DOGE Denizen Marko Elez Leaked API Key for xAI – Krebs on Security
Published on: 2025-07-15
Intelligence Report: DOGE Denizen Marko Elez Leaked API Key for xAI – Krebs on Security
1. BLUF (Bottom Line Up Front)
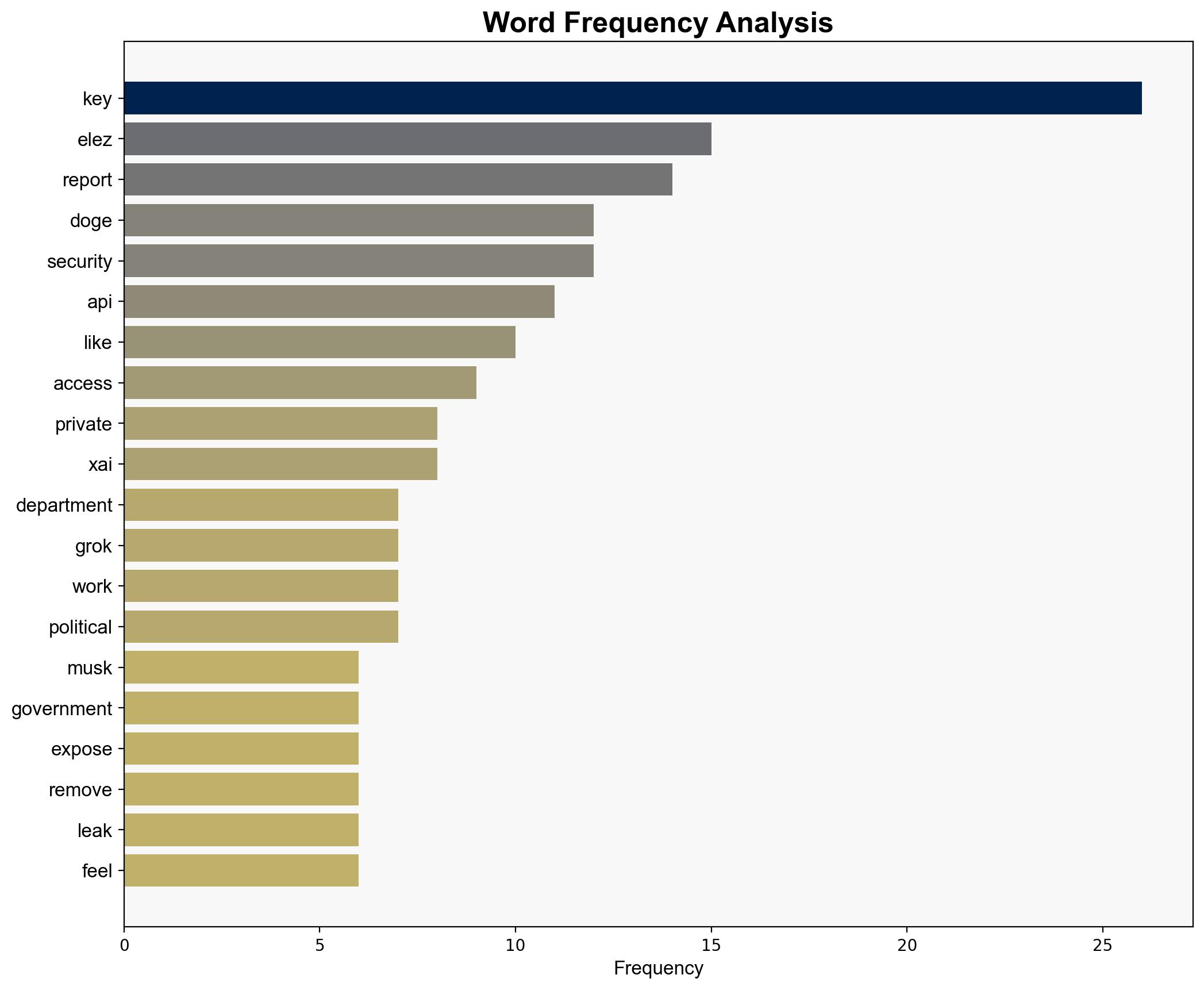
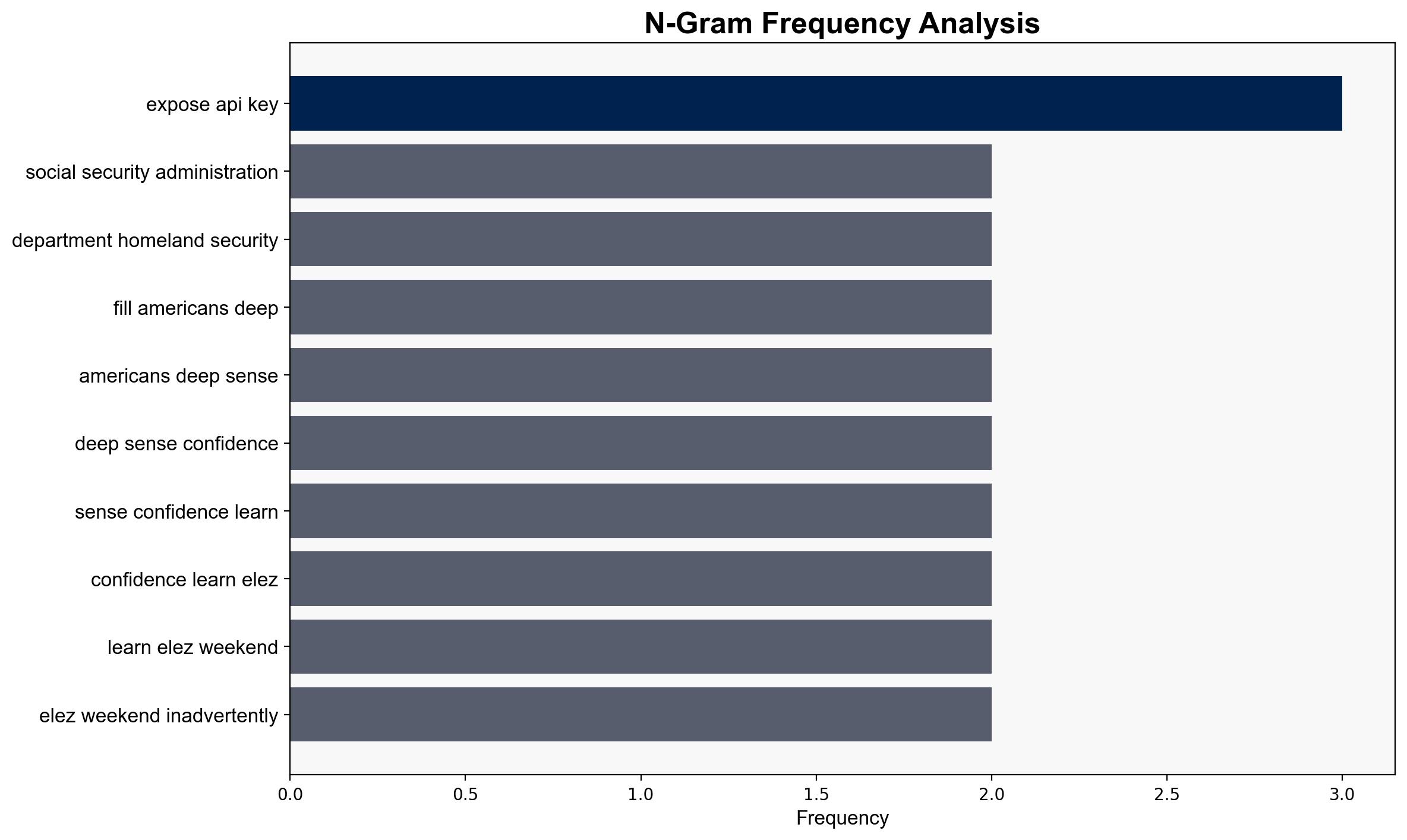
Marko Elez inadvertently leaked a sensitive API key for xAI on GitHub, exposing vulnerabilities in systems connected to various U.S. government departments. This incident highlights critical lapses in operational security and raises concerns about the handling of sensitive information by individuals with access to high-level data. Immediate steps are needed to enhance security protocols and prevent future breaches.
2. Detailed Analysis
The following structured analytic techniques have been applied to ensure methodological consistency:
Adversarial Threat Simulation
Simulated scenarios indicate that similar leaks could be exploited by cyber adversaries to gain unauthorized access to sensitive government systems, potentially compromising national security.
Indicators Development
Monitoring systems should be enhanced to detect unusual access patterns and unauthorized data interactions, providing early warnings of potential breaches.
Bayesian Scenario Modeling
Probabilistic models suggest a moderate likelihood of further security breaches if current protocols remain unchanged, emphasizing the need for immediate corrective action.
Cognitive Bias Stress Test
Analysis indicates potential underestimation of insider threats, necessitating a reevaluation of trust and access levels within sensitive departments.
Causal Layered Analysis (CLA)
The leak is symptomatic of deeper systemic issues, including inadequate security culture and oversight, which require comprehensive policy reforms.
3. Implications and Strategic Risks
The leak could lead to significant political and cyber risks, including unauthorized data access and manipulation. There is a potential for cascading effects, such as the exploitation of compromised systems to launch further attacks or influence operations. The incident underscores the need for robust cybersecurity measures across all government sectors.
