Cybercriminals Target PDF24 App to Install Covert PDFSIDER Backdoor via Spear-Phishing Attacks
Published on: 2026-01-19
AI-powered OSINT brief from verified open sources. Automated NLP signal extraction with human verification. See our Methodology and Why WorldWideWatchers.
Intelligence Report: Hackers Exploiting PDF24 App to Deploy Stealthy PDFSIDER Backdoor
1. BLUF (Bottom Line Up Front)
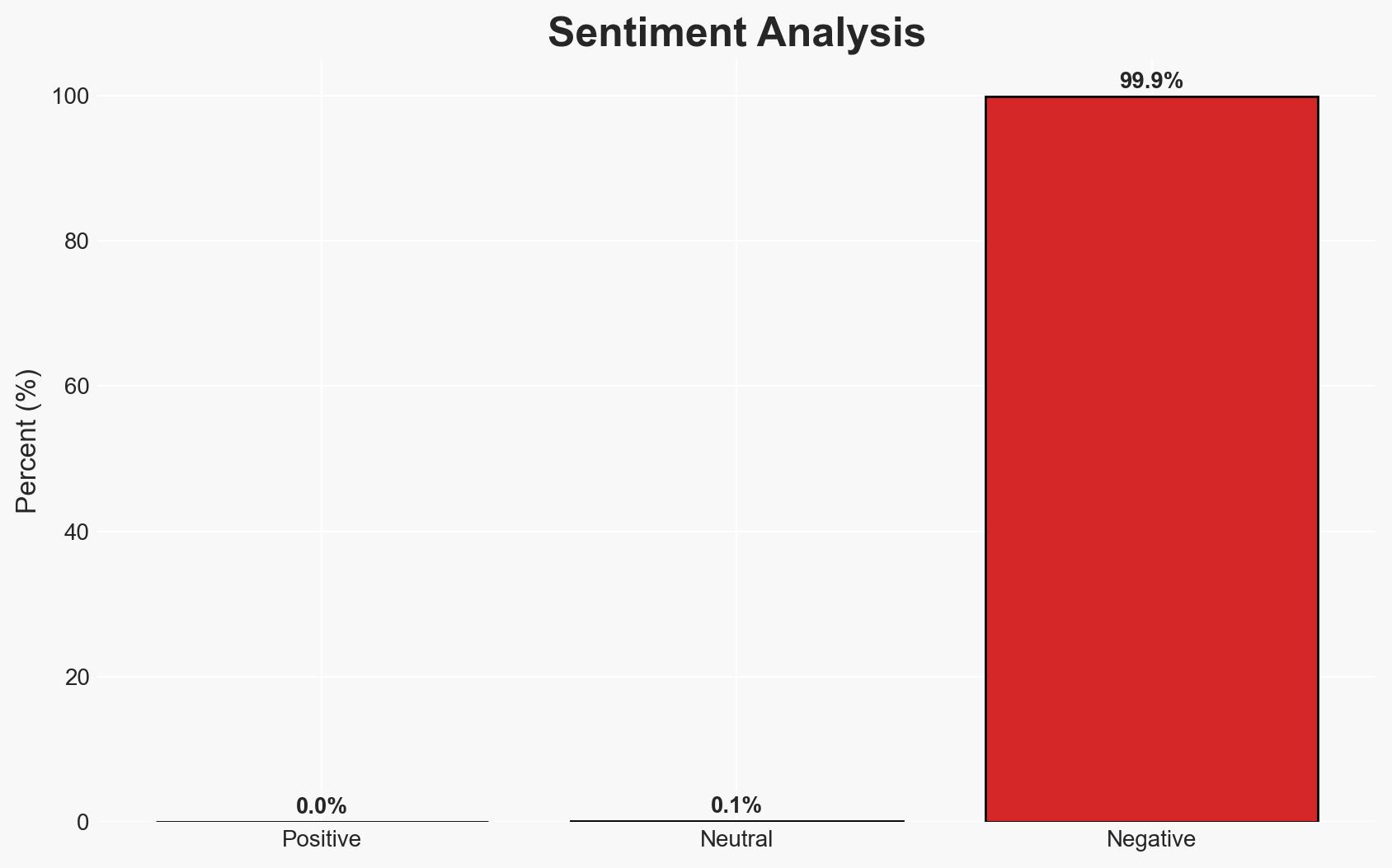
The PDFSIDER malware represents a sophisticated cyber threat exploiting the PDF24 App to create a stealthy backdoor, primarily affecting corporations and potentially linked to known hacking groups like Mustang Panda. The campaign’s advanced techniques suggest a focus on espionage rather than immediate financial gain. Overall, there is moderate confidence in the assessment due to the complexity of the threat and its potential connections to state-sponsored activities.
