Epstein and Barak exploited Nigerian instability to market surveillance tech developed in Palestinian territo…
Published on: 2026-02-18
AI-powered OSINT brief from verified open sources. Automated NLP signal extraction with human verification. See our Methodology and Why WorldWideWatchers.
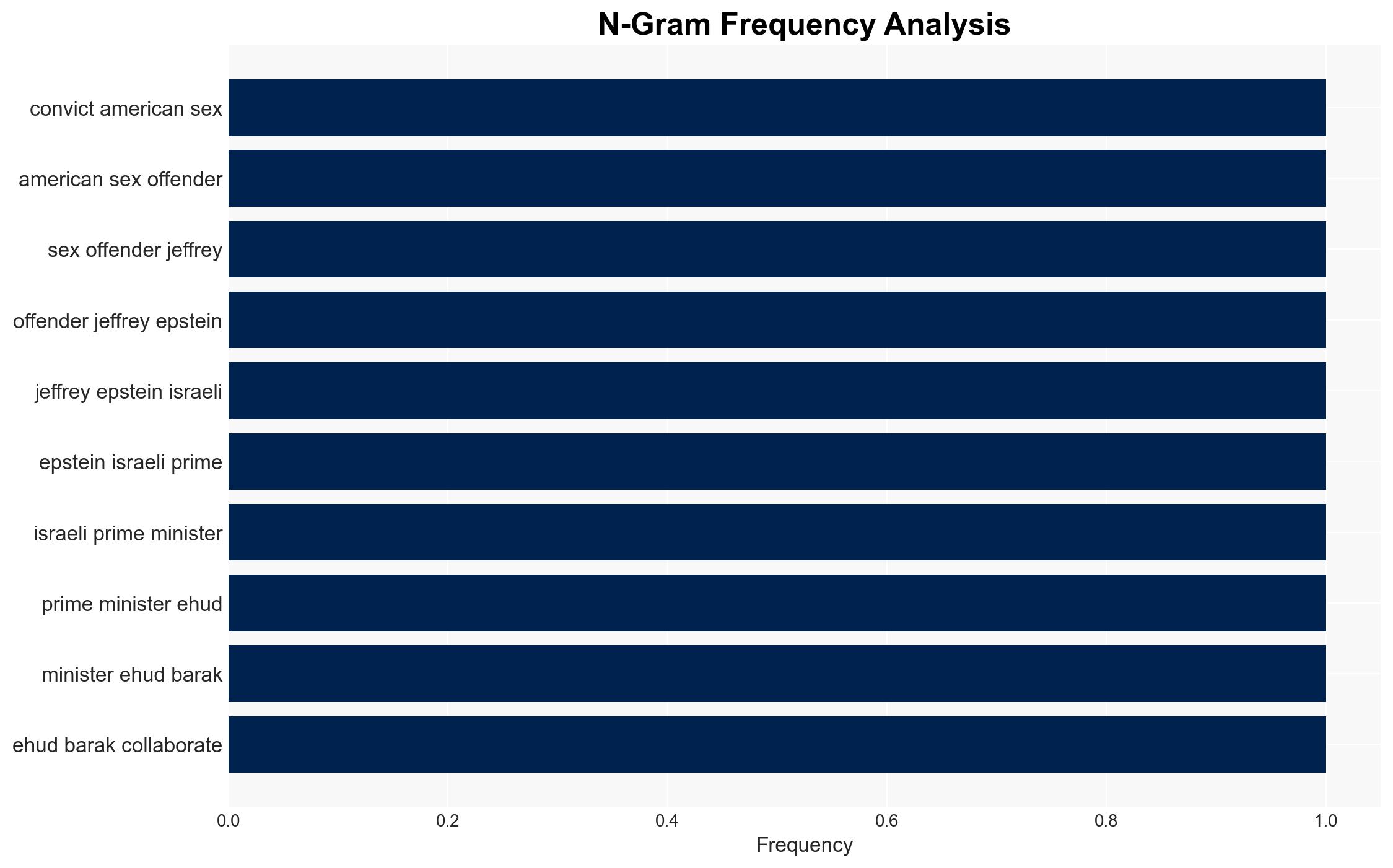
Intelligence Report: Tested on Palestinians Epstein Israels Barak pushed spy tech in Nigeria
1. BLUF (Bottom Line Up Front)
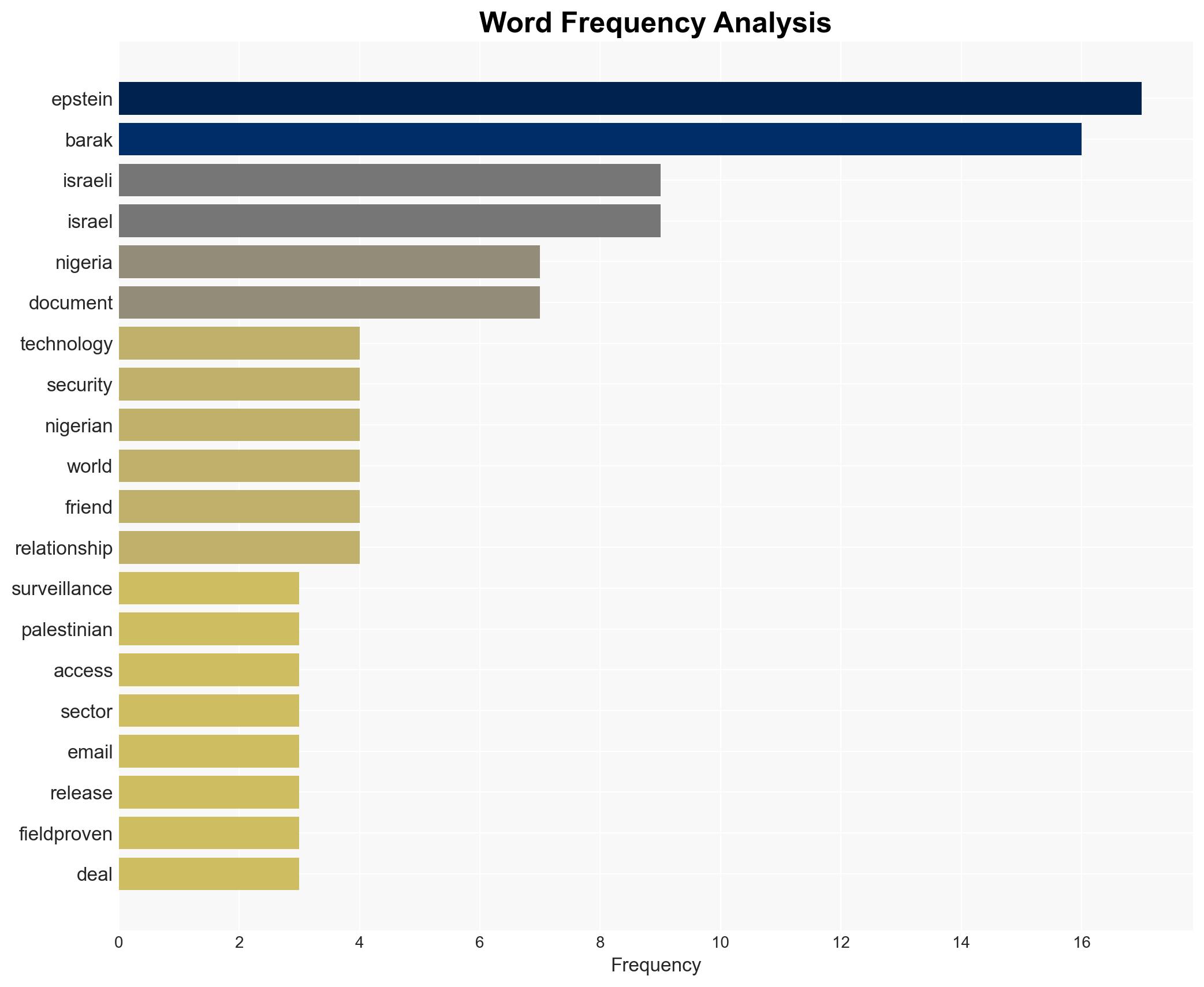
The collaboration between Jeffrey Epstein and Ehud Barak to market Israeli surveillance technology in Nigeria, leveraging instability for commercial gain, suggests a strategic exploitation of regional conflicts. This activity has potential implications for Nigerian sovereignty and regional stability. The most likely hypothesis is that these actions were primarily profit-driven, with moderate confidence due to incomplete data on the full extent of their operations and intentions.
