Dutch Data Protection Authority reveals it was targeted in Ivanti zero-day attacks leading to data breach
Published on: 2026-02-09
AI-powered OSINT brief from verified open sources. Automated NLP signal extraction with human verification. See our Methodology and Why WorldWideWatchers.
Intelligence Report: Dutch data watchdog snitches on itself after getting caught in Ivanti zero-day attacks
1. BLUF (Bottom Line Up Front)
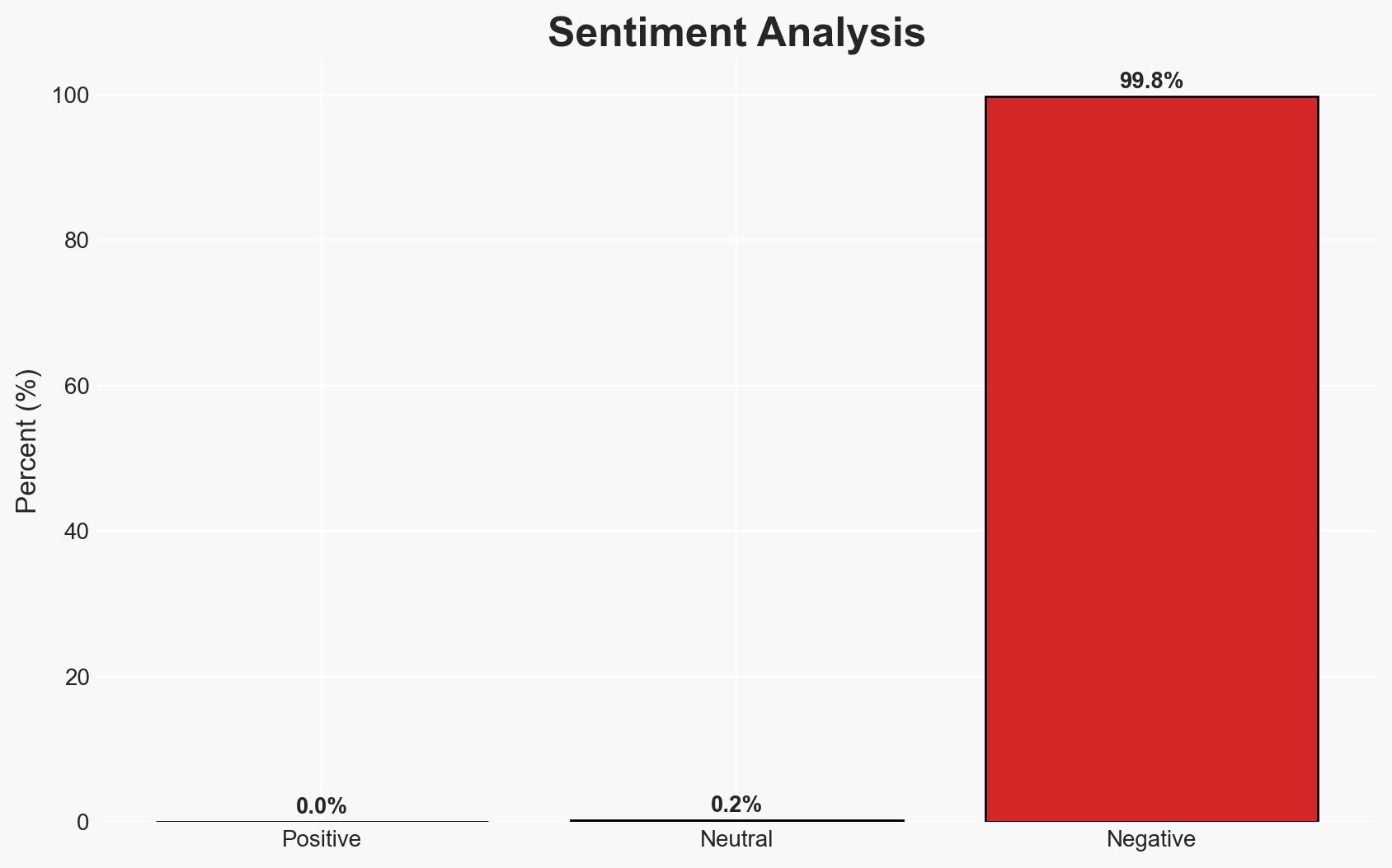
The Dutch Data Protection Authority (AP) and the Council for the Judiciary (RVDR) experienced a data breach due to exploitation of Ivanti zero-day vulnerabilities. The breach potentially exposed personal data of employees. The incident highlights vulnerabilities in internet-facing devices and raises concerns about broader systemic risks. Overall confidence in this assessment is moderate, given the ongoing investigations and limited public details.