4. Recommendations and Outlook
- Implement stringent access controls and regular audits to prevent unauthorized data exposure.
- Enhance training programs focused on operational security and the handling of sensitive information.
- Develop scenario-based response plans to address potential future breaches effectively.
- Best Case: Strengthened security protocols prevent future incidents, restoring confidence in system integrity.
- Worst Case: Continued security lapses lead to significant data breaches, undermining national security.
- Most Likely: Incremental improvements in security measures reduce but do not eliminate the risk of future leaks.
5. Key Individuals and Entities
Marko Elez, Philippe Caturegli
6. Thematic Tags
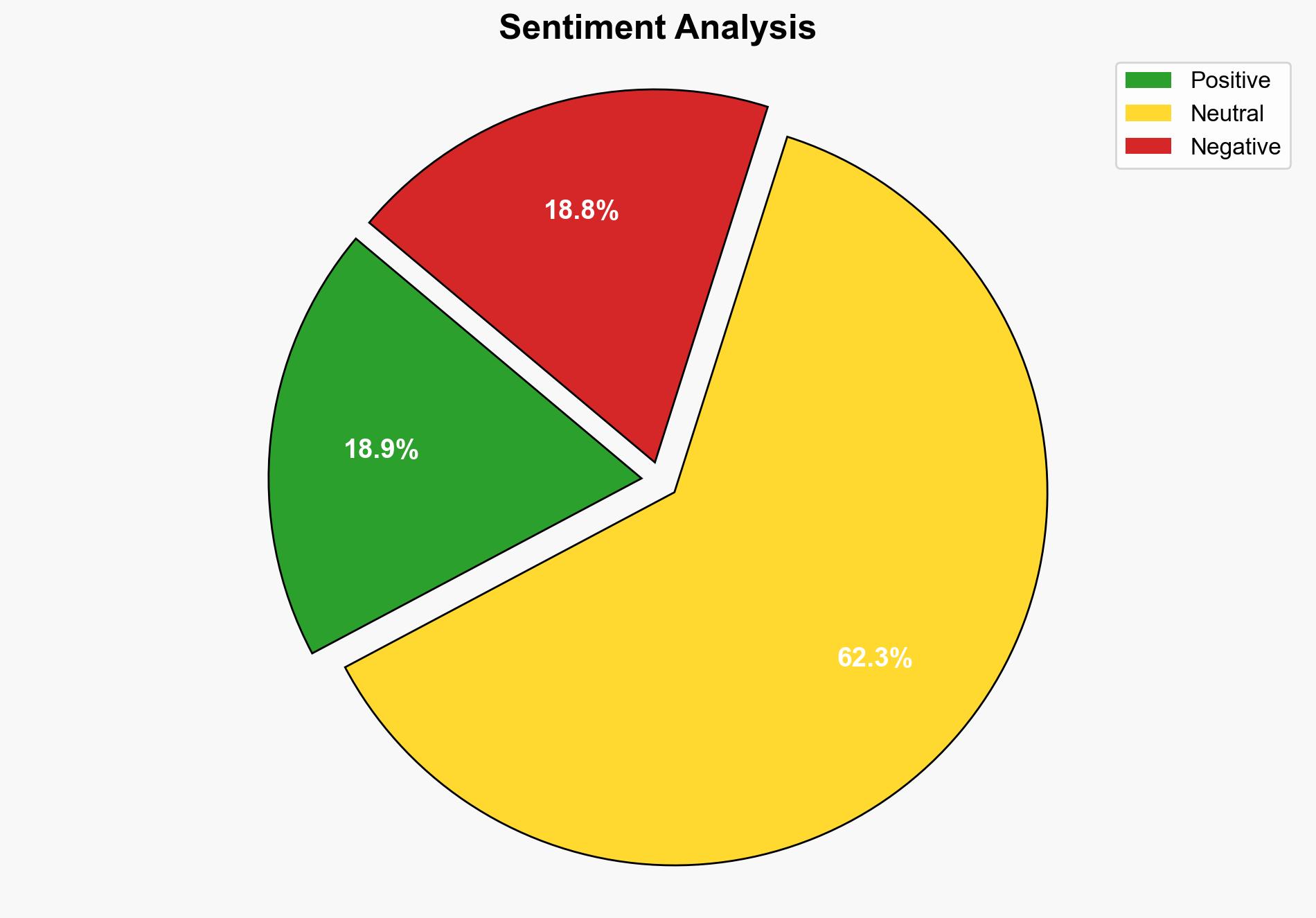
national security threats, cybersecurity, insider threats, operational security