EnOcean SmartServer IoT
Published on: 2026-02-19
AI-powered OSINT brief from verified open sources. Automated NLP signal extraction with human verification. See our Methodology and Why WorldWideWatchers.
Intelligence Report: EnOcean SmartServer IoT
1. BLUF (Bottom Line Up Front)
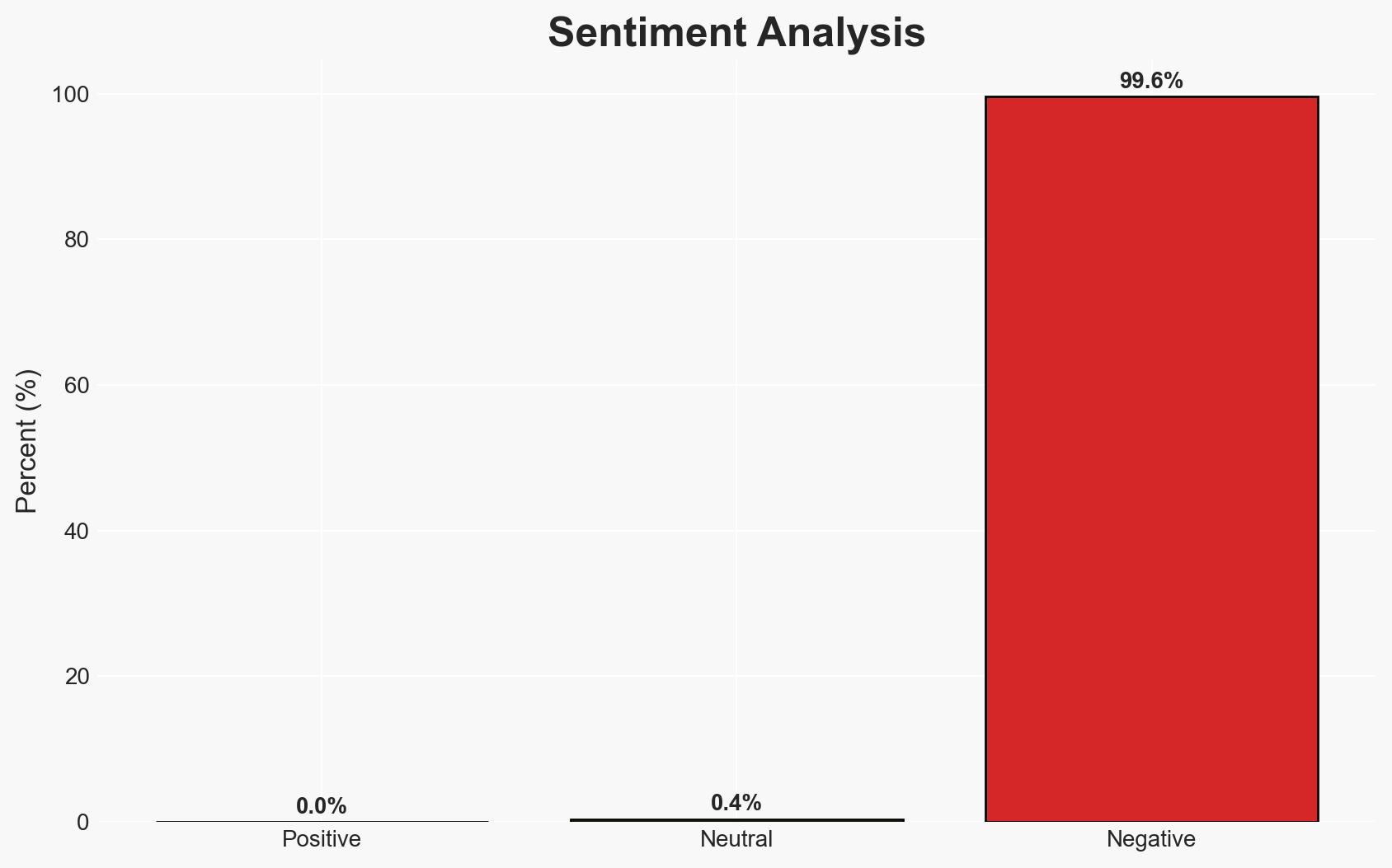
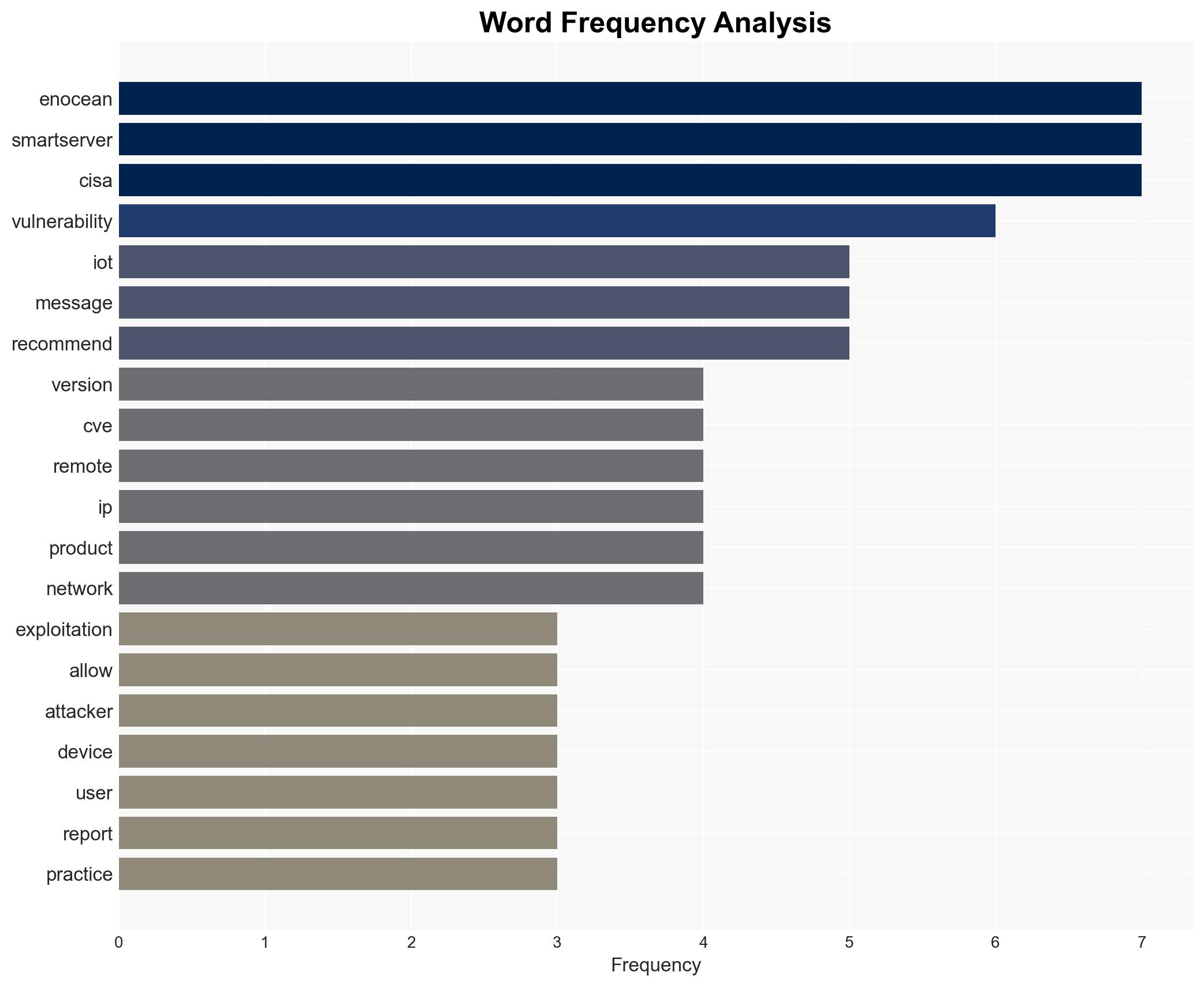
The EnOcean SmartServer IoT platform has identified critical vulnerabilities that could allow remote code execution and memory leaks. These vulnerabilities affect versions <=4.60.009 and have implications for global critical infrastructure sectors. Mitigation measures are available, but the potential for exploitation remains. Overall confidence in this assessment is moderate.
