Cybersecurity Incident at ManageMyHealth Raises Alarm for Patients and GPs
Published on: 2026-01-01
AI-powered OSINT brief from verified open sources. Automated NLP signal extraction with human verification. See our Methodology and Why WorldWideWatchers.
Intelligence Report: Health app cyber breach ‘incredibly concerning’
1. BLUF (Bottom Line Up Front)
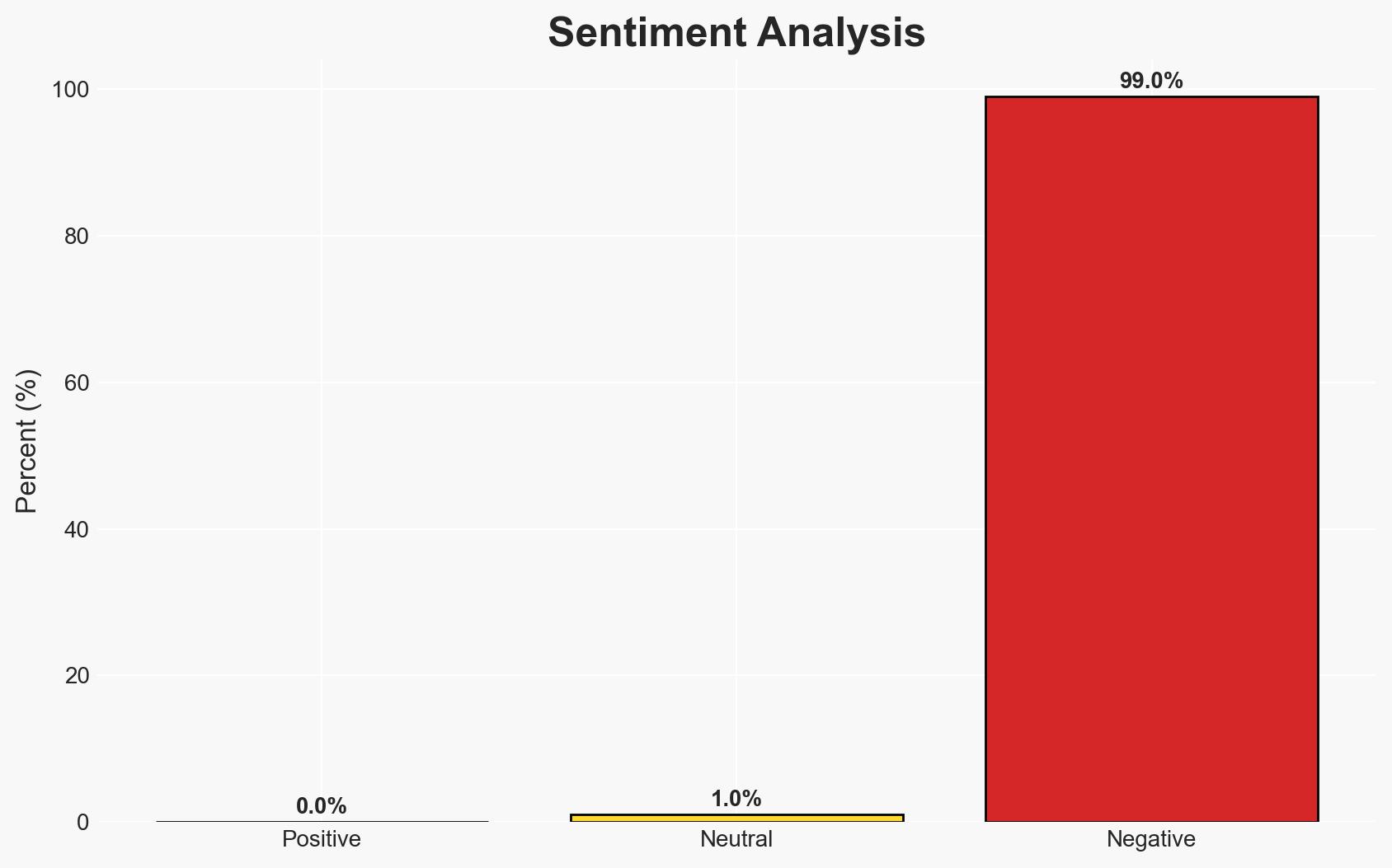
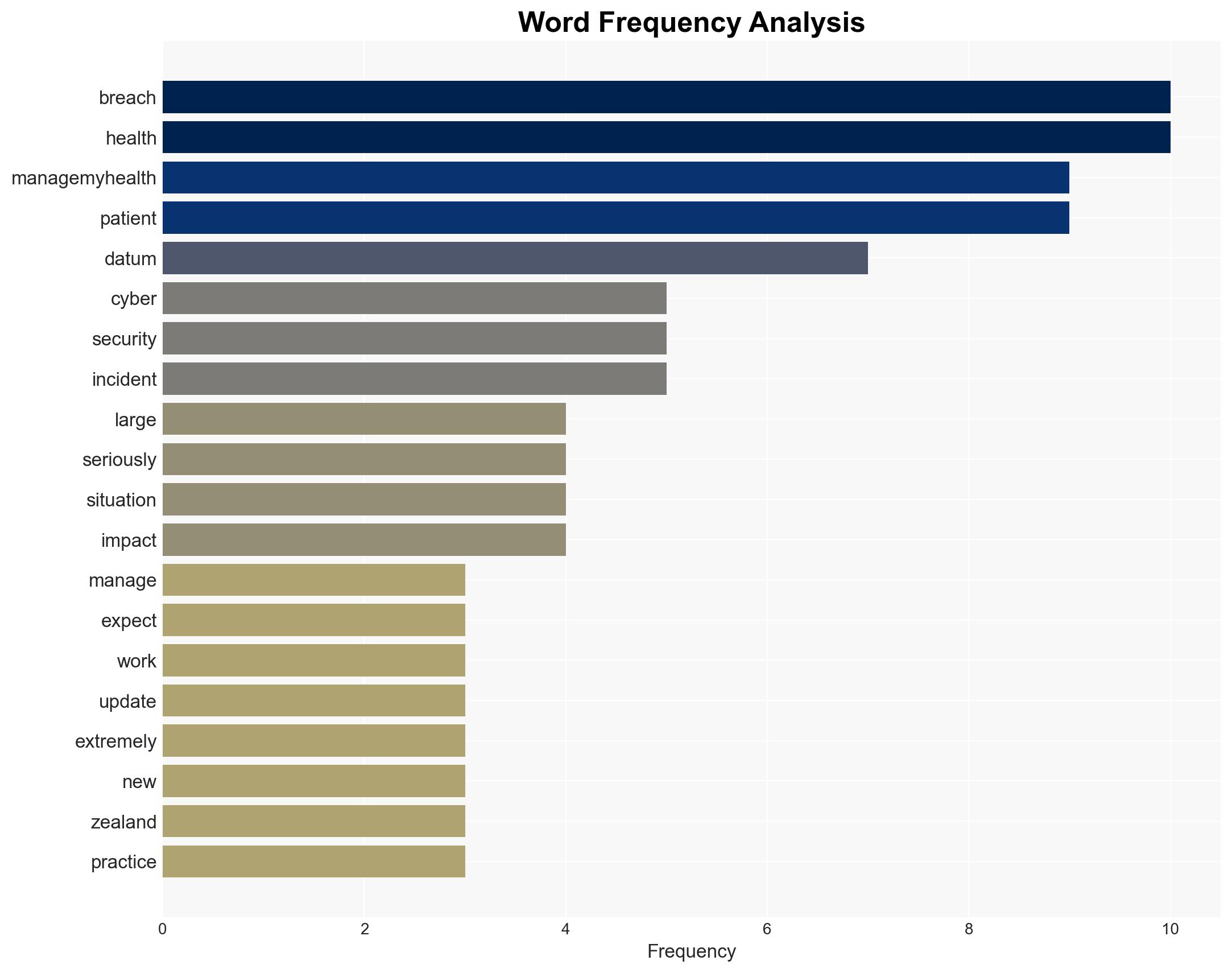
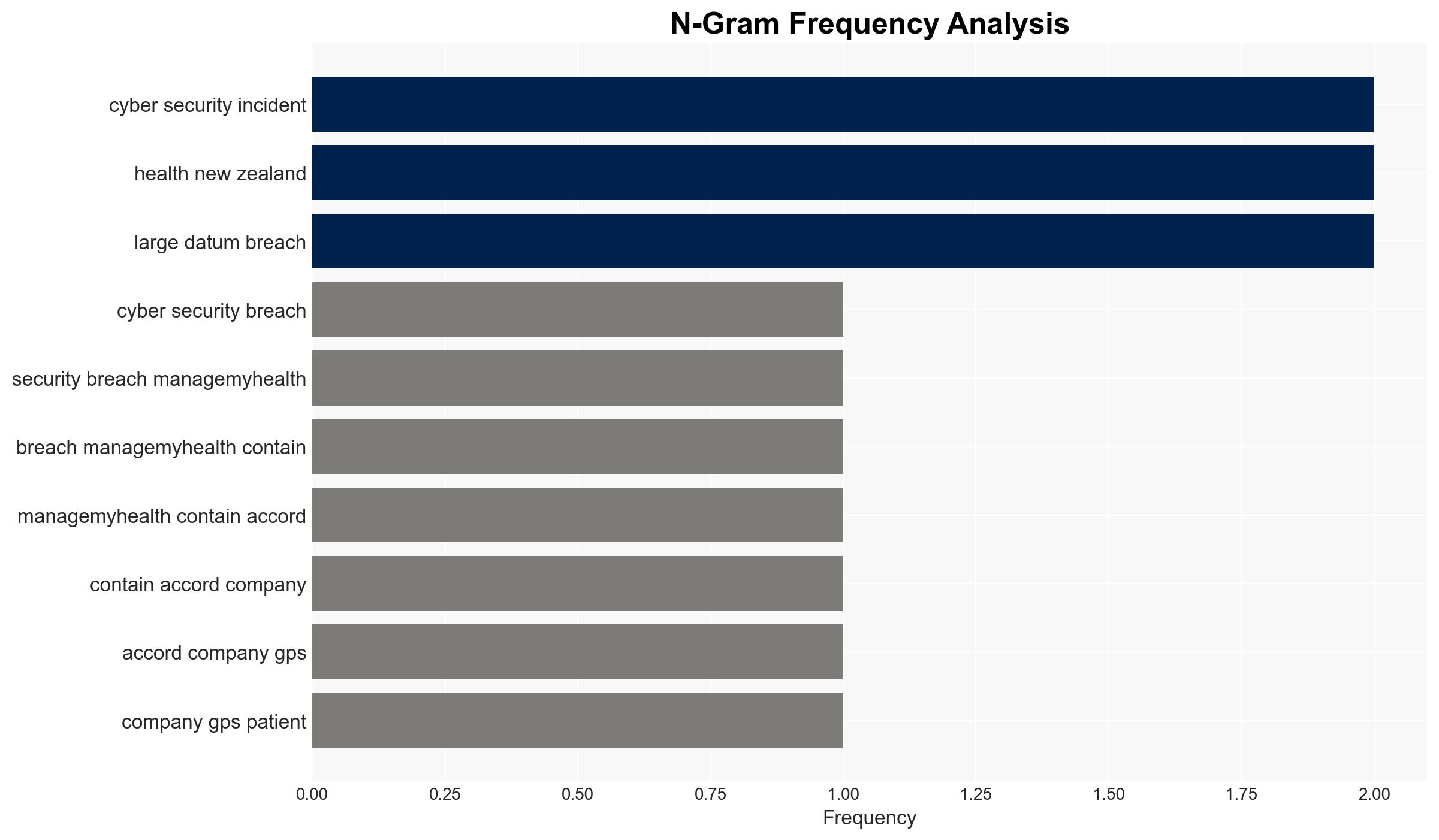
The cyber breach at ManageMyHealth, affecting potentially 6-7% of its 1.8 million users, poses significant risks to patient privacy and data integrity. The incident, involving unauthorized access, is under investigation, with outdated encryption protocols identified as a vulnerability. The breach’s scale is substantial, raising concerns about data security practices. Overall confidence in this assessment is moderate due to ongoing investigations and incomplete data.
