Dutch telecom giant Odido reveals data breach impacting 6.2 million customers’ personal information
Published on: 2026-02-13
AI-powered OSINT brief from verified open sources. Automated NLP signal extraction with human verification. See our Methodology and Why WorldWideWatchers.
Intelligence Report: Top Dutch telco Odido admits 62M customers caught in contact system caper
1. BLUF (Bottom Line Up Front)
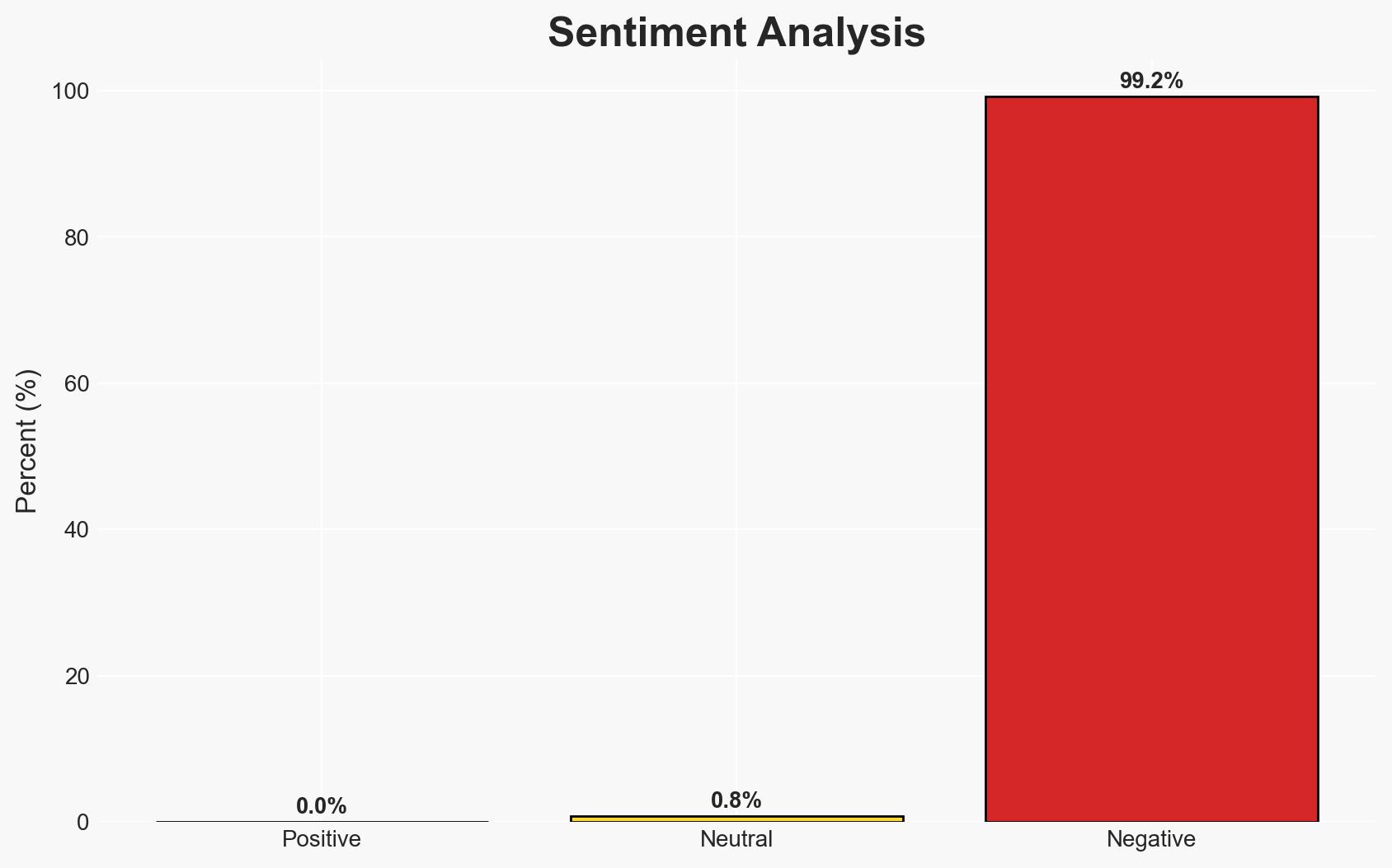
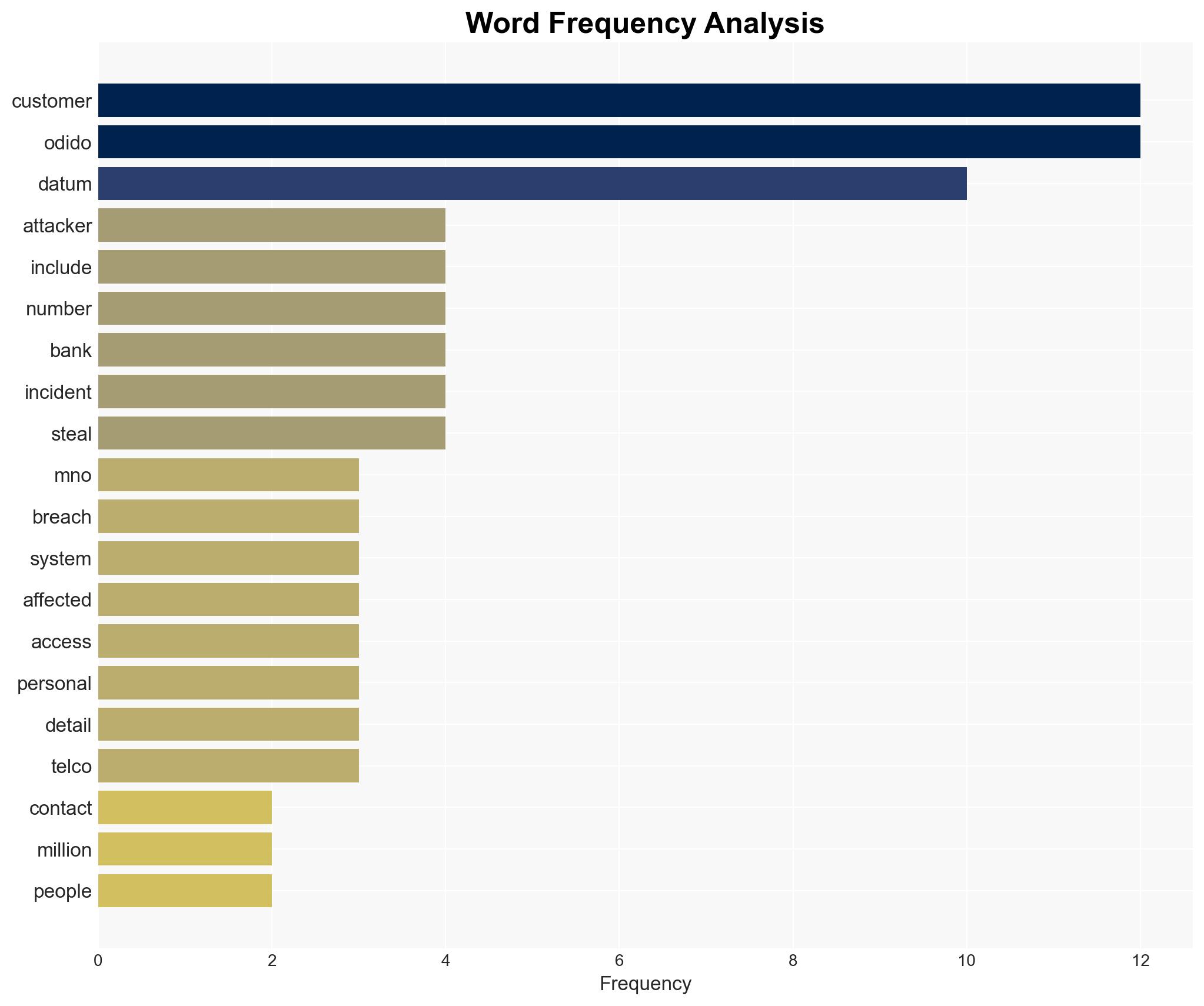
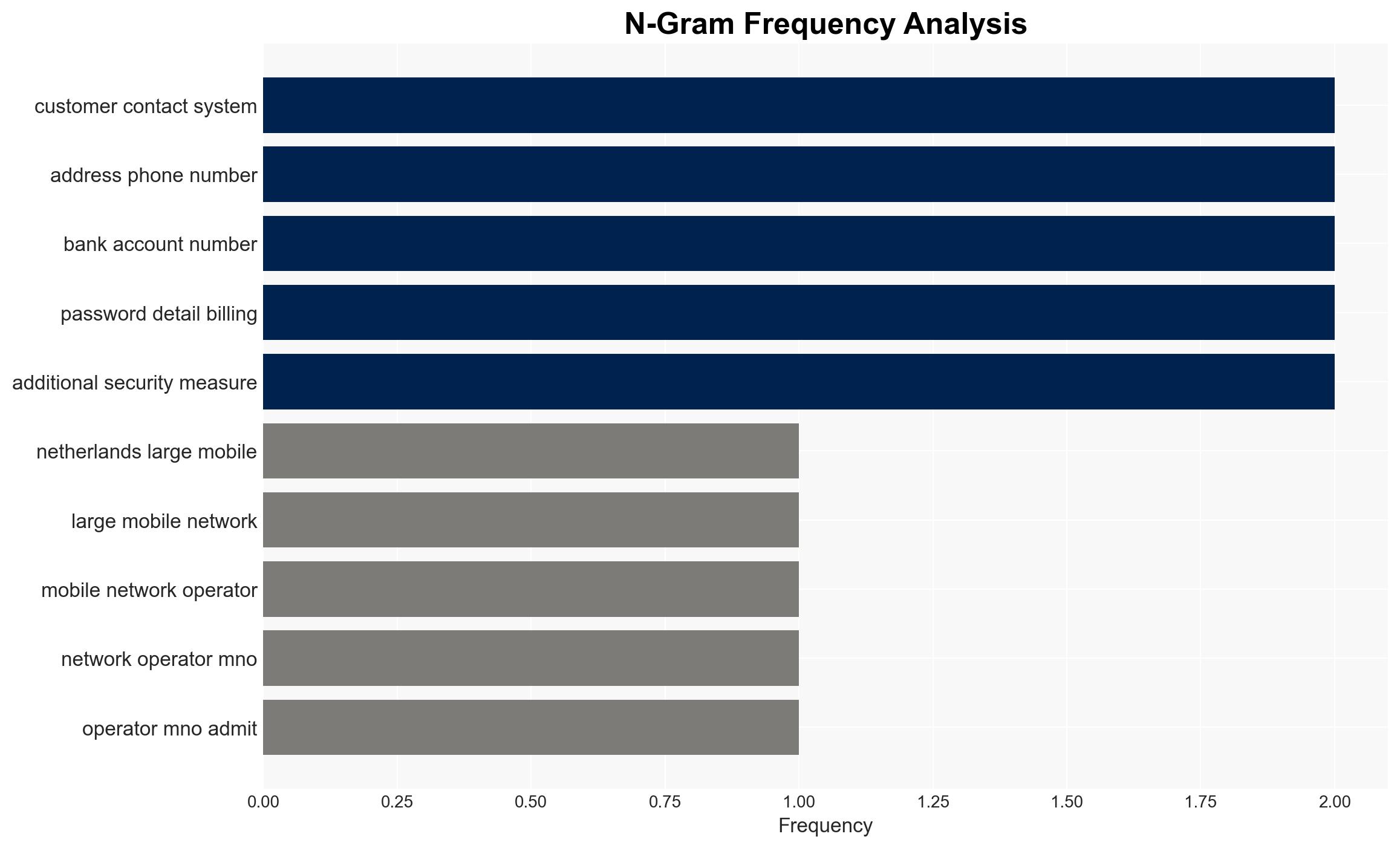
The breach of Odido’s customer contact system has potentially exposed personal data of approximately 6.2 million individuals, posing significant risks of identity theft and fraud. The most likely hypothesis is that this was a financially motivated cyberattack, given the nature of the data accessed. The overall confidence level in this assessment is moderate, due to existing information gaps regarding the attackers’ identity and intentions.
