Dutch Data Protection Authority Reports Cyber Attack Compromising Employee Contact Information via Ivanti Flaw
Published on: 2026-02-10
AI-powered OSINT brief from verified open sources. Automated NLP signal extraction with human verification. See our Methodology and Why WorldWideWatchers.
Intelligence Report: Dutch Authorities Confirm Ivanti Zero-Day Exploit Exposed Employee Contact Data
1. BLUF (Bottom Line Up Front)
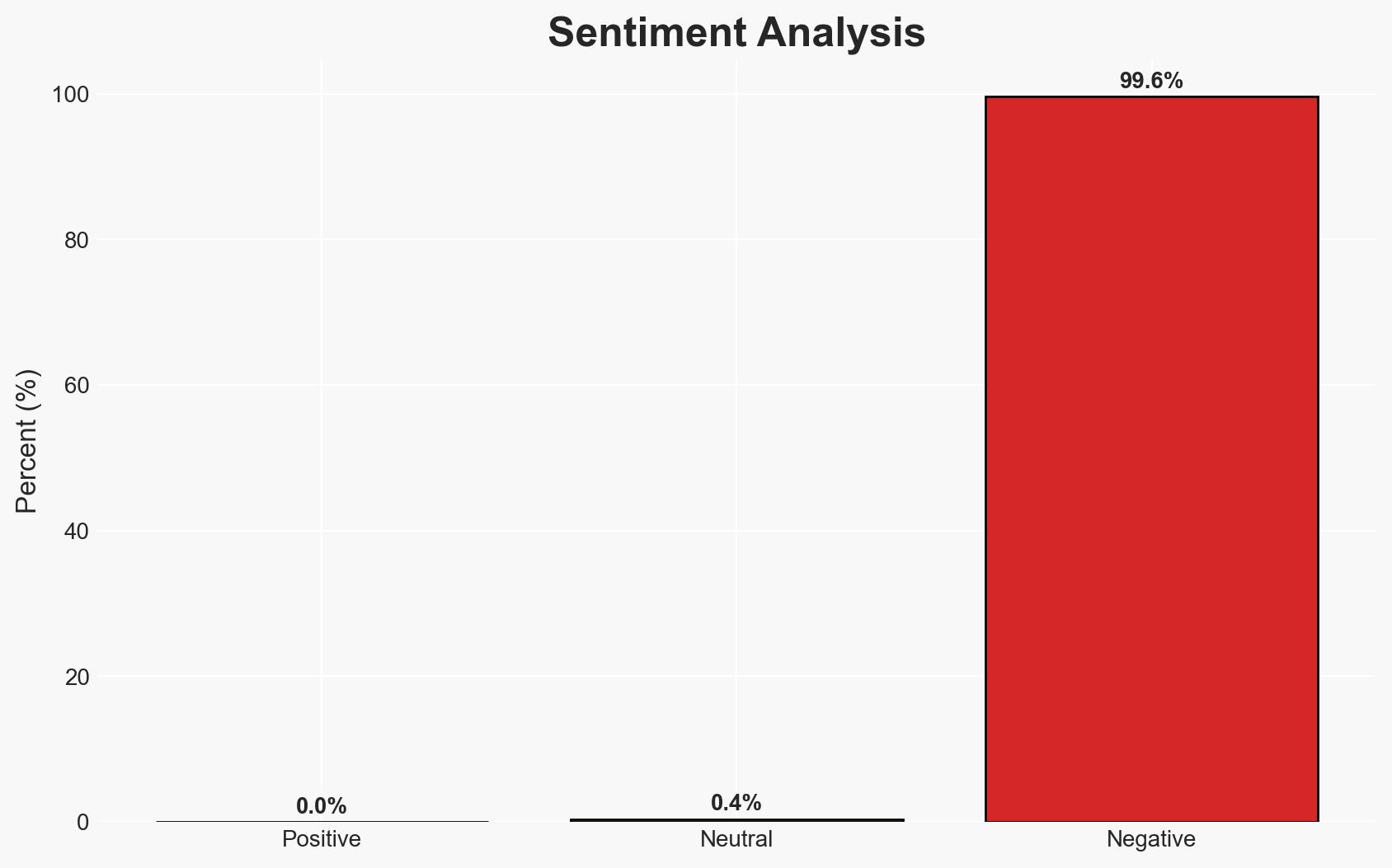
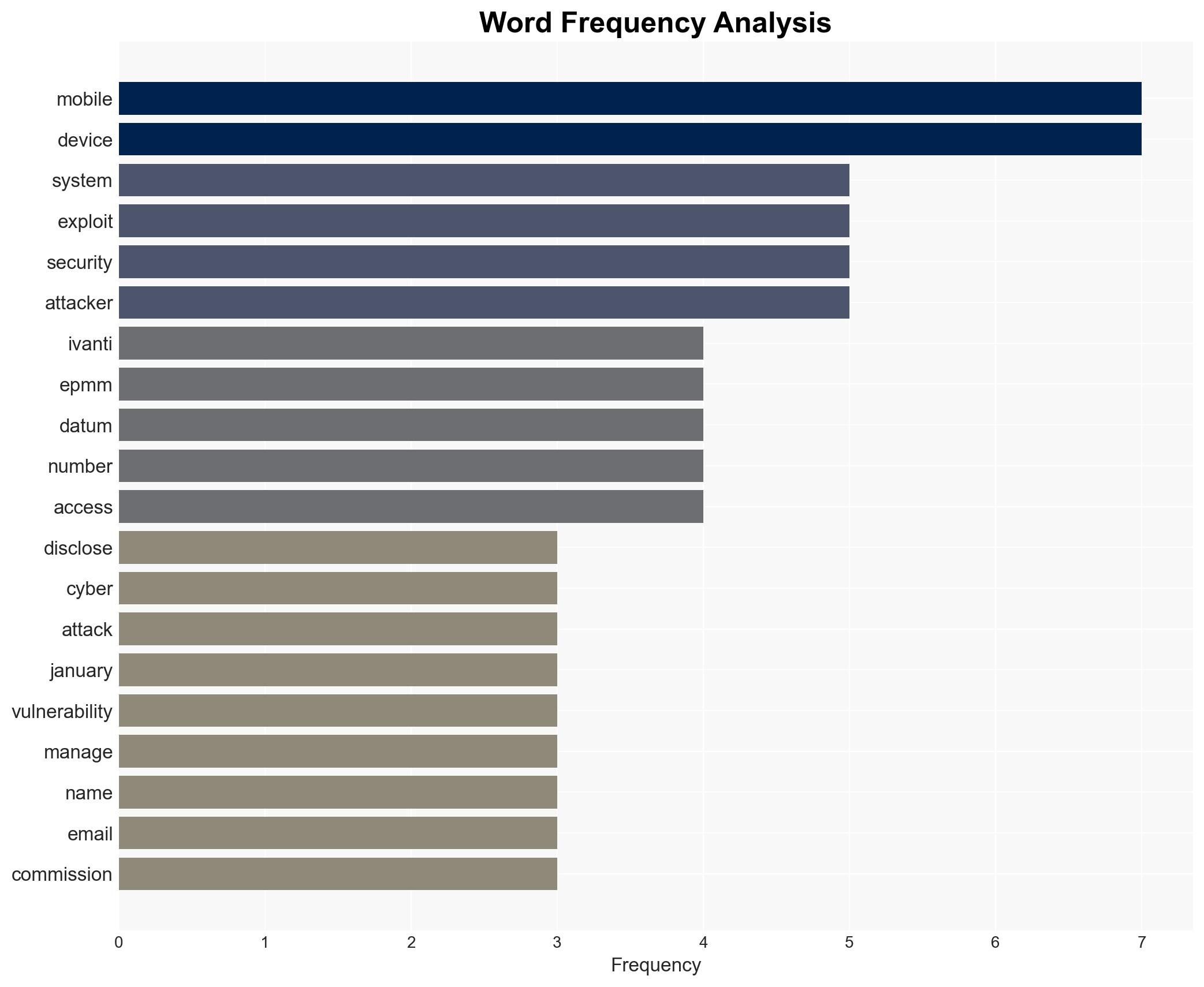
The recent exploitation of zero-day vulnerabilities in Ivanti Endpoint Manager Mobile (EPMM) has compromised employee contact data across multiple European governmental entities, including the Netherlands and Finland. The most likely hypothesis is that these attacks are targeted and coordinated, rather than opportunistic. This assessment is made with moderate confidence due to the limited scope of confirmed victims and the nature of the exploited vulnerabilities.
