Dutch Court Upholds Seven-Year Sentence for Hacker Aiding Cocaine Smugglers via Port IT System Breach
Published on: 2026-01-13
AI-powered OSINT brief from verified open sources. Automated NLP signal extraction with human verification. See our Methodology and Why WorldWideWatchers.
Intelligence Report: Court tosses appeal by hacker who opened port to coke smugglers with malware
1. BLUF (Bottom Line Up Front)
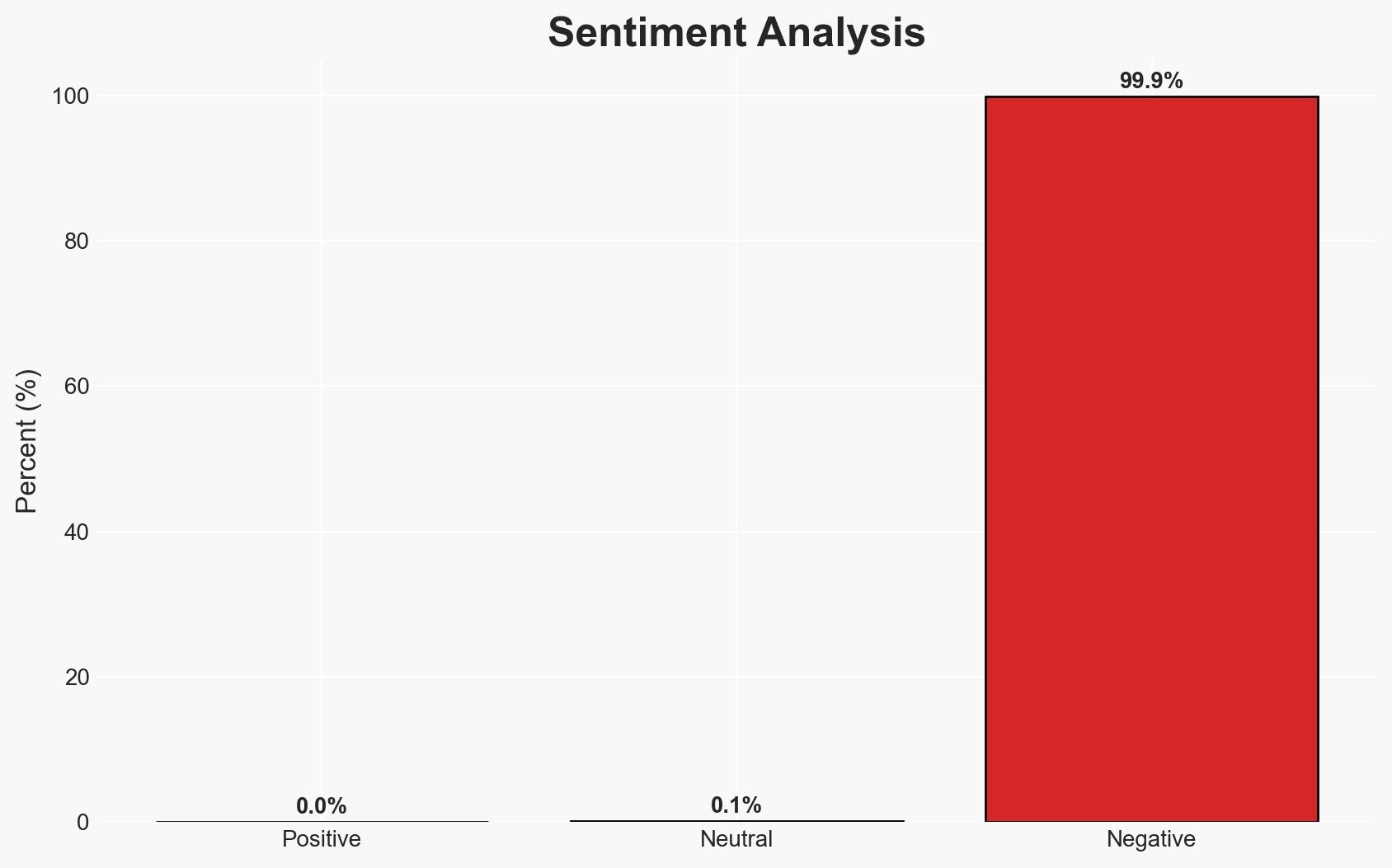
The Dutch appeals court upheld a seven-year sentence for a hacker involved in facilitating cocaine smuggling through port system breaches, rejecting claims of unlawful evidence gathering. This case highlights vulnerabilities in port security systems and the risks of insider threats. The judgment supports the hypothesis of organized crime exploiting cyber capabilities, with moderate confidence.
