Daily Creation of 450,000 Malware Threats: Essential Strategies to Safeguard Your Computer
Published on: 2025-12-03
AI-powered OSINT brief from verified open sources. Automated NLP signal extraction with human verification. See our Methodology and Why WorldWideWatchers.
Intelligence Report: Thousands of Computer Viruses Are Created Every Day Heres How to Protect Your Computer From Cyberattacks
1. BLUF (Bottom Line Up Front)
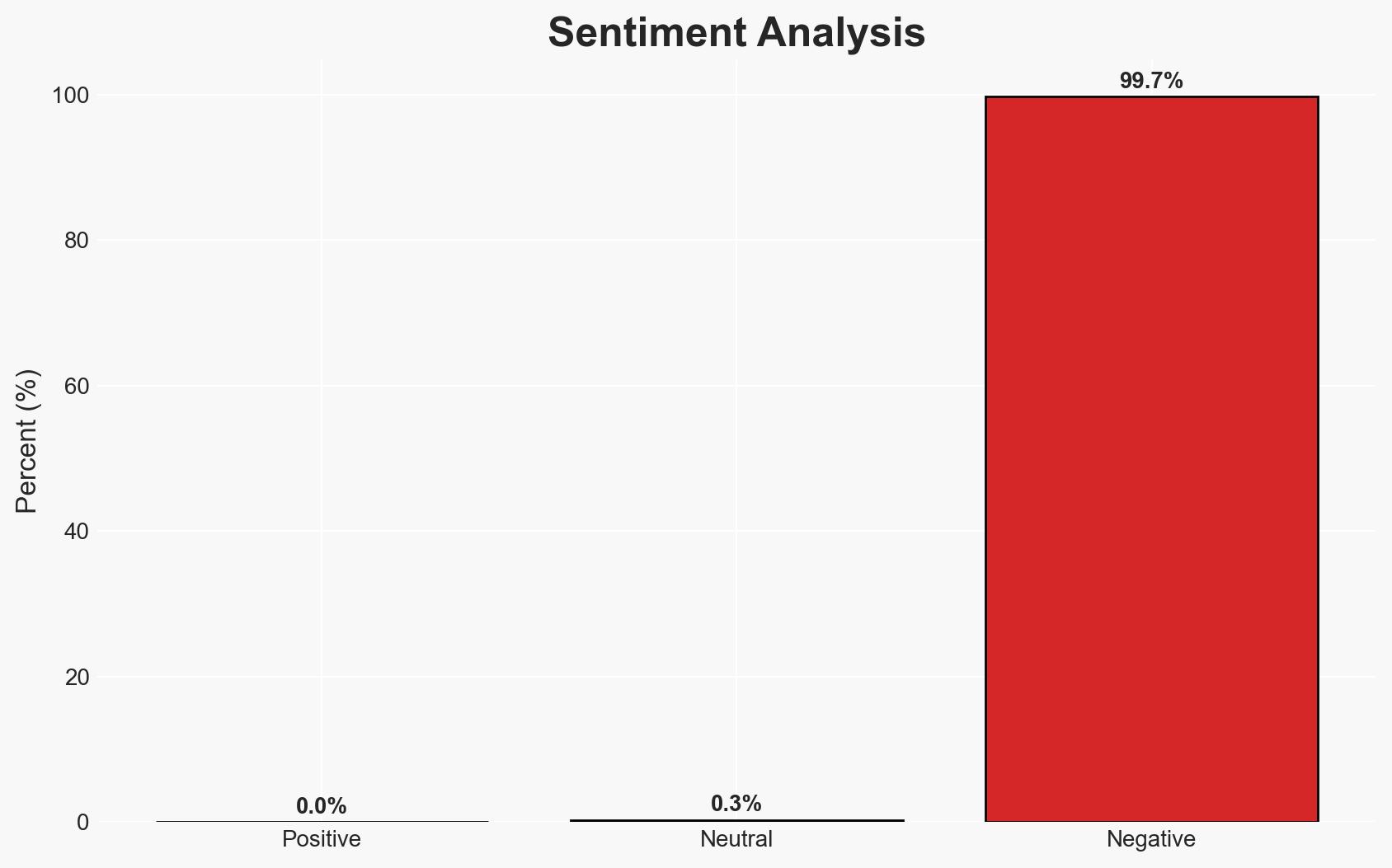
The proliferation of approximately 450,000 new malicious programs daily poses significant cybersecurity threats to individuals and organizations. Effective protection requires timely software updates and robust antivirus measures. The most likely hypothesis is that increased cybersecurity awareness and practices can mitigate these threats, with moderate confidence due to existing information gaps and potential biases in threat reporting.
