Dentsus US subsidiary Merkle hit by cyberattack staff and client data exposed – Securityaffairs.com
Published on: 2025-10-30
Intelligence Report: Dentsus US subsidiary Merkle hit by cyberattack staff and client data exposed – Securityaffairs.com
1. BLUF (Bottom Line Up Front)
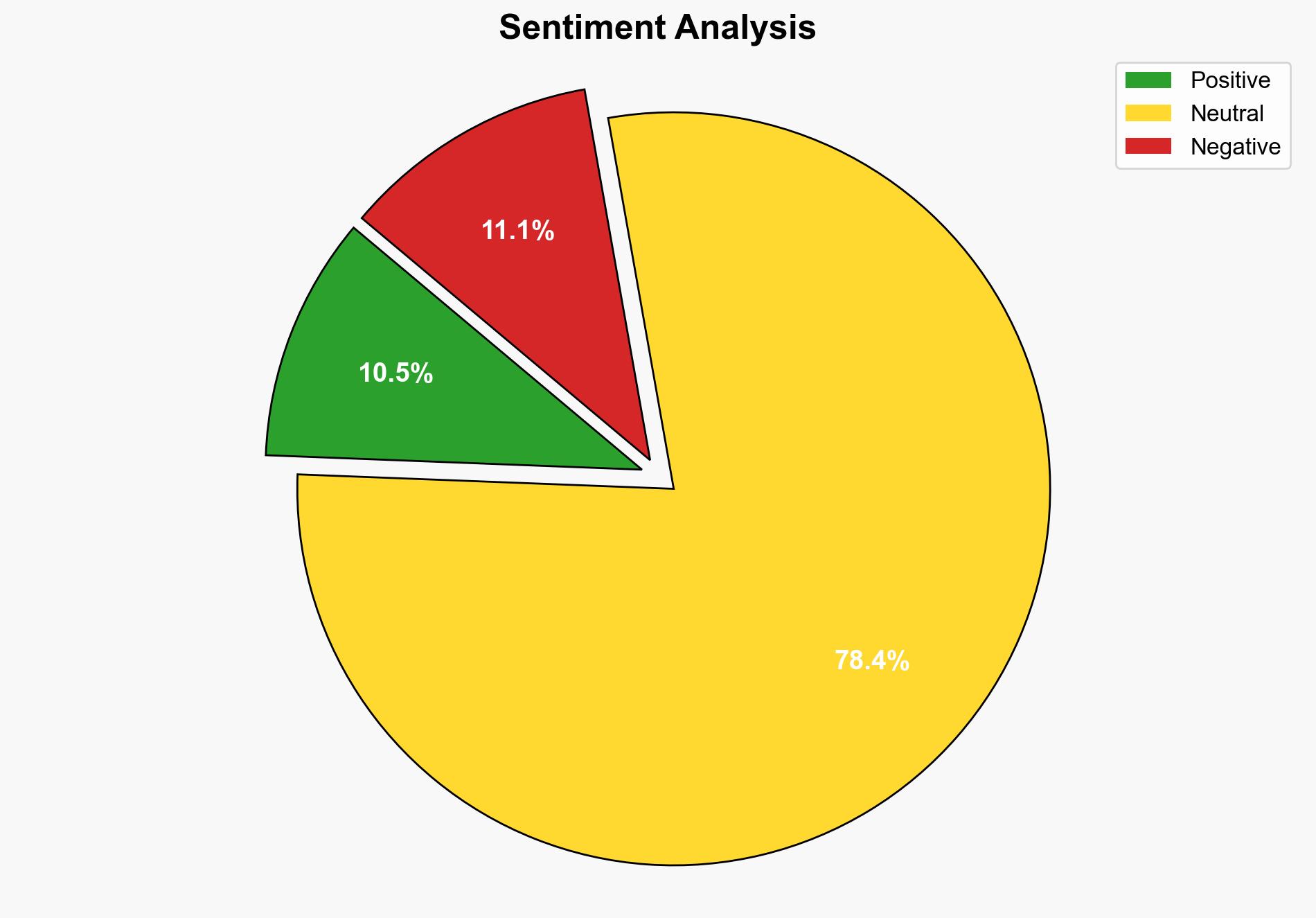
The cyberattack on Merkle, a subsidiary of Dentsu, has exposed sensitive data, including personal and payroll information. The most supported hypothesis is that the attack was financially motivated, potentially involving a ransomware group, although no group has claimed responsibility yet. Confidence level: Moderate. Recommended action: Enhance cybersecurity measures and conduct a thorough forensic investigation to identify vulnerabilities and prevent future breaches.
2. Competing Hypotheses
1. **Financially Motivated Attack**: The attack was orchestrated by cybercriminals aiming to extort money from Dentsu by threatening to release or sell sensitive data.
2. **State-Sponsored Espionage**: The attack was carried out by a state actor seeking to gather intelligence on Dentsu’s operations and clients for strategic advantage.
Using Bayesian Scenario Modeling, the financially motivated attack hypothesis is more supported due to the nature of the data targeted (payroll and personal information) and the lack of immediate claims from state actors, which is common in espionage cases.
3. Key Assumptions and Red Flags
– **Assumptions**: It is assumed that the absence of a ransomware claim does not rule out financial motives. The hypothesis assumes that the data’s nature indicates financial intent.
– **Red Flags**: The lack of immediate responsibility claim by any group could suggest either a sophisticated actor or an internal oversight. The current inability to estimate financial impact raises concerns about the completeness of the internal assessment.
4. Implications and Strategic Risks
The breach could lead to significant financial losses, reputational damage, and regulatory scrutiny for Dentsu. If sensitive client data is exploited, it may result in legal consequences and loss of client trust. The attack highlights potential vulnerabilities in the cybersecurity infrastructure of multinational corporations, which could be exploited in future attacks.
5. Recommendations and Outlook
- Conduct a comprehensive forensic investigation to identify the breach’s origin and scope.
- Implement enhanced cybersecurity protocols, including employee training and regular system audits.
- Engage with cybersecurity experts to develop a robust incident response plan.
- Scenario Projections:
- Best: Quick identification and resolution of vulnerabilities, minimal data exploitation.
- Worst: Data is sold on the dark web, leading to widespread financial and reputational damage.
- Most Likely: Some data exploitation occurs, but damage is contained through swift action.
6. Key Individuals and Entities
– Dentsu
– Merkle
7. Thematic Tags
national security threats, cybersecurity, data breach, corporate espionage