eSentire Reports 389% Surge in Account Compromise Threats Targeting Employee Credentials in 2025
Published on: 2026-01-15
AI-powered OSINT brief from verified open sources. Automated NLP signal extraction with human verification. See our Methodology and Why WorldWideWatchers.
Intelligence Report: eSentire Warns Businesses Hackers are After Your Employees Account Credentials as Account Compromise Threats Surge 389 in 2025
1. BLUF (Bottom Line Up Front)
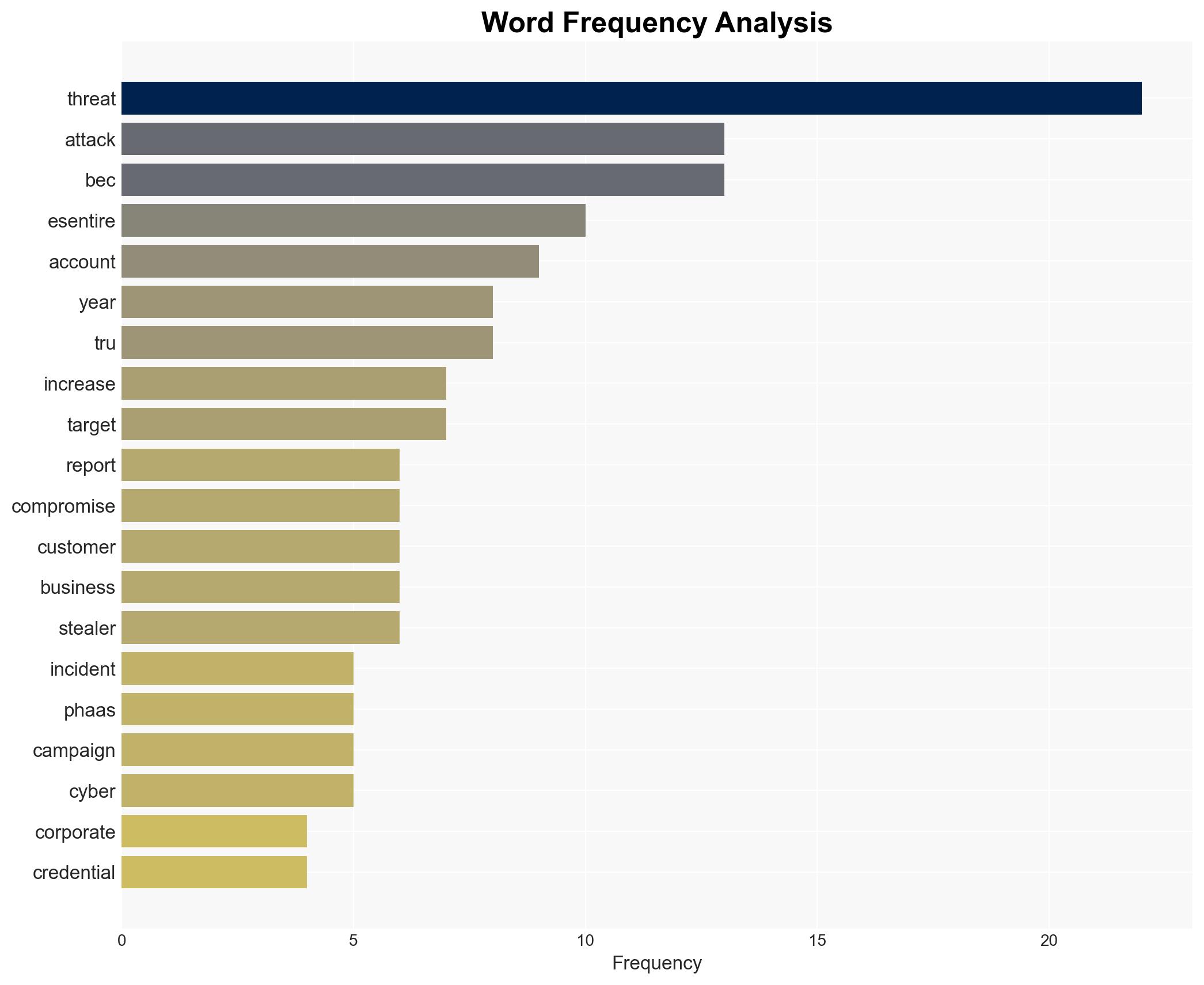
The report by eSentire highlights a significant 389% increase in account compromise threats in 2025, primarily driven by Phishing-as-a-Service (PhaaS) operations targeting corporate credentials. This surge poses a substantial risk to businesses, particularly in sectors prone to Business Email Compromise (BEC). The most likely hypothesis is that the industrialization of cybercrime through PhaaS is the primary driver of this trend. Overall confidence in this assessment is moderate.
