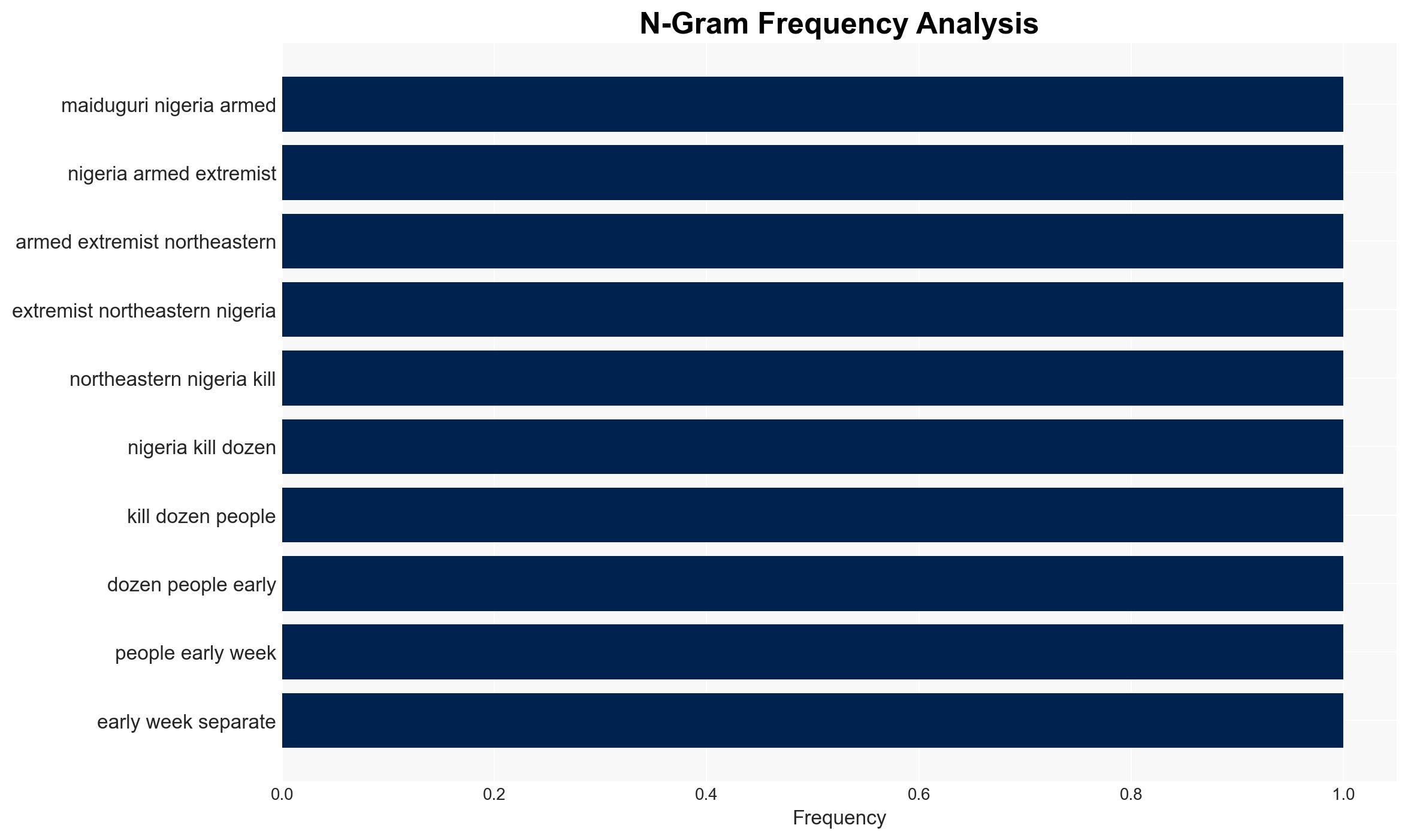
Dozens killed in coordinated attacks by armed extremists in northeastern Nigeria
Published on: 2026-01-31
AI-powered OSINT brief from verified open sources. Automated NLP signal extraction with human verification. See our Methodology and Why WorldWideWatchers.
