Emerging Technologies Enhance ISIL’s Threat to Global Security, UN Counter-Terrorism Chief Informs Security C…
Published on: 2026-02-05
AI-powered OSINT brief from verified open sources. Automated NLP signal extraction with human verification. See our Methodology and Why WorldWideWatchers.
Intelligence Report: Terrorists’ Use of Emerging Technologies Poses Evolving Threat to International Peace Stability Acting UN Counter-Terrorism Chief Warns Security Council
1. BLUF (Bottom Line Up Front)
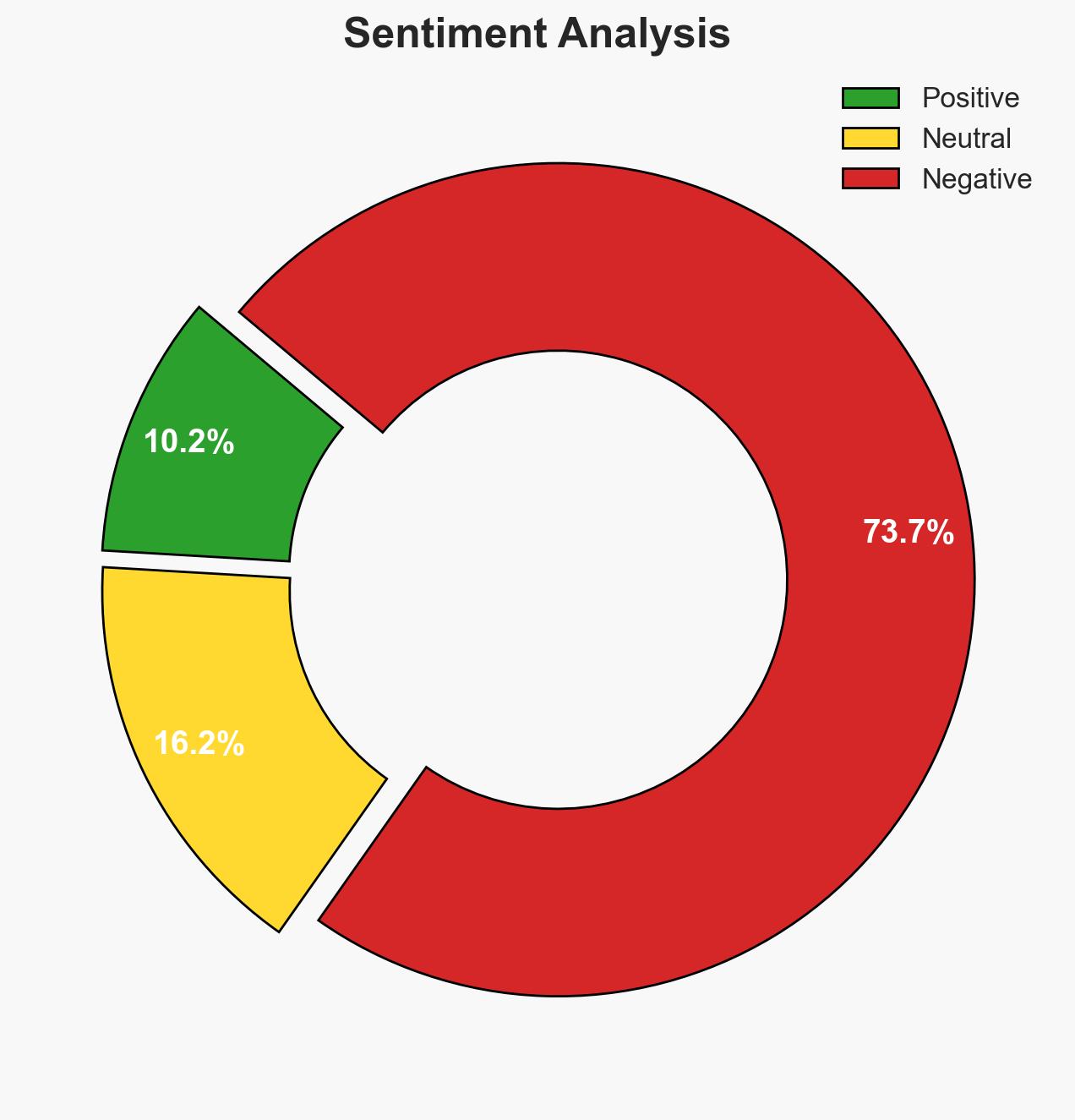
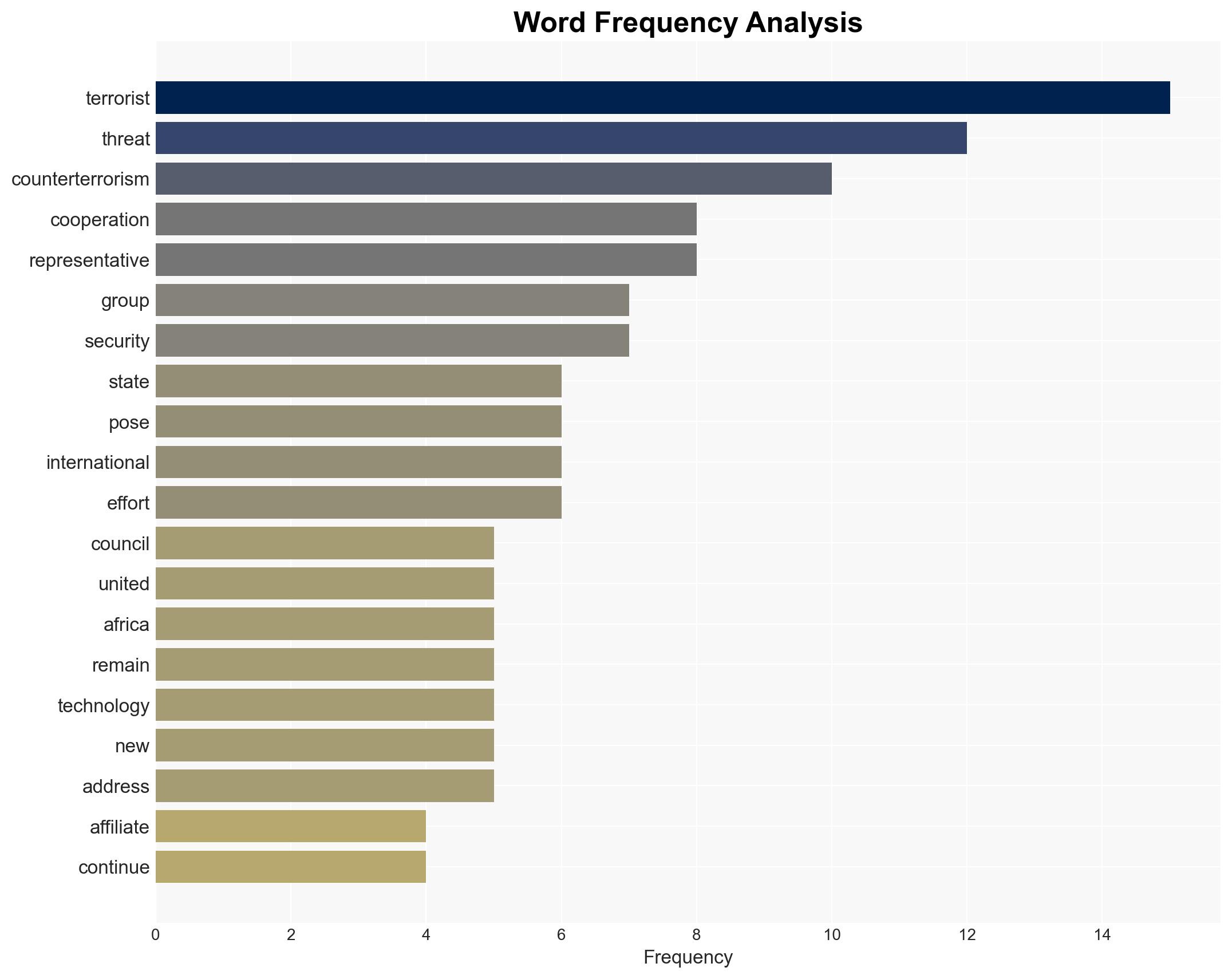
The use of emerging technologies by ISIL/Da’esh and its affiliates, including cryptocurrencies, cybertools, and AI, poses a significant and evolving threat to international peace and security. This threat is particularly pronounced in regions such as West Africa and the Sahel. The current assessment supports the hypothesis that these groups are leveraging technology to enhance their operational capabilities and resilience. Overall confidence in this judgment is moderate, given the complexity and evolving nature of the threat landscape.
