Daniel Vrit Producing UUIDs Version 7 disguised as Version 4 or 8 – Verite.pro
Published on: 2025-11-05
Intelligence Report: Daniel Vrit Producing UUIDs Version 7 disguised as Version 4 or 8 – Verite.pro
1. BLUF (Bottom Line Up Front)
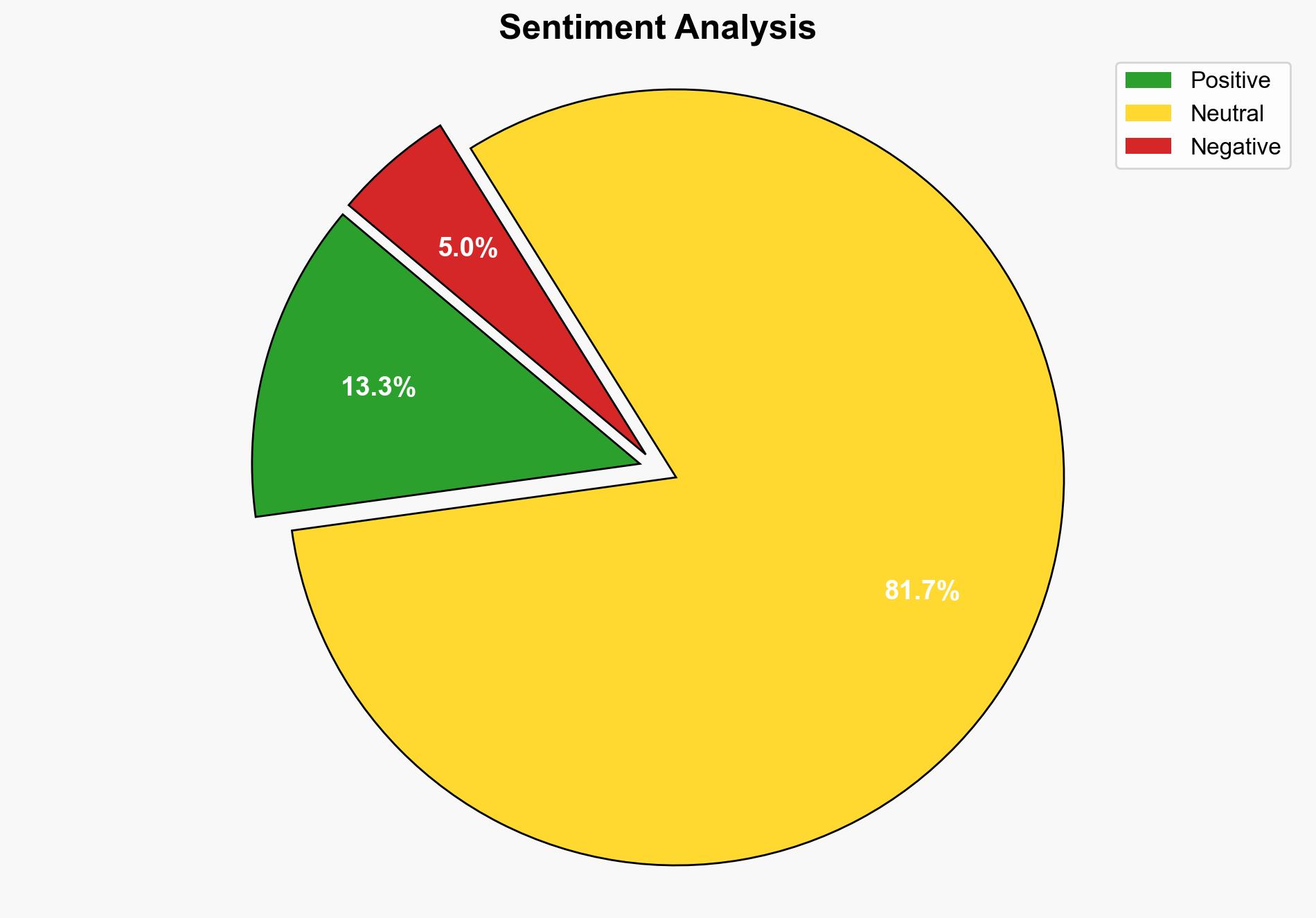
The strategic assessment indicates a moderate confidence level that Daniel Vrit’s UUID manipulation could either be a legitimate technical innovation or a potential cybersecurity risk. The most supported hypothesis suggests a technical advancement aimed at improving database efficiency and security. Recommended action includes monitoring developments and assessing potential cybersecurity implications.