2. Competing Hypotheses
- Hypothesis A: The cyber attacks exploiting Ivanti EPMM vulnerabilities are targeted operations aimed at specific governmental entities to gather sensitive employee data. This is supported by the coordinated timing and the specific targeting of governmental organizations. However, the lack of detailed attribution and the limited number of confirmed victims are key uncertainties.
- Hypothesis B: The attacks are opportunistic, exploiting widely known vulnerabilities in Ivanti EPMM to gather data indiscriminately. This is contradicted by the focused nature of the attacks on specific governmental bodies and the quick containment measures observed, which suggest a more targeted approach.
- Assessment: Hypothesis A is currently better supported due to the pattern of targeting governmental entities and the strategic value of the compromised data. Indicators that could shift this judgment include evidence of broader, non-targeted exploitation or new information on the attackers’ motivations.
3. Key Assumptions and Red Flags
- Assumptions: The vulnerabilities in Ivanti EPMM are the primary vector for these breaches; the attackers have a strategic interest in governmental employee data; containment measures have been effective in preventing further breaches.
- Information Gaps: Detailed attribution of the attackers; full scope of affected entities beyond those disclosed; specific methods used to exploit the vulnerabilities.
- Bias & Deception Risks: Potential underreporting by affected entities; reliance on vendor-provided information which may downplay the scope of the breach; cognitive bias towards assuming state-sponsored involvement without clear evidence.
4. Implications and Strategic Risks
The exploitation of Ivanti EPMM vulnerabilities could lead to increased scrutiny on mobile device management security across governmental and critical infrastructure sectors. Over time, this may prompt regulatory changes and heightened security protocols.
- Political / Geopolitical: Potential for diplomatic tensions if state-sponsored involvement is confirmed; increased collaboration among European cybersecurity agencies.
- Security / Counter-Terrorism: Enhanced threat landscape for governmental entities; potential for exploitation of compromised data in further attacks.
- Cyber / Information Space: Increased focus on zero-day vulnerability management and patching practices; potential for misinformation if the scope of the breach is misrepresented.
- Economic / Social: Potential economic impact on Ivanti and similar vendors; public concern over governmental data security practices.
5. Recommendations and Outlook
- Immediate Actions (0–30 days): Conduct thorough audits of mobile device management systems; implement immediate patching of known vulnerabilities; enhance monitoring for signs of further exploitation.
- Medium-Term Posture (1–12 months): Develop and enforce stricter security protocols for mobile device management; foster international cooperation on cybersecurity threat intelligence sharing.
- Scenario Outlook:
- Best Case: Rapid containment and patching prevent further breaches, leading to improved security practices.
- Worst Case: Further exploitation leads to significant data breaches across multiple sectors, prompting regulatory backlash.
- Most Likely: Continued targeted attacks with gradual improvements in security posture and international cooperation.