2. Competing Hypotheses
- Hypothesis A: ISIL/Da’esh and affiliates are effectively using emerging technologies to enhance their operational capabilities, allowing them to adapt and expand despite counter-terrorism efforts. Evidence includes reported use of cryptocurrencies, AI, and cybertools. Key uncertainties involve the extent of technological sophistication and integration.
- Hypothesis B: The reported use of emerging technologies by ISIL/Da’esh is overstated, and their impact on operational capabilities is limited. This hypothesis is less supported due to consistent reporting of technological adoption and adaptation by these groups.
- Assessment: Hypothesis A is currently better supported due to multiple reports of technological adaptation by ISIL/Da’esh. Indicators such as increased cyber activity or technological sophistication could further support this judgment.
3. Key Assumptions and Red Flags
- Assumptions: ISIL/Da’esh has access to necessary technological expertise; international counter-terrorism efforts remain fragmented; regional instability facilitates terrorist expansion.
- Information Gaps: Detailed intelligence on the specific technologies and platforms used by ISIL/Da’esh; the extent of their technological capabilities.
- Bias & Deception Risks: Potential over-reliance on open-source reporting; risk of underestimating ISIL/Da’esh’s technological sophistication due to cognitive biases.
4. Implications and Strategic Risks
The continued adaptation of ISIL/Da’esh using emerging technologies could lead to increased operational effectiveness and resilience, complicating counter-terrorism efforts globally.
- Political / Geopolitical: Potential for increased regional instability in Africa and the Middle East, straining international diplomatic relations.
- Security / Counter-Terrorism: Enhanced threat environment requiring adaptive and coordinated counter-terrorism strategies.
- Cyber / Information Space: Increased risk of cyber-attacks and propaganda dissemination, challenging information security and public perception.
- Economic / Social: Potential disruption to local economies and social cohesion, particularly in conflict-prone regions.
5. Recommendations and Outlook
- Immediate Actions (0–30 days): Enhance monitoring of terrorist use of technology; strengthen intelligence sharing among international partners.
- Medium-Term Posture (1–12 months): Develop resilience measures against cyber threats; foster regional partnerships to address technological and security challenges.
- Scenario Outlook:
- Best: Effective international cooperation mitigates technological threats.
- Worst: ISIL/Da’esh significantly enhances capabilities, leading to increased attacks.
- Most-Likely: Gradual increase in technological sophistication, requiring adaptive counter-terrorism measures.