2. Competing Hypotheses
- Hypothesis A: The breach was an opportunistic attack exploiting known vulnerabilities in Ivanti’s EPMM, targeting multiple organizations indiscriminately. Supporting evidence includes the rapid exploitation of the vulnerabilities and the nature of EPMM devices as attractive targets. Key uncertainties include the specific motives of the attackers and whether the attack was part of a broader campaign.
- Hypothesis B: The attack was a targeted operation specifically aimed at Dutch governmental bodies to access sensitive data. This hypothesis is supported by the high-value nature of the affected organizations. Contradicting evidence includes the lack of specific targeting indicators and the broader context of similar attacks on other organizations.
- Assessment: Hypothesis A is currently better supported due to the widespread nature of the vulnerability exploitation and the lack of specific evidence indicating targeted intent. Indicators that could shift this judgment include discovery of specific targeting patterns or communications from the attackers.
3. Key Assumptions and Red Flags
- Assumptions: The attackers exploited the vulnerabilities shortly after their disclosure; the breach was not detected immediately; affected organizations have taken appropriate initial response measures.
- Information Gaps: Details on the attackers’ identity and motives; the full extent of data accessed; specific security measures in place at the time of the breach.
- Bias & Deception Risks: Potential underreporting of the breach’s scale by affected organizations; reliance on vendor statements that may downplay the vulnerability’s impact.
4. Implications and Strategic Risks
The exploitation of Ivanti vulnerabilities underscores the persistent threat of zero-day attacks on critical infrastructure. The incident could prompt increased scrutiny of cybersecurity practices within governmental bodies and lead to policy changes.
- Political / Geopolitical: Potential diplomatic tensions if foreign state actors are implicated; increased pressure on government cybersecurity policies.
- Security / Counter-Terrorism: Heightened alert for similar attacks on critical infrastructure; potential for increased cyber defense collaboration.
- Cyber / Information Space: Increased focus on securing internet-facing devices; potential rise in cyber insurance claims and premiums.
- Economic / Social: Possible public concern over data privacy; economic impact on affected organizations due to reputational damage.
5. Recommendations and Outlook
- Immediate Actions (0–30 days): Conduct thorough forensic investigations; enhance monitoring of internet-facing devices; issue public communications to manage reputational impact.
- Medium-Term Posture (1–12 months): Strengthen cybersecurity frameworks; invest in threat intelligence capabilities; foster public-private partnerships for cyber resilience.
- Scenario Outlook:
- Best: Rapid containment and mitigation with no further breaches.
- Worst: Discovery of broader systemic vulnerabilities leading to additional breaches.
- Most-Likely: Incremental improvements in cybersecurity posture with ongoing threat of similar attacks.
