Endesa Investigates Data Breach After Cybercriminal Claims Theft of Personal Information from 20 Million Cust…
Published on: 2026-01-14
AI-powered OSINT brief from verified open sources. Automated NLP signal extraction with human verification. See our Methodology and Why WorldWideWatchers.
Intelligence Report: Spanish power giant sparks breach probe amid claims of massive data grab
1. BLUF (Bottom Line Up Front)
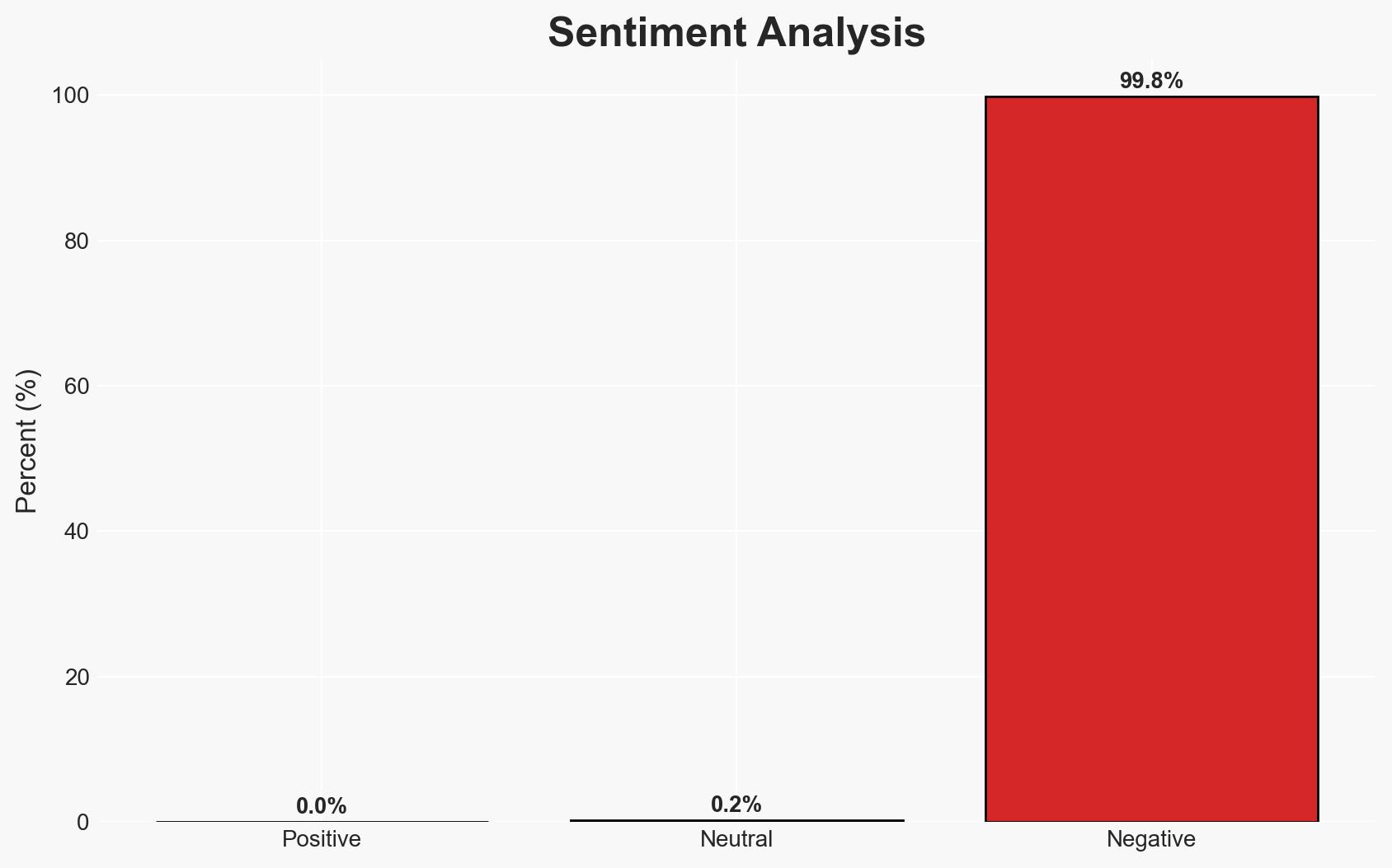
The data breach at Endesa, Spain’s largest electricity utility, potentially exposed personal information of over 20 million individuals. The most likely hypothesis is that the breach resulted from unauthorized access to a commercial platform, with moderate confidence in this assessment. Affected parties include Endesa customers and potentially the broader Enel Group. The overall confidence level in this judgment is moderate due to ongoing investigations and limited public disclosures.