2. Competing Hypotheses
- Hypothesis A: The breach was a targeted attack exploiting known vulnerabilities in ManageMyHealth’s outdated encryption protocols. Supporting evidence includes expert commentary on encryption issues and the large volume of data accessed. Key uncertainties involve the attacker’s identity and motives.
- Hypothesis B: The breach resulted from a broader systemic failure in cybersecurity practices rather than a targeted attack. Evidence includes the lack of immediate ransom demands and the engagement of international forensic consultants. Contradicting evidence is the scale and specific nature of the data accessed.
- Assessment: Hypothesis A is currently better supported due to the specific mention of outdated encryption protocols and the significant data volume accessed. Indicators that could shift this judgment include new information on attacker communications or systemic security audits revealing broader vulnerabilities.
3. Key Assumptions and Red Flags
- Assumptions: The breach was not an insider threat; ManageMyHealth’s reported containment measures are effective; the data breach size is accurately reported; the encryption protocol was the primary vulnerability.
- Information Gaps: Details on the attacker’s identity, specific methods used, and the full extent of data compromised remain unknown.
- Bias & Deception Risks: Potential bias in company statements aiming to minimize reputational damage; risk of underreporting the breach’s impact to maintain public confidence.
4. Implications and Strategic Risks
This breach could undermine public trust in digital health platforms, prompting regulatory scrutiny and potential legal actions. It may also incentivize similar attacks if perceived as lucrative or low-risk.
- Political / Geopolitical: Increased governmental pressure on digital health providers to enhance cybersecurity measures; potential international collaboration on cybersecurity standards.
- Security / Counter-Terrorism: Heightened alert for similar breaches in critical infrastructure sectors; potential exploitation by adversaries to undermine national security.
- Cyber / Information Space: Increased focus on encryption standards and cybersecurity protocols; potential for misinformation or disinformation campaigns exploiting the breach.
- Economic / Social: Financial liabilities for ManageMyHealth; potential loss of consumer trust in digital health solutions, impacting market growth.
5. Recommendations and Outlook
- Immediate Actions (0–30 days): Conduct a comprehensive security audit of ManageMyHealth; enhance encryption protocols; establish clear communication channels with affected users.
- Medium-Term Posture (1–12 months): Develop partnerships for cybersecurity intelligence sharing; invest in advanced threat detection and response capabilities; review and update regulatory frameworks.
- Scenario Outlook:
- Best: Breach contained with minimal data misuse, leading to strengthened cybersecurity measures.
- Worst: Widespread data misuse resulting in significant financial and reputational damage.
- Most-Likely: Moderate data misuse with increased regulatory oversight and improved security protocols.
6. Key Individuals and Entities
- Vino Ramayah, Chief Executive of ManageMyHealth
- Karen Chhour, Duty Minister
- Daniel Ayers, Cyber Security Expert
- Health New Zealand
7. Thematic Tags
cybersecurity, data breach, health information, encryption, digital privacy, regulatory compliance, public trust
Structured Analytic Techniques Applied
- Adversarial Threat Simulation: Model and simulate actions of cyber adversaries to anticipate vulnerabilities and improve resilience.
- Indicators Development: Detect and monitor behavioral or technical anomalies across systems for early threat detection.
- Bayesian Scenario Modeling: Quantify uncertainty and predict cyberattack pathways using probabilistic inference.
Explore more:
Cybersecurity Briefs ·
Daily Summary ·
Support us