Dutch Data Protection Authority and Judiciary Council Breached by Ivanti EPMM Vulnerability Exposing Employee…
Published on: 2026-02-10
AI-powered OSINT brief from verified open sources. Automated NLP signal extraction with human verification. See our Methodology and Why WorldWideWatchers.
Intelligence Report: Dutch agencies hit by Ivanti EPMM exploit exposing employee contact data
1. BLUF (Bottom Line Up Front)
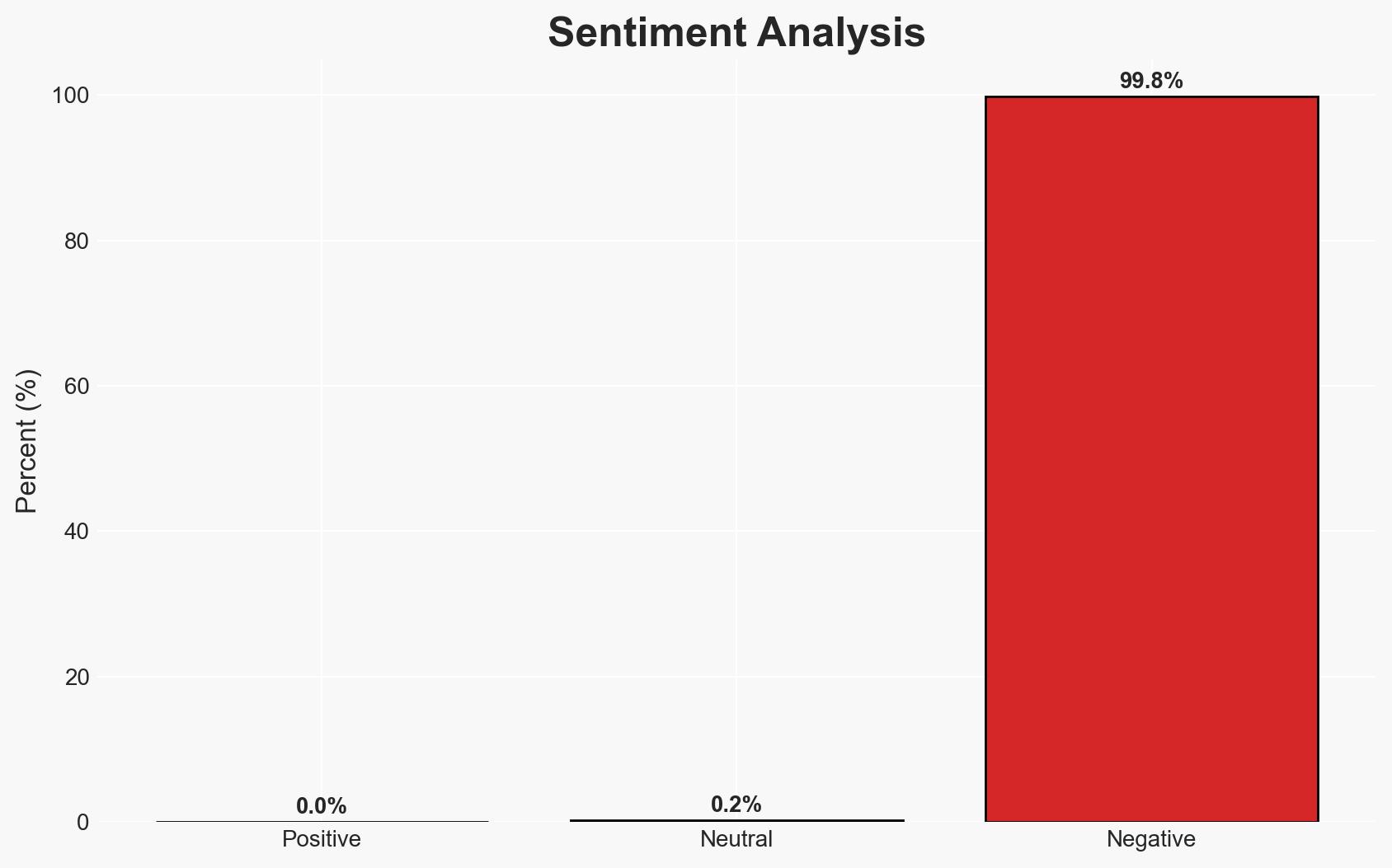
The exploitation of vulnerabilities in Ivanti Endpoint Manager Mobile (EPMM) has led to unauthorized access to employee contact data at Dutch governmental agencies, including the Data Protection Authority and the Council for the Judiciary. The incident highlights potential systemic cybersecurity weaknesses in mobile device management platforms. Moderate confidence in the hypothesis that this is part of a broader cyber threat targeting governmental institutions.
