ESET Threat Report H1 2025 – We Live Security
Published on: 2025-06-26
Intelligence Report: ESET Threat Report H1 2025 – We Live Security
1. BLUF (Bottom Line Up Front)
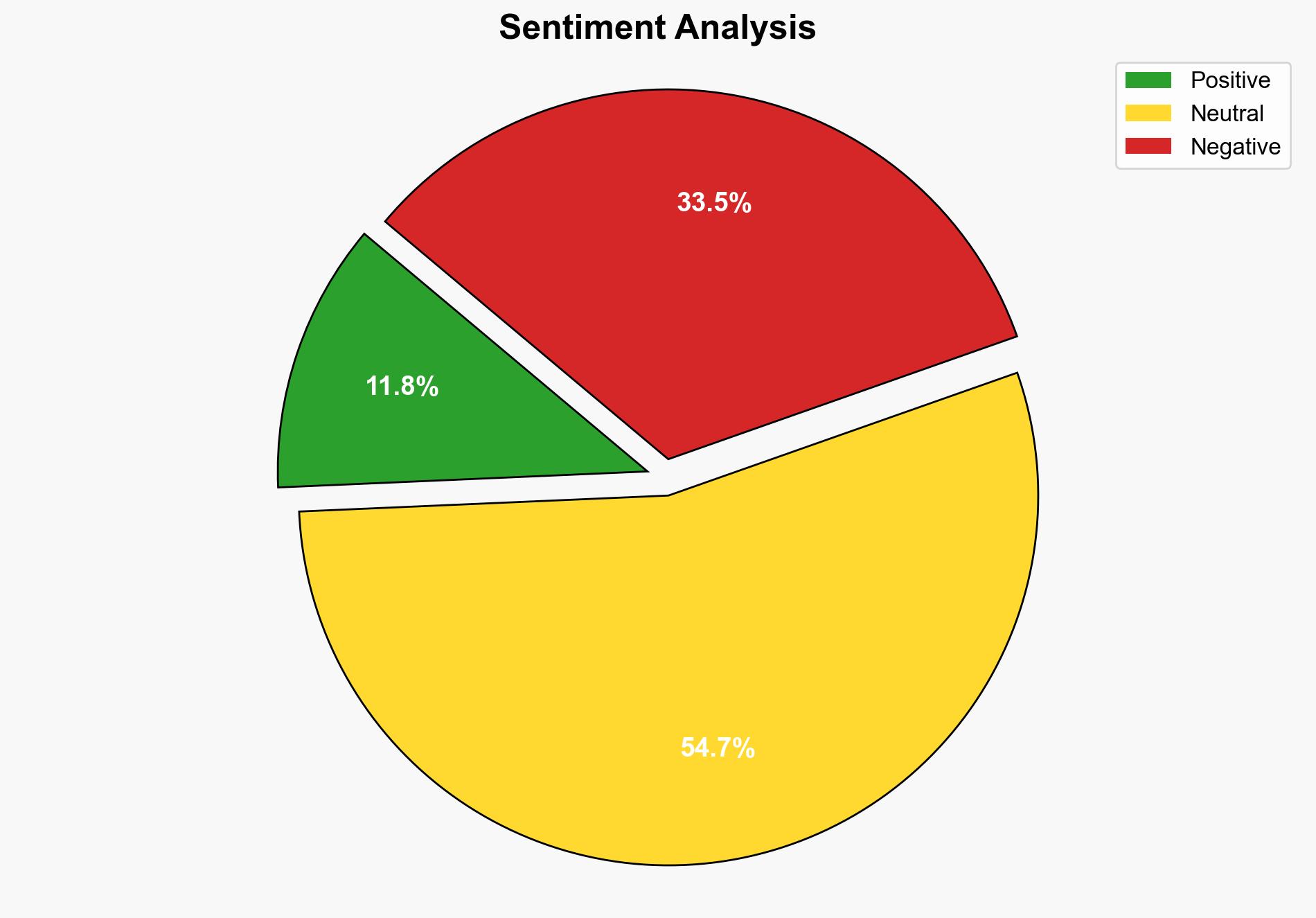
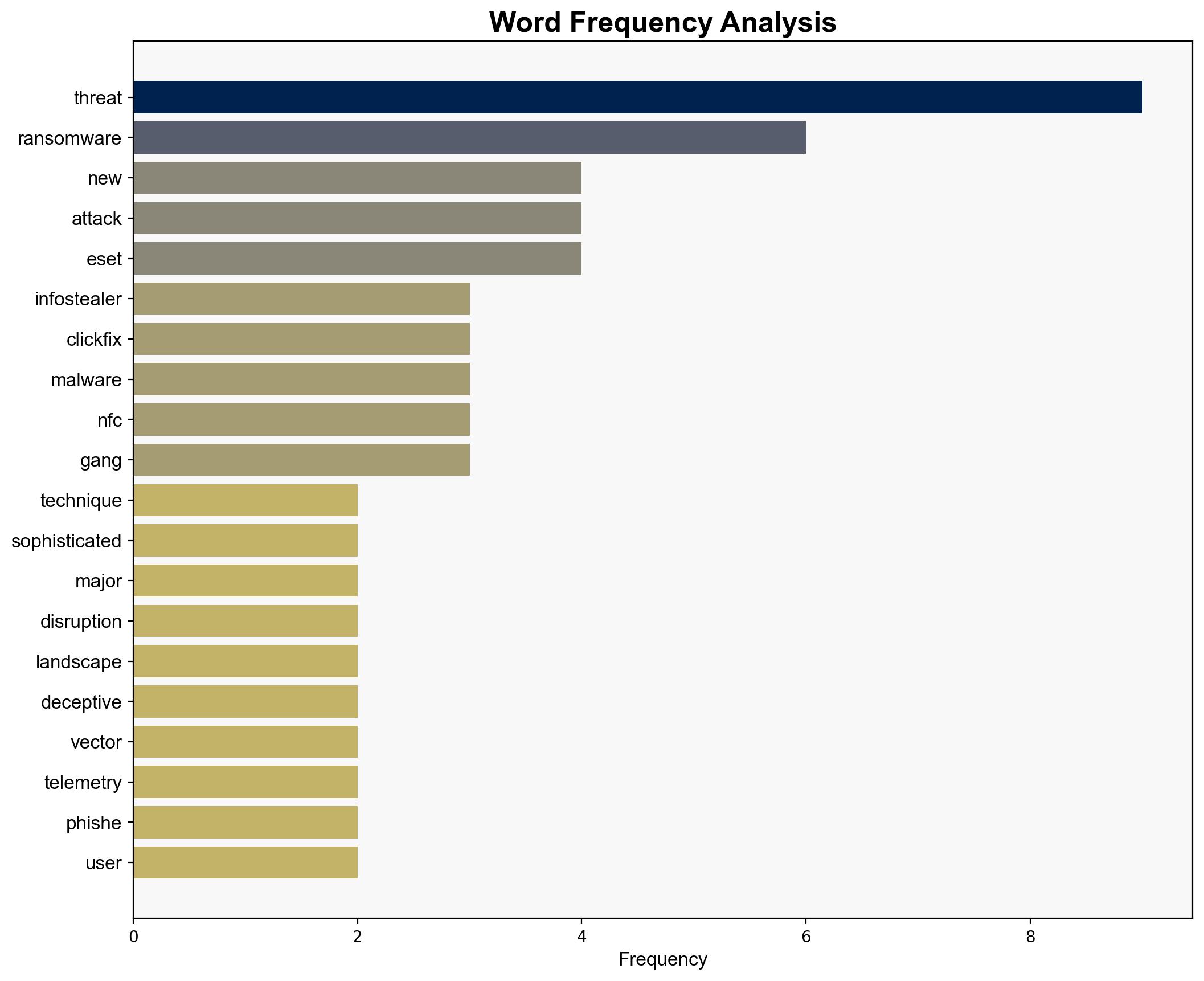
The ESET Threat Report H1 2025 highlights a significant evolution in cyber threats, emphasizing the rise of sophisticated social engineering techniques and mobile threats. Key findings include the emergence of the “clickfix” attack vector, a surge in infostealer malware, and a notable increase in Android adware detections. The report underscores the need for enhanced threat intelligence and adaptive cybersecurity measures to counter these evolving threats.
2. Detailed Analysis
The following structured analytic techniques have been applied to ensure methodological consistency:
Adversarial Threat Simulation
Simulations reveal that adversaries are increasingly leveraging social engineering to exploit user trust, particularly through the “clickfix” vector, which disguises malicious commands as system fixes.
Indicators Development
Monitoring has identified a shift in infostealer dominance, with Snakestealer overtaking Agent Tesla. This shift highlights the need for updated detection protocols.
Bayesian Scenario Modeling
Probabilistic models predict a continued rise in NFC-based fraud, with new threats like ngate and ghosttap adapting to bypass current security measures.
3. Implications and Strategic Risks
The rapid evolution of cyber threats poses systemic risks across multiple domains. The proliferation of ransomware gangs and the sophistication of mobile threats could disrupt critical infrastructure and economic stability. The decline in ransom payments suggests a potential shift in attacker strategies, possibly leading to more destructive attacks if financial incentives diminish.
4. Recommendations and Outlook
- Enhance user awareness programs to mitigate social engineering risks, particularly those involving the “clickfix” vector.
- Invest in advanced threat detection systems to identify and neutralize emerging malware like Snakestealer and NFC-based threats.
- Scenario-based projections suggest that proactive engagement with cybersecurity frameworks will be crucial in the best-case scenario, while failure to adapt could lead to significant disruptions in the worst-case scenario.
5. Key Individuals and Entities
No specific individuals are mentioned in the report. The focus is on malware entities such as Snakestealer, Lumma Stealer, and Danabot.
6. Thematic Tags
national security threats, cybersecurity, cybercrime evolution, mobile threats, ransomware dynamics