Drone attack near Tajikistan-Afghanistan border kills 3 Chinese, heightening security concerns in Central Asia
Published on: 2025-12-03
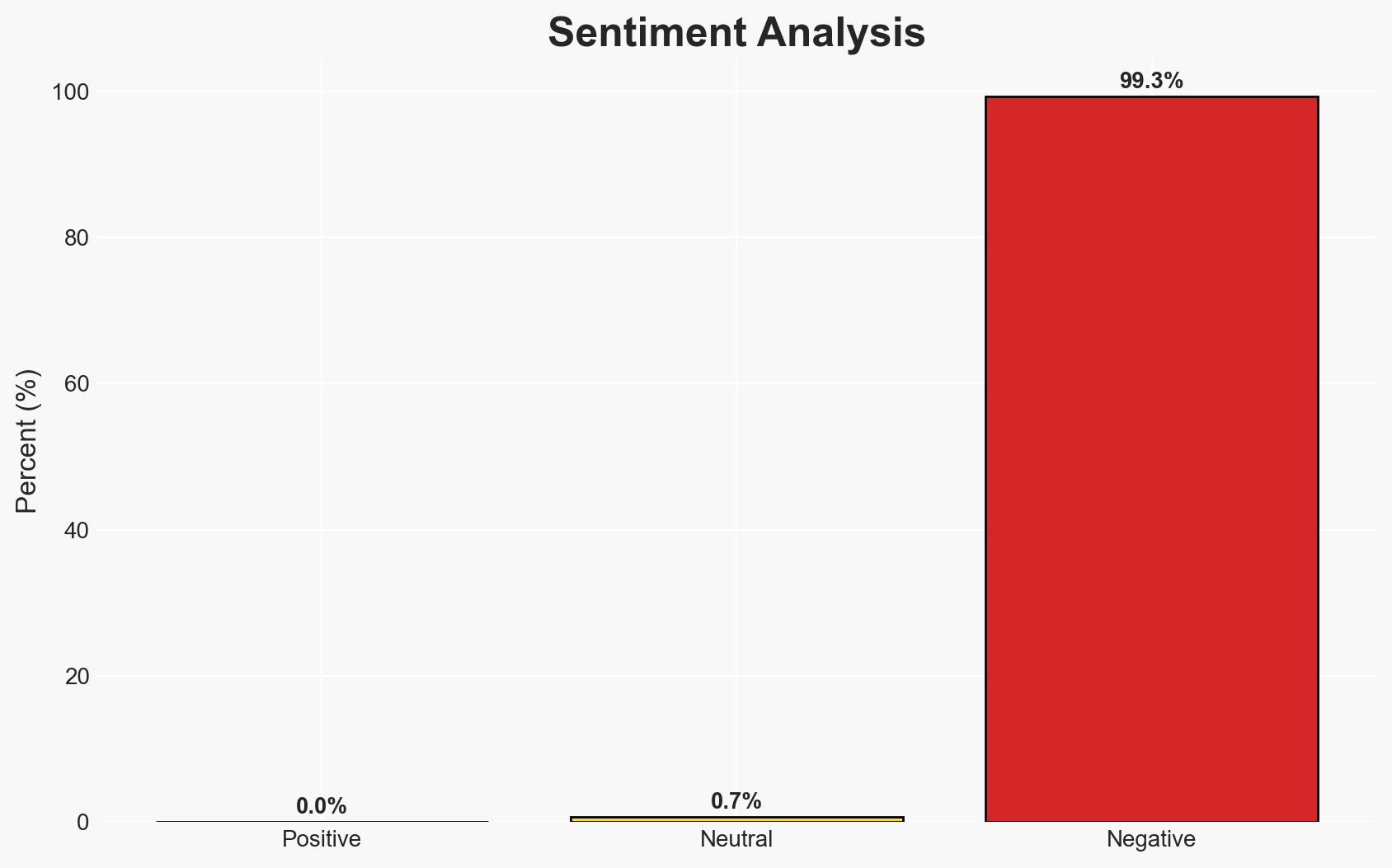
AI-powered OSINT brief from verified open sources. Automated NLP signal extraction with human verification. See our Methodology and Why WorldWideWatchers.
