Dangerous Android VPNs are lurking on the Google Play Store Here are the safe ones that are on sale – TechRadar
Published on: 2025-11-11
AI-powered OSINT brief from verified open sources. Automated NLP signal extraction with human verification. See our Methodology and Why WorldWideWatchers.
Intelligence Report: Dangerous Android VPNs are lurking on the Google Play Store Here are the safe ones that are on sale – TechRadar
1. BLUF (Bottom Line Up Front)
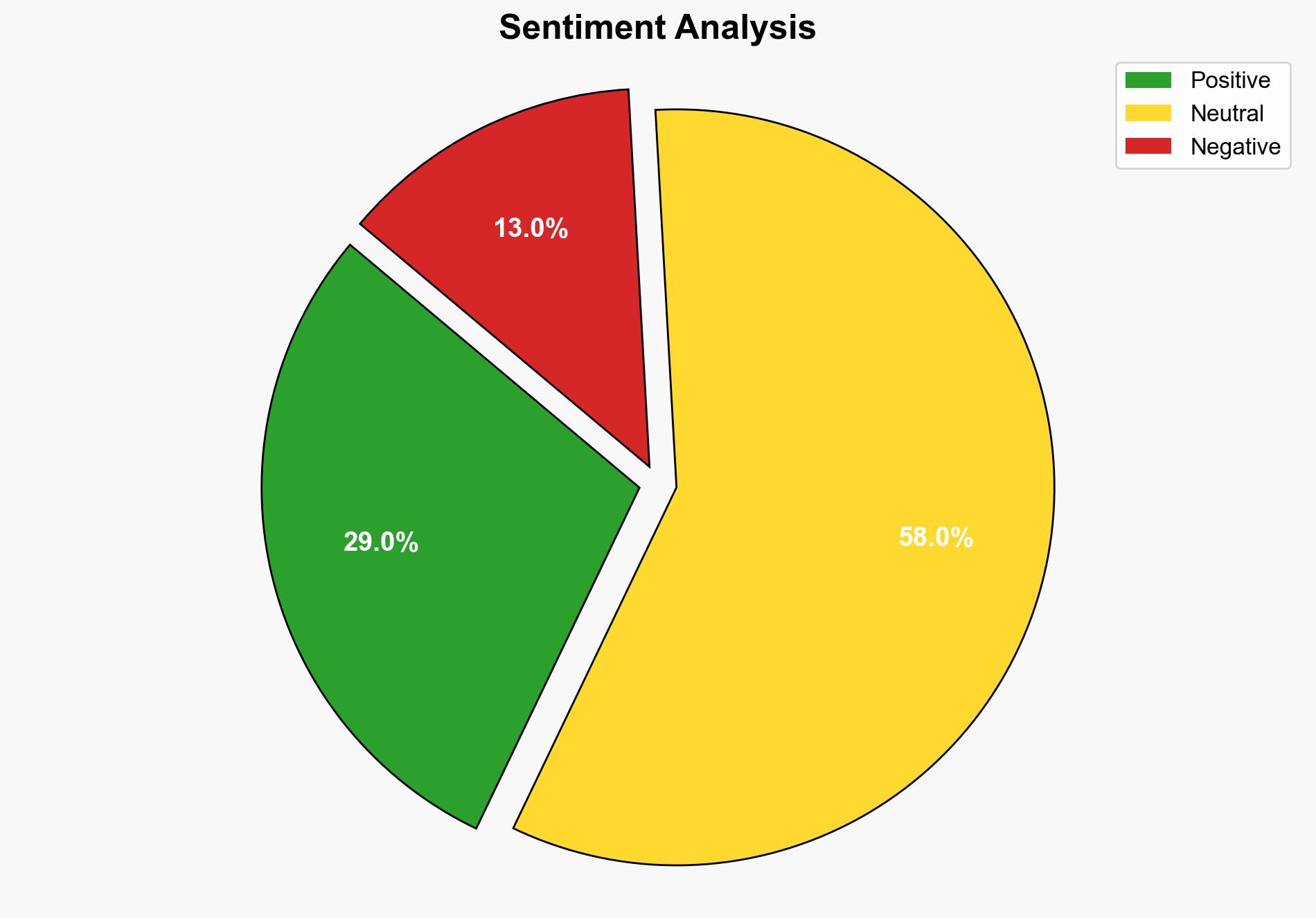
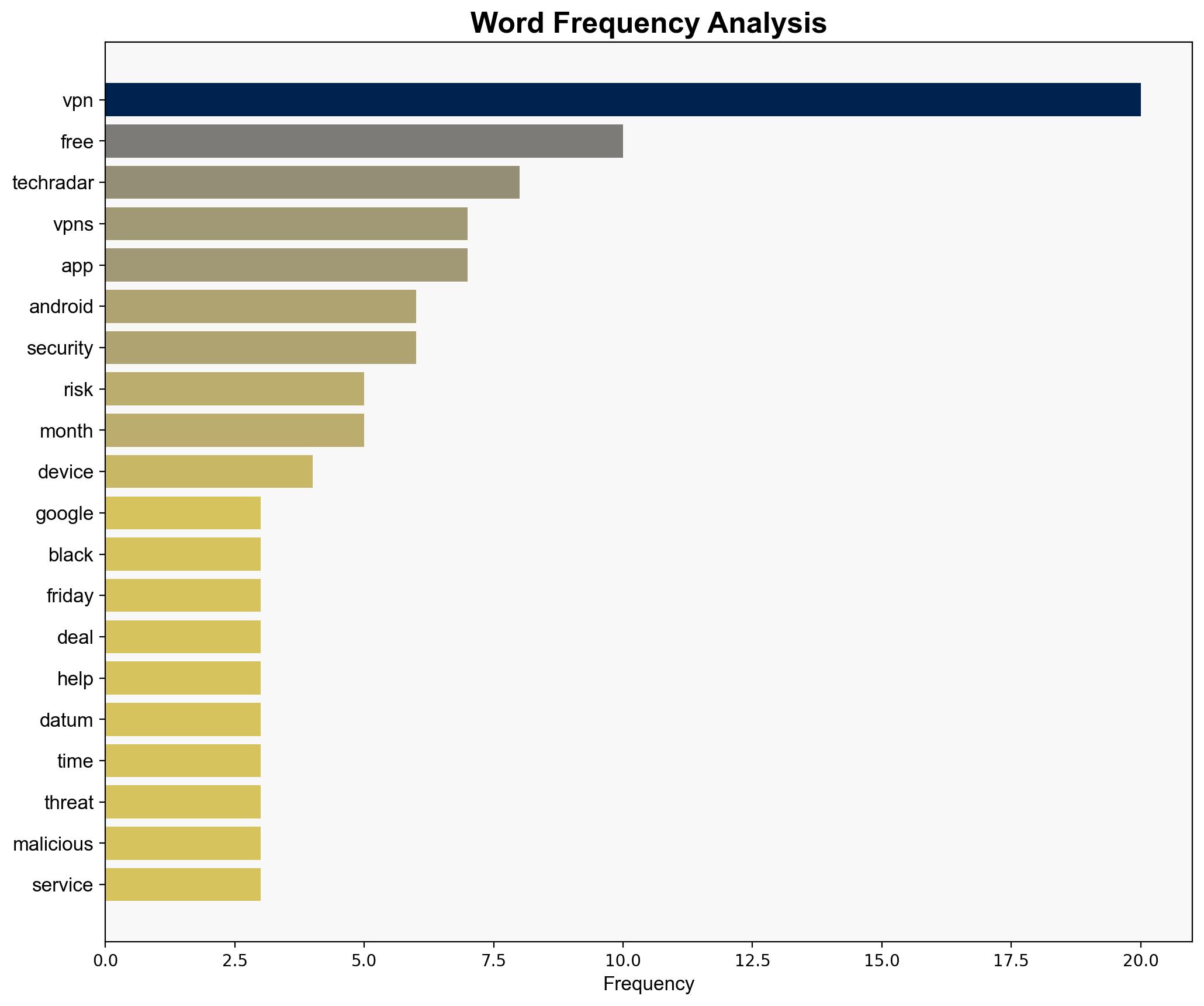
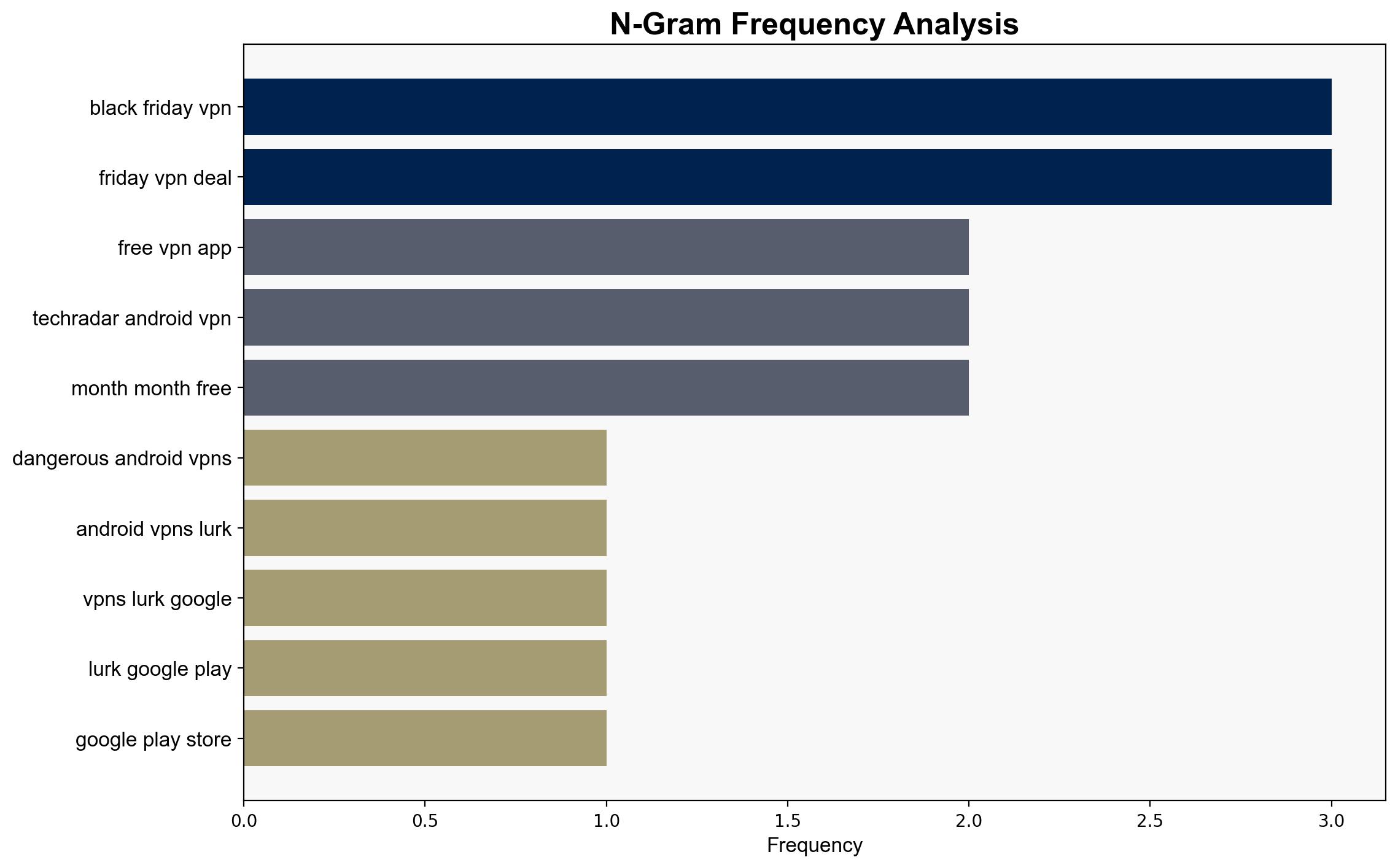
There is a significant threat posed by malicious VPN applications on the Google Play Store, which could compromise user data and privacy. The most supported hypothesis is that cybercriminals are exploiting the demand for free VPN services to deploy spyware and botnets. It is recommended that users be educated on the risks of free VPNs and encouraged to use reputable, paid services. Confidence Level: Moderate.
2. Competing Hypotheses
Hypothesis 1: Malicious actors are deliberately using free VPN applications as a vector to distribute spyware and create botnets, exploiting the high demand for free privacy tools.
Hypothesis 2: The presence of malicious VPNs is primarily due to inadequate vetting processes by app stores, allowing cybercriminals to exploit these gaps unintentionally rather than through a coordinated effort.