2. Competing Hypotheses
- Hypothesis A: The increase in account compromise threats is primarily due to the industrialization of cybercrime, with PhaaS offerings providing sophisticated tools that bypass security measures. Supporting evidence includes the widespread use of PhaaS kits like Tycoon2FA and EvilProxy. Uncertainties include the potential underreporting of other attack vectors.
- Hypothesis B: The surge in account compromises is driven by an increase in general cybercriminal activity and not specifically by PhaaS. This hypothesis is less supported, as the report emphasizes the role of PhaaS in the majority of incidents.
- Assessment: Hypothesis A is currently better supported due to the detailed evidence of PhaaS involvement in the majority of account compromises. Key indicators that could shift this judgment include new data on other significant attack vectors or changes in cybercriminal tactics.
3. Key Assumptions and Red Flags
- Assumptions: PhaaS will continue to evolve and evade security measures; businesses will remain primary targets for credential theft; current security measures are insufficient against advanced PhaaS kits.
- Information Gaps: Specific data on the effectiveness of various security measures against PhaaS; comprehensive statistics on other potential attack vectors.
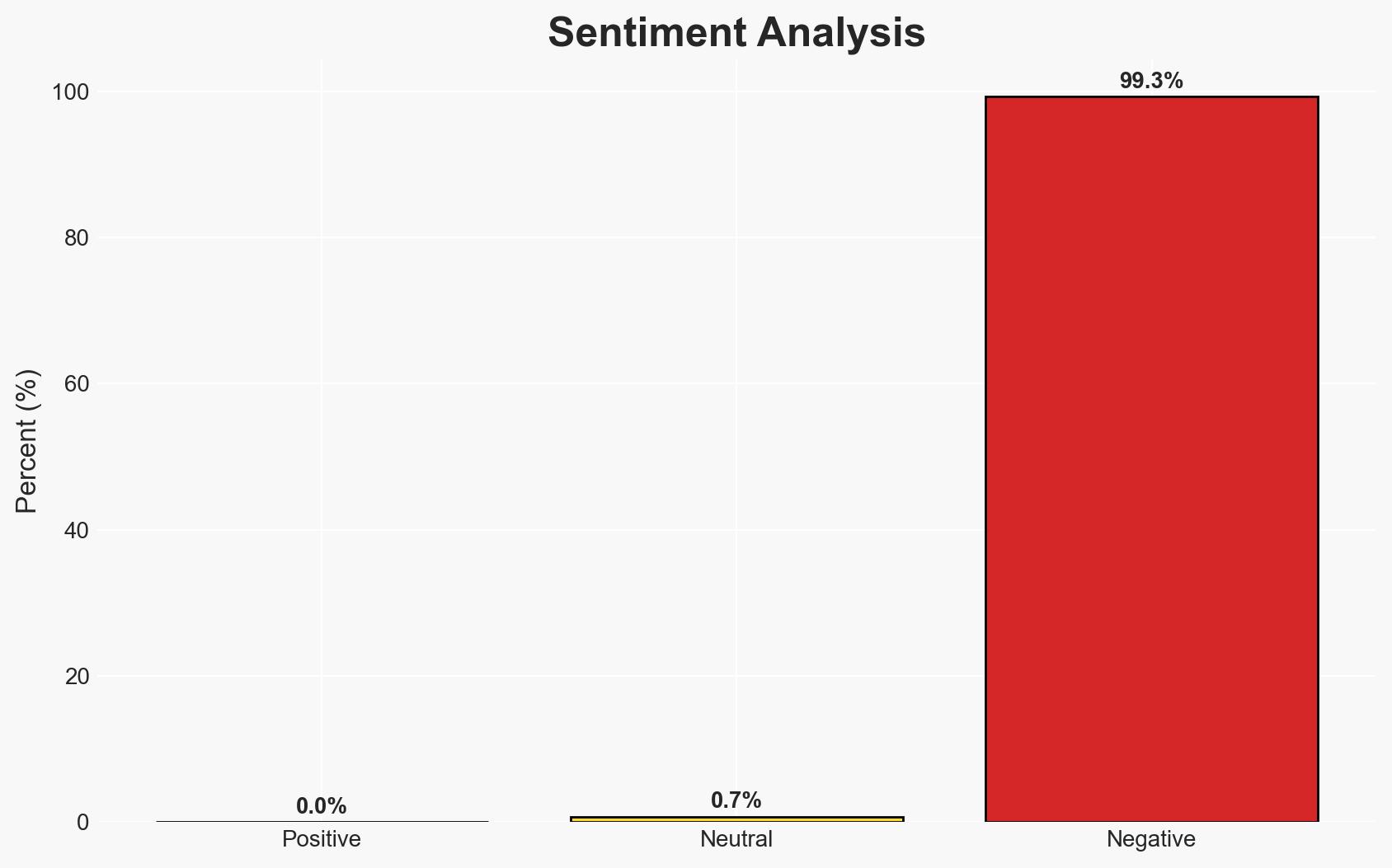
- Bias & Deception Risks: Potential bias in eSentire’s report due to vested interests in promoting their cybersecurity solutions; risk of underestimating other cyber threats not covered in the report.
4. Implications and Strategic Risks
The continued rise of PhaaS could lead to more sophisticated and frequent cyberattacks, impacting business operations and financial stability. This trend may also influence global cybersecurity policies and collaboration efforts.
- Political / Geopolitical: Increased international pressure for stronger cybersecurity regulations and cooperation.
- Security / Counter-Terrorism: Heightened threat environment requiring enhanced security protocols and intelligence sharing.