2. Competing Hypotheses
- Hypothesis A: PDFSIDER is primarily a tool for corporate espionage, targeting high-value corporate networks to extract sensitive information. This is supported by its advanced persistence and evasion techniques, and the targeting of a Fortune 100 corporation. However, the exact scale and scope of the campaign remain uncertain.
- Hypothesis B: PDFSIDER is a multipurpose tool used by various threat actors, including ransomware groups, to deliver diverse payloads. The evidence of ransomware groups adopting PDFSIDER supports this, but it contradicts the APT classification focused on long-term espionage.
- Assessment: Hypothesis A is currently better supported due to the malware’s sophisticated design and espionage-focused features. Indicators such as the use of advanced encryption and stealth techniques suggest a strategic intent beyond immediate financial gain. However, further evidence of ransomware use could shift this assessment.
3. Key Assumptions and Red Flags
- Assumptions: The malware’s primary objective is espionage; PDF24 App vulnerabilities are the main vector; Mustang Panda or similar groups are involved.
- Information Gaps: Full extent of the campaign’s targets; confirmation of Mustang Panda’s involvement; comprehensive list of affected entities.
- Bias & Deception Risks: Potential bias in attributing the attack to known groups without conclusive evidence; possible deception in the use of fake documents and impersonation tactics.
4. Implications and Strategic Risks
This development could signify an escalation in cyber espionage activities, potentially affecting geopolitical stability and corporate security. The use of legitimate software for malicious purposes highlights vulnerabilities in common digital tools.
- Political / Geopolitical: Increased tensions between nation-states if state-sponsored involvement is confirmed.
- Security / Counter-Terrorism: Heightened threat environment for corporations and government entities, necessitating enhanced cybersecurity measures.
- Cyber / Information Space: Potential for widespread adoption of similar techniques by other threat actors, complicating defense strategies.
- Economic / Social: Potential economic impacts from data breaches and loss of intellectual property; erosion of trust in digital tools.
5. Recommendations and Outlook
- Immediate Actions (0–30 days): Enhance monitoring of PDF24 App usage; conduct security audits for DLL side-loading vulnerabilities; increase awareness of spear-phishing tactics.
- Medium-Term Posture (1–12 months): Develop partnerships for information sharing on APT threats; invest in advanced threat detection capabilities; strengthen incident response protocols.
- Scenario Outlook: Best: Effective mitigation reduces threat impact; Worst: Widespread exploitation leads to major breaches; Most-Likely: Continued targeted attacks with gradual improvements in defense.
6. Key Individuals and Entities
- Resecurity (research firm)
- Miron Geek Software GmbH (developer of PDF24 App)
- Mustang Panda (suspected hacking group)
- Not clearly identifiable from open sources in this snippet (other individuals/entities)
7. Thematic Tags
cybersecurity, cyber-espionage, APT, malware, corporate security, cyber defense, DLL side-loading, ransomware
Structured Analytic Techniques Applied
- Adversarial Threat Simulation: Model and simulate actions of cyber adversaries to anticipate vulnerabilities and improve resilience.
- Indicators Development: Detect and monitor behavioral or technical anomalies across systems for early threat detection.
- Bayesian Scenario Modeling: Quantify uncertainty and predict cyberattack pathways using probabilistic inference.
- Network Influence Mapping: Map influence relationships to assess actor impact.
Explore more:
Cybersecurity Briefs ·
Daily Summary ·
Support us