Hypothesis 1 is more likely given the strategic advantage for cybercriminals in using VPNs to gain access to devices and the historical precedent of such tactics. Hypothesis 2 is plausible but less supported due to the increasing sophistication of malicious actors targeting privacy tools.
3. Key Assumptions and Red Flags
Assumptions: It is assumed that users are primarily driven by cost considerations when choosing VPN services, leading them to opt for free options. It is also assumed that malicious actors have the capability to effectively disguise spyware within VPN applications.
Red Flags: The rapid emergence of new, unverified VPN apps and the lack of transparency in their operations are significant red flags. The promotion of free VPNs without clear business models is another indicator of potential deception.
4. Implications and Strategic Risks
The proliferation of malicious VPNs could lead to widespread data breaches, loss of personal information, and the creation of large-scale botnets. This poses a risk not only to individual users but also to broader network security. Politically, this could lead to increased regulatory scrutiny on app stores and privacy tools. Economically, it could damage the reputation of legitimate VPN providers.
5. Recommendations and Outlook
- Enhance public awareness campaigns about the risks of free VPNs and promote the use of reputable, paid services.
- Encourage app stores to implement stricter vetting processes for VPN applications.
- Best-case scenario: Increased user education leads to a decline in the use of malicious VPNs.
- Worst-case scenario: Continued exploitation by cybercriminals results in significant data breaches and loss of trust in VPN services.
- Most-likely scenario: A gradual increase in awareness and regulation reduces the prevalence of malicious VPNs over time.
6. Key Individuals and Entities
Daniel Card, Cyber Security Expert and Fellow at BCS Chartered Institute.
Chiara Castro, Multimedia Journalist at TechRadar.
7. Thematic Tags
Cybersecurity
Structured Analytic Techniques Applied
- Adversarial Threat Simulation: Model and simulate actions of cyber adversaries to anticipate vulnerabilities and improve resilience.
- Indicators Development: Detect and monitor behavioral or technical anomalies across systems for early threat detection.
- Bayesian Scenario Modeling: Quantify uncertainty and predict cyberattack pathways using probabilistic inference.
Explore more:
Cybersecurity Briefs ·
Daily Summary ·
Methodology