traffic. The most likely hypothesis is that the campaign is driven by financially motivated cybercriminals, with moderate confidence due to limited attribution data.
2. Competing Hypotheses
- Hypothesis A: The campaign is orchestrated by financially motivated cybercriminals aiming to redirect traffic for cryptomining and data theft. Supporting evidence includes the retrieval of cryptomining binaries and the targeting of high-value domains. However, the lack of direct attribution to specific criminal groups remains a key uncertainty.
- Hypothesis B: The campaign is state-sponsored, aiming to disrupt or surveil government and educational institutions. This is supported by the targeting of .edu and .gov domains. Contradicting evidence includes the use of cryptomining, which is typically associated with financial motives rather than state actors.
- Assessment: Hypothesis A is currently better supported due to the financial nature of the payloads and the broad targeting strategy. Indicators such as direct attribution to known criminal groups or shifts in targeting patterns could alter this assessment.
3. Key Assumptions and Red Flags
- Assumptions: The attackers are primarily motivated by financial gain; NGINX servers remain a key vector for exploitation; current defensive measures are insufficient to prevent further exploitation.
- Information Gaps: Specific attribution to threat actor groups; detailed understanding of the attackers’ infrastructure and command-and-control mechanisms.
- Bias & Deception Risks: Potential bias in attributing motives based on payloads; risk of deception through false-flag operations or misattribution of IP addresses.
4. Implications and Strategic Risks
This development could lead to increased cyber threats against critical infrastructure and heightened geopolitical tensions if state sponsorship is confirmed. The exploitation of NGINX servers may encourage similar tactics by other threat actors.
