DeadLock Ransomware Group Employs Blockchain Smart Contracts for Enhanced Operational Stealth
Published on: 2026-01-14
AI-powered OSINT brief from verified open sources. Automated NLP signal extraction with human verification. See our Methodology and Why WorldWideWatchers.
Intelligence Report: ‘Imagination the limit’ DeadLock ransomware gang using smart contracts to hide their work
1. BLUF (Bottom Line Up Front)
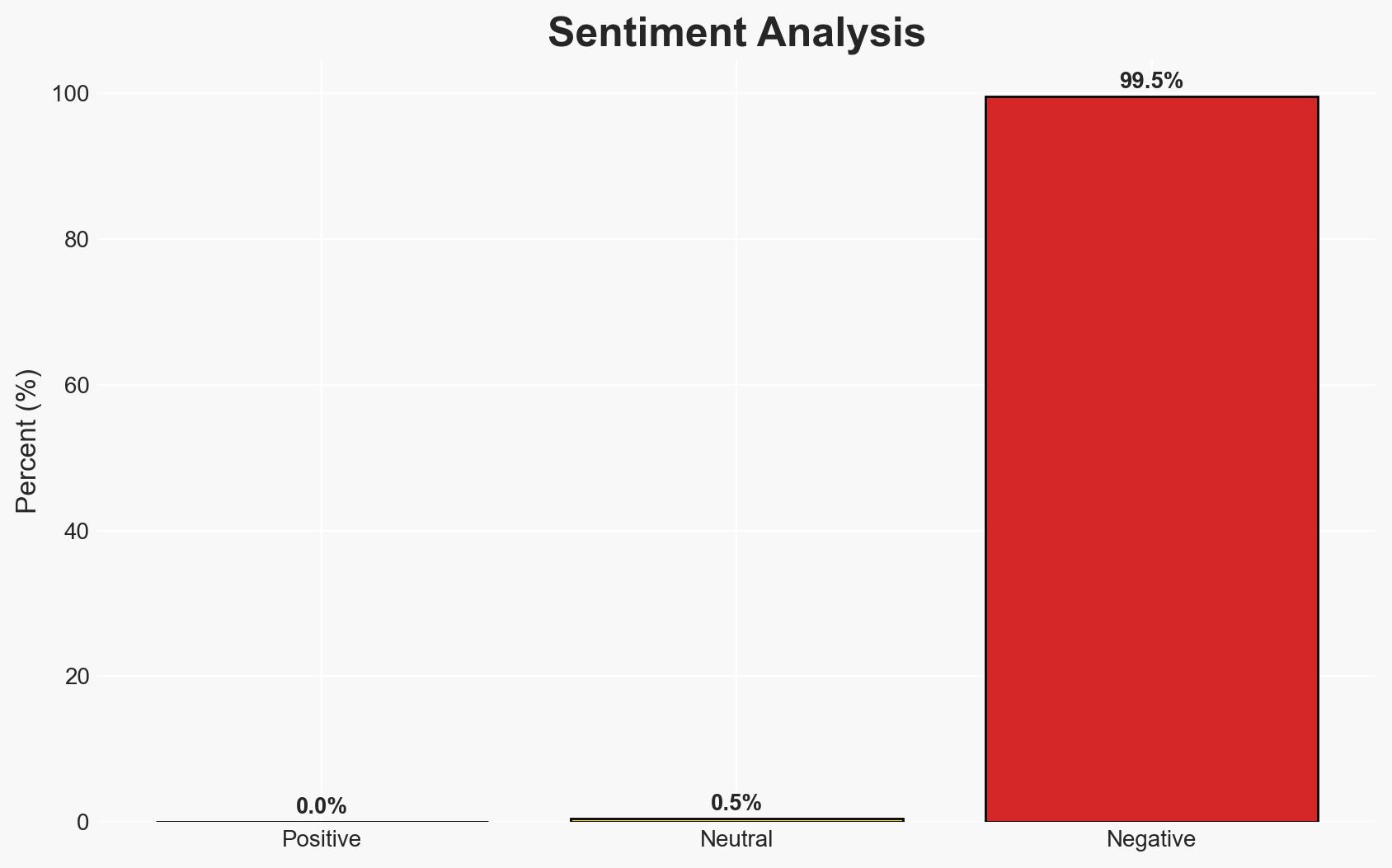
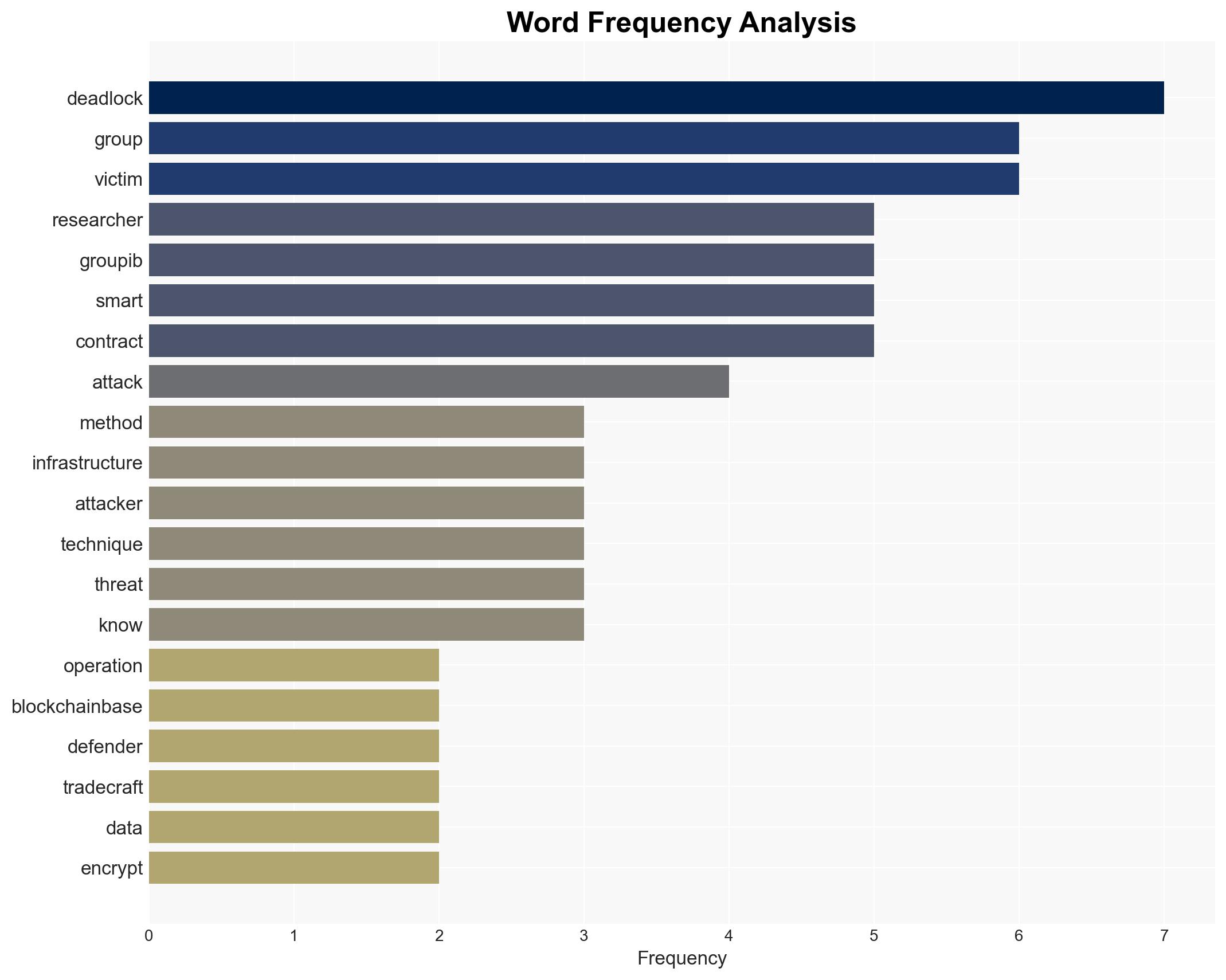
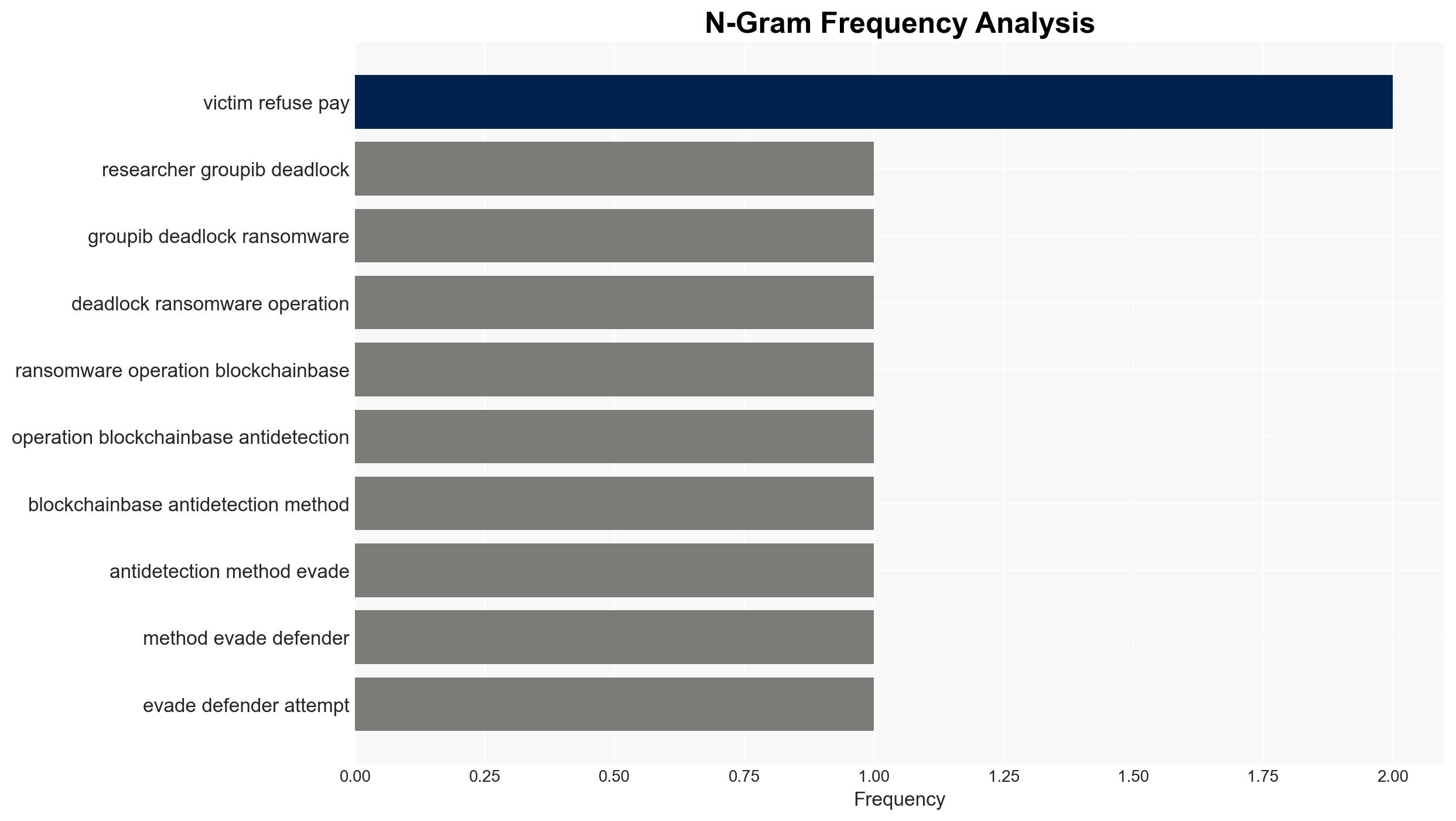
The DeadLock ransomware group is employing blockchain-based smart contracts to obscure its command-and-control infrastructure, complicating detection and mitigation efforts. This novel approach, which leverages Polygon smart contracts, poses a significant challenge to cybersecurity defenses. The group’s tactics, including the absence of a data leak site, suggest a strategic shift in ransomware operations. Overall, the confidence level in this assessment is moderate due to existing information gaps regarding their initial access methods.
