Data breach at Canadian Investment Regulatory Organization affects 750,000 individuals in August 2025 incident
Published on: 2026-01-16
AI-powered OSINT brief from verified open sources. Automated NLP signal extraction with human verification. See our Methodology and Why WorldWideWatchers.
Intelligence Report: Data breach at Canadas Investment Watchdog Canadian Investment Regulatory Organization impacts 750000 people
1. BLUF (Bottom Line Up Front)
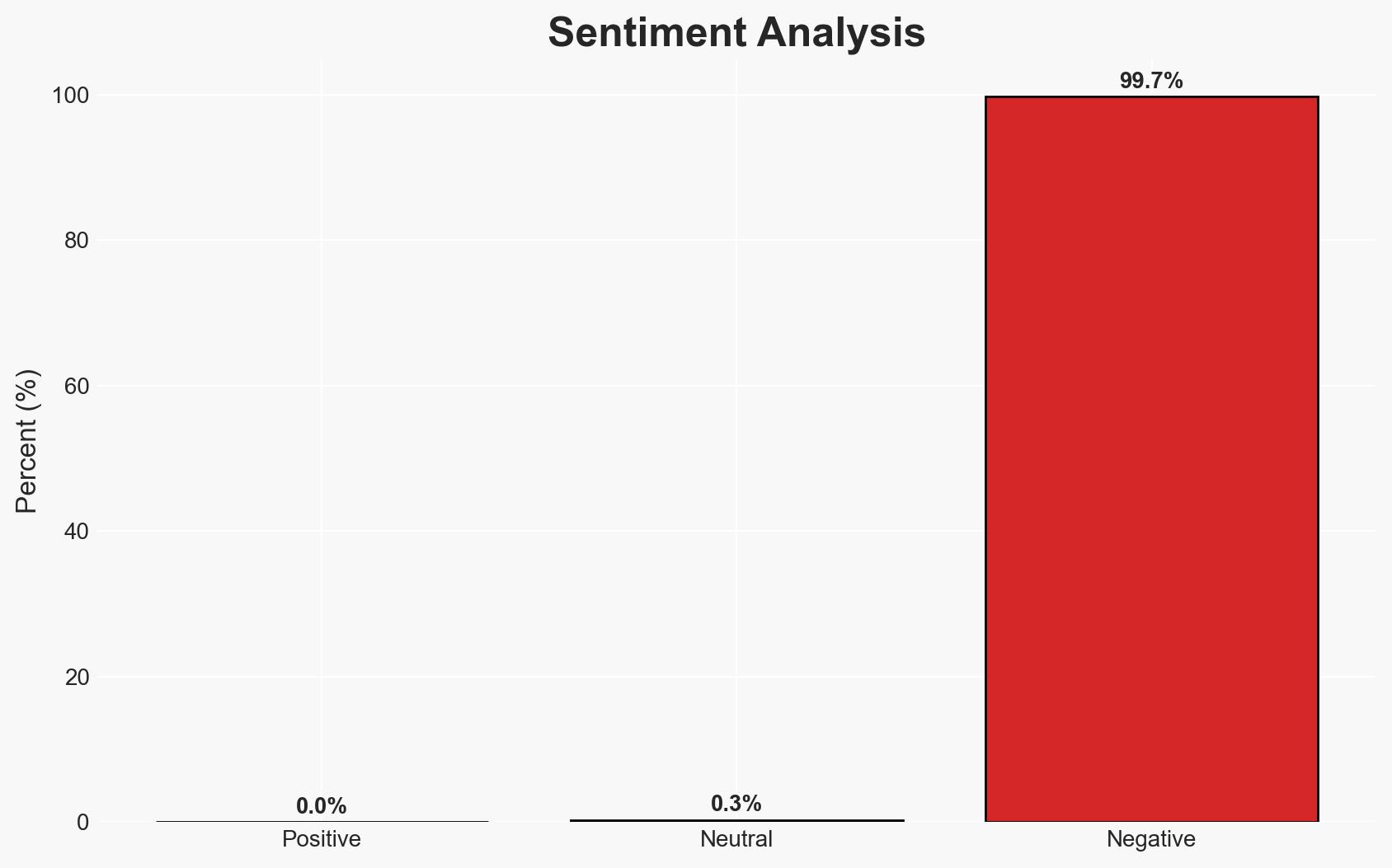
The data breach at the Canadian Investment Regulatory Organization (CIRO) affected approximately 750,000 individuals, exposing sensitive personal and financial data. The breach, attributed to a phishing attack, was contained without disrupting critical operations. The most likely hypothesis is that the breach was opportunistic rather than targeted, with moderate confidence due to limited evidence of ongoing threat or data misuse.
