Enhanced CatBoost Algorithm for Robust DDoS Detection in Cloud VMs Achieves 99.2% Accuracy
Published on: 2026-01-15
AI-powered OSINT brief from verified open sources. Automated NLP signal extraction with human verification. See our Methodology and Why WorldWideWatchers.
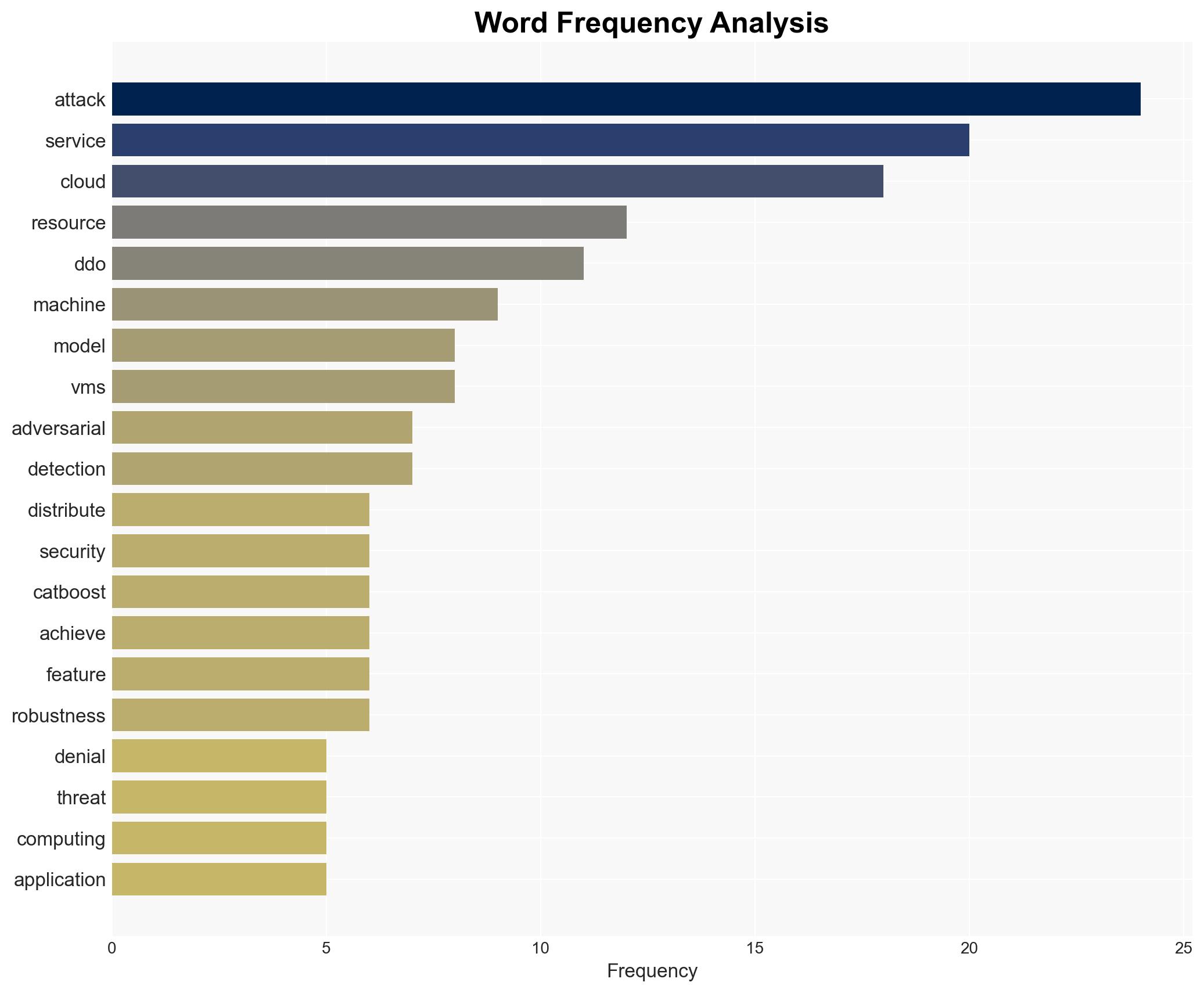
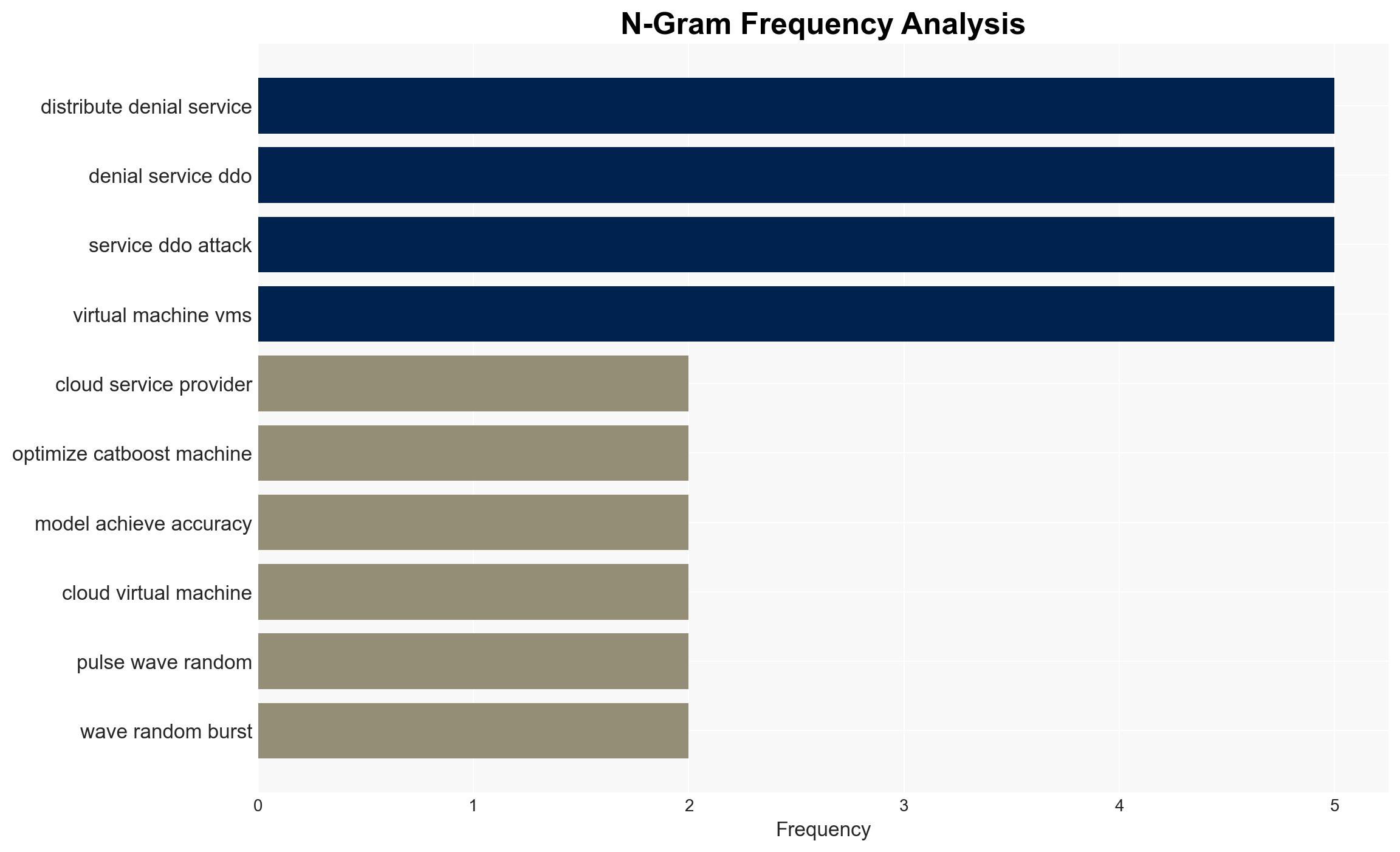