2. Competing Hypotheses
- Hypothesis A: The vulnerabilities will be actively exploited by cyber threat actors targeting critical infrastructure. This is supported by the widespread deployment of the affected systems and the critical nature of the vulnerabilities. However, no public exploitation has been reported, which introduces uncertainty.
- Hypothesis B: The vulnerabilities will not lead to significant exploitation due to the high complexity of the attack and the availability of mitigations. The lack of reported exploitation supports this, but the potential for sophisticated actors to overcome these barriers remains.
- Assessment: Hypothesis B is currently better supported due to the absence of reported exploitation and the complexity of the attack. Indicators such as increased scanning activity or reports of exploitation could shift this judgment.
3. Key Assumptions and Red Flags
- Assumptions: Organizations will implement recommended mitigations; the vulnerabilities require high technical expertise to exploit; no state-sponsored actors are currently targeting these vulnerabilities.
- Information Gaps: Specific details on the deployment scale of affected systems and the presence of any ongoing exploitation attempts.
- Bias & Deception Risks: Potential over-reliance on vendor and CISA reports; lack of independent verification may introduce confirmation bias.
4. Implications and Strategic Risks
The vulnerabilities in EnOcean SmartServer IoT could lead to significant security risks if exploited, affecting critical infrastructure globally. The evolution of this threat will depend on the response of affected organizations and the actions of potential threat actors.
- Political / Geopolitical: Potential for increased geopolitical tension if state actors are implicated in exploiting these vulnerabilities.
- Security / Counter-Terrorism: Increased risk of cyber-attacks on critical infrastructure, potentially impacting national security.
- Cyber / Information Space: Heightened focus on cyber defense and information security practices; potential for misinformation or disinformation campaigns.
- Economic / Social: Disruption to services reliant on affected systems could impact economic stability and social trust in technology.
5. Recommendations and Outlook
- Immediate Actions (0–30 days): Encourage organizations to apply software updates and follow CISA’s recommended practices; increase monitoring for signs of exploitation.
- Medium-Term Posture (1–12 months): Develop partnerships for information sharing; enhance cybersecurity resilience through training and infrastructure upgrades.
- Scenario Outlook:
- Best: Vulnerabilities are patched with no exploitation, leading to improved security practices.
- Worst: Widespread exploitation occurs, causing significant disruption to critical infrastructure.
- Most-Likely: Limited exploitation with increased security measures mitigating broader impacts.
6. Key Individuals and Entities
- EnOcean Edge Inc
- Amir Zaltzman, Claroty Team82
- CISA (Cybersecurity and Infrastructure Security Agency)
- Not clearly identifiable from open sources in this snippet.
7. Thematic Tags
cybersecurity, critical infrastructure, vulnerability management, remote code execution, information technology, cyber defense, risk mitigation
Structured Analytic Techniques Applied
- Adversarial Threat Simulation: Model and simulate actions of cyber adversaries to anticipate vulnerabilities and improve resilience.
- Indicators Development: Detect and monitor behavioral or technical anomalies across systems for early threat detection.
- Bayesian Scenario Modeling: Quantify uncertainty and predict cyberattack pathways using probabilistic inference.
- Network Influence Mapping: Map influence relationships to assess actor impact.
Explore more:
Cybersecurity Briefs ·
Daily Summary ·
Support us