Dangerous new Linux malware strikes – thousands of users see passwords personal info stolen here’s what we know – TechRadar
Published on: 2025-08-05
Intelligence Report: Dangerous new Linux malware strikes – thousands of users see passwords personal info stolen here’s what we know – TechRadar
1. BLUF (Bottom Line Up Front)
The most supported hypothesis suggests that the PSA Stealer malware is part of a sophisticated cybercriminal operation with potential ties to organized crime networks. This hypothesis is supported by the malware’s advanced features and the geographic distribution of its victims. The recommended action is to enhance international cybersecurity collaboration and improve detection and response capabilities. Confidence Level: Moderate.
2. Competing Hypotheses
Hypothesis 1: The PSA Stealer malware is orchestrated by a Vietnamese-speaking cybercriminal group with ties to organized crime, aiming to sell stolen data on Telegram-based marketplaces. This is supported by the malware’s sophisticated evasion techniques and the specific targeting of high-value data like credit card information and cryptocurrency wallets.
Hypothesis 2: The PSA Stealer is a state-sponsored cyber-espionage tool disguised as a criminal operation to mask its true intent. This hypothesis considers the possibility of a nation-state actor using the malware to gather intelligence under the guise of financial theft, leveraging the malware’s advanced capabilities and widespread impact.
3. Key Assumptions and Red Flags
– Assumption 1: The attribution to Vietnamese-speaking actors is accurate and not a false flag operation.
– Assumption 2: The primary motive is financial gain rather than espionage.
– Red Flag: Lack of direct evidence linking the malware to specific individuals or groups.
– Blind Spot: Limited visibility into the malware’s distribution channels and the full extent of its impact.
4. Implications and Strategic Risks
The PSA Stealer poses significant risks to global cybersecurity, with potential economic impacts due to data breaches and financial theft. The malware’s ability to evade detection suggests a high level of sophistication, raising concerns about future iterations and the potential for more targeted attacks. Geopolitically, if state-sponsored, it could escalate tensions between nations, especially if linked to a nation-state actor.