2. Competing Hypotheses
- Hypothesis A: The rapid creation of new malware is primarily driven by organized cybercriminal groups seeking financial gain. Supporting evidence includes the targeting of personal data for theft and ransom. Contradicting evidence is the lack of specific attribution to organized groups in the snippet.
- Hypothesis B: The increase in malware is largely due to the availability of malware creation tools and scripts, enabling less sophisticated actors to participate in cybercrime. This is supported by the sheer volume of new malware and the general accessibility of such tools. Contradicting evidence includes the absence of explicit mention of these tools in the snippet.
- Assessment: Hypothesis B is currently better supported due to the high volume of malware, suggesting widespread participation rather than concentrated efforts by a few groups. Indicators that could shift this judgment include evidence of coordinated campaigns or specific group attributions.
3. Key Assumptions and Red Flags
- Assumptions: The snippet assumes that antivirus software and regular updates are effective against most threats; that users will implement recommended security practices; that the volume of malware correlates with threat level.
- Information Gaps: Lack of detailed attribution for malware sources; effectiveness data of current antivirus solutions against new threats; user compliance rates with security recommendations.
- Bias & Deception Risks: Potential bias in underestimating the sophistication of threats; risk of over-reliance on vendor-provided security solutions; possible manipulation in threat reporting to drive software sales.
4. Implications and Strategic Risks
The continuous evolution of malware could lead to increased cybersecurity incidents, affecting both individuals and organizations. This trend may drive policy changes and influence international cybersecurity cooperation.
- Political / Geopolitical: Potential for increased tensions between nations over cyber attribution and response measures.
- Security / Counter-Terrorism: Heightened risk of cyberattacks on critical infrastructure, requiring enhanced defensive measures.
- Cyber / Information Space: Escalation in cyber defense spending and innovation in cybersecurity technologies.
- Economic / Social: Potential economic impact from data breaches and ransomware attacks, affecting consumer trust and business operations.
5. Recommendations and Outlook
- Immediate Actions (0–30 days): Increase public awareness campaigns on cybersecurity best practices; enhance monitoring of emerging threats.
- Medium-Term Posture (1–12 months): Develop partnerships with cybersecurity firms for threat intelligence sharing; invest in advanced threat detection capabilities.
- Scenario Outlook:
- Best: Effective global cooperation reduces malware proliferation.
- Worst: Major cyberattack on critical infrastructure causes widespread disruption.
- Most-Likely: Continued rise in malware with incremental improvements in defense strategies.
6. Key Individuals and Entities
- Not clearly identifiable from open sources in this snippet.