Intelligence Report: Armed extremists kill dozens in northeastern Nigeria
1. BLUF (Bottom Line Up Front)
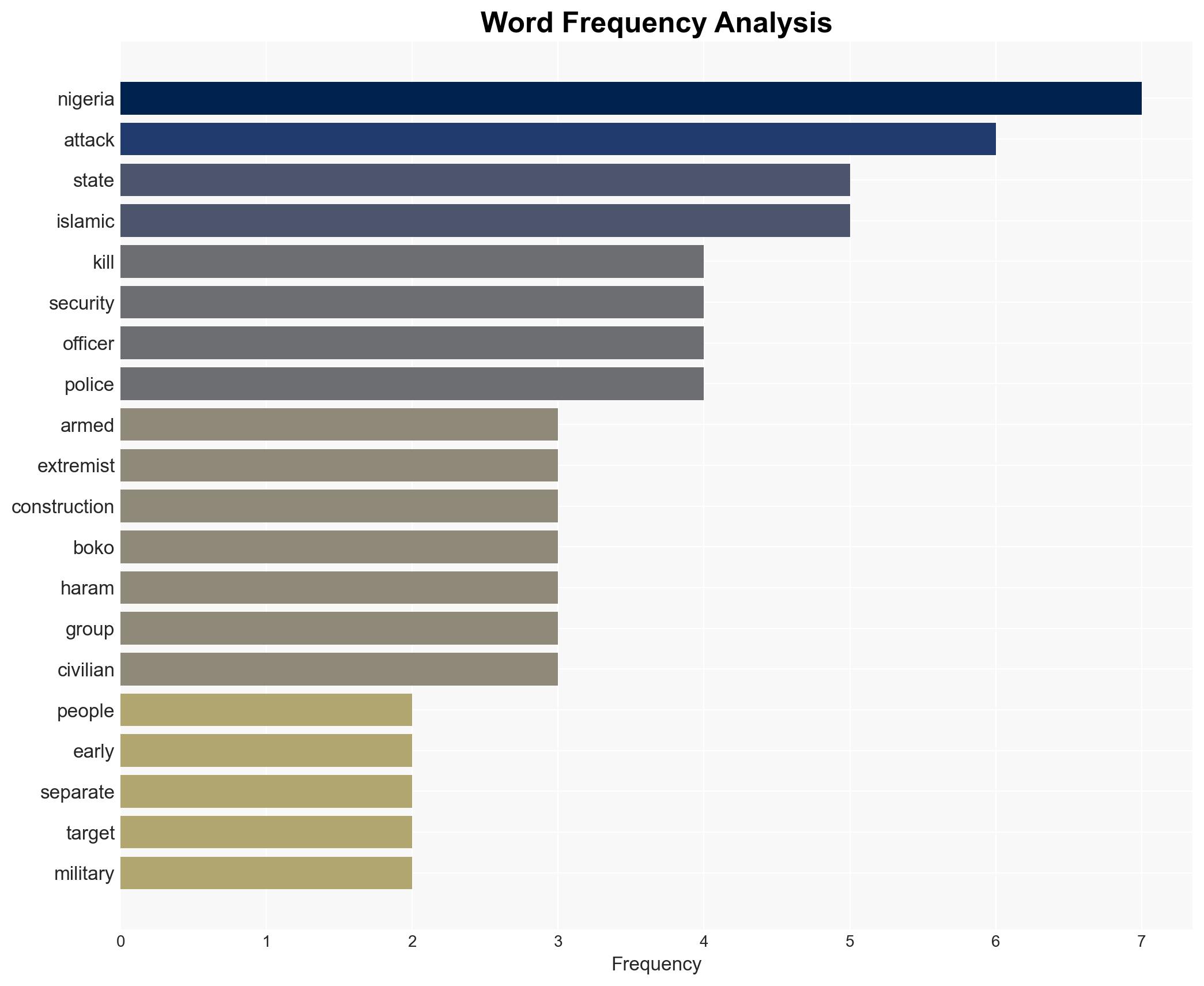
Armed extremists, likely affiliated with Boko Haram or ISWAP, conducted lethal attacks in northeastern Nigeria, killing dozens, including construction workers and military personnel. The attacks underscore persistent security challenges in the region. The most likely hypothesis is that Boko Haram is responsible, given their historical opposition to development projects. Overall confidence in this assessment is moderate due to limited specific attribution evidence.
2. Competing Hypotheses
- Hypothesis A: Boko Haram is responsible for the attacks, as they have a history of targeting development projects and military installations in Borno State. This is supported by the police official’s statement and historical patterns. However, there is uncertainty due to the lack of direct claims of responsibility.
- Hypothesis B: The attacks were carried out by ISWAP, given their operational presence in the region and recent activity. This hypothesis is less supported due to the absence of specific indicators linking ISWAP to these particular incidents.
- Assessment: Hypothesis A is currently better supported due to historical patterns and the police official’s assessment. Key indicators that could shift this judgment include claims of responsibility or further intelligence linking ISWAP to the attacks.
3. Key Assumptions and Red Flags
- Assumptions: Boko Haram opposes development projects; ISWAP is active in the region; local security forces have limited capacity to prevent such attacks; the information from local sources is reliable.
- Information Gaps: Specific attribution of the attacks; detailed intelligence on the attackers’ identities and affiliations; confirmation of drone usage.