2. Competing Hypotheses
- Hypothesis A: The cyberattacks are part of a coordinated campaign by a state-sponsored actor targeting European governmental institutions to gather intelligence. Supporting evidence includes the simultaneous targeting of multiple agencies and the European Commission. However, the lack of direct attribution and specific motives remains a key uncertainty.
- Hypothesis B: The attacks are opportunistic cybercrime activities exploiting known vulnerabilities for financial gain or data resale. This is supported by the typical pattern of exploiting newly disclosed vulnerabilities. Contradicting evidence includes the focus on governmental agencies rather than broader targets.
- Assessment: Hypothesis A is currently better supported due to the strategic nature of the targets and the timing of the attacks. Indicators that could shift this judgment include evidence of financial transactions involving the stolen data or attribution to known cybercriminal groups.
3. Key Assumptions and Red Flags
- Assumptions: The attackers have advanced capabilities to exploit newly disclosed vulnerabilities; the primary objective is intelligence gathering; affected agencies have not yet fully assessed the breach’s scope.
- Information Gaps: Lack of specific attribution to a threat actor; details on the full extent of data accessed; potential connections to other recent cyber incidents.
- Bias & Deception Risks: Potential confirmation bias in attributing attacks to state-sponsored actors without concrete evidence; risk of deception by attackers to mask true intentions.
4. Implications and Strategic Risks
This development could lead to increased scrutiny and pressure on governmental cybersecurity measures, potentially prompting policy changes or international cooperation efforts. The incident may also embolden other actors to exploit similar vulnerabilities.
- Political / Geopolitical: Potential for increased tensions between affected states and suspected sponsoring nations, leading to diplomatic repercussions.
- Security / Counter-Terrorism: Heightened alertness and resource allocation towards protecting critical infrastructure and governmental data.
- Cyber / Information Space: Increased focus on securing mobile device management systems and patch management processes.
- Economic / Social: Potential public concern over data privacy and governmental cybersecurity capabilities, impacting trust in public institutions.
5. Recommendations and Outlook
- Immediate Actions (0–30 days): Conduct thorough forensic analysis to ascertain the breach’s scope, enhance monitoring of affected systems, and expedite patching processes.
- Medium-Term Posture (1–12 months): Develop and implement comprehensive cybersecurity training for staff, strengthen international cybersecurity collaboration, and review mobile device management protocols.
- Scenario Outlook: Best: Rapid containment and no further incidents; Worst: Escalation with additional breaches and data leaks; Most-Likely: Continued probing of vulnerabilities with sporadic incidents.
