Data breach at Central Maine Healthcare affects over 145,000 patients’ personal and medical information
Published on: 2026-01-15
AI-powered OSINT brief from verified open sources. Automated NLP signal extraction with human verification. See our Methodology and Why WorldWideWatchers.
Intelligence Report: Central Maine Healthcare data breach impacted over 145000 patients
1. BLUF (Bottom Line Up Front)
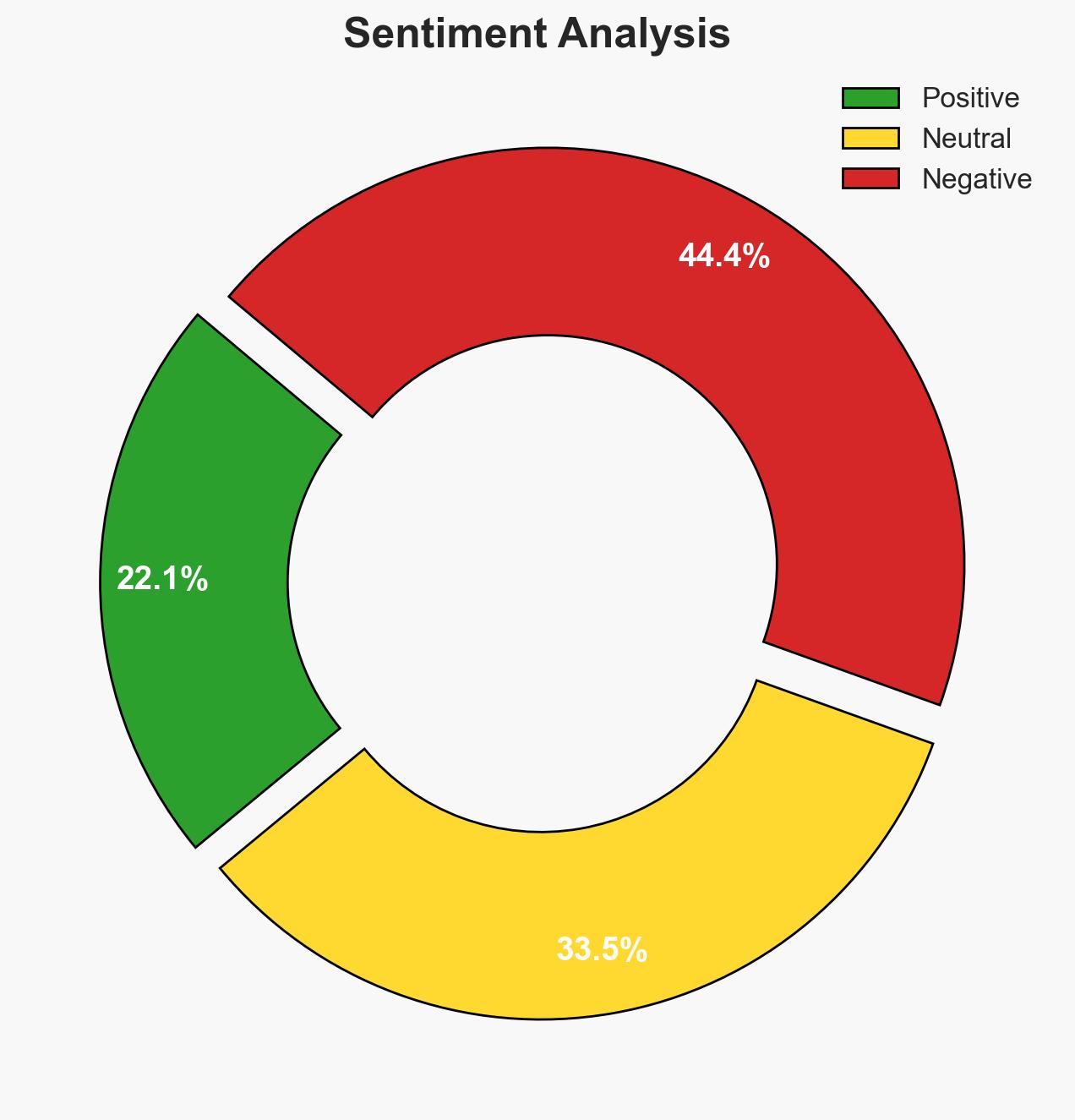
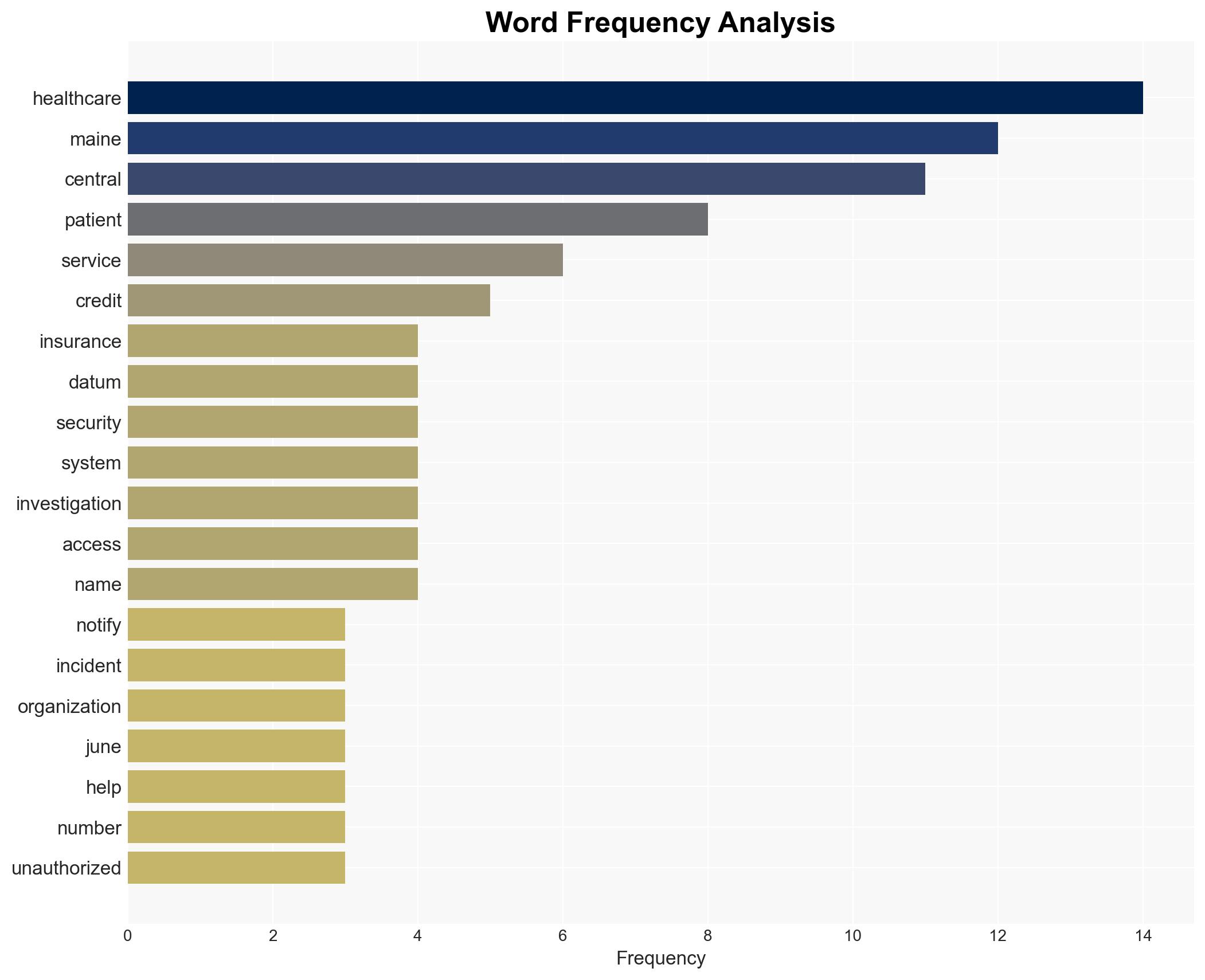
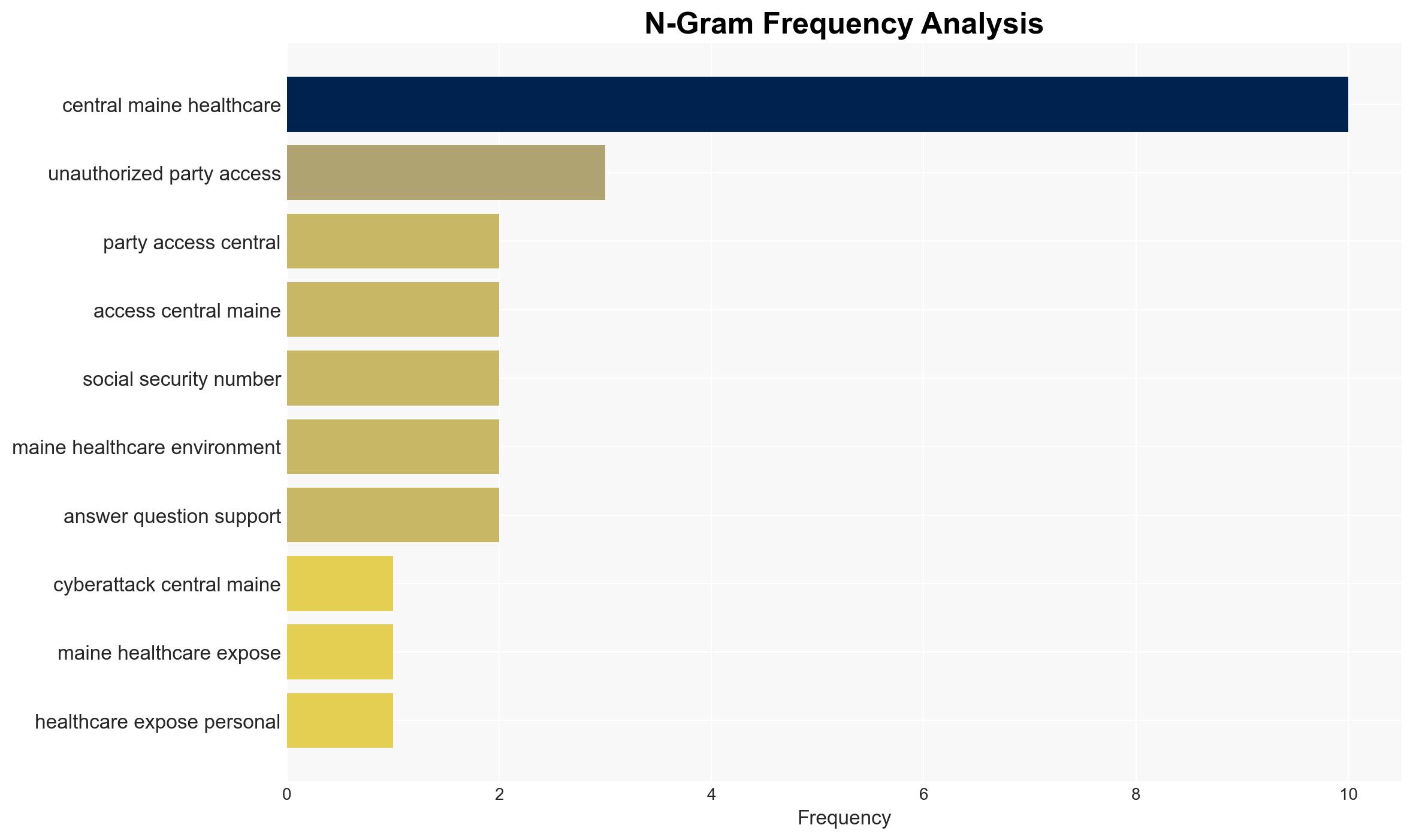
The data breach at Central Maine Healthcare exposed sensitive information of approximately 145,000 patients, posing significant risks to personal data security and privacy. The breach, occurring between March and June 2025, highlights vulnerabilities in healthcare IT systems. The most likely hypothesis is that the breach resulted from a targeted cyberattack exploiting these vulnerabilities. Overall confidence in this assessment is moderate due to incomplete information on the attacker’s identity and methods.