Intelligence Report: Optimized CatBoost machine learning OCML for DDoS detection in cloud virtual machines with time-series and adversarial robustness
1. BLUF (Bottom Line Up Front)
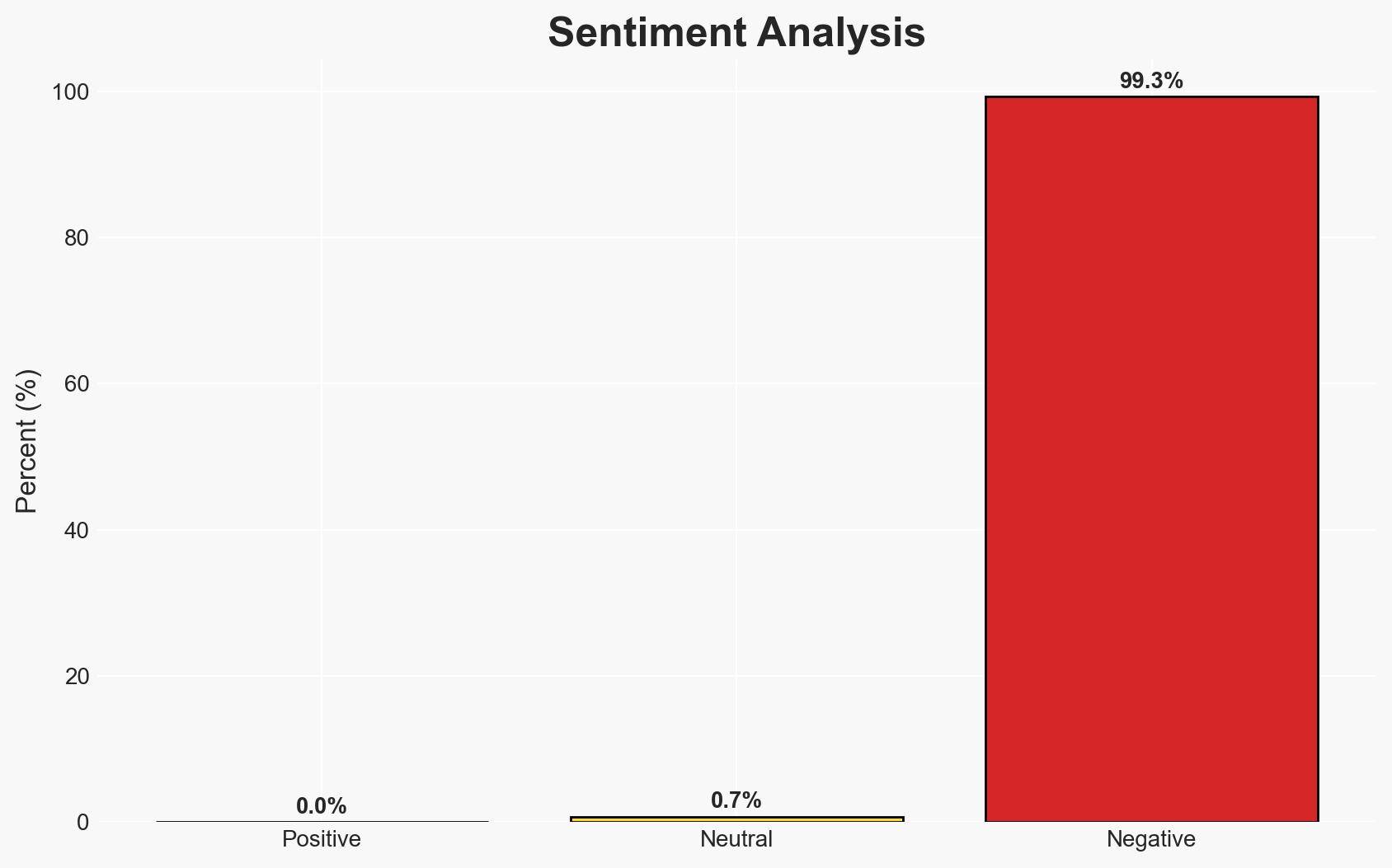
The implementation of the Optimized CatBoost machine learning algorithm (OCML) for detecting DDoS attacks in cloud virtual machines shows promising results, achieving high accuracy and robustness against adversarial attacks. This development could significantly enhance cloud security, benefiting cloud service providers and users. However, the model’s effectiveness against evolving threats remains uncertain. Overall, there is moderate confidence in the current assessment.