7. Thematic Tags
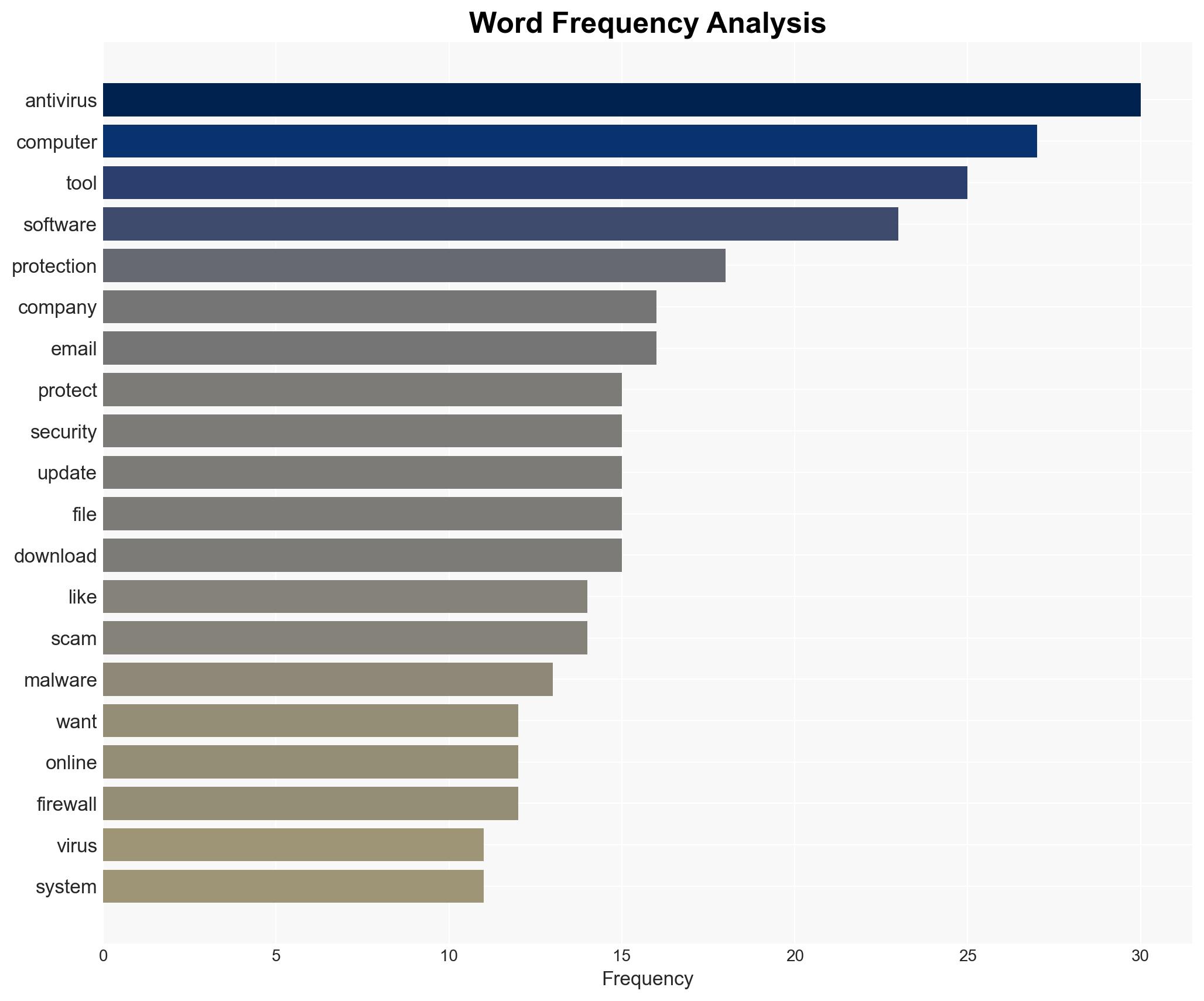
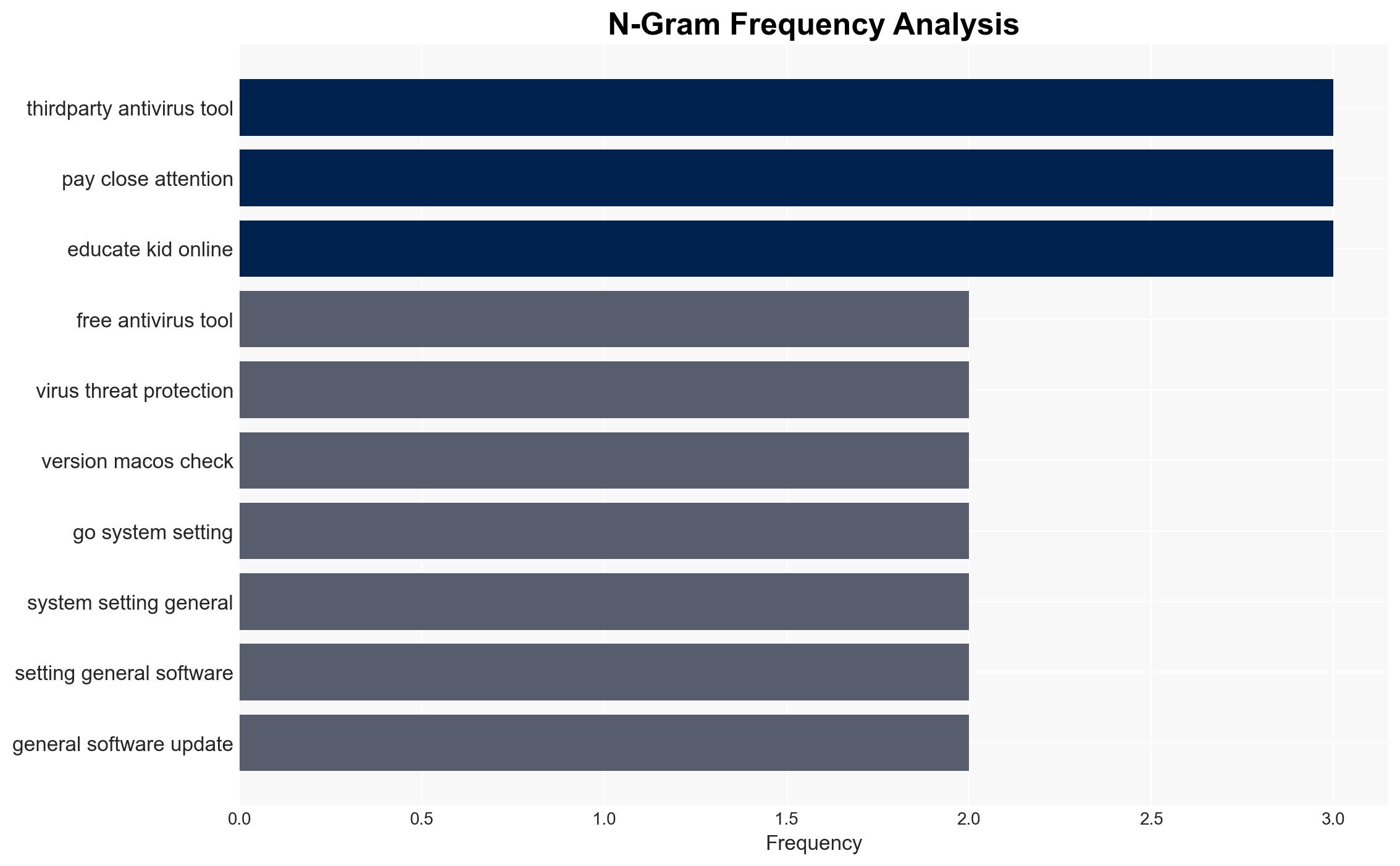
Cybersecurity, malware, antivirus, cybercrime, data protection, information security, threat mitigation
Structured Analytic Techniques Applied
- Adversarial Threat Simulation: Model and simulate actions of cyber adversaries to anticipate vulnerabilities and improve resilience.
- Indicators Development: Detect and monitor behavioral or technical anomalies across systems for early threat detection.
- Bayesian Scenario Modeling: Quantify uncertainty and predict cyberattack pathways using probabilistic inference.
- Network Influence Mapping: Map influence relationships to assess actor impact.
Explore more:
Cybersecurity Briefs ·
Daily Summary ·
Support us