Energy Sector Faces Phishing Threats from Sophisticated AiTM Campaign Targeting Enterprise Accounts
Published on: 2026-01-22
AI-powered OSINT brief from verified open sources. Automated NLP signal extraction with human verification. See our Methodology and Why WorldWideWatchers.
Intelligence Report: Energy sector orgs targeted with AiTM phishing campaign
1. BLUF (Bottom Line Up Front)
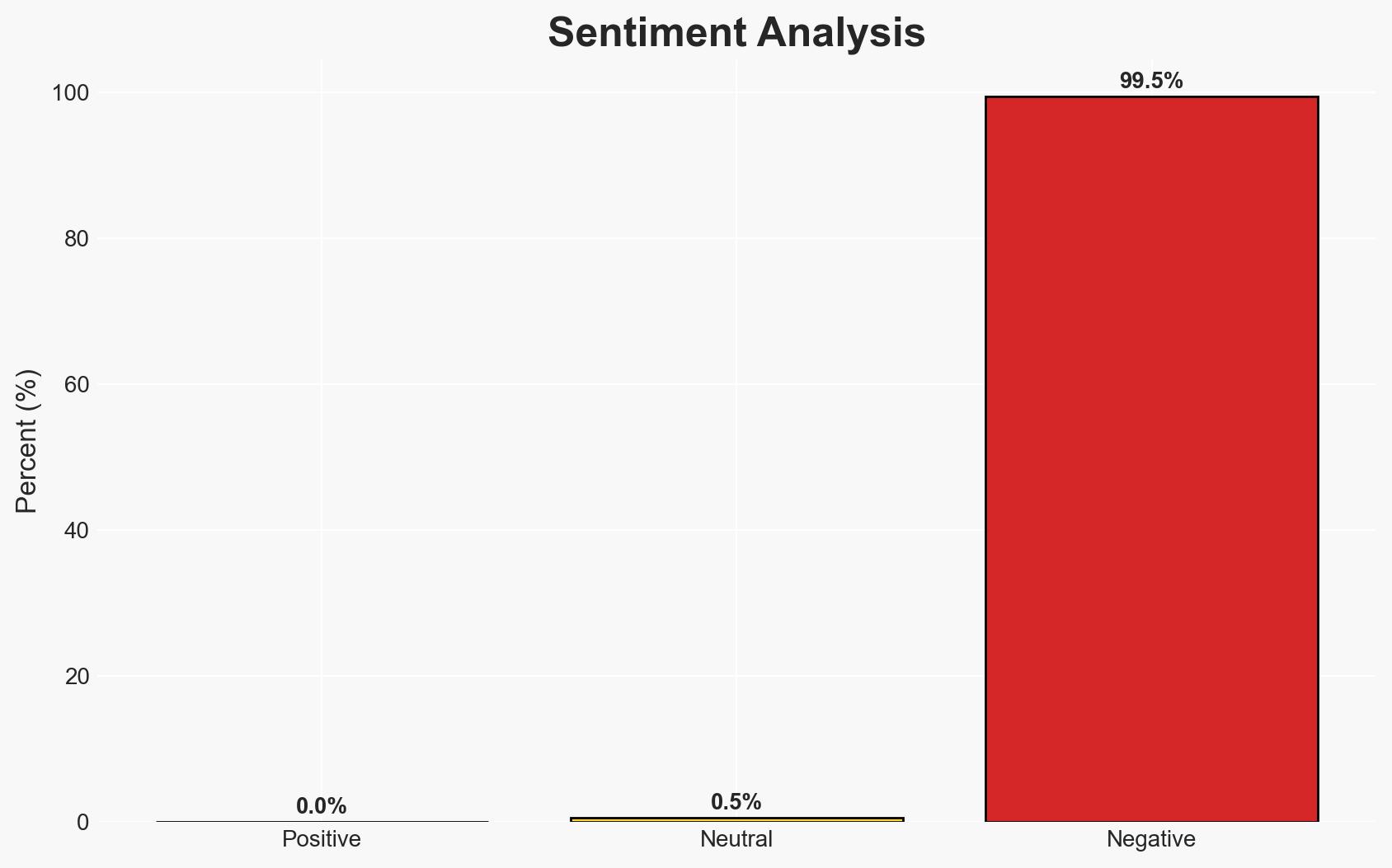
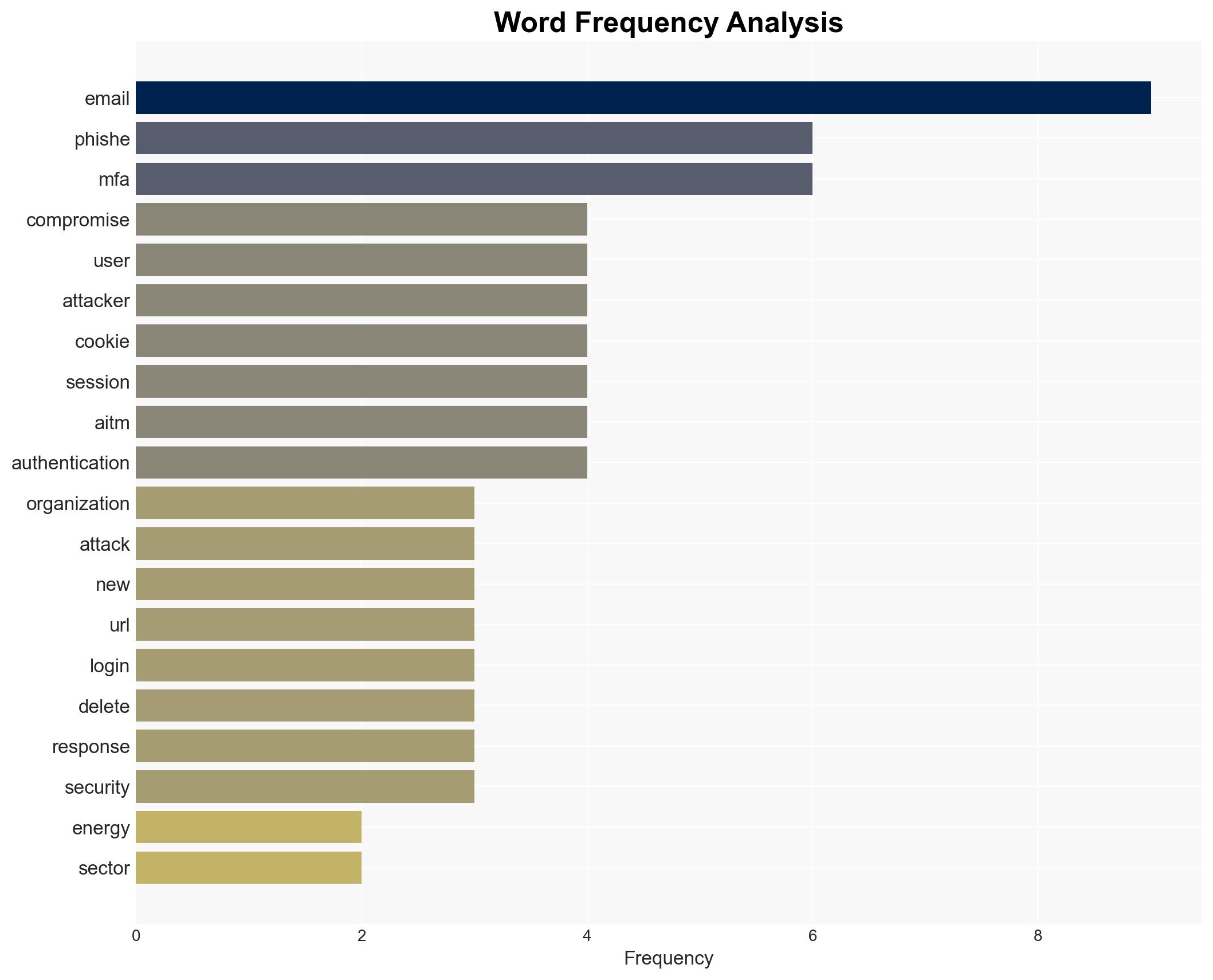
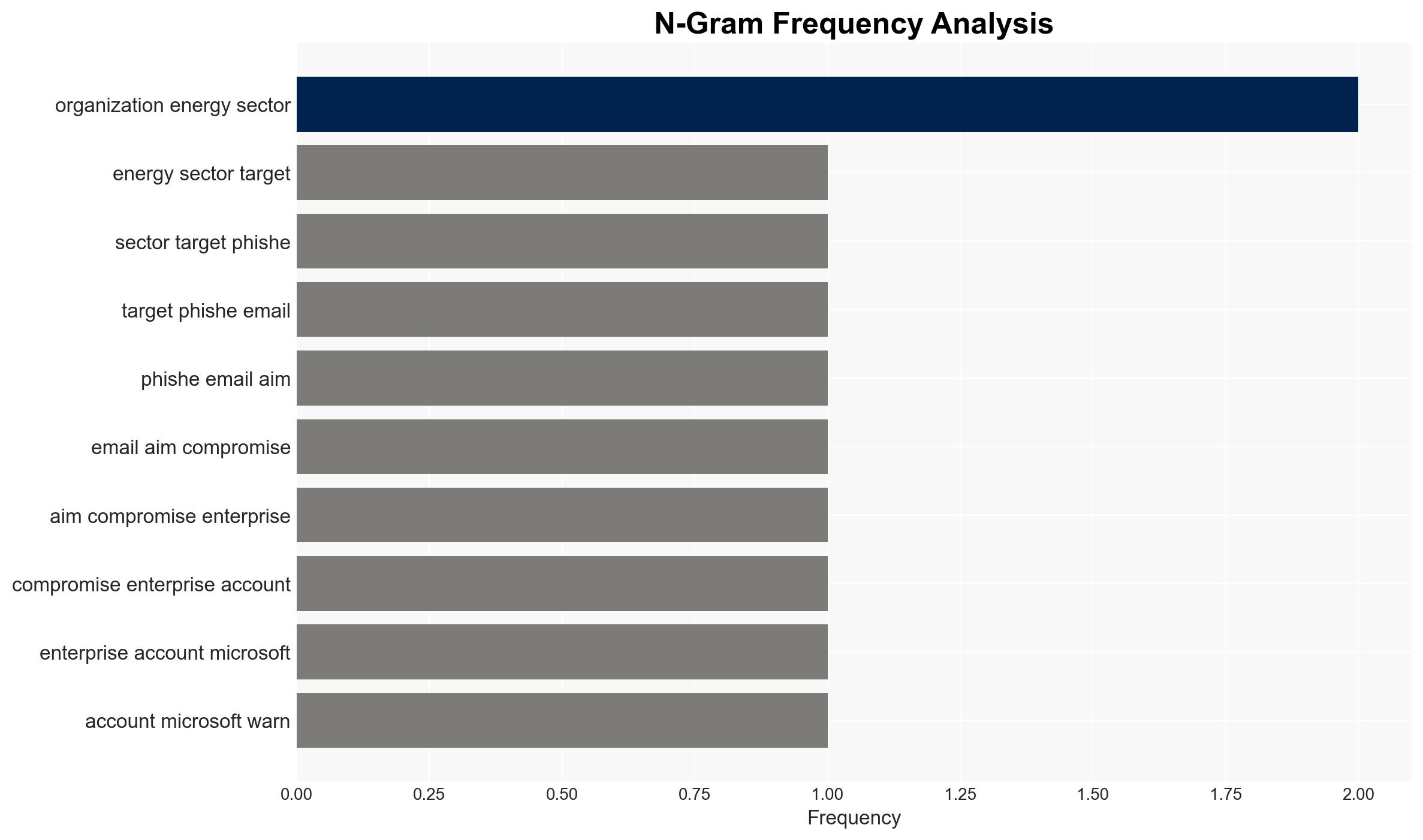
Energy sector organizations are being targeted by a sophisticated AiTM phishing campaign, which exploits compromised email accounts to bypass traditional security measures. The campaign’s complexity suggests a high level of operational capability. The most likely hypothesis is that this campaign is part of a broader effort to compromise critical infrastructure. Overall confidence in this assessment is moderate due to limited visibility into the attackers’ ultimate objectives.
2. Competing Hypotheses
- Hypothesis A: The phishing campaign is a targeted effort by a state-sponsored actor aiming to disrupt energy sector operations. Supporting evidence includes the campaign’s sophistication and targeting of critical infrastructure. However, the specific state actor remains unidentified, creating uncertainty.
- Hypothesis B: The campaign is conducted by a financially motivated cybercriminal group seeking to exploit compromised accounts for monetary gain. This is supported by the use of phishing techniques common in financially motivated attacks, but the targeting of the energy sector suggests a broader intent.