2. Competing Hypotheses
- Hypothesis A: The OCML model significantly enhances cloud security against DDoS attacks, providing a reliable solution for cloud service providers. Supporting evidence includes the high accuracy rates achieved in testing. However, uncertainties remain regarding its performance against novel or sophisticated attack vectors.
- Hypothesis B: The OCML model, while effective in controlled environments, may not perform as well in real-world scenarios due to evolving attack techniques and environmental variables. This hypothesis is supported by the lower accuracy rates against certain adversarial attacks.
- Assessment: Hypothesis A is currently better supported due to the model’s demonstrated high accuracy in detecting DDoS attacks. However, ongoing monitoring of its performance in diverse operational settings is necessary to validate this assessment.
3. Key Assumptions and Red Flags
- Assumptions: The model’s testing environment accurately reflects real-world conditions; adversarial attacks used in testing are representative of potential threats; cloud service providers will adopt the model without significant modification.
- Information Gaps: Lack of data on the model’s performance in diverse operational environments and against emerging DDoS techniques.
- Bias & Deception Risks: Potential confirmation bias in evaluating the model’s effectiveness based on selected datasets; risk of adversarial actors manipulating test conditions to undermine confidence in the model.
4. Implications and Strategic Risks
The deployment of the OCML model could alter the landscape of cloud security, potentially reducing the frequency and impact of DDoS attacks. However, adversaries may adapt their tactics, leading to an arms race in cyber capabilities.
- Political / Geopolitical: Enhanced cloud security could reduce state-sponsored cyber operations targeting critical infrastructure.
- Security / Counter-Terrorism: Improved defenses may force threat actors to diversify attack strategies, potentially increasing complexity in the threat environment.
- Cyber / Information Space: The model’s success could drive further innovation in machine learning applications for cybersecurity.
- Economic / Social: Increased cloud security could bolster trust in cloud services, driving economic growth and digital transformation.
5. Recommendations and Outlook
- Immediate Actions (0–30 days): Conduct pilot implementations of the OCML model in varied environments; monitor performance and gather data on real-world effectiveness.
- Medium-Term Posture (1–12 months): Develop partnerships with cybersecurity firms to enhance model adaptability; invest in research on emerging DDoS techniques.
- Scenario Outlook:
- Best: Widespread adoption of the model leads to a significant reduction in DDoS incidents.
- Worst: Adversaries quickly adapt, rendering the model less effective.
- Most-Likely: The model provides a temporary advantage, necessitating continuous updates to maintain effectiveness.
6. Key Individuals and Entities
- Not clearly identifiable from open sources in this snippet.
7. Thematic Tags
cybersecurity, cloud security, DDoS detection, machine learning, cyber defense, adversarial robustness, cloud computing, cybersecurity innovation
Structured Analytic Techniques Applied
- Adversarial Threat Simulation: Model hostile behavior to identify vulnerabilities.
- Indicators Development: Detect and monitor behavioral or technical anomalies across systems for early threat detection.
- Bayesian Scenario Modeling: Forecast futures under uncertainty via probabilistic logic.
- ACH 2.0: Machine-assisted hypothesis testing for intent reconstruction.
- Network Influence Mapping: Map influence relationships to assess actor impact.
Explore more:
Cybersecurity Briefs ·
Daily Summary ·
Support us