2. Competing Hypotheses
- Hypothesis A: Epstein and Barak’s activities were primarily motivated by financial gain, using security technology as a pretext to access Nigeria’s resource sectors. This is supported by the documented focus on commercial interests and infrastructure projects. However, the full extent of their influence on Nigerian policy remains uncertain.
- Hypothesis B: The collaboration was part of a broader geopolitical strategy by Israel to expand its influence in Africa through technology exports. While Israeli firms did institutionalize cyber expertise in Nigeria, there is limited evidence directly linking these activities to state-level geopolitical objectives.
- Assessment: Hypothesis A is currently better supported due to the explicit financial motivations and documented commercial engagements. Indicators such as further disclosures of state-level involvement could shift this judgment.
3. Key Assumptions and Red Flags
- Assumptions: The primary motivation was financial gain; Nigerian officials were complicit or unaware of the broader implications; Israeli technology was effectively integrated into Nigerian systems.
- Information Gaps: Detailed financial records of transactions; Nigerian government’s internal communications regarding these deals; full scope of technology deployment and its impact.
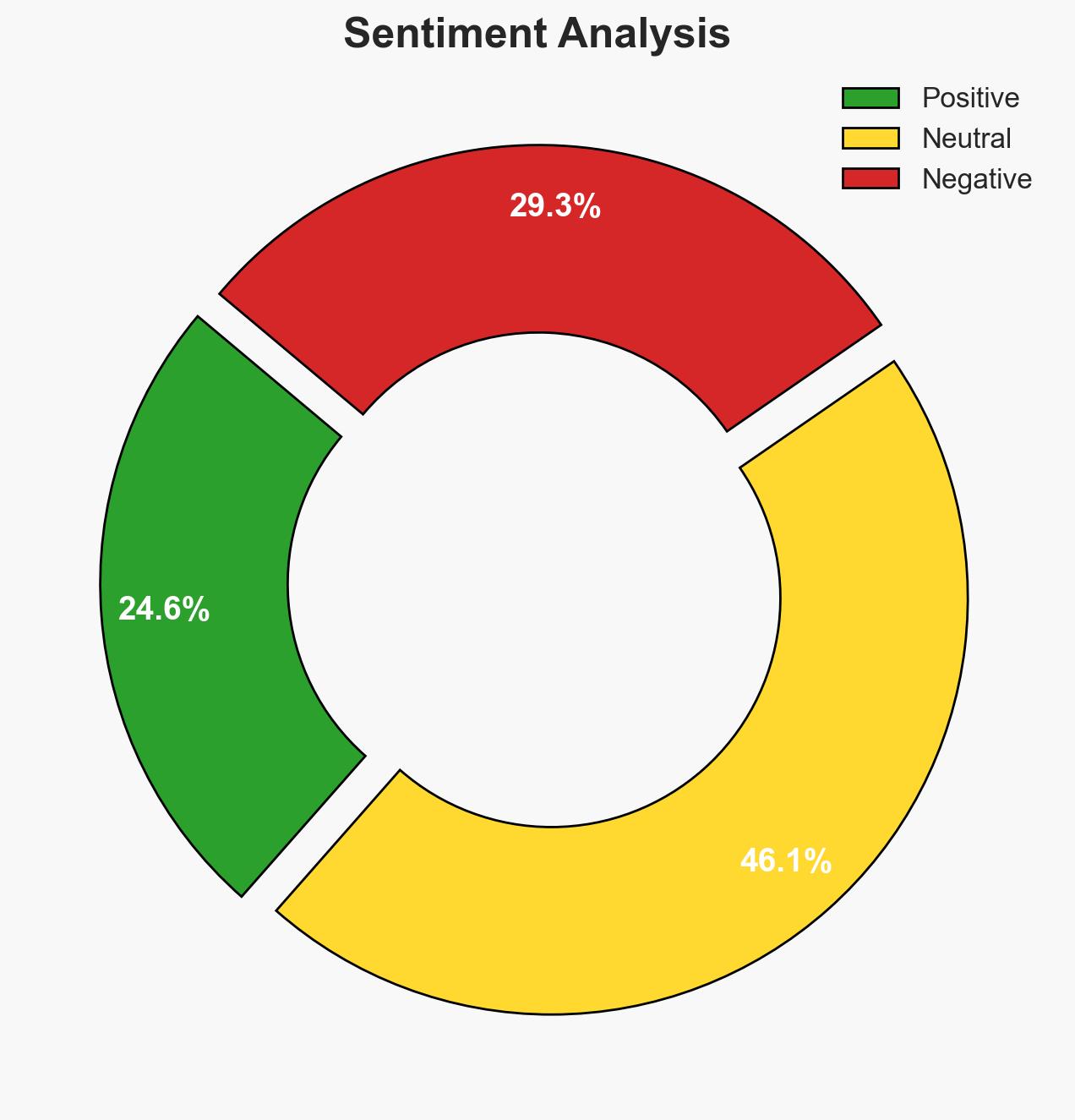
- Bias & Deception Risks: Potential bias in source reporting due to political agendas; risk of deception by involved parties to obscure true intentions or scale of operations.
4. Implications and Strategic Risks
This development could exacerbate regional instability by embedding foreign interests in Nigeria’s security and economic sectors, potentially undermining national sovereignty and fueling local discontent.
- Political / Geopolitical: Increased foreign influence in Nigeria could alter regional power dynamics and provoke responses from other international actors.