- Political / Geopolitical: Potential diplomatic fallout if state involvement is suspected, especially if government domains are compromised.
- Security / Counter-Terrorism: Increased risk to national security infrastructure and potential for broader cyber-espionage campaigns.
- Cyber / Information Space: Escalation in cyber operations targeting open-source software vulnerabilities, leading to broader impacts on internet security.
- Economic / Social: Potential economic impacts from disrupted web services and loss of trust in digital infrastructure.
5. Recommendations and Outlook
- Immediate Actions (0–30 days): Enhance monitoring of NGINX server configurations, deploy patches for React2Shell, and increase awareness among affected sectors.
- Medium-Term Posture (1–12 months): Develop partnerships for threat intelligence sharing, invest in cybersecurity training, and improve incident response capabilities.
- Scenario Outlook:
- Best: Successful mitigation and patching reduce exploitation attempts.
- Worst: Widespread disruption of critical services and confirmed state involvement.
- Most-Likely: Continued exploitation with gradual improvements in defensive measures.
6. Key Individuals and Entities
- Ryan Simon (Security Researcher)
- Datadog Security Labs
- GreyNoise (Threat Intelligence Firm)
- Not clearly identifiable from open sources in this snippet.
7. Thematic Tags
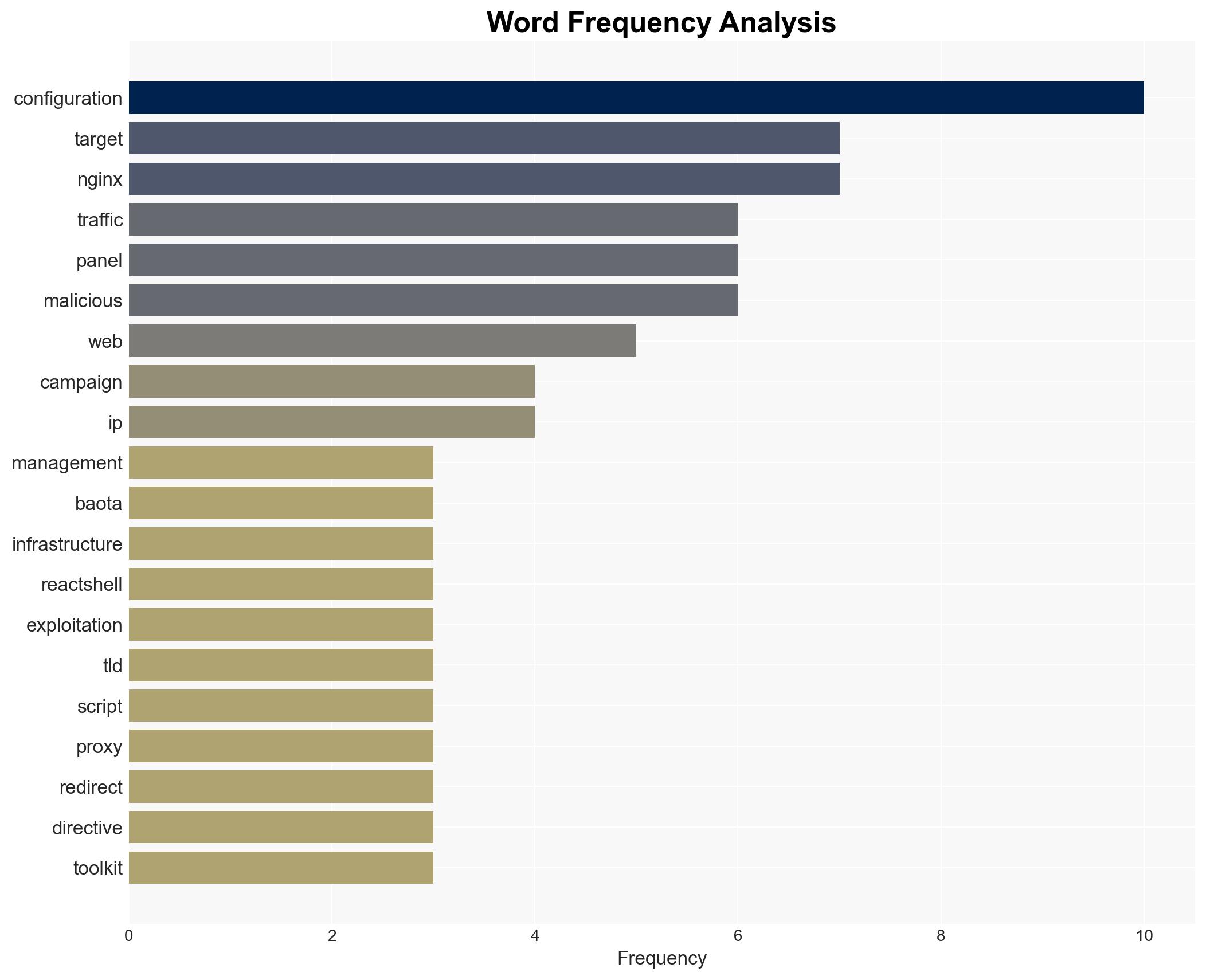
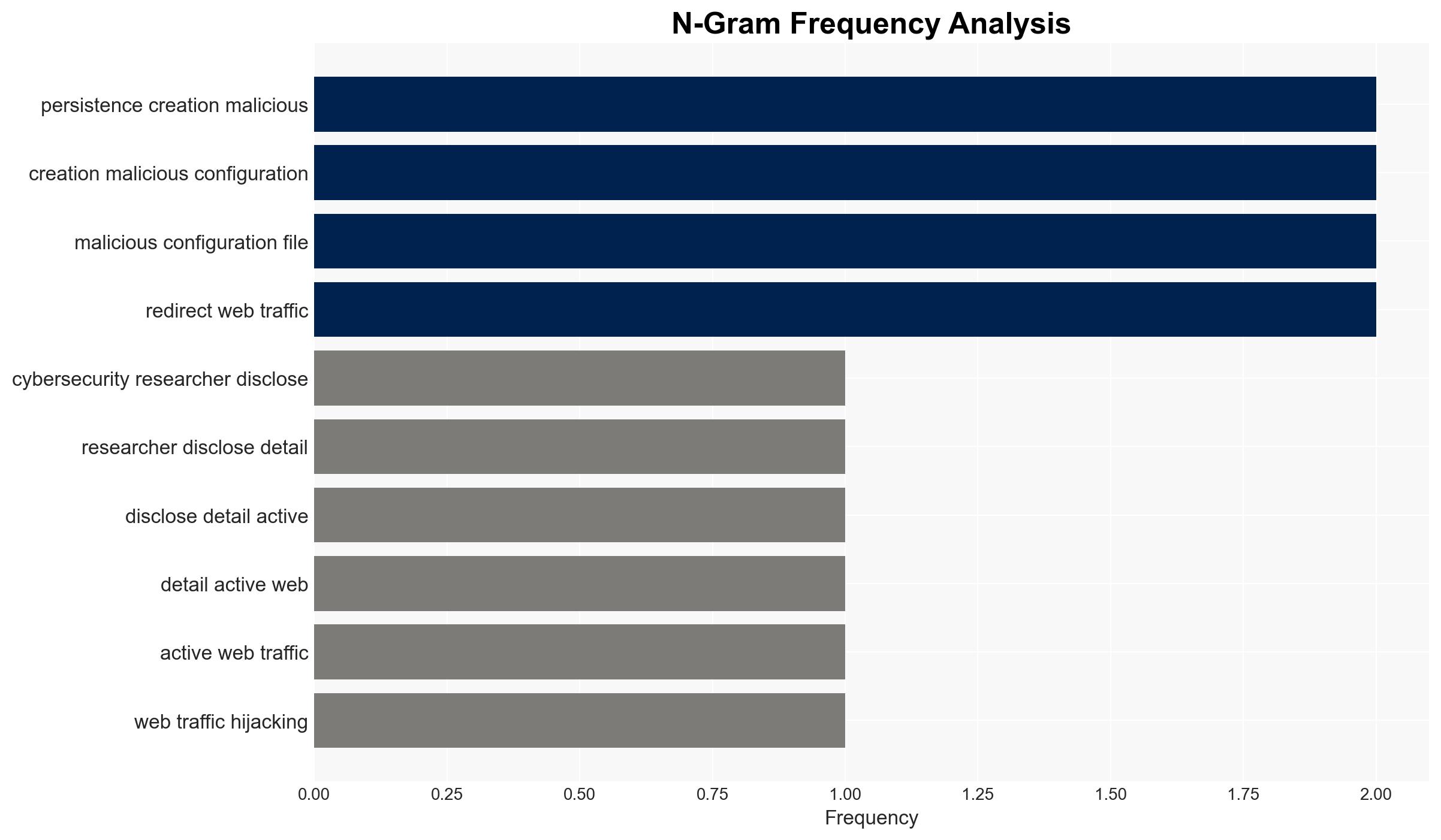
cybersecurity, web traffic hijacking, NGINX, React2Shell, cybercrime, cryptomining, threat intelligence
Structured Analytic Techniques Applied
- Adversarial Threat Simulation: Model and simulate actions of cyber adversaries to anticipate vulnerabilities and improve resilience.
- Indicators Development: Detect and monitor behavioral or technical anomalies across systems for early threat detection.
- Bayesian Scenario Modeling: Quantify uncertainty and predict cyberattack pathways using probabilistic inference.
Explore more:
Cybersecurity Briefs ·
Daily Summary ·
Support us