2. Competing Hypotheses
- Hypothesis A: The breach was conducted by financially motivated cybercriminals seeking to exploit personal data for fraud. This is supported by the type of data accessed, which includes bank account numbers and personal identifiers. However, the absence of immediate data publication introduces uncertainty.
- Hypothesis B: The breach was part of a broader espionage effort by a state-sponsored actor aiming to gather intelligence on Dutch citizens. This is less supported due to the lack of evidence indicating state actor involvement and the focus on financial data.
- Assessment: Hypothesis A is currently better supported due to the financial nature of the data accessed and the typical patterns of cybercriminal activity. Indicators that could shift this judgment include evidence of data being used for non-financial purposes or links to state-sponsored entities.
3. Key Assumptions and Red Flags
- Assumptions: The breach was detected and contained promptly; the attackers’ primary motive is financial gain; Odido’s additional security measures are effective.
- Information Gaps: Identity and motives of the attackers; whether the data has been sold or shared on the dark web; effectiveness of Odido’s response measures.
- Bias & Deception Risks: Potential underreporting by Odido to minimize reputational damage; reliance on Odido’s internal assessments without independent verification.
4. Implications and Strategic Risks
This breach could have cascading effects on consumer trust, regulatory scrutiny, and the broader telecom sector’s cybersecurity posture. The situation may evolve as more information about the breach and its exploitation emerges.
- Political / Geopolitical: Increased regulatory scrutiny and potential legislative action on data protection in the Netherlands.
- Security / Counter-Terrorism: Elevated risk of identity theft and fraud, potentially funding other illicit activities.
- Cyber / Information Space: Potential for increased cyberattacks targeting telecoms, exploiting perceived vulnerabilities.
- Economic / Social: Erosion of consumer trust in digital services, impacting customer retention and brand reputation.
5. Recommendations and Outlook
- Immediate Actions (0–30 days): Enhance monitoring of dark web for signs of data sale; increase public awareness campaigns on fraud prevention; verify the efficacy of implemented security measures.
- Medium-Term Posture (1–12 months): Strengthen partnerships with cybersecurity firms; invest in advanced threat detection capabilities; engage with regulators to shape data protection policies.
- Scenario Outlook:
- Best: Data remains unused, and Odido strengthens its cybersecurity, restoring customer trust.
- Worst: Data is exploited extensively, leading to widespread fraud and regulatory penalties.
- Most-Likely: Some data is used for fraud, prompting moderate regulatory action and increased security investments by Odido.
6. Key Individuals and Entities
- Søren Abildgaard, CEO of Odido
- Odido, Dutch mobile network operator
- Ben, subsidiary of Odido
- Simpel, subsidiary of Odido
7. Thematic Tags
cybersecurity, data breach, identity theft, telecom sector, regulatory compliance, fraud prevention, consumer protection
Structured Analytic Techniques Applied
- Adversarial Threat Simulation: Model and simulate actions of cyber adversaries to anticipate vulnerabilities and improve resilience.
- Indicators Development: Detect and monitor behavioral or technical anomalies across systems for early threat detection.
- Bayesian Scenario Modeling: Quantify uncertainty and predict cyberattack pathways using probabilistic inference.
- Network Influence Mapping: Map influence relationships to assess actor impact.
Explore more:
Cybersecurity Briefs ·
Daily Summary ·
Support us