DEFCON AI Cyber Challenge Winners Revealed in DARPAs 4M Cybersecurity Showdown – Infosecurity Magazine
Published on: 2025-08-09
Intelligence Report: DEFCON AI Cyber Challenge Winners Revealed in DARPAs 4M Cybersecurity Showdown – Infosecurity Magazine
1. BLUF (Bottom Line Up Front)
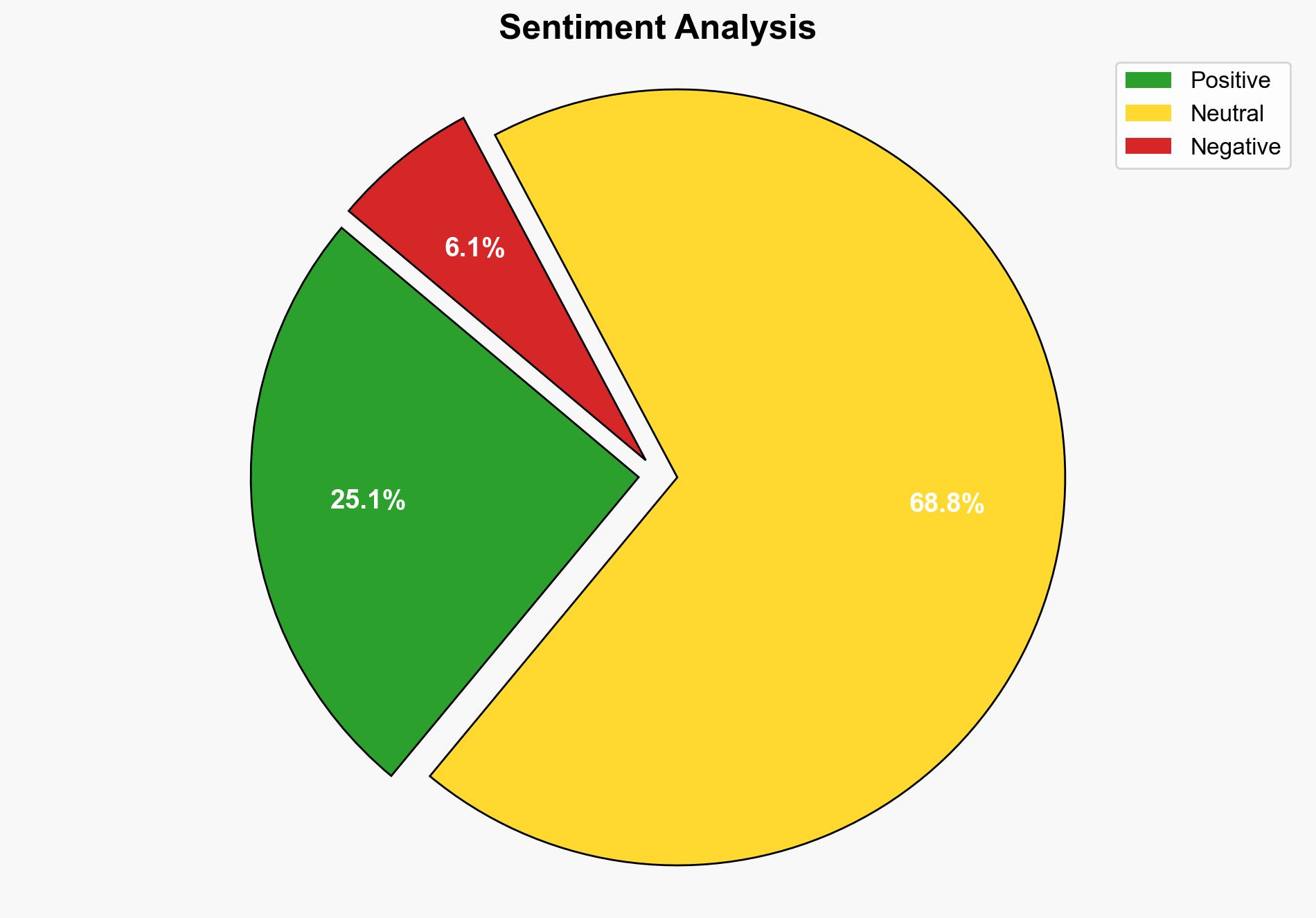
The DEFCON AI Cyber Challenge highlighted significant advancements in AI-powered cybersecurity tools, with the winning teams demonstrating capabilities that could revolutionize vulnerability detection and patching. The most supported hypothesis is that these tools will enhance national cybersecurity infrastructure, reducing the time to detect and patch vulnerabilities. Confidence Level: High. Recommended action is to expedite integration of these AI tools into critical infrastructure cybersecurity protocols.
2. Competing Hypotheses
Hypothesis 1: The AI-powered cybersecurity tools developed during the DEFCON challenge will significantly improve the speed and efficiency of vulnerability detection and patching in critical infrastructure, enhancing national security.
Hypothesis 2: Despite the advancements, the AI tools may face challenges in real-world deployment due to integration issues, resistance from existing cybersecurity frameworks, or unforeseen vulnerabilities within the AI models themselves.
Using ACH 2.0, Hypothesis 1 is better supported by the evidence of significant improvements in detection and patching times during the competition, as well as the backing of major tech companies ensuring computational resources.
