Emergency Patch Released for Microsoft Office Zero-Day Exploit Bypassing Document Security Measures
Published on: 2026-01-29
AI-powered OSINT brief from verified open sources. Automated NLP signal extraction with human verification. See our Methodology and Why WorldWideWatchers.
Intelligence Report: Microsoft Office zero-day lets malicious documents slip past security checks
1. BLUF (Bottom Line Up Front)
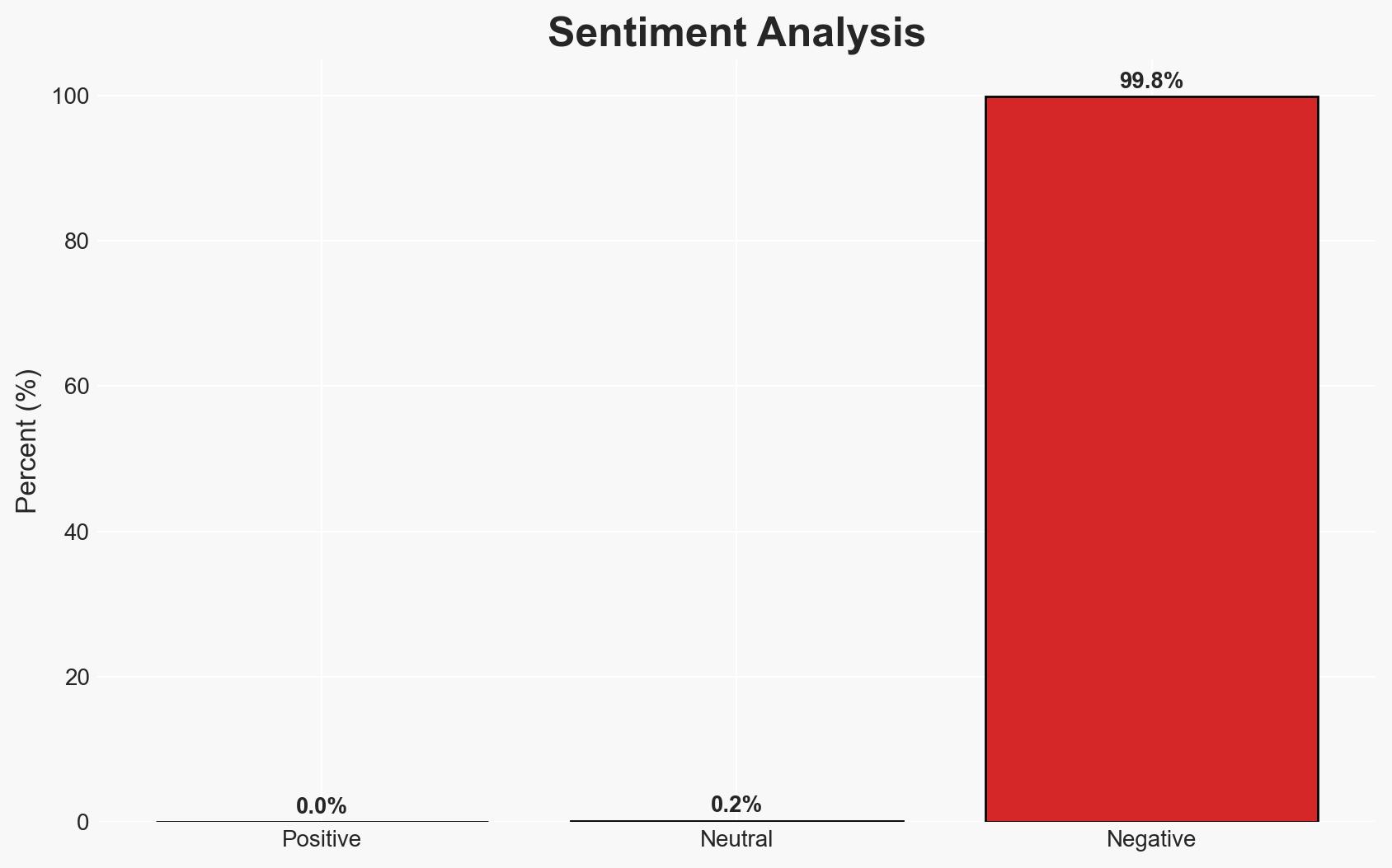
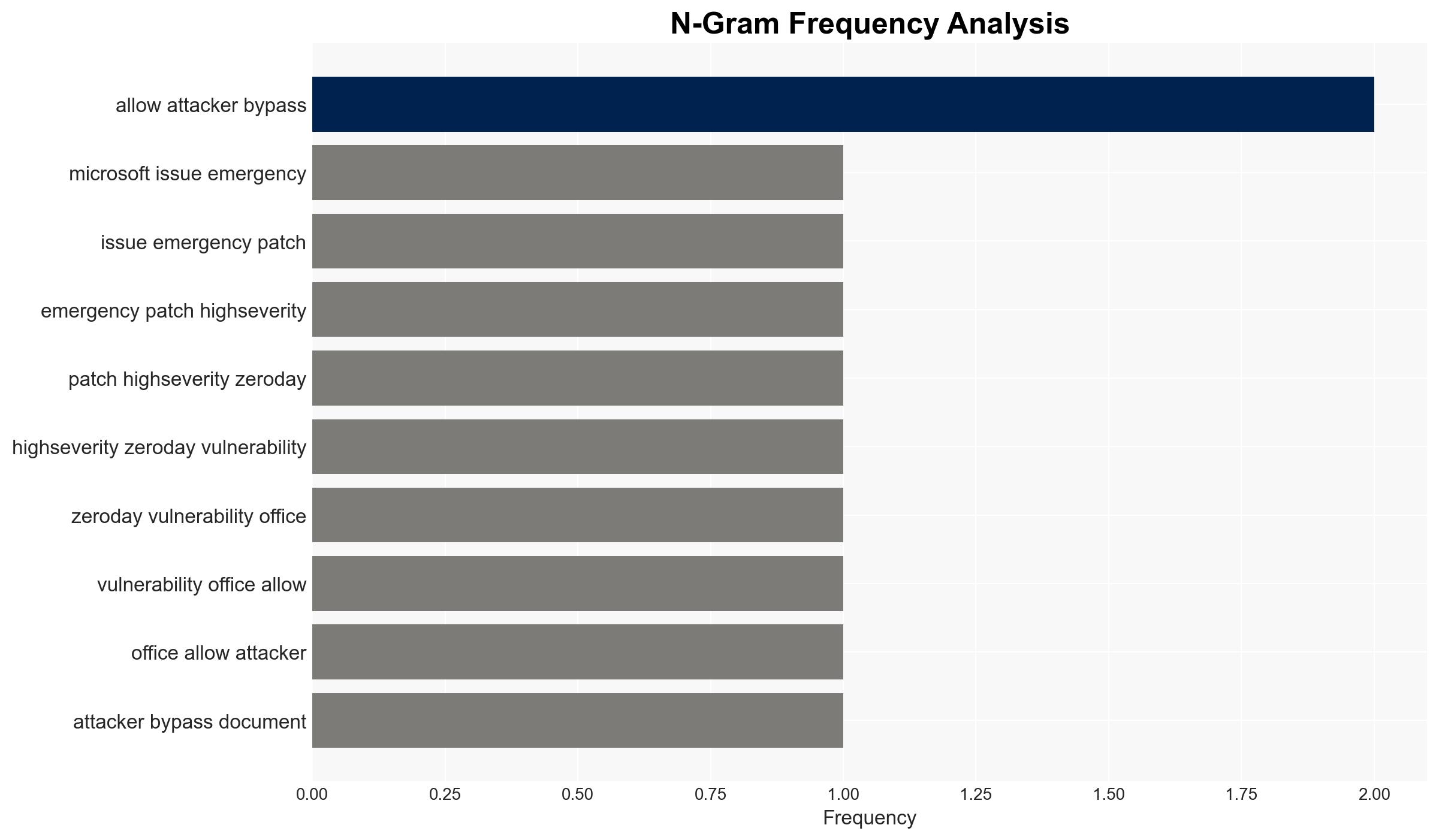
A high-severity zero-day vulnerability in Microsoft Office, identified as CVE-2026-21509, is actively being exploited, allowing attackers to bypass document security checks. This affects multiple Office versions, posing significant risks to users who have not applied the emergency patch. The most likely hypothesis is that cybercriminals are leveraging this vulnerability for widespread attacks, with moderate confidence in this assessment due to the availability of exploit code and ongoing exploitation reports.