2. Competing Hypotheses
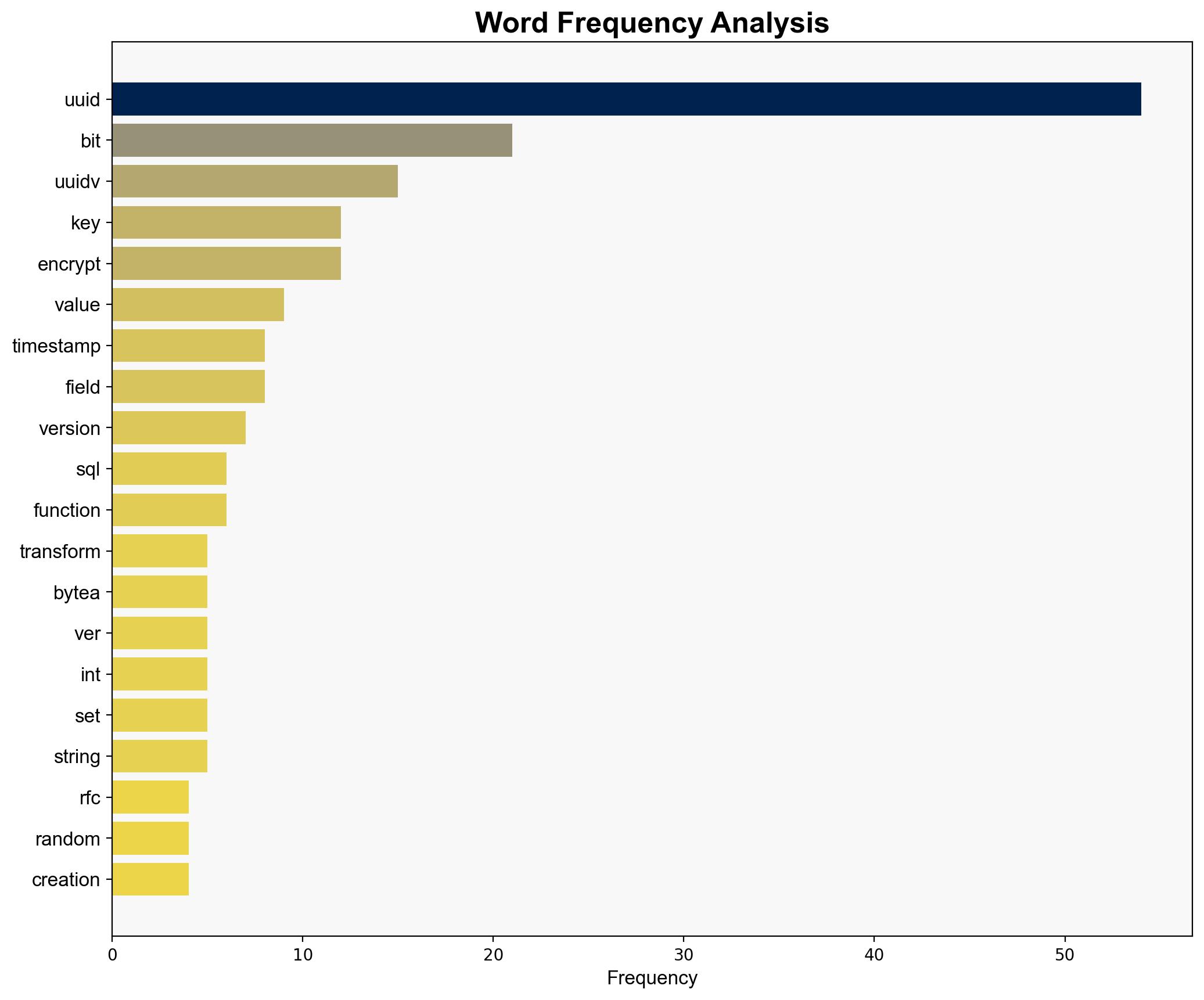
1. **Hypothesis A**: Daniel Vrit is innovating UUID technology to enhance database performance and security by embedding timestamps and encryption, thereby improving sorting and access efficiency.
2. **Hypothesis B**: The UUID manipulation is a deceptive practice aimed at creating vulnerabilities or exploiting existing systems by disguising UUID versions, potentially facilitating unauthorized data access or manipulation.
Using the Analysis of Competing Hypotheses (ACH) 2.0, Hypothesis A is better supported due to the detailed technical description and the focus on efficiency and security improvements. Hypothesis B lacks direct evidence of malicious intent but remains plausible given the potential for misuse.
3. Key Assumptions and Red Flags
– **Assumptions**: It is assumed that the technical descriptions provided are accurate and that the intent is to improve UUID functionality.
– **Red Flags**: The lack of explicit mention of security testing or third-party validation raises concerns about potential vulnerabilities.
– **Blind Spots**: There is limited information on how these UUIDs are being implemented in real-world applications, which could mask potential security issues.
4. Implications and Strategic Risks
– **Cybersecurity Risks**: If UUIDs are improperly secured, they could be exploited to gain unauthorized access to systems or data.
– **Economic Implications**: Improved database efficiency could benefit businesses, but security breaches could lead to financial losses.
– **Geopolitical Risks**: If exploited, this technology could be used in cyber warfare or espionage, impacting national security.
5. Recommendations and Outlook
- Conduct a thorough cybersecurity assessment of the UUID technology to identify potential vulnerabilities.
- Engage with cybersecurity experts to evaluate the implications of widespread adoption.
- Scenario Projections:
- **Best Case**: The technology enhances database operations without security issues, leading to widespread adoption.
- **Worst Case**: Security vulnerabilities are exploited, leading to significant data breaches and loss of trust.
- **Most Likely**: The technology is adopted with caution, and security measures are implemented to mitigate risks.
6. Key Individuals and Entities
– Daniel Vrit
7. Thematic Tags
national security threats, cybersecurity, database technology, encryption, UUID manipulation