2. Competing Hypotheses
- Hypothesis A: The breach was a targeted cyberattack by a sophisticated actor exploiting specific vulnerabilities in Central Maine Healthcare’s IT systems. Supporting evidence includes the extended period of unauthorized access and the sensitive nature of the data accessed. Key uncertainties include the identity and motives of the attacker.
- Hypothesis B: The breach resulted from an internal security lapse or accidental exposure, rather than a deliberate external attack. This is less supported due to the duration of unauthorized access and the specific targeting of sensitive data.
- Assessment: Hypothesis A is currently better supported due to the nature and scope of the breach, indicating a deliberate and potentially sophisticated attack. Indicators that could shift this judgment include new evidence of internal malfeasance or accidental data exposure.
3. Key Assumptions and Red Flags
- Assumptions: The breach was conducted by an external actor; Central Maine Healthcare’s IT systems had exploitable vulnerabilities; the data accessed is of high value to the attacker.
- Information Gaps: Lack of detailed information on the attacker’s identity, methods, and specific vulnerabilities exploited.
- Bias & Deception Risks: Potential bias in reporting from Central Maine Healthcare to minimize perceived negligence; risk of deception if the attacker is attempting to mislead attribution efforts.
4. Implications and Strategic Risks
This breach could lead to increased scrutiny of healthcare IT security practices and potentially influence regulatory changes. The exposure of sensitive patient data may result in identity theft and financial fraud, impacting patient trust and organizational reputation.
- Political / Geopolitical: Potential for regulatory changes in healthcare data protection laws.
- Security / Counter-Terrorism: Increased risk of similar attacks on healthcare systems, requiring enhanced security measures.
- Cyber / Information Space: Highlights vulnerabilities in healthcare IT infrastructure, possibly encouraging further cyberattacks.
- Economic / Social: Potential financial losses for affected individuals and increased costs for healthcare providers to enhance security.
5. Recommendations and Outlook
- Immediate Actions (0–30 days): Conduct a comprehensive security audit of Central Maine Healthcare’s IT systems; enhance monitoring for suspicious activities; engage with law enforcement and cybersecurity experts for further investigation.
- Medium-Term Posture (1–12 months): Develop and implement robust cybersecurity policies; invest in staff training and awareness programs; establish partnerships with cybersecurity firms for ongoing support.
- Scenario Outlook:
- Best: Rapid identification and mitigation of vulnerabilities, leading to improved security posture.
- Worst: Further breaches occur, leading to significant financial and reputational damage.
- Most-Likely: Incremental improvements in security with occasional minor breaches as systems are fortified.
6. Key Individuals and Entities
- Central Maine Healthcare
- Cyberscout (a TransUnion company)
- Maine Attorney General’s Office
- Not clearly identifiable from open sources in this snippet.
7. Thematic Tags
cybersecurity, data breach, healthcare IT, identity theft, regulatory compliance, information security, patient privacy
Structured Analytic Techniques Applied
- Adversarial Threat Simulation: Model and simulate actions of cyber adversaries to anticipate vulnerabilities and improve resilience.
- Indicators Development: Detect and monitor behavioral or technical anomalies across systems for early threat detection.
- Bayesian Scenario Modeling: Quantify uncertainty and predict cyberattack pathways using probabilistic inference.
Explore more:
Cybersecurity Briefs ·
Daily Summary ·
Support us