- Security / Counter-Terrorism: The integration of foreign surveillance technology may enhance counter-terrorism capabilities but also raises concerns about misuse and civil liberties.
- Cyber / Information Space: Institutionalization of Israeli cyber expertise could lead to increased cyber capabilities but also potential vulnerabilities if not properly managed.
- Economic / Social: Economic benefits may be offset by social unrest if perceived as foreign exploitation; potential impacts on local industries and employment.
5. Recommendations and Outlook
- Immediate Actions (0–30 days): Monitor Nigerian government responses; engage with local stakeholders to assess impacts; review international legal frameworks on foreign technology deployment.
- Medium-Term Posture (1–12 months): Develop partnerships with Nigerian entities to ensure technology use aligns with national interests; enhance oversight mechanisms for foreign investments.
- Scenario Outlook:
- Best: Technology integration leads to improved security and economic growth, with transparent governance.
- Worst: Increased foreign control leads to political instability and economic exploitation.
- Most-Likely: Continued foreign involvement with mixed outcomes on security and economic fronts, contingent on governance quality.
6. Key Individuals and Entities
- Jeffrey Epstein, Ehud Barak, DP World, Nigerian government officials, Aharon Ze’evi Farkash, FST Bio
7. Thematic Tags
cybersecurity, surveillance technology, foreign influence, economic exploitation, cyber integration, regional stability, geopolitical strategy, counter-terrorism
Structured Analytic Techniques Applied
- Adversarial Threat Simulation: Model and simulate actions of cyber adversaries to anticipate vulnerabilities and improve resilience.
- Indicators Development: Detect and monitor behavioral or technical anomalies across systems for early threat detection.
- Bayesian Scenario Modeling: Quantify uncertainty and predict cyberattack pathways using probabilistic inference.
Explore more:
Cybersecurity Briefs ·
Daily Summary ·
Support us