Enterprise security faces new challenge as attackers master art of digital impersonation – TechRadar
Published on: 2025-08-25
Intelligence Report: Enterprise security faces new challenge as attackers master art of digital impersonation – TechRadar
1. BLUF (Bottom Line Up Front)
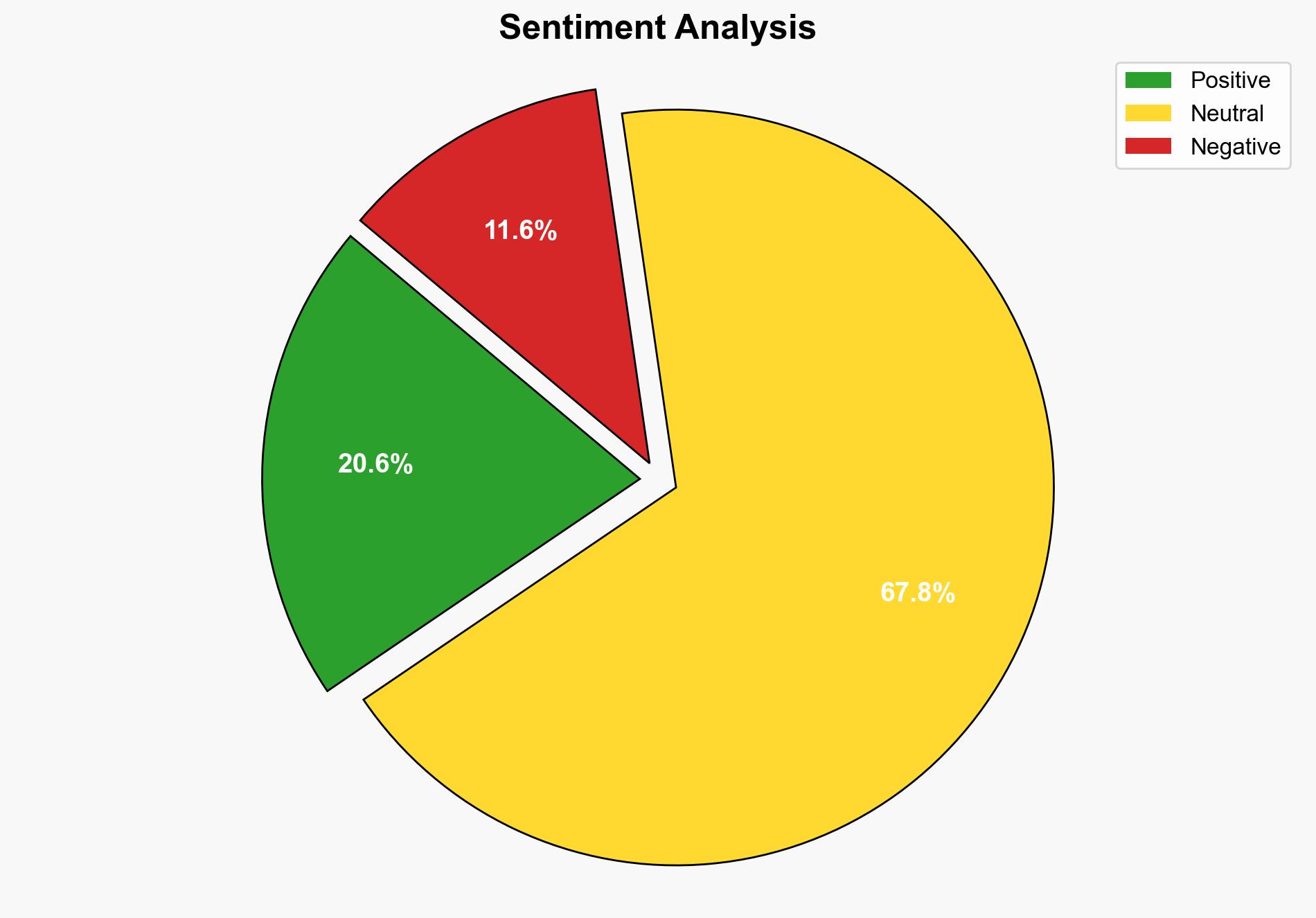
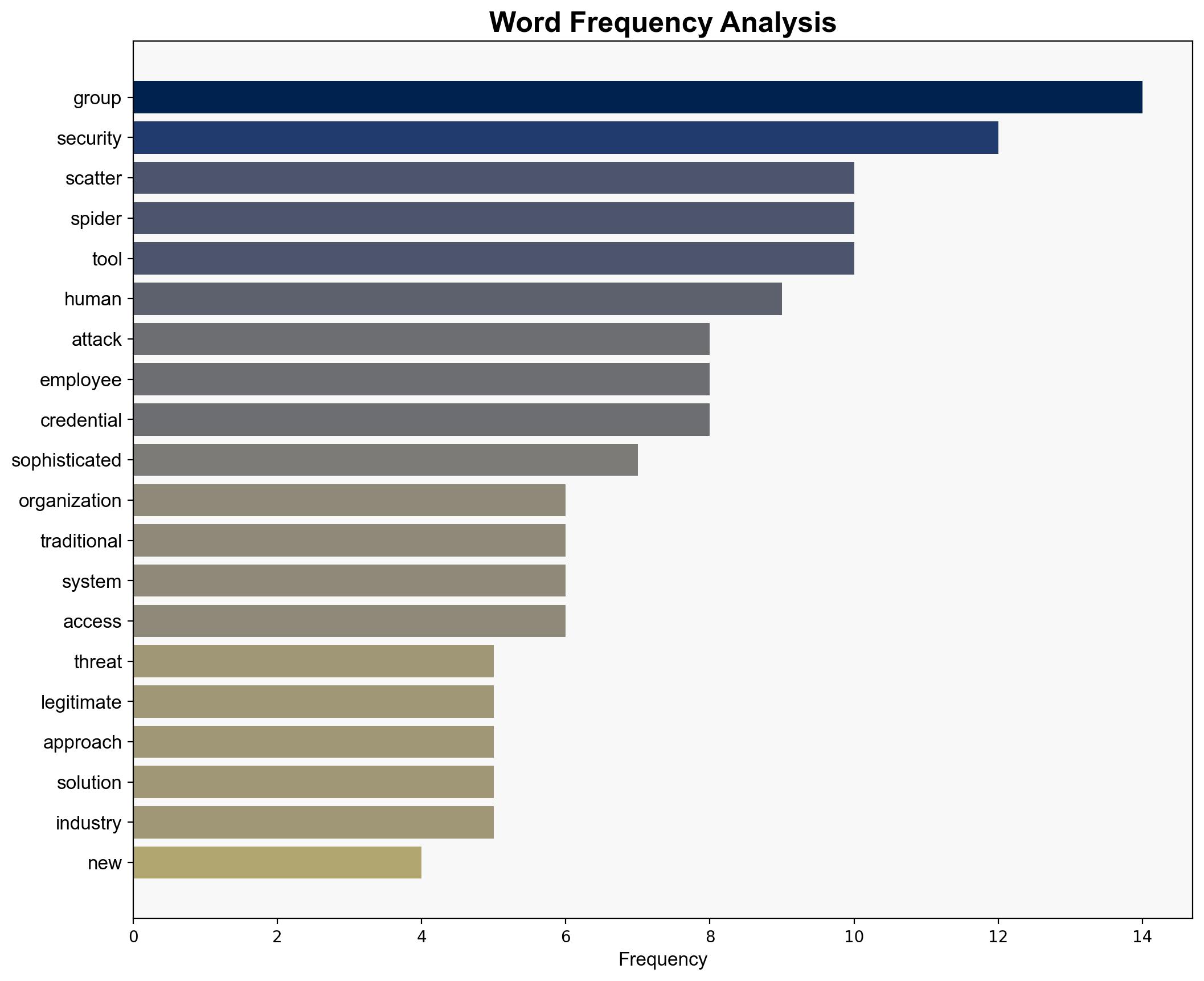
The most supported hypothesis is that the Scatter Spider group represents a significant evolution in cyber threats by prioritizing human psychology over traditional malware. This approach increases the difficulty of detection and mitigation. Confidence Level: High. Recommended action includes enhancing employee training on social engineering and investing in behavioral-based detection systems.