Intelligence Report: Drone strike on Tajik-Afghan border kills 3 Chinese nationals amid rising regional tensions
1. BLUF (Bottom Line Up Front)
The drone-assisted attack on the Tajik-Afghan border, resulting in the deaths of three Chinese nationals, underscores escalating regional instability and the growing threat to Chinese interests in Central Asia. The most likely hypothesis is that the attack was conducted by ISKP or Jamaat Ansarullah, though attribution remains uncertain. This incident highlights the evolving tactics of insurgent groups and the geopolitical risks associated with China’s Belt and Road Initiative. Overall confidence in this assessment is moderate.
2. Competing Hypotheses
- Hypothesis A: The attack was carried out by ISKP, leveraging advanced asymmetric warfare tactics such as weaponized drones. This is supported by ISKP’s known activity in the region and previous clashes with Tajik forces. However, the lack of a claim of responsibility introduces uncertainty.
- Hypothesis B: The attack was executed by remnants of Jamaat Ansarullah, a group with a history of conflict with Tajik authorities. This hypothesis is supported by the group’s operational history but lacks direct evidence linking them to the current incident.
- Assessment: Hypothesis A is currently better supported due to ISKP’s capability and history of similar attacks. Indicators such as a claim of responsibility or further intelligence on ISKP’s movements could solidify this judgment.
3. Key Assumptions and Red Flags
- Assumptions: The attack was premeditated and involved cross-border elements; insurgent groups have the capability to deploy weaponized drones; China will respond diplomatically to protect its interests.
- Information Gaps: Direct evidence linking the attackers to a specific group; intelligence on the planning and execution of the attack; insights into the strategic objectives of the perpetrators.
- Bias & Deception Risks: Potential bias in attributing the attack to groups with known animosity towards Tajikistan; risk of deception by groups seeking to mislead attribution efforts.
4. Implications and Strategic Risks
This development could exacerbate regional tensions and complicate China’s strategic investments in Central Asia. It may also embolden other insurgent groups to adopt similar tactics.
- Political / Geopolitical: Potential strain on Tajik-Afghan relations and increased Chinese diplomatic pressure on both countries.
- Security / Counter-Terrorism: Heightened security measures along the border and increased counter-terrorism operations in the region.
- Cyber / Information Space: Potential for increased propaganda and misinformation campaigns by insurgent groups to exploit the incident.
- Economic / Social: Possible disruptions to Chinese investments and projects, leading to economic instability in affected areas.
5. Recommendations and Outlook
- Immediate Actions (0–30 days): Enhance border security and surveillance, initiate joint investigations with Afghan authorities, and increase diplomatic engagement with China.
- Medium-Term Posture (1–12 months): Strengthen regional counter-terrorism partnerships, invest in drone defense technologies, and develop contingency plans for protecting foreign nationals.
- Scenario Outlook:
- Best: Successful attribution and neutralization of the responsible group, leading to improved regional security.
- Worst: Escalation of cross-border violence and further attacks on foreign nationals, destabilizing the region.
- Most-Likely: Continued low-level insurgent activity with periodic attacks, maintaining a state of heightened alert.
6. Key Individuals and Entities
- ISKP (Islamic State-Khorasan Province)
- Jamaat Ansarullah
- Taliban (Afghan government)
- LLC Shahin SM (Targeted company)
- Chinese Foreign Ministry
- Tajik Foreign Ministry
7. Thematic Tags
Regional Focus, counter-terrorism, regional security, asymmetric warfare, Belt and Road Initiative, drone warfare, Central Asia instability, geopolitical risk
Structured Analytic Techniques Applied
- Causal Layered Analysis (CLA): Analyze events across surface happenings, systems, worldviews, and myths.
- Cross-Impact Simulation: Model ripple effects across neighboring states, conflicts, or economic dependencies.
- Scenario Generation: Explore divergent futures under varying assumptions to identify plausible paths.
- Network Influence Mapping: Map influence relationships to assess actor impact.
Explore more:
Regional Focus Briefs ·
Daily Summary ·
Support us