Cybersecurity Risks for Industrial Automation in Eastern Europe: Q3 2025 Analysis
Published on: 2025-12-22
AI-powered OSINT brief from verified open sources. Automated NLP signal extraction with human verification. See our Methodology and Why WorldWideWatchers.
Intelligence Report: Threat landscape for industrial automation systems Europe Q3 2025
1. BLUF (Bottom Line Up Front)
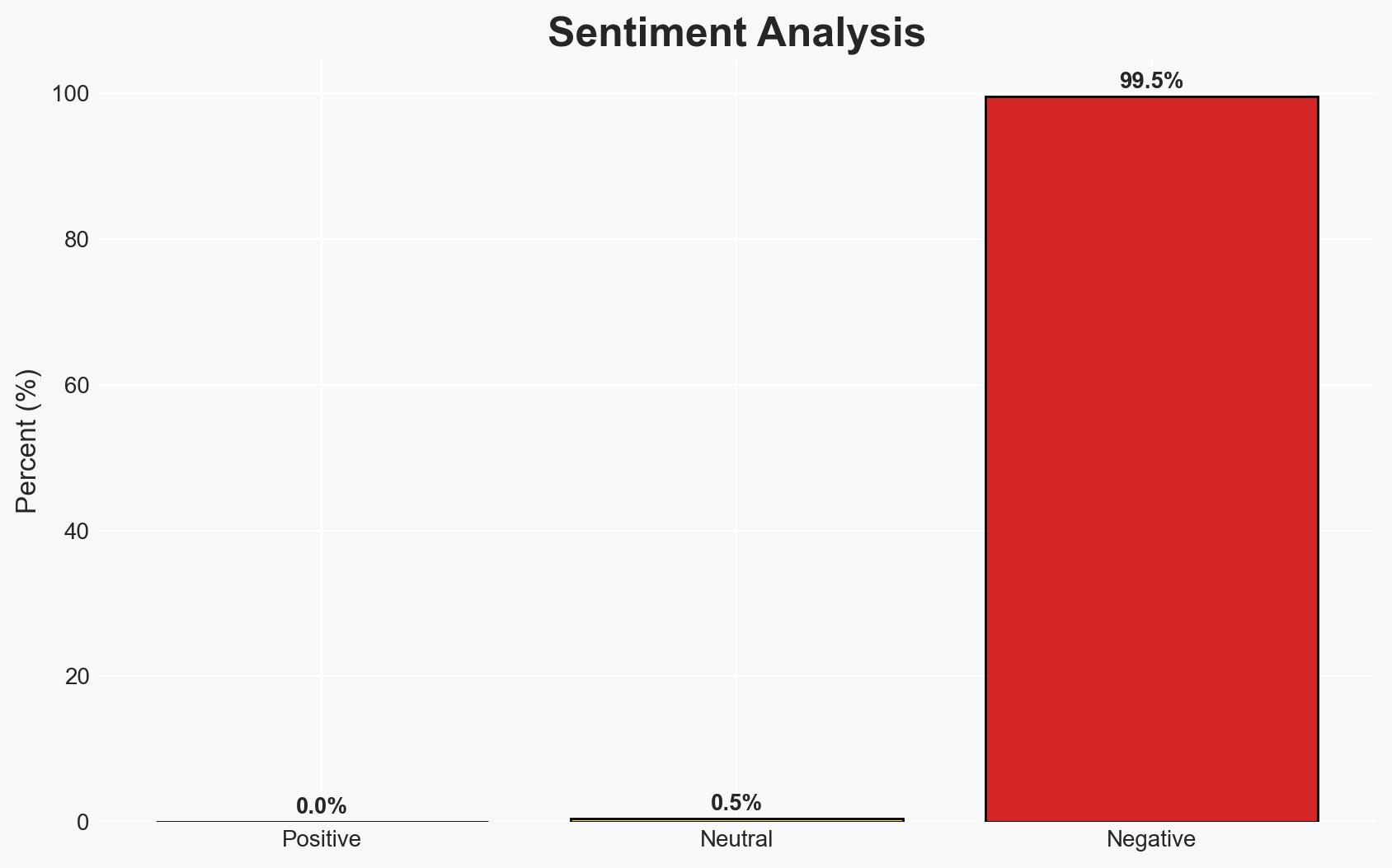
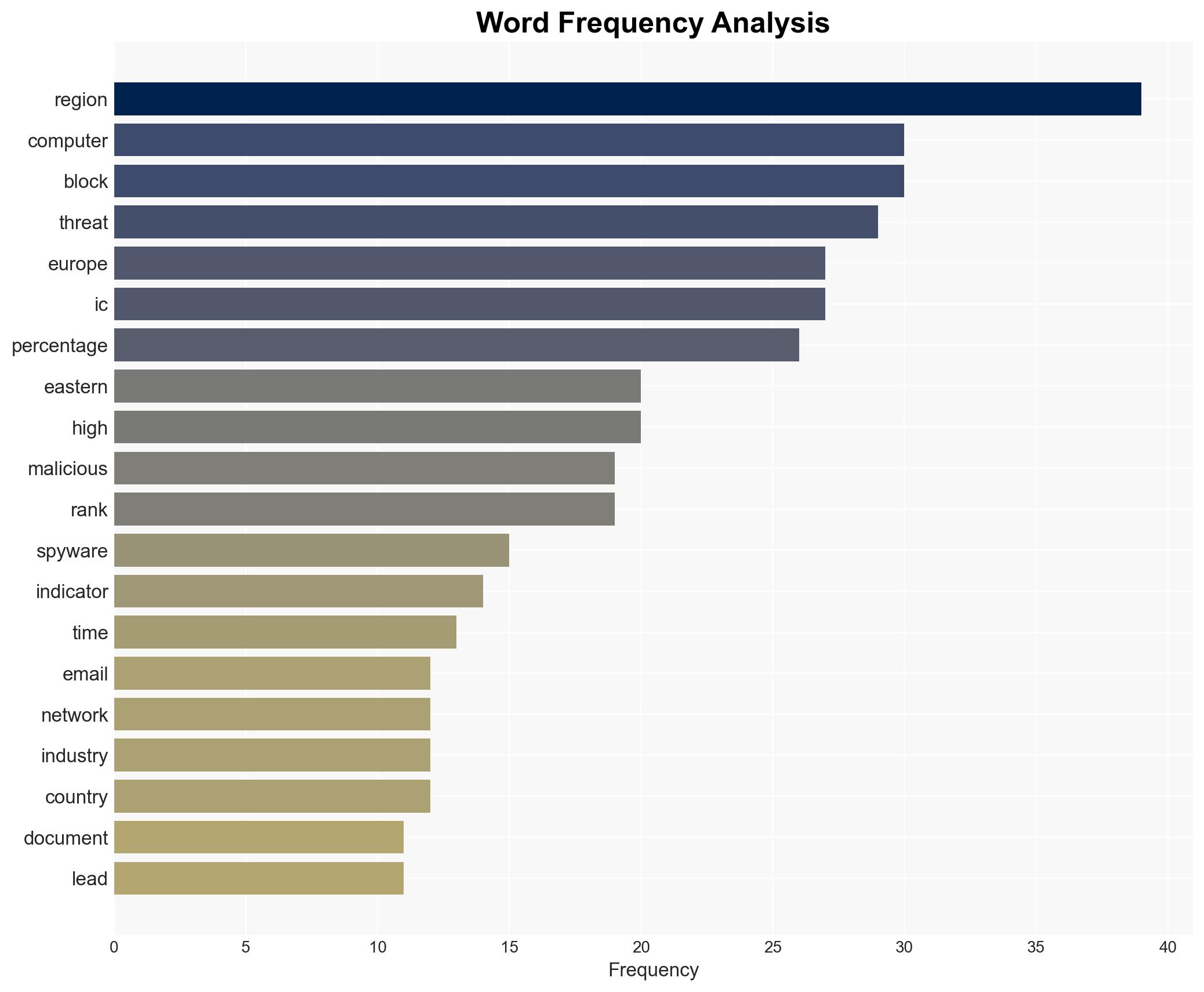
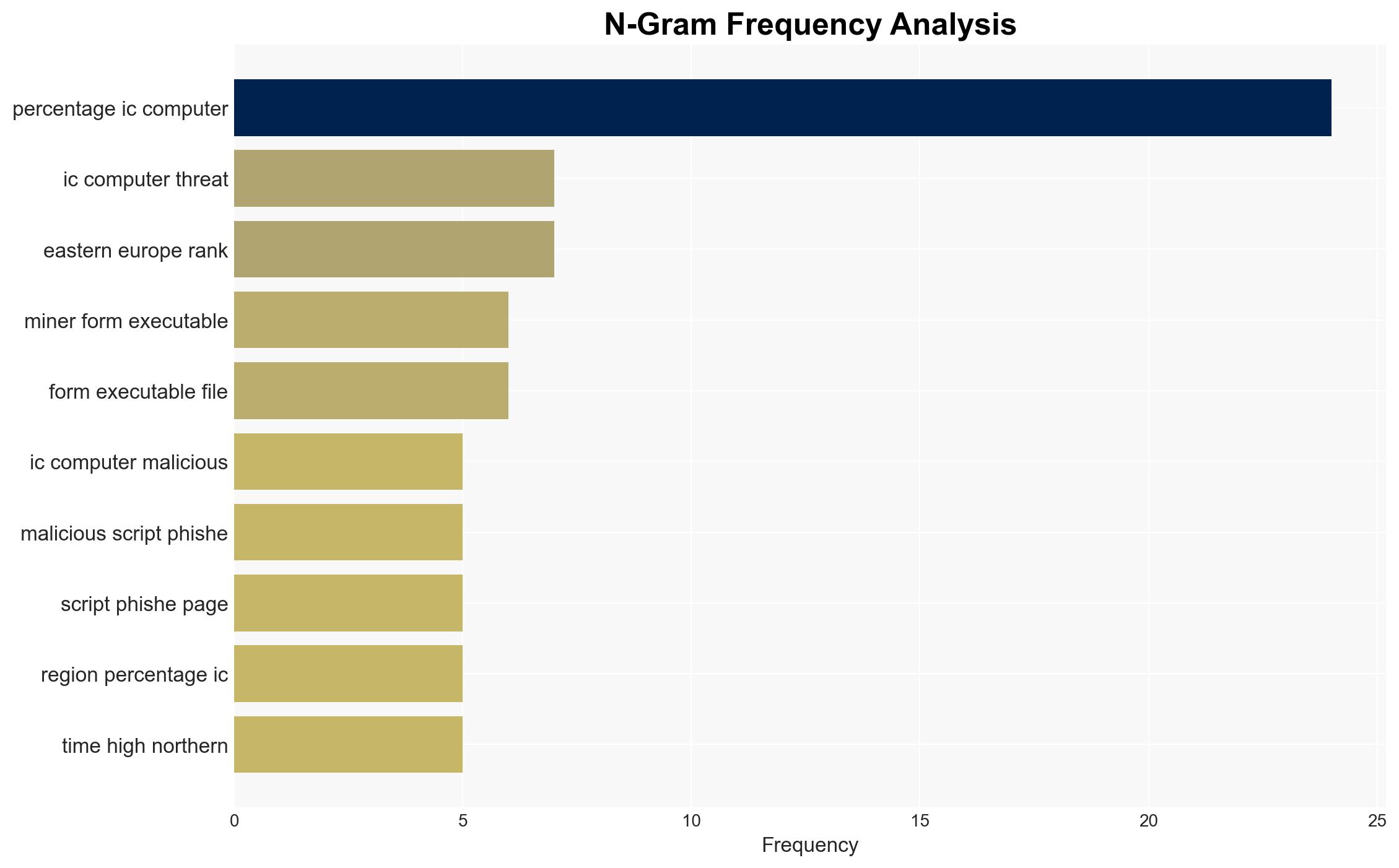
The threat landscape for industrial automation systems in Eastern Europe is characterized by a high risk of targeted cyber attacks, particularly through email threats and spyware. The building automation industry is notably vulnerable. Despite a decrease in overall threat indicators, the region remains a significant target. Overall confidence in this assessment is moderate due to existing information gaps and potential biases.