3. Key Assumptions and Red Flags
Assumptions for Hypothesis 1 include the seamless integration of AI tools into existing systems and the continued support from tech giants. For Hypothesis 2, assumptions involve potential resistance from cybersecurity professionals and unforeseen technical challenges. Red flags include the lack of detailed information on real-world deployment tests and the absence of data on long-term effectiveness.
4. Implications and Strategic Risks
The successful deployment of these AI tools could set a new standard in cybersecurity, potentially reducing the risk of cyberattacks on critical infrastructure. However, failure to integrate these tools effectively could lead to vulnerabilities being exploited, undermining trust in AI solutions. Geopolitically, this advancement could shift the balance of cyber capabilities, prompting adversaries to accelerate their own AI developments.
5. Recommendations and Outlook
- Conduct pilot programs to test AI tools in controlled real-world environments to identify integration challenges.
- Develop training programs for cybersecurity professionals to adapt to AI-enhanced systems.
- Scenario Projections:
- Best Case: Seamless integration leads to a 50% reduction in vulnerability patching times across critical sectors.
- Worst Case: Integration issues lead to new vulnerabilities, causing a major cyber incident.
- Most Likely: Gradual adoption with incremental improvements in cybersecurity efficiency.
6. Key Individuals and Entities
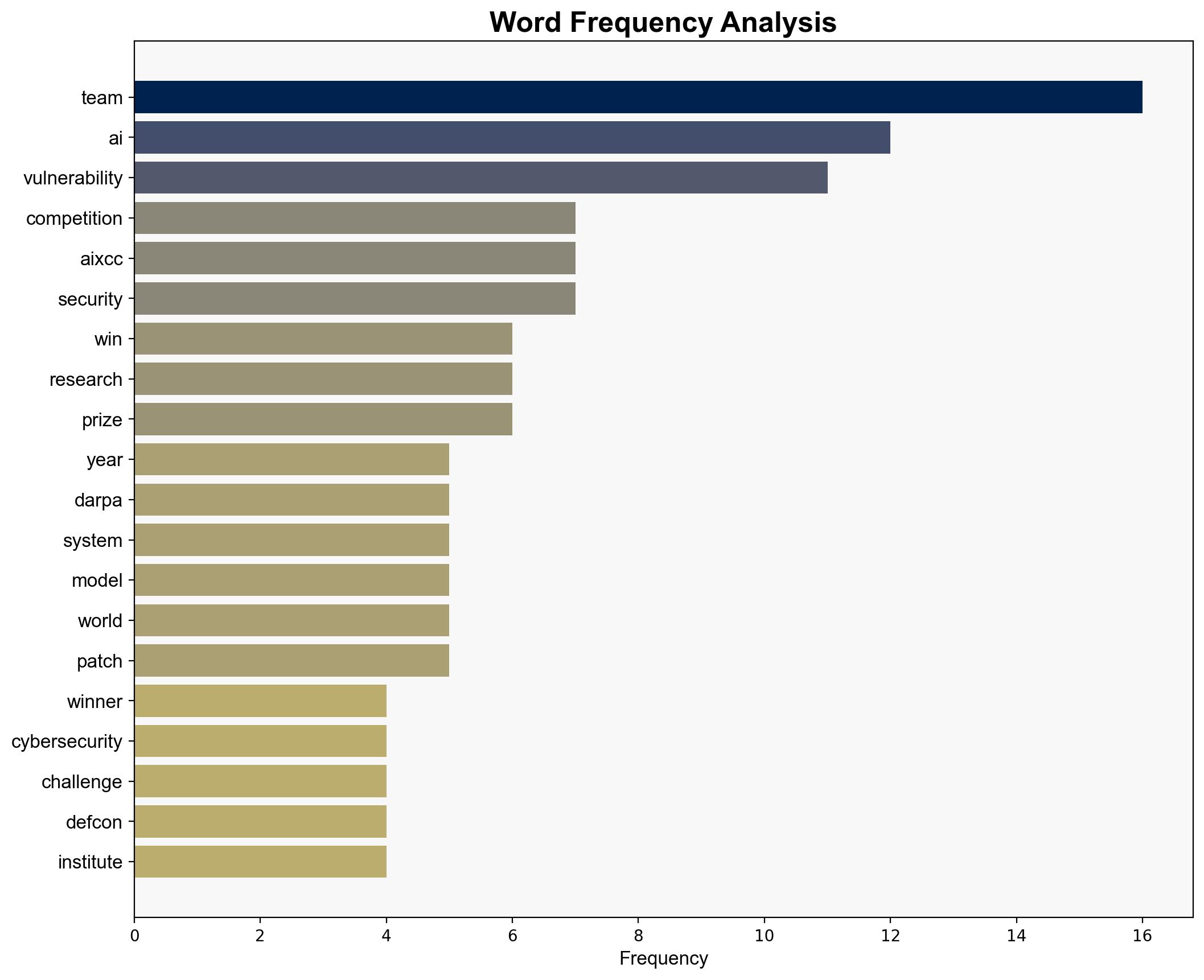
Jim O’Neill, Andrew Carney, Stephen Winchell, Georgia Institute of Technology, Samsung Research, Korea Advanced Institute of Science and Technology, Pohang University of Science and Technology, Trail of Bits, Theori Group.
7. Thematic Tags
national security threats, cybersecurity, counter-terrorism, regional focus