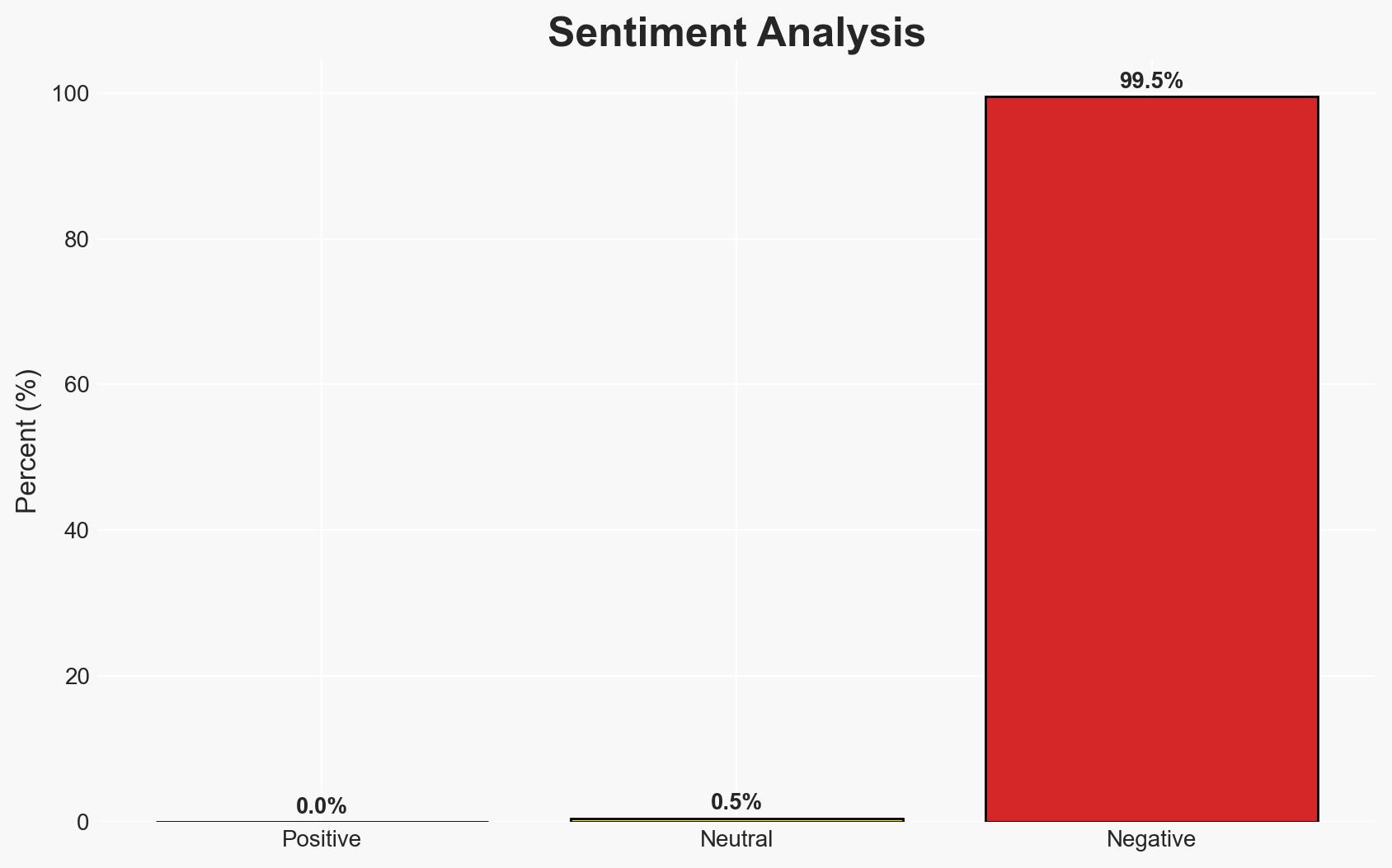
- Bias & Deception Risks: Potential bias from local security sources; risk of misinformation from extremist groups; lack of independent verification of events.
4. Implications and Strategic Risks
The attacks could exacerbate regional instability and undermine confidence in the Nigerian government’s ability to maintain security. This may lead to increased international scrutiny and potential intervention.
- Political / Geopolitical: Potential for increased international pressure on Nigeria to address security issues; possible strain on regional relations if violence spills over borders.
- Security / Counter-Terrorism: Heightened threat level in northeastern Nigeria; potential for further attacks on infrastructure and military targets.
- Cyber / Information Space: Potential use of digital platforms by extremist groups to claim responsibility or spread propaganda.
- Economic / Social: Disruption to local economies and development projects; increased displacement and humanitarian needs.
5. Recommendations and Outlook
- Immediate Actions (0–30 days): Enhance intelligence sharing with regional partners; increase security presence in vulnerable areas; monitor extremist communications for claims of responsibility.
- Medium-Term Posture (1–12 months): Strengthen military and civilian task force capabilities; develop community engagement programs to counter extremist narratives; explore diplomatic avenues for regional cooperation.
- Scenario Outlook: Best: Successful containment and reduction of extremist activity. Worst: Escalation of attacks leading to broader regional instability. Most-Likely: Continued sporadic attacks with limited containment success.
6. Key Individuals and Entities
- Not clearly identifiable from open sources in this snippet.
7. Thematic Tags
Counter-Terrorism, Boko Haram, ISWAP, Nigeria security, regional instability, military operations, extremist violence
Structured Analytic Techniques Applied
- ACH 2.0: Reconstruct likely threat actor intentions via hypothesis testing and structured refutation.
- Indicators Development: Track radicalization signals and propaganda patterns to anticipate operational planning.
- Narrative Pattern Analysis: Analyze spread/adaptation of ideological narratives for recruitment/incitement signals.
Explore more:
Counter-Terrorism Briefs ·
Daily Summary ·
Support us