Email breaches are the silent killers of business growth – Help Net Security
Published on: 2025-10-30
Intelligence Report: Email breaches are the silent killers of business growth – Help Net Security
1. BLUF (Bottom Line Up Front)
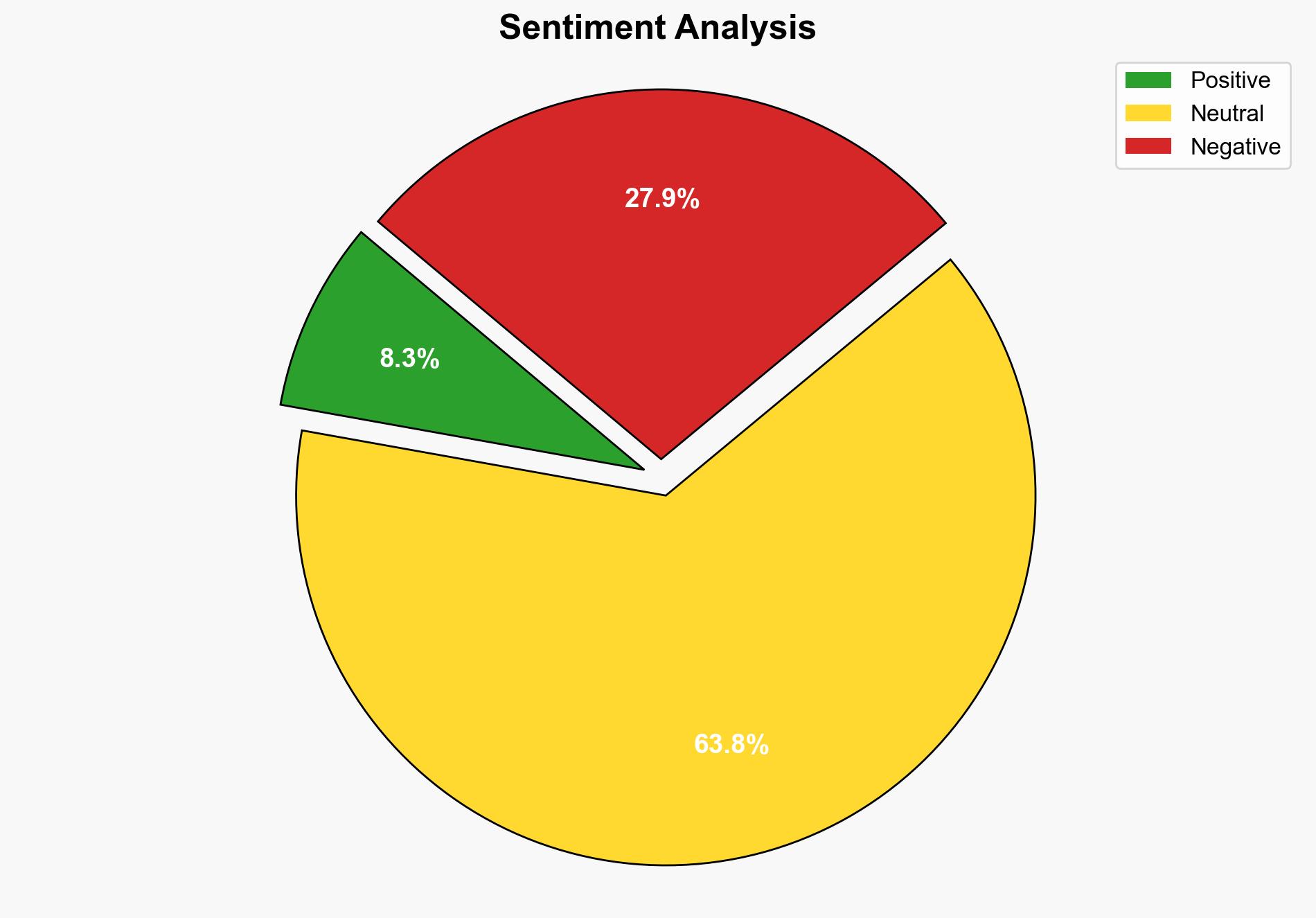
Email breaches pose a significant threat to business growth by facilitating ransomware attacks, data theft, and reputational damage. The hypothesis that email breaches are a primary vector for ransomware is better supported. Confidence level: Moderate. Recommended action: Enhance email security measures, focusing on rapid detection and response capabilities.
2. Competing Hypotheses
1. **Hypothesis A**: Email breaches are primarily responsible for enabling ransomware attacks and subsequent business disruptions.
2. **Hypothesis B**: Email breaches are a symptom of broader cybersecurity vulnerabilities, with ransomware attacks driven by multiple factors beyond email security.
Using Analysis of Competing Hypotheses (ACH 2.0), Hypothesis A is more supported due to the direct correlation between email breaches and ransomware incidents reported. The data indicates that slow detection of email breaches increases ransomware risk, suggesting a causal relationship.
3. Key Assumptions and Red Flags
– **Assumptions**:
– Email breaches are the initial vector for most ransomware attacks.
– Organizations lack adequate detection and response capabilities.
– **Red Flags**:
– Potential underreporting of breaches due to reputational concerns.
– Over-reliance on email security tools without addressing broader cybersecurity frameworks.
4. Implications and Strategic Risks
– **Economic**: Increased costs for breach recovery and potential loss of business.
– **Cyber**: Escalation of ransomware attacks leading to more sophisticated cyber threats.
– **Geopolitical**: Potential exploitation by state actors using email breaches as a low-cost, high-impact attack vector.
– **Psychological**: Erosion of trust among customers and partners, impacting long-term business relationships.
5. Recommendations and Outlook
- Implement advanced email filtering and anomaly detection systems to reduce breach detection time.
- Conduct regular cybersecurity training for employees to recognize and report suspicious emails.
- Develop automated incident response protocols to swiftly contain breaches.
- Scenario Projections:
- Best Case: Rapid adoption of enhanced security measures reduces breach incidents by 50% within a year.
- Worst Case: Continued slow detection leads to a significant increase in ransomware attacks, causing severe business disruptions.
- Most Likely: Incremental improvements in detection and response reduce breach impact but do not eliminate the threat entirely.
6. Key Individuals and Entities
– Neal Bradbury, CPO of Barracuda, highlighted the challenges of detecting advanced evasion techniques in email threats.
7. Thematic Tags
national security threats, cybersecurity, counter-terrorism, regional focus