6. Key Individuals and Entities
- Arno Rutte, Justice Secretary
- Eddie van Marum, Secretary for Kingdom Relations
- Dutch Data Protection Authority (AP)
- Council for the Judiciary (RVDR)
- National Cyber Security Centre Netherlands (NCSC-NL)
- US Cybersecurity and Infrastructure Security Agency (CISA)
- Ivanti
7. Thematic Tags
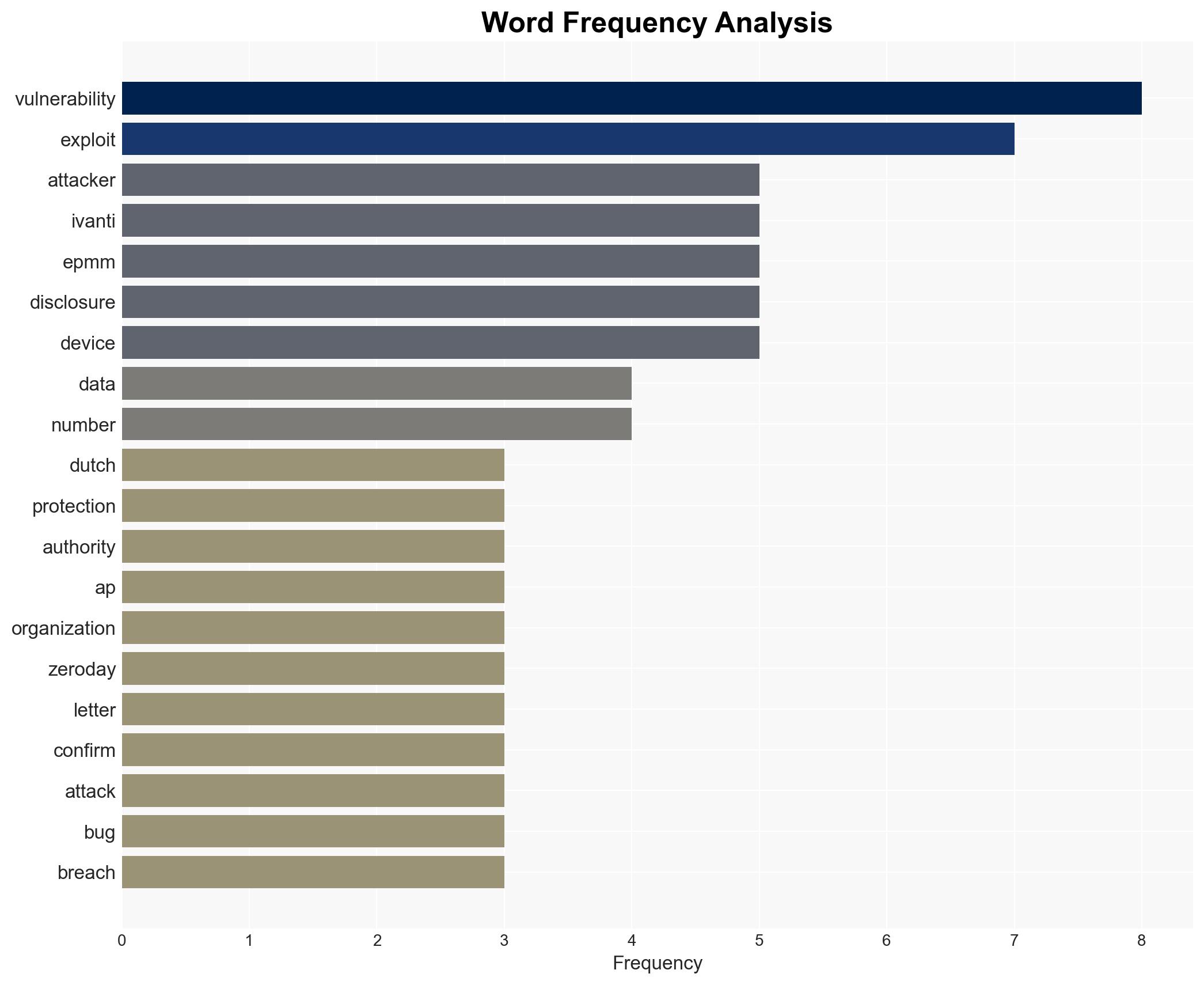
cybersecurity, data breach, zero-day vulnerabilities, governmental cybersecurity, internet-facing devices, public sector, threat intelligence
Structured Analytic Techniques Applied
- Adversarial Threat Simulation: Model and simulate actions of cyber adversaries to anticipate vulnerabilities and improve resilience.
- Indicators Development: Detect and monitor behavioral or technical anomalies across systems for early threat detection.
- Bayesian Scenario Modeling: Quantify uncertainty and predict cyberattack pathways using probabilistic inference.
Explore more:
Cybersecurity Briefs ·
Daily Summary ·
Support us