- Cyber / Information Space: Escalation in cyber warfare tactics and the potential for state-sponsored actors to exploit PhaaS.
- Economic / Social: Potential economic losses from BEC attacks and increased cybersecurity costs for businesses.
5. Recommendations and Outlook
- Immediate Actions (0–30 days): Enhance monitoring of PhaaS activities; increase employee awareness and training on phishing threats; implement advanced security measures like behavioral analytics.
- Medium-Term Posture (1–12 months): Develop partnerships with cybersecurity firms for threat intelligence sharing; invest in research and development of new security technologies; strengthen regulatory frameworks.
- Scenario Outlook:
- Best: Successful mitigation of PhaaS threats through international cooperation and technological advancements.
- Worst: PhaaS operations become more sophisticated, leading to widespread economic disruption.
- Most-Likely: Continued evolution of PhaaS with incremental improvements in defense mechanisms.
6. Key Individuals and Entities
- Spence Hutchinson, Senior Manager of TRU
- eSentire, cybersecurity solutions provider
- Threat Response Unit (TRU), eSentire’s security research team
- Not clearly identifiable from open sources in this snippet.
7. Thematic Tags
cybersecurity, phishing-as-a-service, business email compromise, account compromise, threat intelligence, cybercrime, corporate security
Structured Analytic Techniques Applied
- Adversarial Threat Simulation: Model and simulate actions of cyber adversaries to anticipate vulnerabilities and improve resilience.
- Indicators Development: Detect and monitor behavioral or technical anomalies across systems for early threat detection.
- Bayesian Scenario Modeling: Quantify uncertainty and predict cyberattack pathways using probabilistic inference.
- Network Influence Mapping: Map influence relationships to assess actor impact.
Explore more:
Cybersecurity Briefs ·
Daily Summary ·
Support us