6. Key Individuals and Entities
- State Secretary Rutte (JenV)
- State Secretary Van Marum (BZK)
- Dutch Data Protection Authority (AP)
- Council for the Judiciary (Rvdr)
- National Cyber Security Center (NCSC)
- European Commission
7. Thematic Tags
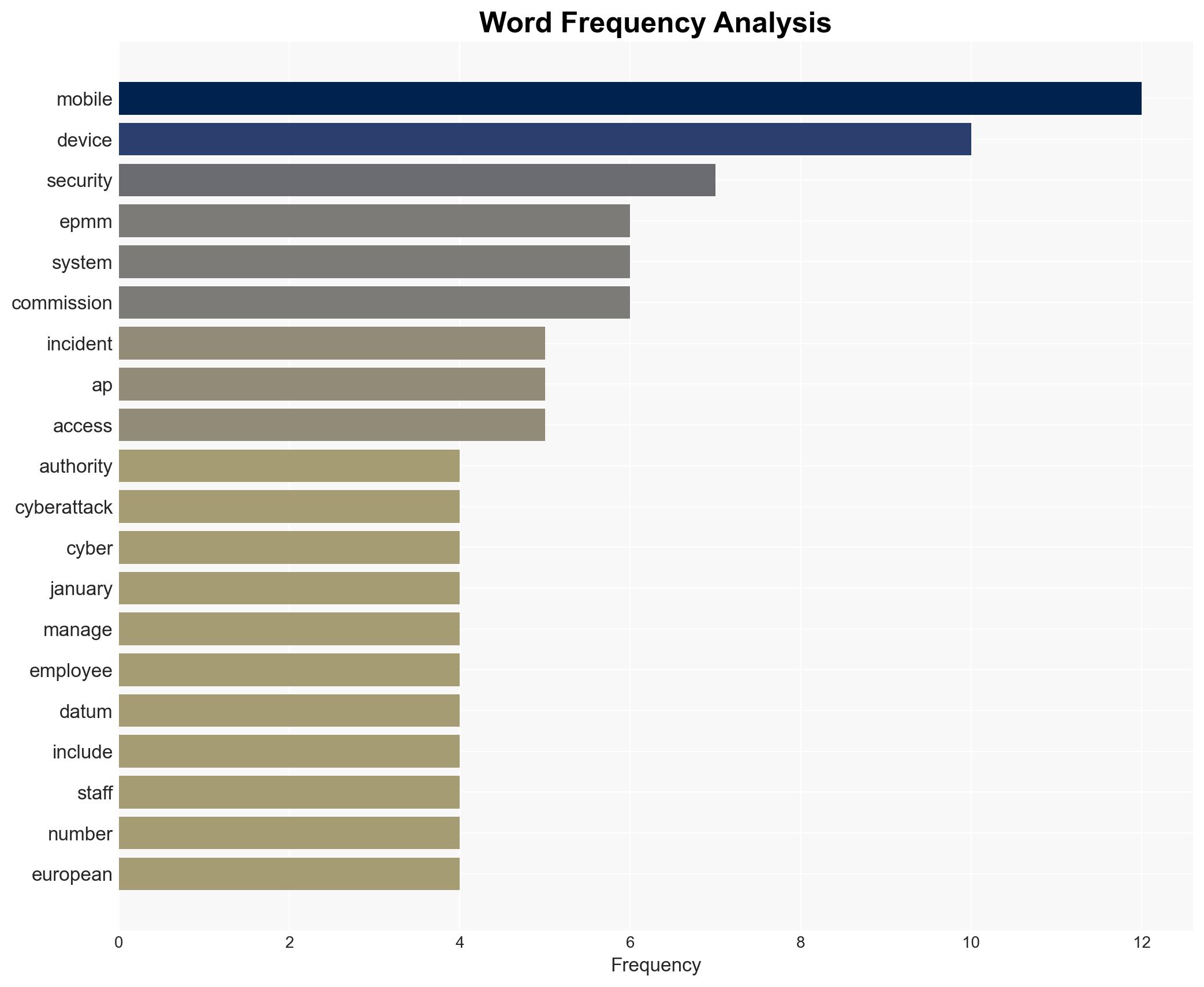
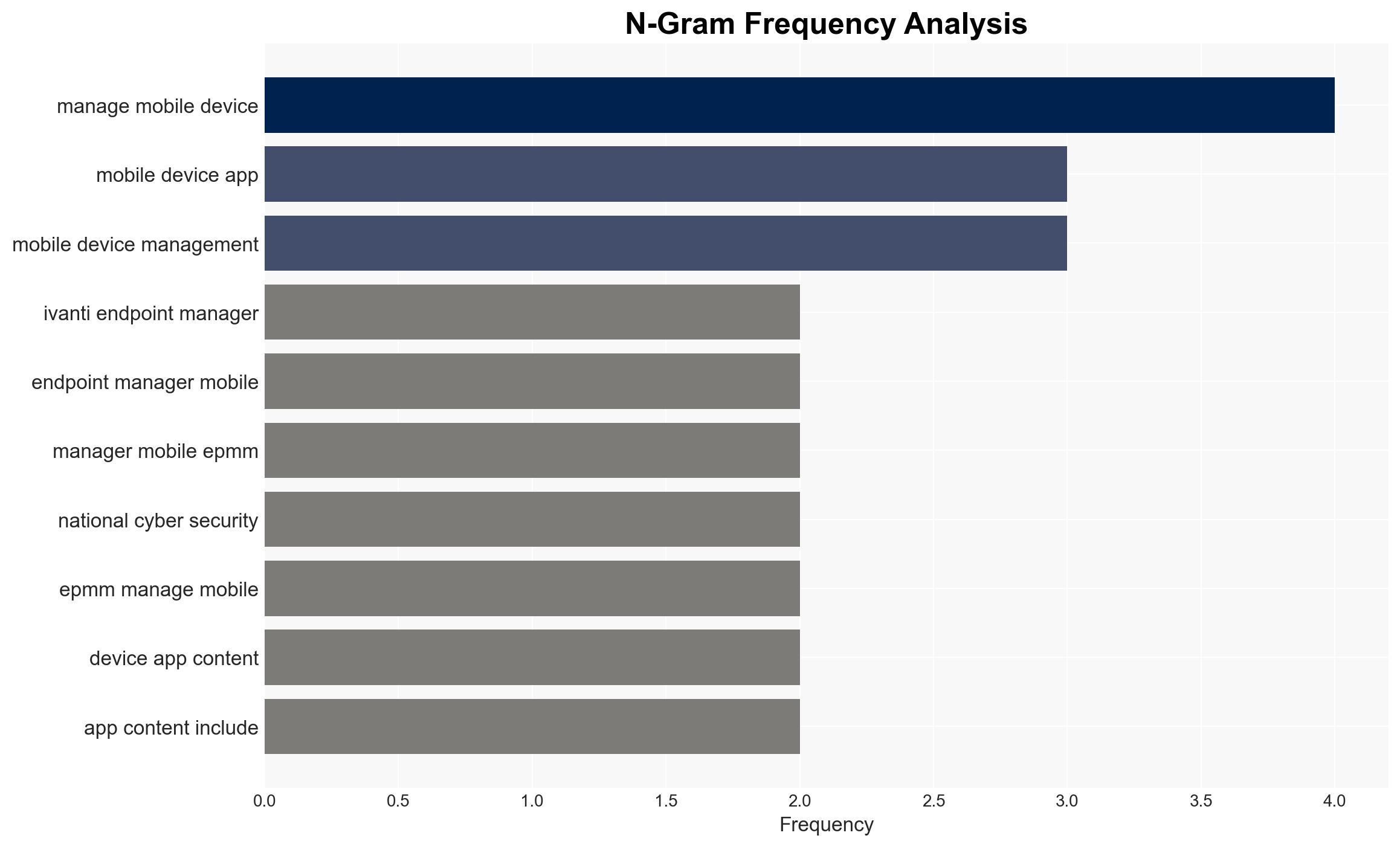
cybersecurity, data breach, governmental institutions, mobile device management, state-sponsored threats, vulnerability exploitation, European Union
Structured Analytic Techniques Applied
- Adversarial Threat Simulation: Model and simulate actions of cyber adversaries to anticipate vulnerabilities and improve resilience.
- Indicators Development: Detect and monitor behavioral or technical anomalies across systems for early threat detection.
- Bayesian Scenario Modeling: Quantify uncertainty and predict cyberattack pathways using probabilistic inference.
Explore more:
Cybersecurity Briefs ·
Daily Summary ·
Support us