- Assessment: Hypothesis A is currently better supported due to the strategic targeting of the energy sector, which aligns with state-sponsored objectives. Indicators such as attribution to a specific state actor or evidence of financial transactions could shift this judgment.
3. Key Assumptions and Red Flags
- Assumptions: The attackers have a high level of technical capability; the energy sector is a deliberate target; compromised email accounts are a primary vector for attack.
- Information Gaps: Specific attribution to a state or non-state actor; the full scope of compromised entities; the ultimate objectives of the attackers.
- Bias & Deception Risks: Potential bias in attributing state sponsorship without clear evidence; deception risk from attackers using false flags to mislead attribution efforts.
4. Implications and Strategic Risks
This development could lead to increased vulnerabilities in critical infrastructure, potentially affecting national security and economic stability. The campaign may evolve to target other sectors, increasing the overall threat landscape.
- Political / Geopolitical: Potential escalation in cyber tensions if state sponsorship is confirmed, leading to diplomatic strains.
- Security / Counter-Terrorism: Increased risk of operational disruptions in the energy sector, necessitating enhanced security measures.
- Cyber / Information Space: Highlighting the need for improved cyber defenses and awareness of AiTM techniques.
- Economic / Social: Potential economic impact due to disruptions in energy supply, affecting both industry and consumers.
5. Recommendations and Outlook
- Immediate Actions (0–30 days): Implement enhanced monitoring of email systems, conduct security audits, and revoke compromised session cookies.
- Medium-Term Posture (1–12 months): Develop partnerships for threat intelligence sharing, invest in advanced MFA solutions, and conduct regular cybersecurity training.
- Scenario Outlook: Best: Rapid containment and attribution lead to improved defenses. Worst: Widespread disruption in the energy sector. Most-Likely: Continued targeting with incremental improvements in sector defenses.
6. Key Individuals and Entities
- Not clearly identifiable from open sources in this snippet.
7. Thematic Tags
cybersecurity, phishing, energy sector, critical infrastructure, state-sponsored threats, cybercrime, AiTM attacks
Structured Analytic Techniques Applied
- Adversarial Threat Simulation: Model and simulate actions of cyber adversaries to anticipate vulnerabilities and improve resilience.
- Indicators Development: Detect and monitor behavioral or technical anomalies across systems for early threat detection.
- Bayesian Scenario Modeling: Quantify uncertainty and predict cyberattack pathways using probabilistic inference.
Explore more:
Cybersecurity Briefs ·
Daily Summary ·
Support us