6. Key Individuals and Entities
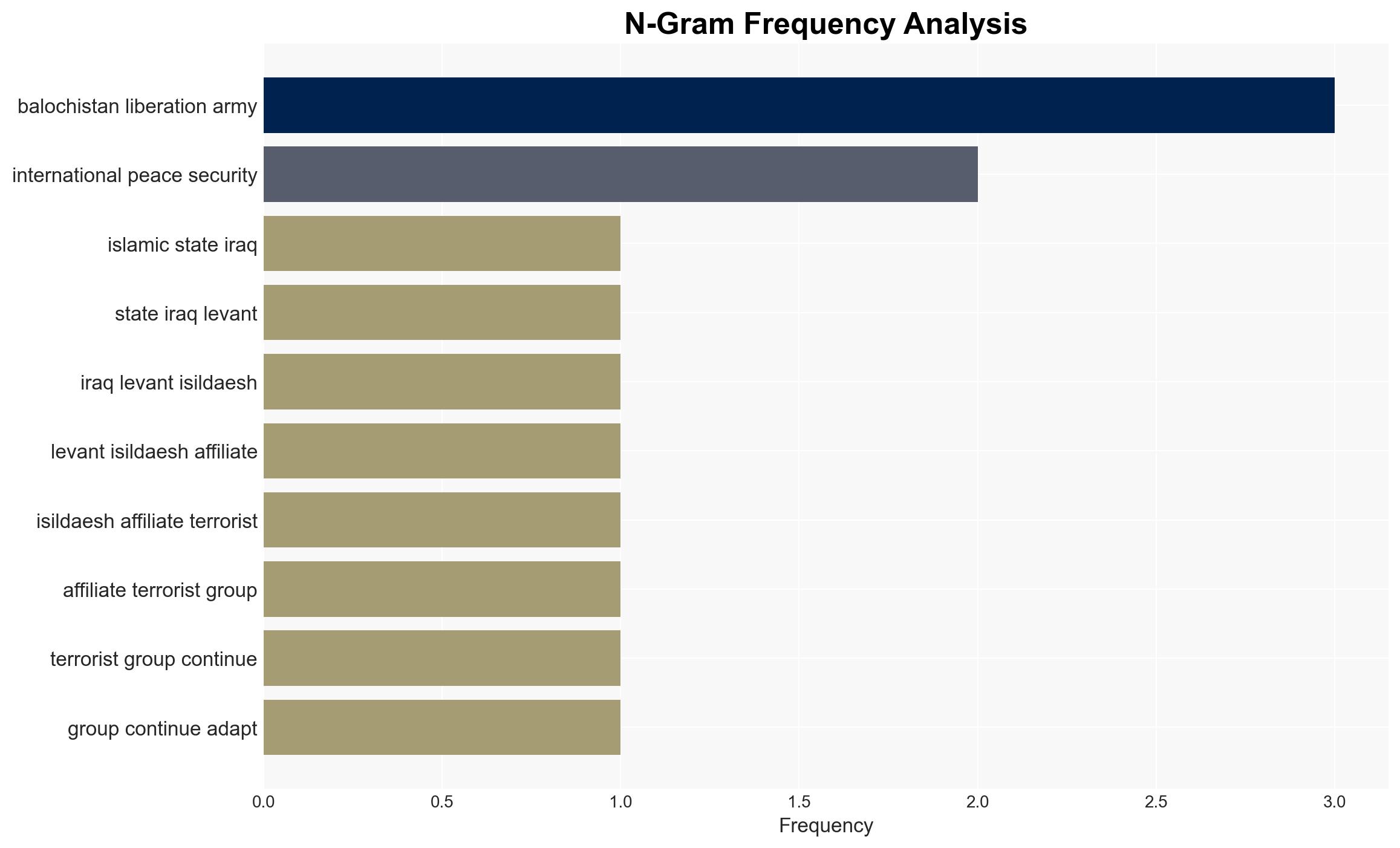
- Islamic State in Iraq and the Levant (ISIL/Da’esh)
- Islamic State West Africa Province
- ISIL-Khorasan (ISIL-K)
- Alexandre Zouev, Acting Under-Secretary-General of the United Nations Office of Counter-Terrorism
- Natalia Gherman, Executive Director of the Counter-Terrorism Committee Executive Directorate
7. Thematic Tags
Counter-Terrorism, emerging technologies, cyber threats, regional instability, international cooperation, ISIL/Da’esh, security strategy
Structured Analytic Techniques Applied
- ACH 2.0: Reconstruct likely threat actor intentions via hypothesis testing and structured refutation.
- Indicators Development: Track radicalization signals and propaganda patterns to anticipate operational planning.
- Narrative Pattern Analysis: Analyze spread/adaptation of ideological narratives for recruitment/incitement signals.
Explore more:
Counter-Terrorism Briefs ·
Daily Summary ·
Support us