6. Key Individuals and Entities
- Ivanti (Vendor)
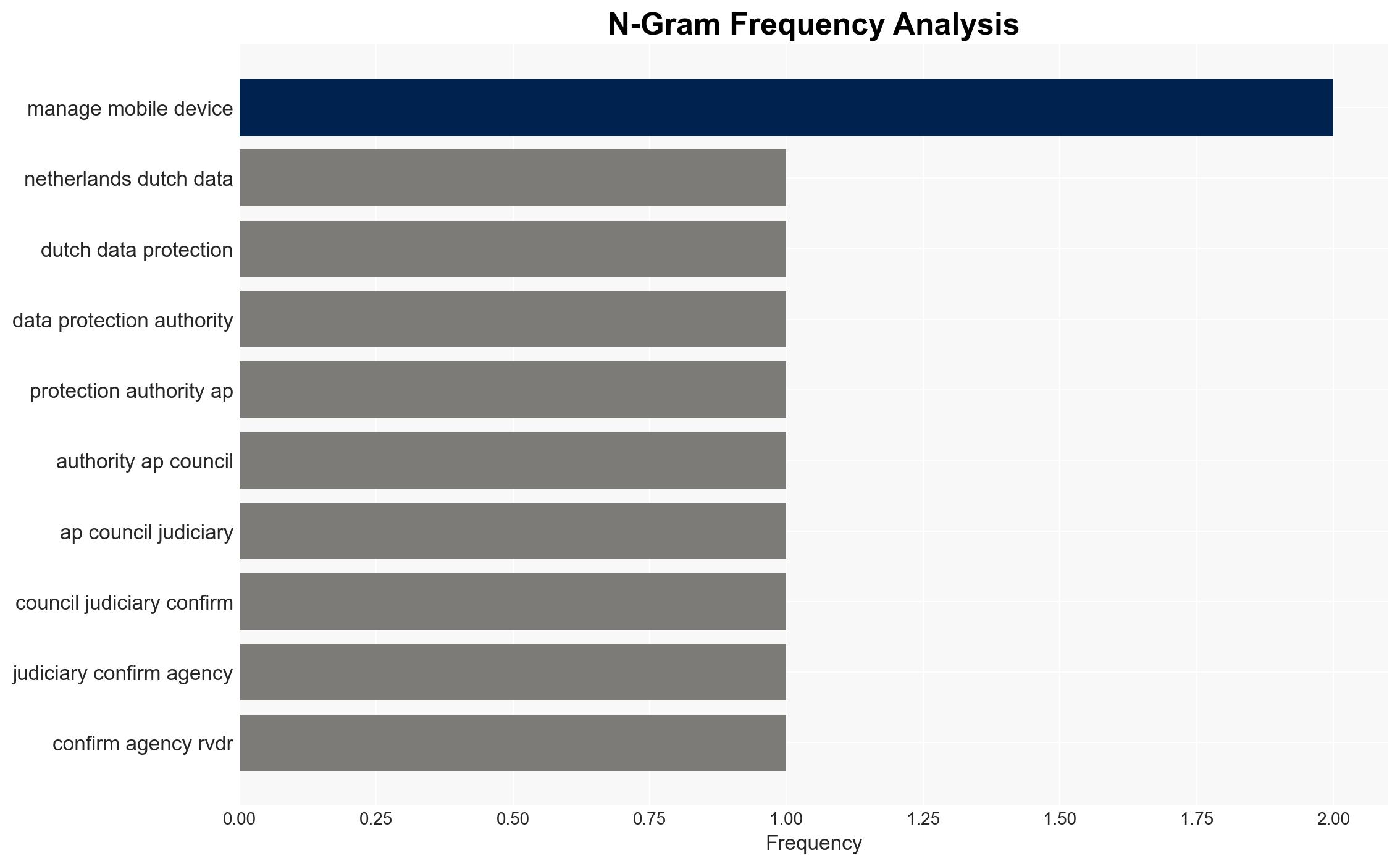
- Dutch Data Protection Authority (AP)
- Council for the Judiciary (Rvdr)
- National Cyber Security Center (NCSC)
- European Commission
- Valtori (Finland’s state ICT provider)
- Benjamin Harris, CEO of watchTowr
7. Thematic Tags
cybersecurity, zero-day vulnerabilities, governmental data breach, mobile device management, European cybersecurity, targeted cyber attacks
Structured Analytic Techniques Applied
- Adversarial Threat Simulation: Model and simulate actions of cyber adversaries to anticipate vulnerabilities and improve resilience.
- Indicators Development: Detect and monitor behavioral or technical anomalies across systems for early threat detection.
- Bayesian Scenario Modeling: Quantify uncertainty and predict cyberattack pathways using probabilistic inference.
Explore more:
Cybersecurity Briefs ·
Daily Summary ·
Support us