2. Competing Hypotheses
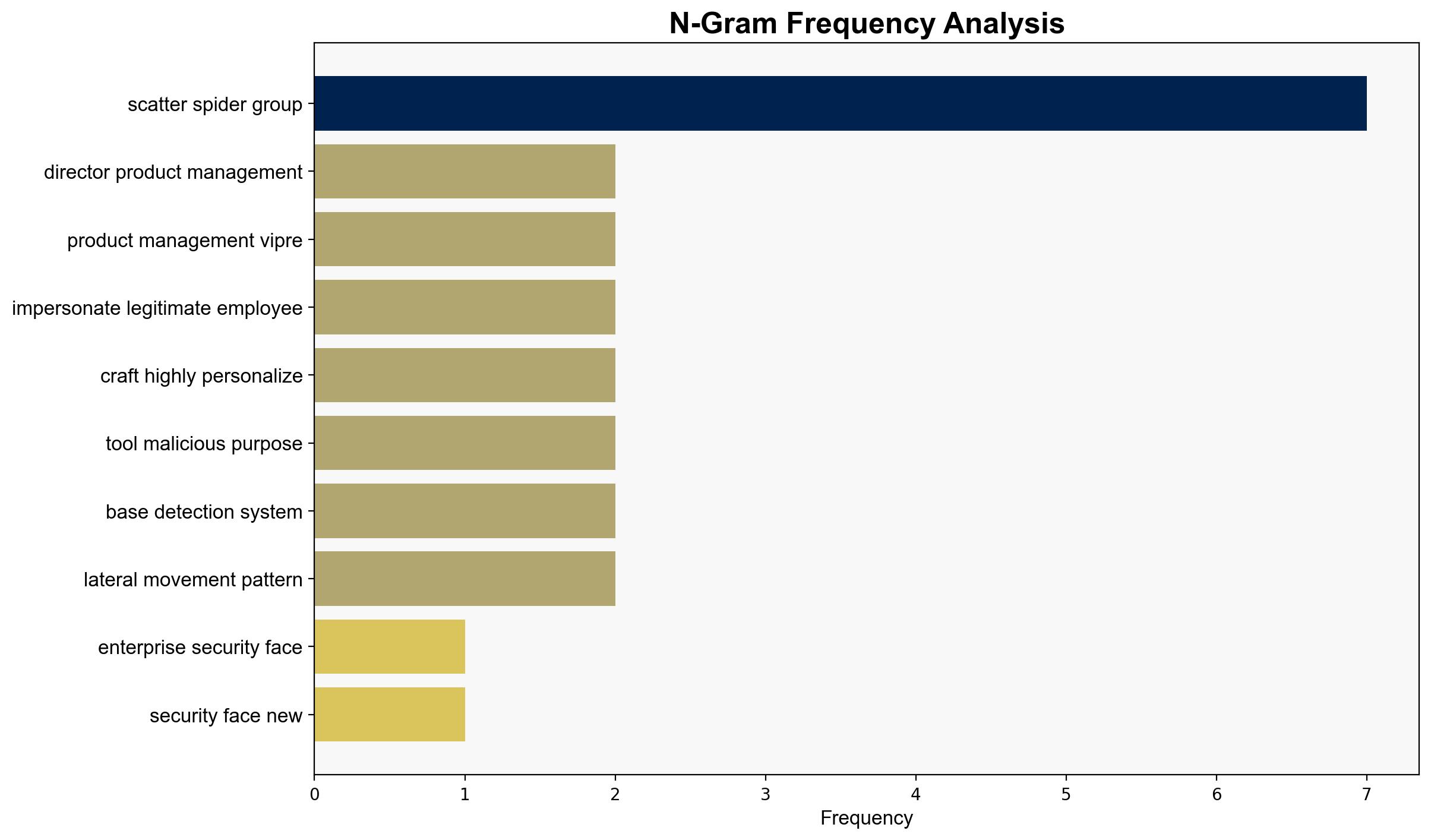
1. **Hypothesis A**: Scatter Spider is a highly sophisticated cybercriminal group that has fundamentally transformed attack paradigms by mastering digital impersonation and social engineering, posing a significant threat to enterprise security.
2. **Hypothesis B**: Scatter Spider’s activities are exaggerated, and the group is not significantly different from existing cybercriminal entities; their success is due to exploiting existing vulnerabilities rather than novel methods.
Using ACH 2.0, Hypothesis A is better supported due to the detailed description of their methods, including AI-driven phishing and voice cloning, which indicate a higher level of sophistication than typical cybercriminal activities.
3. Key Assumptions and Red Flags
– **Assumptions**: It is assumed that the Scatter Spider group has access to advanced AI tools and that their methods are not easily replicable by other groups.
– **Red Flags**: Lack of specific evidence on the group’s size and origin. Possible over-reliance on anecdotal evidence from affected organizations.
– **Blind Spots**: Potential underestimation of other groups adopting similar tactics, leading to a broader threat landscape.
4. Implications and Strategic Risks
The emergence of Scatter Spider suggests a shift in cyber threats towards exploiting human factors, increasing the risk of breaches despite traditional security measures. This could lead to economic losses, reputational damage, and increased costs for cybersecurity. The group’s success may inspire copycat attacks, escalating the threat level across industries.
5. Recommendations and Outlook
- Enhance employee training programs focused on recognizing social engineering tactics.
- Invest in behavioral-based detection systems that identify anomalies in user behavior.
- Scenario Projections:
- Best Case: Organizations adapt quickly, reducing the effectiveness of Scatter Spider’s methods.
- Worst Case: Widespread adoption of similar tactics by other groups, overwhelming current security systems.
- Most Likely: Gradual increase in similar attacks, prompting a shift in cybersecurity strategies towards human-centric defenses.
6. Key Individuals and Entities
– Scatter Spider
– UNC Oktapus
– Muddled Libra
7. Thematic Tags
national security threats, cybersecurity, counter-terrorism, regional focus