2. Competing Hypotheses
- Hypothesis A: The breach was a result of unauthorized access to Endesa’s commercial platform, exploiting a software flaw or stolen credentials. Supporting evidence includes Endesa’s acknowledgment of unauthorized access and the immediate containment actions. Contradicting evidence is the lack of detailed disclosure on the breach mechanism.
- Hypothesis B: The breach claims are exaggerated by cybercriminals to pressure Endesa, with the actual data exposure being less severe. Supporting evidence includes the common practice of cybercriminals inflating claims. Contradicting evidence is Endesa’s notification to the data protection authority, indicating a significant breach.
- Assessment: Hypothesis A is currently better supported due to Endesa’s official statements and actions taken. Future forensic findings or disclosures could shift this judgment.
3. Key Assumptions and Red Flags
- Assumptions: Endesa’s internal investigation will provide accurate findings; the breach was not state-sponsored; the data protection measures post-breach are effective.
- Information Gaps: Specific details on how the breach occurred and the exact volume of data compromised.
- Bias & Deception Risks: Potential bias in Endesa’s public communications to minimize reputational damage; possible exaggeration by the cybercriminals to increase leverage.
4. Implications and Strategic Risks
This breach could lead to increased scrutiny of Endesa’s cybersecurity measures and broader implications for the energy sector’s digital security. The situation may evolve with further disclosures or additional breaches.
- Political / Geopolitical: Potential regulatory pressures on energy utilities to enhance cybersecurity standards.
- Security / Counter-Terrorism: Increased risk of similar attacks on critical infrastructure, necessitating heightened vigilance.
- Cyber / Information Space: Potential for increased phishing and social engineering attacks targeting affected individuals.
- Economic / Social: Possible financial losses for Endesa and affected customers, impacting trust and customer relations.
5. Recommendations and Outlook
- Immediate Actions (0–30 days): Enhance monitoring of affected systems, increase customer awareness on phishing risks, and collaborate with cybersecurity firms for forensic analysis.
- Medium-Term Posture (1–12 months): Strengthen cybersecurity infrastructure, conduct regular security audits, and engage in public-private partnerships for threat intelligence sharing.
- Scenario Outlook:
- Best: Breach impact is contained with minimal data misuse, leading to improved cybersecurity measures.
- Worst: Further breaches occur, leading to significant financial and reputational damage.
- Most-Likely: Investigation reveals moderate data exposure, prompting regulatory action and improved security protocols.
6. Key Individuals and Entities
- Endesa
- Enel Group
- Agencia Española de Protección de Datos
- Cybercriminal using the handle “Spain”
7. Thematic Tags
cybersecurity, data breach, energy sector, regulatory compliance, information security, critical infrastructure, cybercrime
Structured Analytic Techniques Applied
- Adversarial Threat Simulation: Model and simulate actions of cyber adversaries to anticipate vulnerabilities and improve resilience.
- Indicators Development: Detect and monitor behavioral or technical anomalies across systems for early threat detection.
- Bayesian Scenario Modeling: Quantify uncertainty and predict cyberattack pathways using probabilistic inference.
Explore more:
Cybersecurity Briefs ·
Daily Summary ·
Support us