5. Recommendations and Outlook
- Enhance international cooperation on cybersecurity to share threat intelligence and improve collective defense mechanisms.
- Invest in advanced threat detection technologies to identify and mitigate similar threats in the future.
- Scenario Projections:
- Best Case: Rapid identification and neutralization of the threat, minimizing impact and preventing future attacks.
- Worst Case: Failure to contain the malware leads to widespread data breaches and financial losses, with potential geopolitical fallout if state-sponsored.
- Most Likely: Continued evolution of the malware with periodic successful attacks, necessitating ongoing vigilance and adaptation of defense strategies.
6. Key Individuals and Entities
– SentinelLabs (Security Researcher)
– Beazley Security (Security Researcher)
– Telegram-based marketplaces (Potential data buyers)
7. Thematic Tags
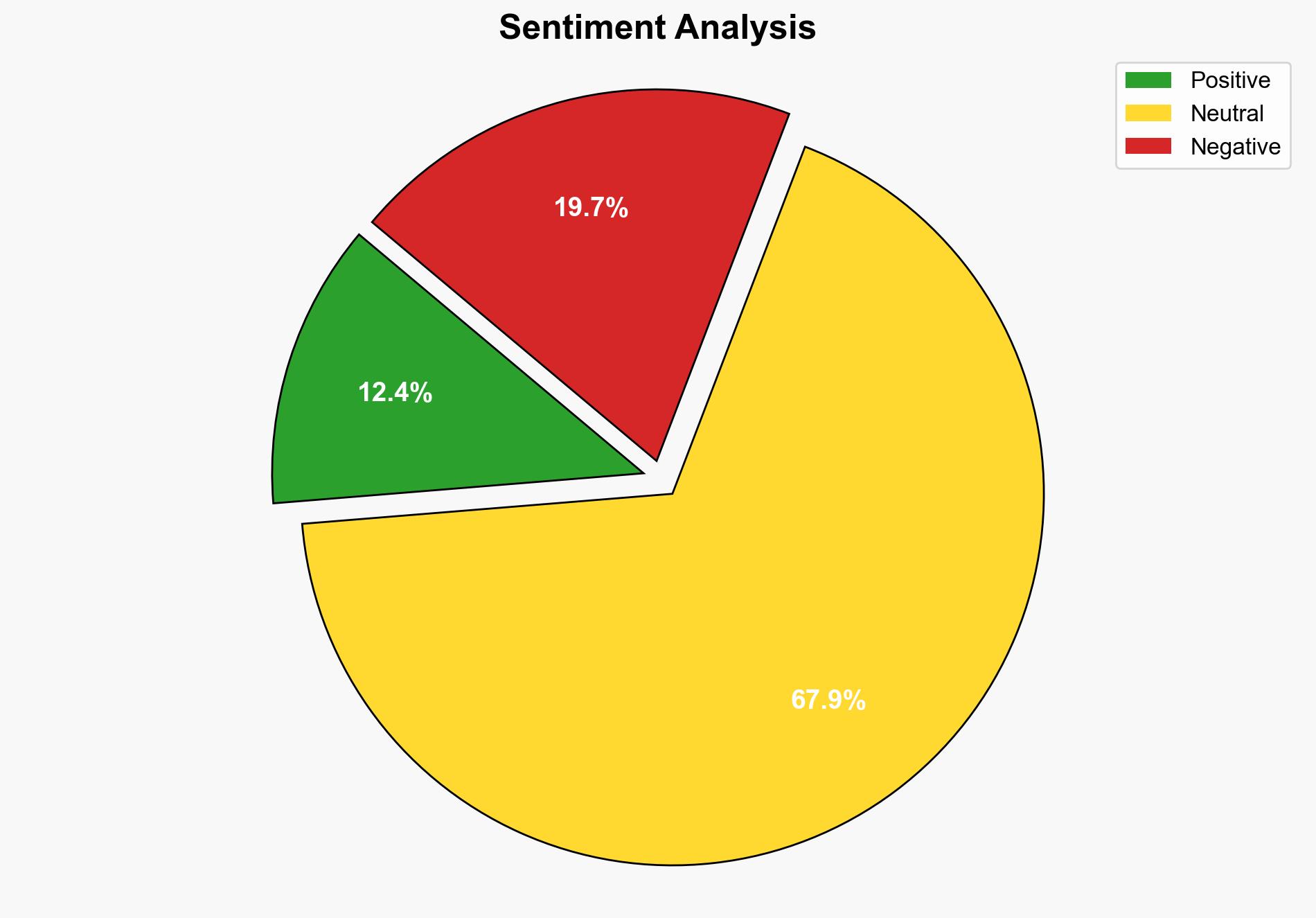
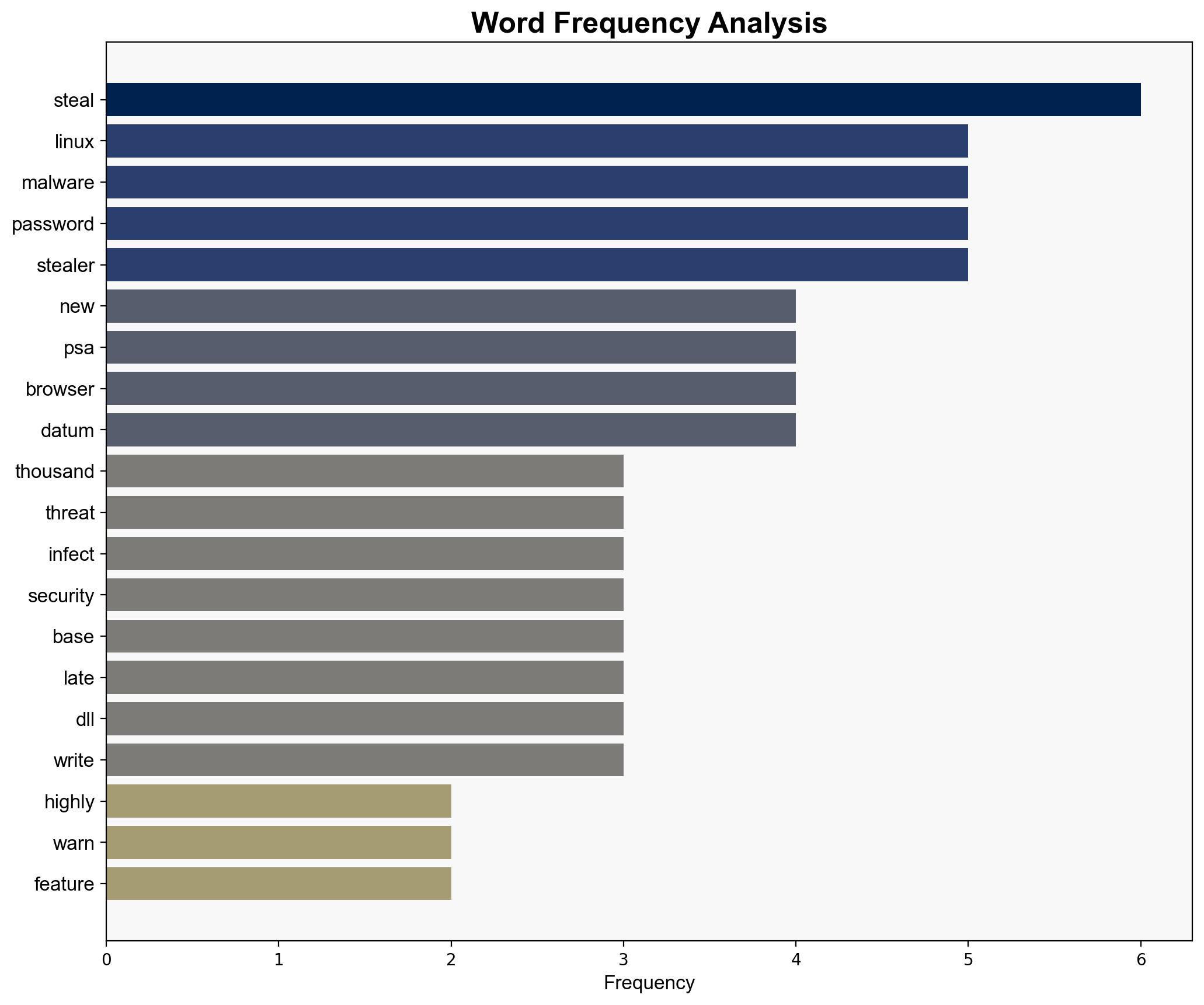
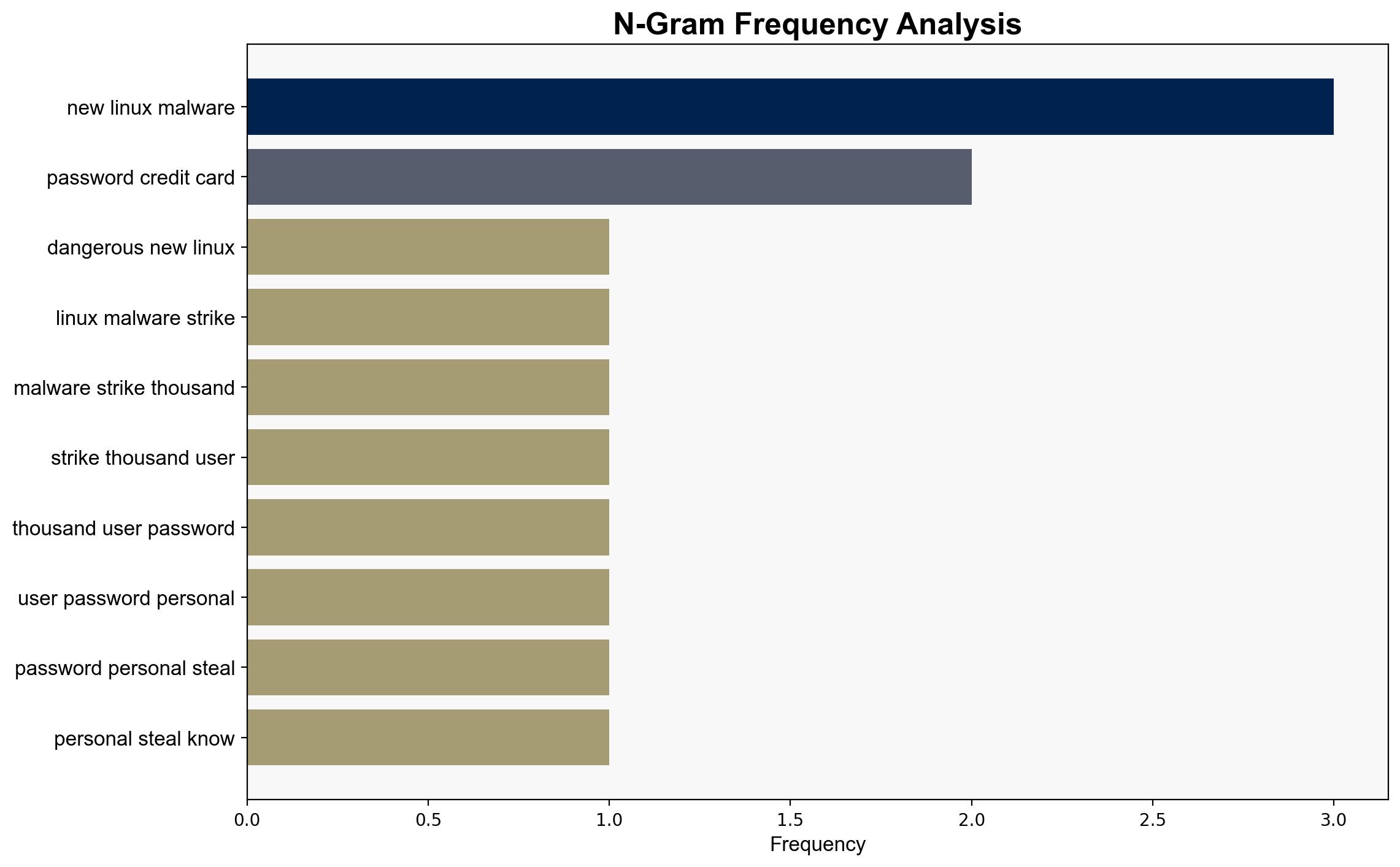
national security threats, cybersecurity, counter-terrorism, regional focus