Cybercriminals Target Company Insiders with Financial Incentives to Compromise Security Systems
Published on: 2025-12-22
AI-powered OSINT brief from verified open sources. Automated NLP signal extraction with human verification. See our Methodology and Why WorldWideWatchers.
Intelligence Report: Insider Threat Hackers Paying Company Insiders to Bypass Security
1. BLUF (Bottom Line Up Front)
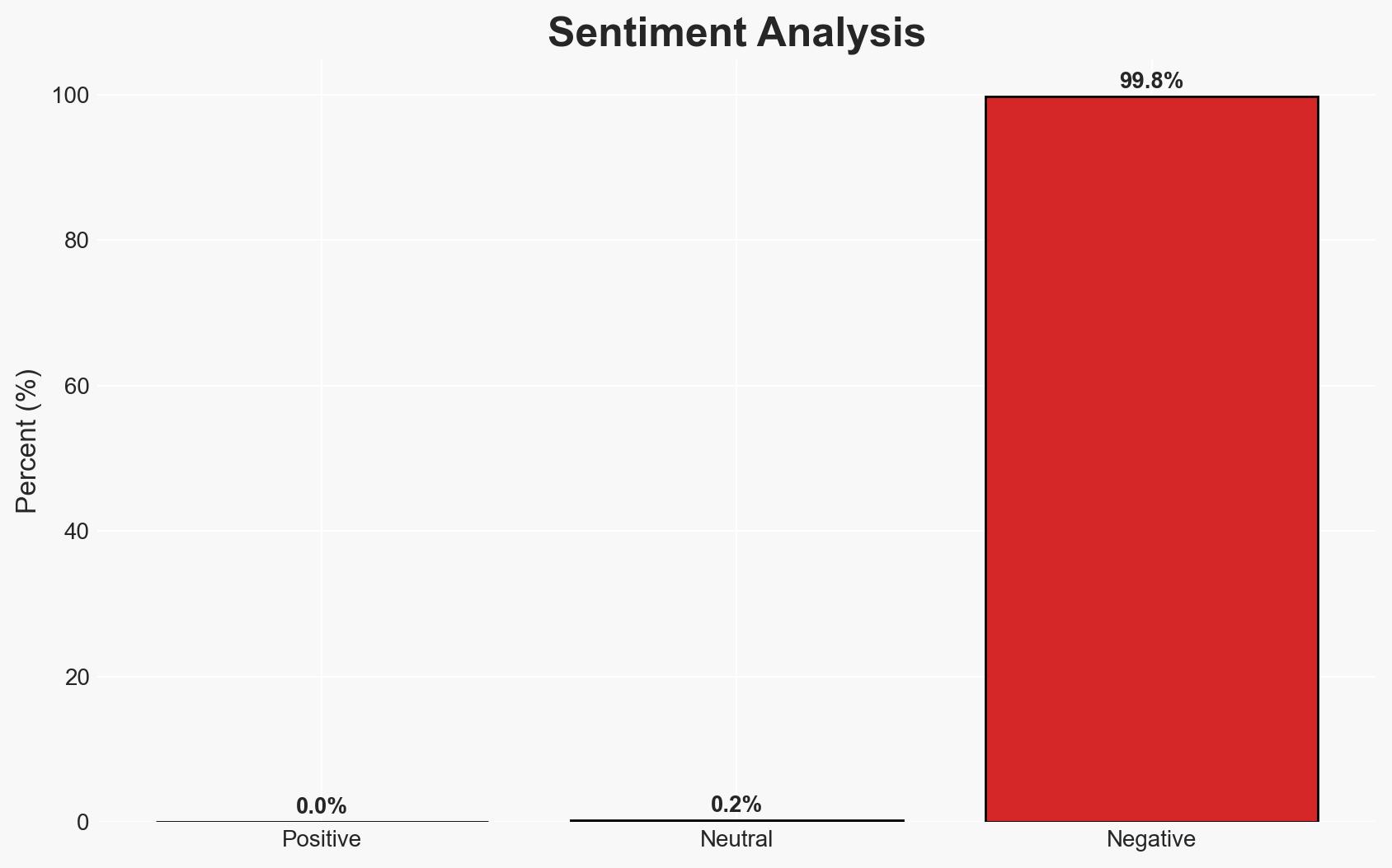
Cybercriminals are increasingly recruiting company insiders to bypass security measures, posing a significant threat to various sectors including finance, technology, and telecommunications. The most likely hypothesis is that this trend will continue to grow, leveraging emotional and financial incentives to compromise organizational security. This assessment is made with moderate confidence due to the evolving nature of cyber threats and insider involvement.