2. Competing Hypotheses
- Hypothesis A: Cybercriminals are exploiting the zero-day vulnerability primarily for financial gain through widespread phishing campaigns. This is supported by the public availability of exploit code and the nature of the vulnerability, which is conducive to mass exploitation. However, there is uncertainty about the scale and specific targets of these campaigns.
- Hypothesis B: State-sponsored actors are exploiting the vulnerability for espionage purposes, targeting specific high-value entities. While plausible, there is limited direct evidence supporting this, and the widespread nature of the vulnerability’s exploitation suggests a broader, less targeted approach.
- Assessment: Hypothesis A is currently better supported due to the public availability of exploit code and reports of active exploitation in the wild. Indicators such as targeted phishing campaigns or specific geopolitical tensions could shift this judgment towards Hypothesis B.
3. Key Assumptions and Red Flags
- Assumptions: The vulnerability is being actively exploited; the emergency patch effectively mitigates the risk; cybercriminals prioritize financial over espionage objectives.
- Information Gaps: Specific details on the actors exploiting the vulnerability and their targets; comprehensive data on the exploitation scale and geographic distribution.
- Bias & Deception Risks: Potential bias in overestimating the financial motivation due to the commonality of such attacks; deception risk from actors using the vulnerability to mask more sophisticated operations.
4. Implications and Strategic Risks
This vulnerability could lead to increased cyber-attacks, affecting both individual users and organizations, potentially disrupting operations and causing financial losses. Over time, this could lead to heightened scrutiny of software security practices and increased demand for cybersecurity solutions.
- Political / Geopolitical: Potential for increased tensions if state actors are implicated; could influence international cybersecurity policy discussions.
- Security / Counter-Terrorism: Increased risk of cyber-attacks on critical infrastructure if exploited by malicious actors.
- Cyber / Information Space: Heightened awareness and potential increase in cybersecurity measures; risk of misinformation if the vulnerability is used in disinformation campaigns.
- Economic / Social: Potential economic impact from disrupted business operations; increased public concern over digital security.
5. Recommendations and Outlook
- Immediate Actions (0–30 days): Urgently apply the Microsoft patch across all affected systems; increase monitoring for phishing campaigns; educate users on recognizing suspicious documents.
- Medium-Term Posture (1–12 months): Develop partnerships with cybersecurity firms for threat intelligence sharing; enhance internal cybersecurity training and awareness programs.
- Scenario Outlook:
- Best: Rapid patch adoption minimizes impact, and no significant breaches occur.
- Worst: Major breaches occur before patch adoption, leading to significant financial and reputational damage.
- Most-Likely: Moderate exploitation continues, with sporadic breaches as organizations gradually apply patches.
