Denmark accuses Russia of cyberattacks targeting critical infrastructure amid ongoing hybrid warfare efforts
Published on: 2025-12-19
AI-powered OSINT brief from verified open sources. Automated NLP signal extraction with human verification. See our Methodology and Why WorldWideWatchers.
Intelligence Report: Denmark blames Russia for destructive cyberattack on water utility
1. BLUF (Bottom Line Up Front)
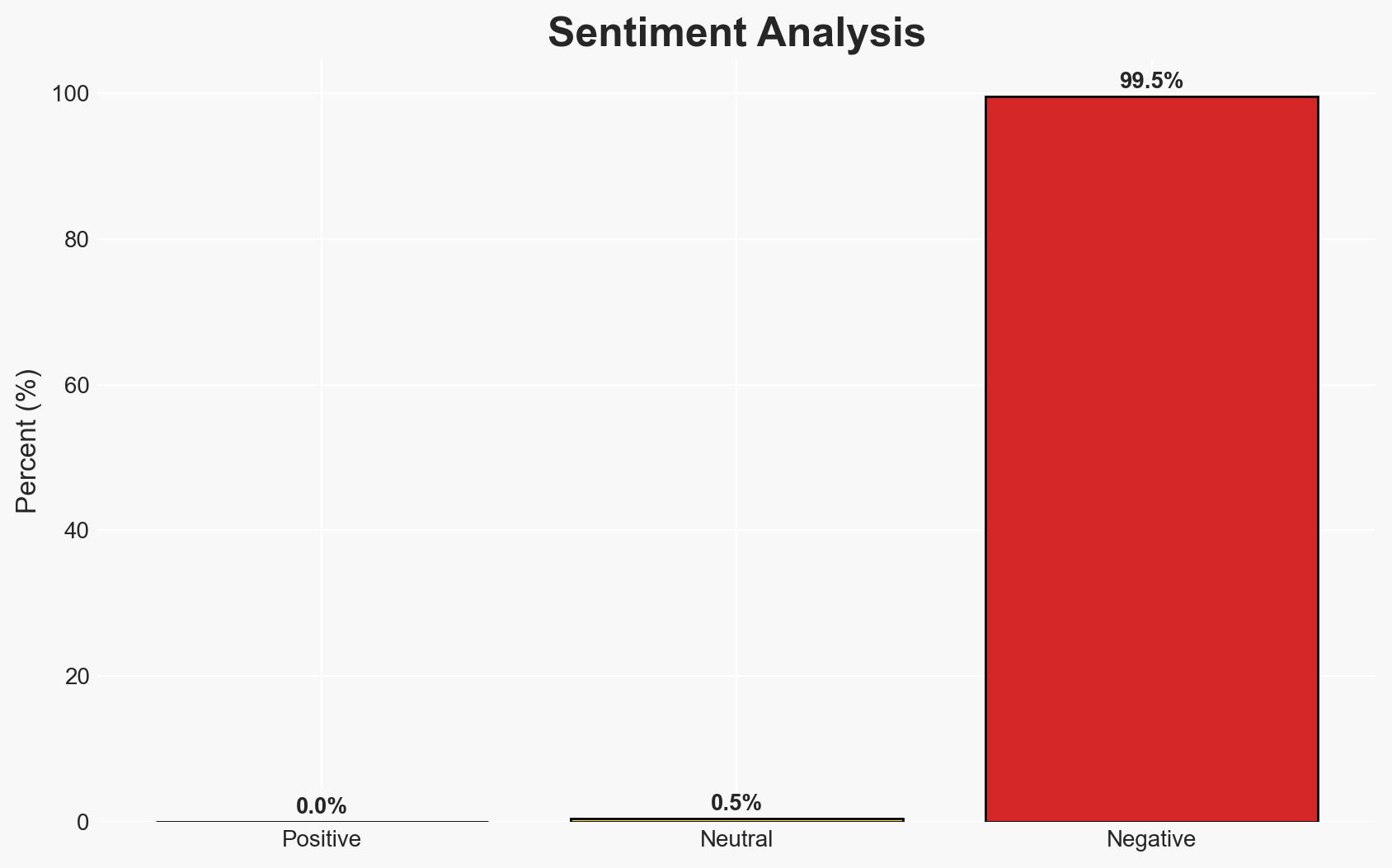
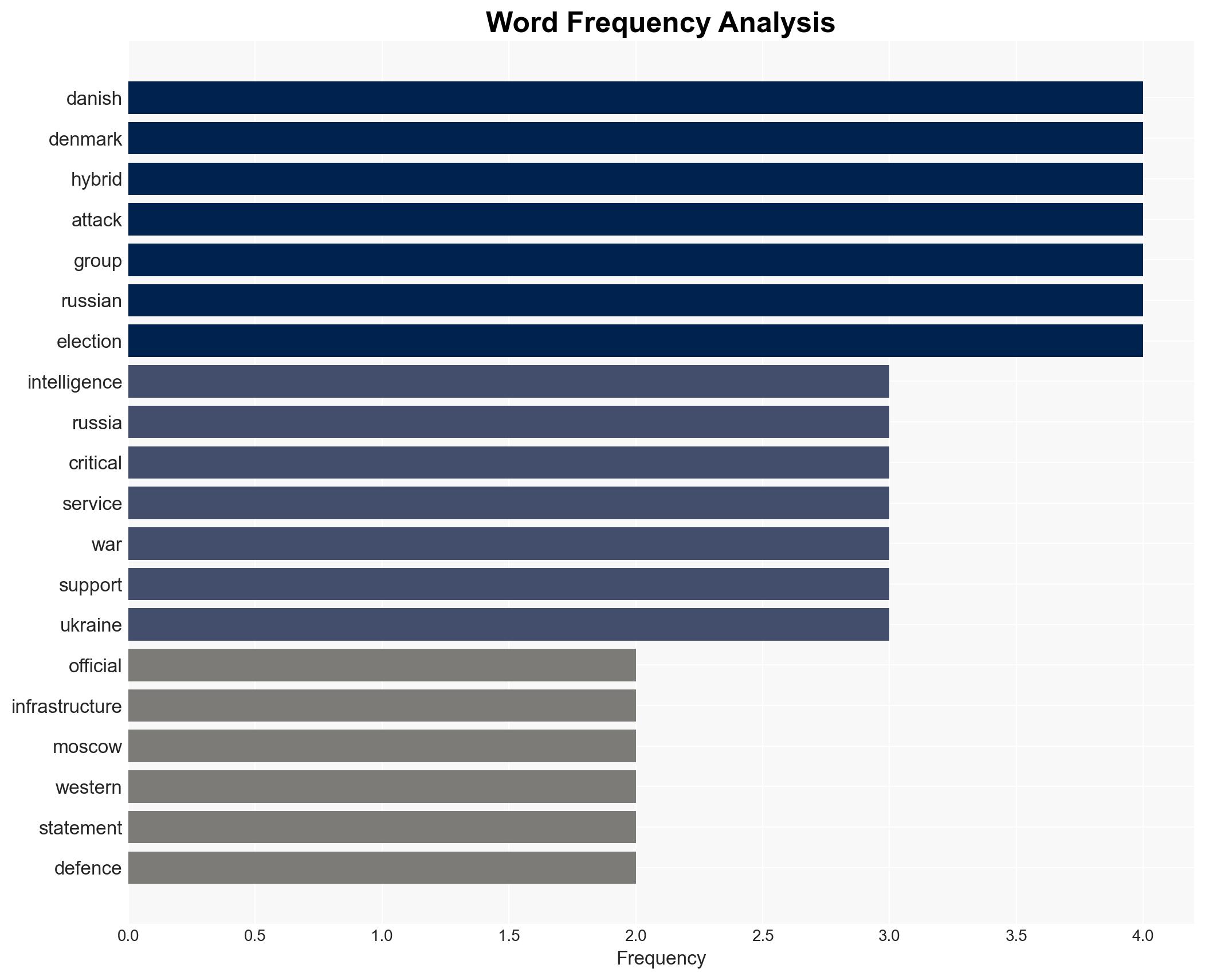
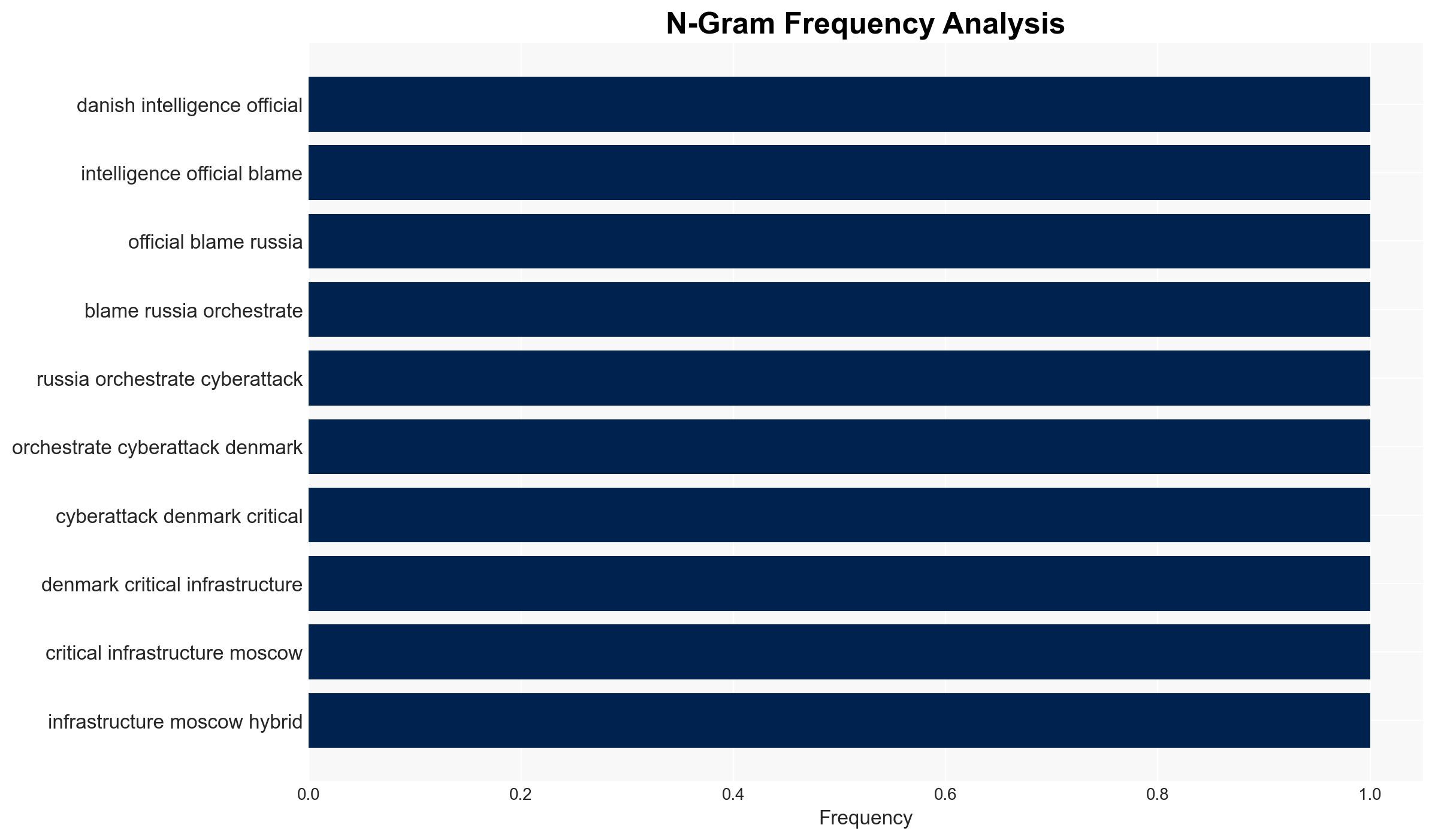
The Danish Defence Intelligence Service (DDIS) has attributed recent cyberattacks on Denmark’s critical infrastructure to Russian state-sponsored groups, Z-Pentest and NoName057(16). These actions are part of Russia’s broader hybrid warfare strategy against Western nations, aimed at undermining support for Ukraine. The evidence supports the hypothesis that Russia is actively engaging in cyber operations to destabilize European political processes. Overall confidence in this assessment is moderate, given the potential for information manipulation and the complexity of attribution in cyber operations.
