Employees keep finding new ways around company access controls – Help Net Security
Published on: 2025-11-03
Intelligence Report: Employees keep finding new ways around company access controls – Help Net Security
1. BLUF (Bottom Line Up Front)
The most supported hypothesis is that the rapid adoption of AI and SaaS tools, combined with inadequate oversight and policy enforcement, is leading to significant security vulnerabilities within organizations. Confidence in this assessment is moderate due to the complexity of the issue and the potential for rapid technological changes. It is recommended that organizations enhance their oversight mechanisms and update their security policies to address these emerging threats.
2. Competing Hypotheses
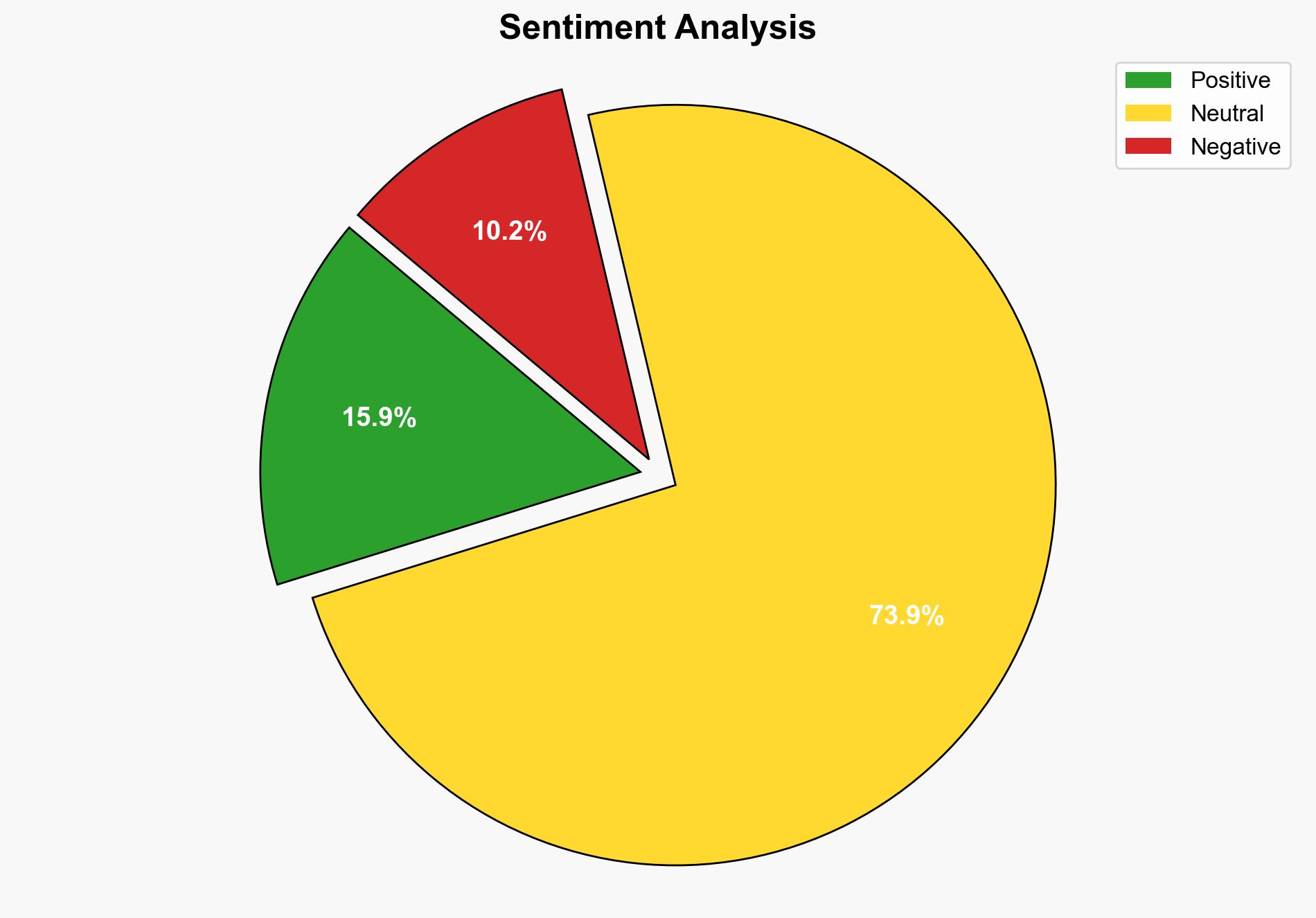
1. **Hypothesis A**: The primary driver of security breaches is the rapid adoption of AI and SaaS tools without adequate oversight and policy enforcement. Employees are using unauthorized tools, leading to shadow IT and increased vulnerabilities.
2. **Hypothesis B**: The main issue is the inherent weaknesses in existing security measures, such as password management and device control, which are being exploited by employees regardless of AI and SaaS adoption.
Using the Analysis of Competing Hypotheses (ACH) 2.0, Hypothesis A is better supported due to the evidence of widespread use of unauthorized tools and the lack of comprehensive AI policies. Hypothesis B is less supported as it does not fully account for the specific challenges posed by new technologies.
3. Key Assumptions and Red Flags
– **Assumptions**: It is assumed that employees intentionally bypass controls due to lack of awareness or convenience, rather than malicious intent. It is also assumed that organizations have not yet fully adapted their policies to the rapid technological changes.
– **Red Flags**: The report lacks specific data on the extent of AI and SaaS usage and the effectiveness of current security policies. There is also a potential bias towards blaming technology rather than examining organizational culture or training.
4. Implications and Strategic Risks
The continued use of unauthorized tools and weak security measures could lead to significant data breaches, financial losses, and reputational damage. The gap between technology adoption and policy enforcement may widen, increasing the risk of cyberattacks. Organizations may face regulatory penalties if they fail to comply with emerging cybersecurity standards.
5. Recommendations and Outlook
- Implement comprehensive AI and SaaS governance frameworks to monitor and manage tool usage.
- Enhance employee training on cybersecurity policies and the risks of unauthorized tool use.
- Adopt advanced identity and access management solutions, such as passkeys and biometric authentication, to strengthen security.
- Scenario Projections:
- Best Case: Organizations successfully integrate new technologies with robust security policies, reducing vulnerabilities.
- Worst Case: Continued policy gaps lead to major data breaches and regulatory penalties.
- Most Likely: Incremental improvements in security policies and technology adoption, with ongoing challenges in managing shadow IT.
6. Key Individuals and Entities
Brian Morris, CISO of Gray Medium, is mentioned in the context of advocating for passkey adoption.
7. Thematic Tags
cybersecurity, technology adoption, organizational policy, data breaches, AI governance