6. Key Individuals and Entities
- Microsoft Corporation
- Cybercriminal groups (not specifically identifiable from open sources in this snippet)
- Potential state-sponsored actors (not clearly identifiable from open sources in this snippet)
7. Thematic Tags
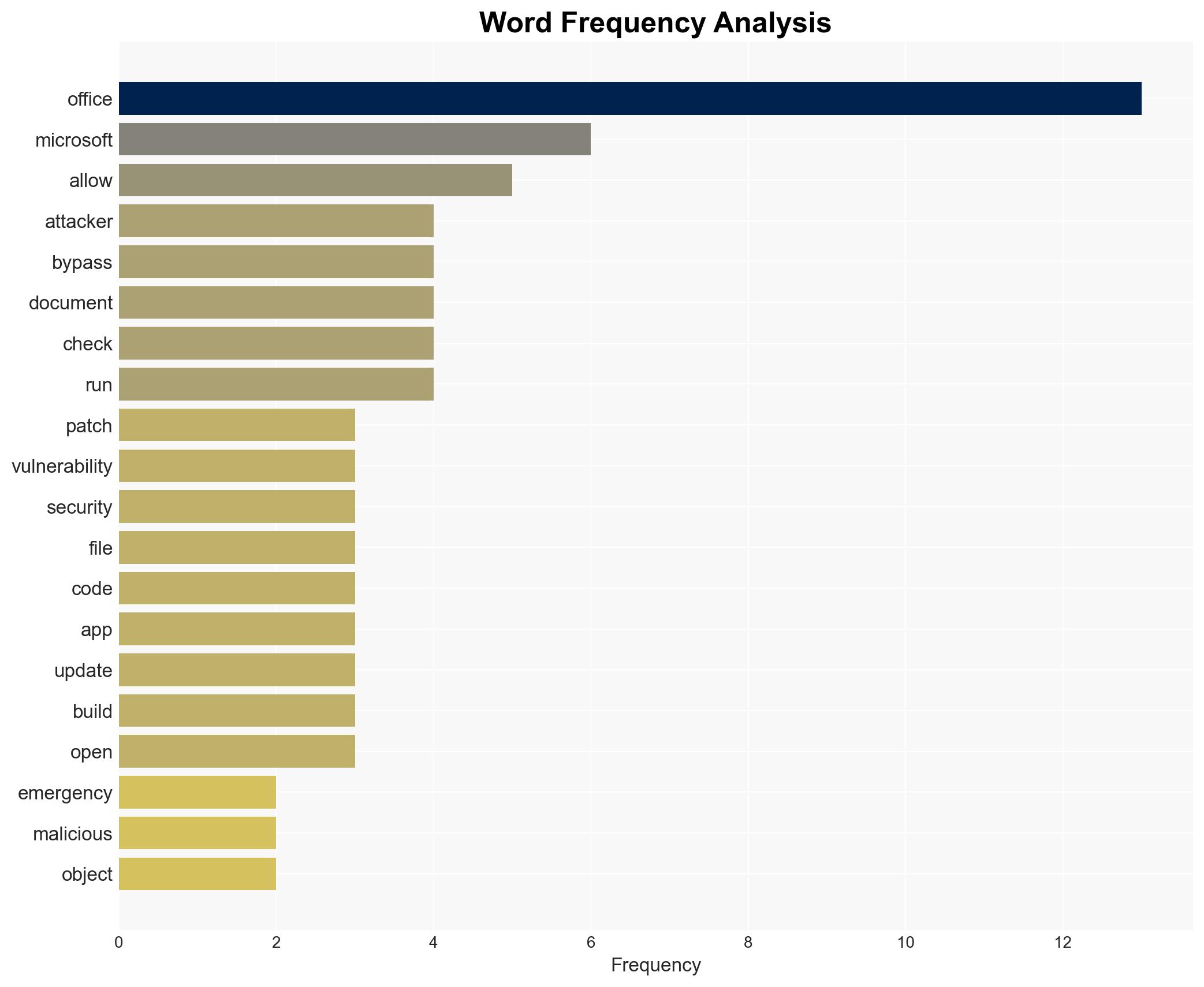
cybersecurity, zero-day vulnerability, Microsoft Office, phishing, cybercrime, software patching, information security
Structured Analytic Techniques Applied
- Adversarial Threat Simulation: Model and simulate actions of cyber adversaries to anticipate vulnerabilities and improve resilience.
- Indicators Development: Detect and monitor behavioral or technical anomalies across systems for early threat detection.
- Bayesian Scenario Modeling: Forecast futures under uncertainty via probabilistic logic.
Explore more:
Cybersecurity Briefs ·
Daily Summary ·
Support us