2. Competing Hypotheses
- Hypothesis A: Russia is directly orchestrating cyberattacks on Denmark’s critical infrastructure as part of a coordinated hybrid warfare strategy. This is supported by DDIS’s attribution of the attacks to Russian state-linked groups and the alignment with Russia’s geopolitical objectives. Key uncertainties include the potential for misattribution and the true extent of state control over these groups.
- Hypothesis B: The cyberattacks are the work of independent pro-Russian hacktivist groups acting autonomously, without direct state orchestration. This is contradicted by the DDIS’s assertion of state involvement and the strategic alignment of the attacks with Russian geopolitical goals.
- Assessment: Hypothesis A is currently better supported due to the direct attribution by Danish intelligence and the strategic context of the attacks. Indicators that could shift this judgment include credible evidence of independent hacktivist activity or new intelligence suggesting limited state control.
3. Key Assumptions and Red Flags
- Assumptions: The Russian state has control over Z-Pentest and NoName057(16); Denmark’s critical infrastructure is a strategic target for Russia; Russia seeks to undermine Western support for Ukraine.
- Information Gaps: Detailed technical evidence linking the cyberattacks to Russian state actors; the extent of coordination between Russian intelligence and the identified groups.
- Bias & Deception Risks: Potential confirmation bias in intelligence assessments; risk of Russian disinformation campaigns to obscure true attribution.
4. Implications and Strategic Risks
This development could escalate tensions between Russia and Western nations, potentially leading to increased cyber defense measures and diplomatic confrontations. It may also influence public perception and political stability in affected countries.
- Political / Geopolitical: Increased diplomatic strain between Russia and Denmark; potential for broader EU or NATO involvement in response measures.
- Security / Counter-Terrorism: Heightened alert levels for critical infrastructure protection; potential for retaliatory cyber operations.
- Cyber / Information Space: Increased focus on cyber defense capabilities; potential for further Russian cyber operations targeting other Western nations.
- Economic / Social: Potential economic impacts from disrupted services; increased public concern over cyber vulnerabilities.
5. Recommendations and Outlook
- Immediate Actions (0–30 days): Enhance monitoring of critical infrastructure networks; engage in diplomatic dialogues with Russia; increase public awareness of cyber threats.
- Medium-Term Posture (1–12 months): Develop resilience measures for critical infrastructure; strengthen international cyber cooperation; invest in cybersecurity capabilities.
- Scenario Outlook:
- Best: Diplomatic resolutions lead to de-escalation and improved cyber defenses.
- Worst: Escalation of cyberattacks results in significant infrastructure damage and geopolitical conflict.
- Most-Likely: Continued low-level cyber operations with periodic diplomatic tensions.
6. Key Individuals and Entities
- Danish Defence Intelligence Service (DDIS)
- Z-Pentest
- NoName057(16)
- Troels Lund Poulsen, Danish Defence Minister
- Russian state actors (not clearly identifiable from open sources in this snippet)
7. Thematic Tags
cybersecurity, hybrid warfare, critical infrastructure, Russia-West relations, cyber defense, geopolitical tensions, influence operations
Structured Analytic Techniques Applied
- Adversarial Threat Simulation: Model and simulate actions of cyber adversaries to anticipate vulnerabilities and improve resilience.
- Indicators Development: Detect and monitor behavioral or technical anomalies across systems for early threat detection.
- Bayesian Scenario Modeling: Quantify uncertainty and predict cyberattack pathways using probabilistic inference.
- Narrative Pattern Analysis: Deconstruct and track propaganda or influence narratives.
Explore more:
Cybersecurity Briefs ·
Daily Summary ·
Support us