2. Competing Hypotheses
- Hypothesis A: The breach was an opportunistic attack by cybercriminals seeking financial gain. Supporting evidence includes the nature of the phishing attack and the lack of evidence of data misuse or dark web activity. Key uncertainties include the identity and motivations of the threat actors.
- Hypothesis B: The breach was a targeted attack aimed at undermining CIRO’s regulatory functions. This is contradicted by the absence of disruption to critical operations and no evidence of data misuse. However, the copying of investigative data could suggest a more strategic intent.
- Assessment: Hypothesis A is currently better supported due to the opportunistic nature of phishing attacks and the lack of evidence suggesting a targeted campaign. Indicators such as the emergence of data on the dark web or further attacks on CIRO could shift this judgment.
3. Key Assumptions and Red Flags
- Assumptions: CIRO’s containment measures were effective; the breach was not state-sponsored; affected data has not been misused.
- Information Gaps: The identity of the threat actors; the full scope of data copied; potential vulnerabilities in CIRO’s cybersecurity infrastructure.
- Bias & Deception Risks: Possible underreporting by CIRO to minimize reputational damage; reliance on CIRO’s internal assessments without independent verification.
4. Implications and Strategic Risks
This development could lead to increased scrutiny of CIRO’s cybersecurity practices and regulatory oversight. It may also influence broader cybersecurity policies and investor confidence in regulatory bodies.
- Political / Geopolitical: Potential for regulatory reforms or increased government oversight of self-regulatory organizations.
- Security / Counter-Terrorism: Minimal direct impact on counter-terrorism, but highlights vulnerabilities in critical regulatory infrastructure.
- Cyber / Information Space: Potential for increased cyber threats targeting financial regulatory bodies; need for enhanced cybersecurity measures.
- Economic / Social: Possible erosion of trust in financial markets and regulatory bodies, impacting investor behavior and market stability.
5. Recommendations and Outlook
- Immediate Actions (0–30 days): Enhance monitoring for data misuse; conduct a comprehensive cybersecurity audit; engage with affected individuals to mitigate potential identity theft.
- Medium-Term Posture (1–12 months): Develop resilience measures, including staff training and incident response plans; consider partnerships with cybersecurity firms for ongoing threat assessments.
- Scenario Outlook: Best: No further incidents and improved cybersecurity posture. Worst: Data misuse leading to financial fraud and regulatory backlash. Most-Likely: Continued monitoring with no significant misuse detected, leading to gradual restoration of confidence.
6. Key Individuals and Entities
- Canadian Investment Regulatory Organization (CIRO)
- Not clearly identifiable from open sources in this snippet.
7. Thematic Tags
cybersecurity, data breach, financial regulation, phishing attack, identity theft, regulatory oversight, investor protection
Structured Analytic Techniques Applied
- Adversarial Threat Simulation: Model and simulate actions of cyber adversaries to anticipate vulnerabilities and improve resilience.
- Indicators Development: Detect and monitor behavioral or technical anomalies across systems for early threat detection.
- Bayesian Scenario Modeling: Quantify uncertainty and predict cyberattack pathways using probabilistic inference.
Explore more:
Cybersecurity Briefs ·
Daily Summary ·
Support us