2. Competing Hypotheses
- Hypothesis A: Cybercriminals are primarily using financial incentives to recruit insiders, exploiting economic vulnerabilities among employees. This is supported by evidence of high payouts for insider cooperation. However, the extent of insider willingness and the scale of recruitment efforts remain uncertain.
- Hypothesis B: Emotional manipulation and dissatisfaction with work conditions are the primary drivers for insider cooperation, as suggested by advertisements framing collaboration as a path to financial freedom. This hypothesis is less supported due to limited direct evidence of emotional manipulation being the primary motivator.
- Assessment: Hypothesis A is currently better supported due to the clear financial incentives documented in the report. Indicators such as increased insider recruitment advertisements and financial distress among employees could shift this judgment.
3. Key Assumptions and Red Flags
- Assumptions: Insiders are motivated primarily by financial gain; cybercriminals have the resources to pay significant sums; insider recruitment is widespread across sectors.
- Information Gaps: Detailed statistics on the number of insiders recruited and the success rate of these operations; the full scope of sectors affected.
- Bias & Deception Risks: Potential bias in reporting from cybersecurity firms with vested interests; deception by cybercriminals overstating insider recruitment success to deter companies.
4. Implications and Strategic Risks
This development could lead to increased insider threats, complicating organizational security efforts and potentially resulting in significant data breaches. The trend may also encourage more sophisticated cybercriminal tactics.
- Political / Geopolitical: Potential for international tensions if state actors are implicated or if critical infrastructure is targeted.
- Security / Counter-Terrorism: Increased insider threats could complicate counter-terrorism efforts by providing adversaries with sensitive information.
- Cyber / Information Space: Enhanced cyber threat landscape with more frequent and sophisticated attacks leveraging insider access.
- Economic / Social: Potential economic impacts from data breaches and loss of consumer trust; social unrest if critical services are disrupted.
5. Recommendations and Outlook
- Immediate Actions (0–30 days): Implement enhanced monitoring of employee activities and dark web mentions; conduct security awareness training focusing on insider threats.
- Medium-Term Posture (1–12 months): Develop partnerships with cybersecurity firms for threat intelligence sharing; invest in advanced security technologies to detect insider threats.
- Scenario Outlook:
- Best: Companies successfully mitigate insider threats through enhanced security measures.
- Worst: Widespread insider cooperation leads to significant data breaches and operational disruptions.
- Most-Likely: Continued insider recruitment with sporadic but impactful breaches, necessitating ongoing vigilance.
6. Key Individuals and Entities
- Not clearly identifiable from open sources in this snippet.
7. Thematic Tags
cybersecurity, insider threats, cybercrime, financial incentives, data breaches, organizational security, cyber-espionage
Structured Analytic Techniques Applied
- Adversarial Threat Simulation: Model and simulate actions of cyber adversaries to anticipate vulnerabilities and improve resilience.
- Indicators Development: Detect and monitor behavioral or technical anomalies across systems for early threat detection.
- Bayesian Scenario Modeling: Quantify uncertainty and predict cyberattack pathways using probabilistic inference.
- Network Influence Mapping: Map influence relationships to assess actor impact.
Explore more:
Cybersecurity Briefs ·
Daily Summary ·
Support us