2. Competing Hypotheses
- Hypothesis A: The hacker acted independently to exploit port systems for personal gain, using organized crime networks opportunistically. Evidence includes the hacker’s central role and direct communications with accomplices. Uncertainties include the extent of organized crime’s influence over the hacker.
- Hypothesis B: The hacker was a key operative within a larger organized crime syndicate, tasked specifically with enabling drug smuggling operations. Supporting evidence includes coordinated use of encrypted communications and sophisticated cyber tactics. Contradictory evidence is limited but includes the hacker’s apparent autonomy in decision-making.
- Assessment: Hypothesis B is currently better supported due to the structured and coordinated nature of the operation, as evidenced by the use of encrypted communications and tactical shifts. Indicators such as further arrests or evidence of broader syndicate involvement could reinforce this judgment.
3. Key Assumptions and Red Flags
- Assumptions: The hacker had significant technical skills; organized crime networks are increasingly leveraging cyber capabilities; insider threats are a critical vulnerability in port security.
- Information Gaps: The full extent of the hacker’s connections to organized crime and the potential existence of other compromised ports remain unknown.
- Bias & Deception Risks: Potential bias in interpreting the hacker’s communications as indicative of broader syndicate involvement; risk of deception in the hacker’s claims of independence.
4. Implications and Strategic Risks
This development underscores the intersection of cybercrime and traditional organized crime, with potential for increased sophistication in smuggling operations.
- Political / Geopolitical: Potential strain on international law enforcement cooperation if evidence handling is contested.
- Security / Counter-Terrorism: Increased risk of similar cyber-enabled smuggling operations at other ports.
- Cyber / Information Space: Highlighted need for enhanced cybersecurity measures in critical infrastructure.
- Economic / Social: Potential economic impact from disrupted port operations and increased security costs.
5. Recommendations and Outlook
- Immediate Actions (0–30 days): Enhance monitoring of port cybersecurity; review insider threat protocols; increase intelligence sharing on organized crime cyber tactics.
- Medium-Term Posture (1–12 months): Develop resilience measures for port infrastructure; strengthen international partnerships for cybercrime prevention; invest in training for detecting insider threats.
- Scenario Outlook: Best: Strengthened port security deters future breaches. Worst: Increased cyber-enabled smuggling operations. Most-Likely: Gradual improvement in security with occasional breaches as tactics evolve.
6. Key Individuals and Entities
- Not clearly identifiable from open sources in this snippet.
7. Thematic Tags
cybersecurity, cybercrime, organized crime, port security, insider threat, encrypted communications, drug smuggling
Structured Analytic Techniques Applied
- Adversarial Threat Simulation: Model and simulate actions of cyber adversaries to anticipate vulnerabilities and improve resilience.
- Indicators Development: Detect and monitor behavioral or technical anomalies across systems for early threat detection.
- Bayesian Scenario Modeling: Quantify uncertainty and predict cyberattack pathways using probabilistic inference.
- Network Influence Mapping: Map influence relationships to assess actor impact.
Explore more:
Cybersecurity Briefs ·
Daily Summary ·
Support us