2. Competing Hypotheses
- Hypothesis A: DeadLock’s use of smart contracts is primarily a technical innovation aimed at enhancing operational security and evading detection. This is supported by their sophisticated use of blockchain technology and the absence of a data leak site. However, the lack of detailed information on their access methods creates uncertainty.
- Hypothesis B: The adoption of smart contracts by DeadLock is a strategic deception to mislead cybersecurity efforts and possibly mask a more conventional ransomware operation. This hypothesis is less supported due to the lack of evidence suggesting deliberate misinformation or deception.
- Assessment: Hypothesis A is currently better supported due to the observed technical sophistication and the alignment with broader trends in ransomware evolution. Indicators that could shift this judgment include new intelligence on their access techniques or evidence of deliberate misinformation.
3. Key Assumptions and Red Flags
- Assumptions: DeadLock’s primary goal is financial gain; smart contracts are used to enhance operational security; the absence of a data leak site is a strategic choice.
- Information Gaps: Specific methods of initial network access; detailed motivations behind the absence of a data leak site; potential state sponsorship or affiliations.
- Bias & Deception Risks: Potential over-reliance on technical sophistication as an indicator of threat level; source bias from cybersecurity firms with vested interests; possible misinterpretation of blockchain use as purely defensive.
4. Implications and Strategic Risks
The use of smart contracts by ransomware groups like DeadLock could signal a shift in cybercriminal tactics, potentially leading to increased difficulty in tracking and neutralizing such threats.
- Political / Geopolitical: Potential for increased tension between states if state-sponsored actors adopt similar techniques.
- Security / Counter-Terrorism: Enhanced threat landscape complexity, requiring adaptation in defensive strategies.
- Cyber / Information Space: Evolution of ransomware tactics could lead to broader adoption of blockchain technologies in cybercrime.
- Economic / Social: Increased financial risk for organizations, potentially impacting economic stability and public trust in digital systems.
5. Recommendations and Outlook
- Immediate Actions (0–30 days): Enhance monitoring of blockchain transactions; develop detection capabilities for smart contract-based C2 infrastructure.
- Medium-Term Posture (1–12 months): Invest in blockchain analysis tools; foster partnerships with cybersecurity firms specializing in blockchain threats.
- Scenario Outlook:
- Best: Effective countermeasures are developed, reducing the threat from smart contract-based ransomware.
- Worst: Widespread adoption of these techniques leads to a surge in successful ransomware attacks.
- Most-Likely: Gradual increase in smart contract use, necessitating ongoing adaptation of defensive measures.
6. Key Individuals and Entities
- DeadLock ransomware group
- Group-IB (Cybersecurity firm)
- Xabier Eizaguirre (Threat Intelligence Analyst, Group-IB)
- Google Threat Intelligence Group (GTIG)
- North Korean state-sponsored attackers (as a comparative reference)
7. Thematic Tags
cybersecurity, ransomware, blockchain, smart contracts, cyber defense, cybersecurity innovation, threat intelligence, cybercrime evolution
Structured Analytic Techniques Applied
- Adversarial Threat Simulation: Model and simulate actions of cyber adversaries to anticipate vulnerabilities and improve resilience.
- Indicators Development: Detect and monitor behavioral or technical anomalies across systems for early threat detection.
- Bayesian Scenario Modeling: Quantify uncertainty and predict cyberattack pathways using probabilistic inference.
- Network Influence Mapping: Map influence relationships to assess actor impact.
Explore more:
Cybersecurity Briefs ·
Daily Summary ·
Support us