2. Competing Hypotheses
- Hypothesis A: The high incidence of email threats and spyware in Eastern Europe is primarily due to increased targeting by advanced persistent threat (APT) groups exploiting regional vulnerabilities. This is supported by the higher-than-average rates of blocked threats and malicious documents. However, the specific attribution to APT groups lacks direct evidence.
- Hypothesis B: The elevated threat levels are a result of broader global trends in cybercrime, with Eastern Europe being a convenient target due to less robust cybersecurity measures. While this hypothesis explains the regional vulnerability, it does not account for the specific targeting of industrial systems.
- Assessment: Hypothesis A is currently better supported due to the specific targeting of industrial systems and the use of sophisticated attack vectors. Key indicators that could shift this judgment include evidence of increased cybersecurity measures or a change in threat actor tactics.
3. Key Assumptions and Red Flags
- Assumptions: The data accurately reflects the threat landscape; threat actors are primarily external; industrial systems are inadequately protected; regional cybersecurity capabilities are limited.
- Information Gaps: Lack of specific attribution to threat actors; insufficient data on the effectiveness of regional cybersecurity measures; unclear motivations behind targeting specific industries.
- Bias & Deception Risks: Potential for cognitive bias in interpreting threat data; source bias from cybersecurity firms with vested interests; possible deception by threat actors to obscure true intentions.
4. Implications and Strategic Risks
The current threat landscape could lead to increased regional instability and economic disruption if industrial systems are compromised. Over time, this may necessitate stronger international cooperation and cybersecurity investments.
- Political / Geopolitical: Potential for increased tensions between Eastern European countries and perceived state-sponsored attackers.
- Security / Counter-Terrorism: Heightened alertness and resource allocation towards cybersecurity defenses; potential for spillover into physical security domains.
- Cyber / Information Space: Increased cyber defense initiatives and information sharing among affected industries and governments.
- Economic / Social: Potential economic impact on industries due to disruptions; possible public concern over cybersecurity vulnerabilities.
5. Recommendations and Outlook
- Immediate Actions (0–30 days): Enhance monitoring of phishing and spyware activities; initiate threat intelligence sharing among regional partners; conduct vulnerability assessments of critical infrastructure.
- Medium-Term Posture (1–12 months): Develop resilience measures through cybersecurity training; establish partnerships with international cybersecurity entities; invest in advanced threat detection technologies.
- Scenario Outlook: Best: Strengthened cybersecurity measures reduce threat levels. Worst: Major cyber attack disrupts industrial operations. Most-Likely: Continued moderate threat level with sporadic incidents, driven by both APT and cybercriminal activities.
6. Key Individuals and Entities
- Not clearly identifiable from open sources in this snippet.
7. Thematic Tags
cybersecurity, industrial cybersecurity, phishing, spyware, Eastern Europe, building automation, cyber threats, threat intelligence
Structured Analytic Techniques Applied
- Adversarial Threat Simulation: Model and simulate actions of cyber adversaries to anticipate vulnerabilities and improve resilience.
- Indicators Development: Detect and monitor behavioral or technical anomalies across systems for early threat detection.
- Bayesian Scenario Modeling: Quantify uncertainty and predict cyberattack pathways using probabilistic inference.
- Network Influence Mapping: Map influence relationships to assess actor impact.
Explore more:
Cybersecurity Briefs ·
Daily Summary ·
Support us