EU Enhances Cybersecurity Regulations for Technology Supply Chains to Boost Resilience and Product Safety
Published on: 2026-01-21
AI-powered OSINT brief from verified open sources. Automated NLP signal extraction with human verification. See our Methodology and Why WorldWideWatchers.
Intelligence Report: EU tightens cybersecurity rules for tech supply chains
1. BLUF (Bottom Line Up Front)
The European Commission’s new cybersecurity package aims to enhance the EU’s cyber resilience, focusing on securing ICT supply chains and telecommunications networks. The initiative is likely to improve cybersecurity standards across the EU, affecting businesses, public authorities, and citizens. The most likely hypothesis is that these measures will lead to increased trust and security in ICT products, with moderate confidence in this assessment due to potential implementation challenges and geopolitical tensions.
2. Competing Hypotheses
- Hypothesis A: The new cybersecurity measures will significantly enhance the EU’s cyber resilience by securing ICT supply chains and reducing reliance on high-risk suppliers. Supporting evidence includes the introduction of a risk-based framework and mandatory derisking of telecommunications networks. Key uncertainties involve the effectiveness of implementation and compliance by businesses.
- Hypothesis B: The cybersecurity measures may face significant implementation challenges, leading to limited impact on overall cyber resilience. Contradicting evidence includes potential resistance from businesses due to increased regulatory burdens and geopolitical pushback from affected third-country suppliers.
- Assessment: Hypothesis A is currently better supported due to the structured approach and involvement of ENISA and other stakeholders. However, indicators such as business compliance rates and geopolitical reactions could shift this judgment.
3. Key Assumptions and Red Flags
- Assumptions: The EU Member States will uniformly adopt and enforce the new measures; Businesses will comply with the certification schemes; ENISA will effectively coordinate the implementation.
- Information Gaps: Specific details on the enforcement mechanisms and penalties for non-compliance; Data on the current cybersecurity posture of EU businesses.
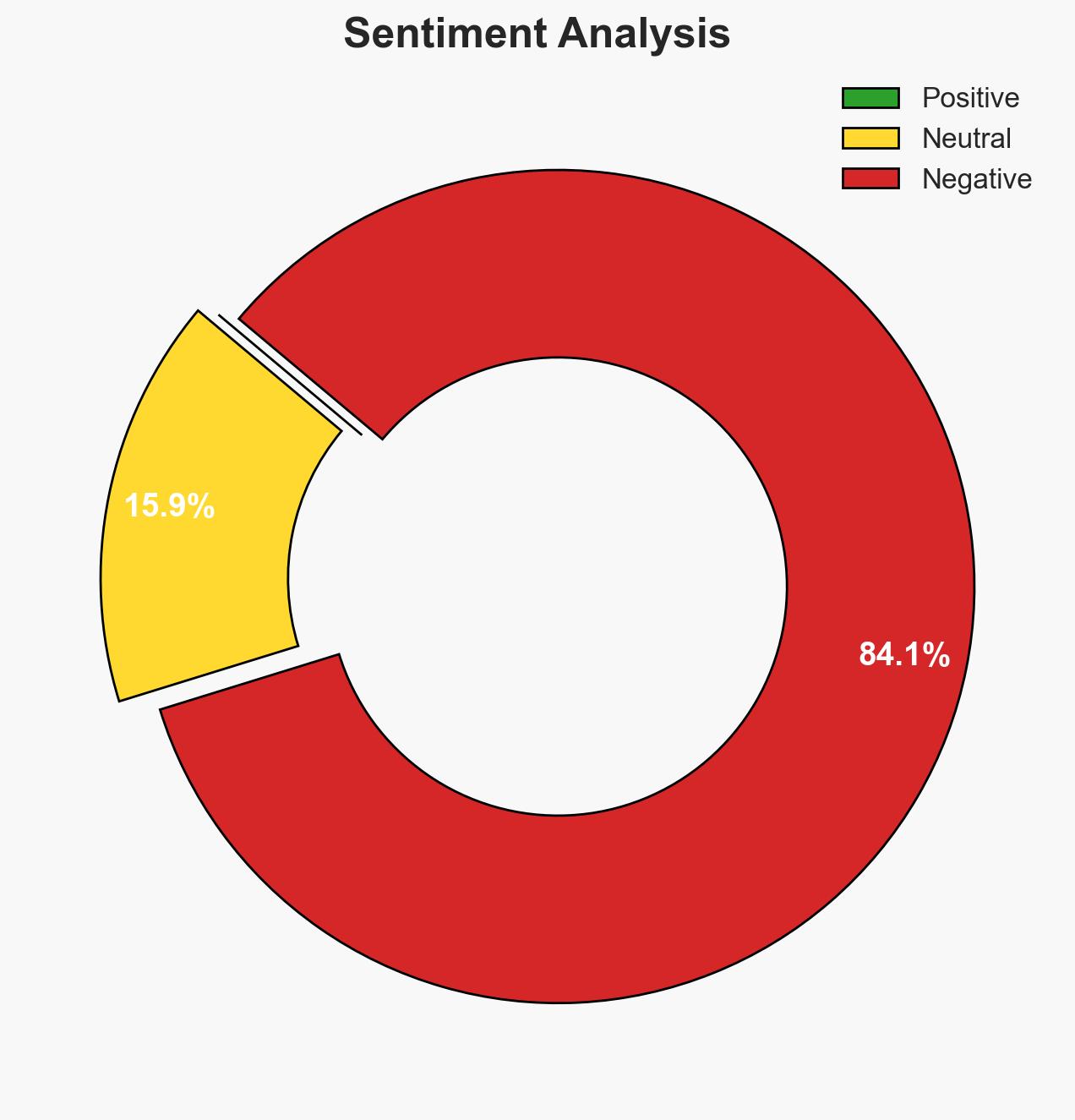
- Bias & Deception Risks: Potential bias in reporting from EU sources emphasizing positive outcomes; Risk of manipulation by third-country suppliers downplaying the security risks of their products.
4. Implications and Strategic Risks
The development could lead to a more secure ICT environment in the EU, but may also strain relationships with non-EU suppliers and complicate trade dynamics.
- Political / Geopolitical: Potential escalation with third countries perceived as high-risk suppliers; Increased EU cohesion on cybersecurity policy.
- Security / Counter-Terrorism: Improved resilience against cyber threats and reduced vulnerability to cyber espionage and attacks.
- Cyber / Information Space: Enhanced cybersecurity standards could deter cybercriminal activities targeting EU infrastructure.
- Economic / Social: Potential short-term economic impact on businesses due to compliance costs; Long-term benefits from increased consumer trust in ICT products.
5. Recommendations and Outlook
- Immediate Actions (0–30 days): Monitor compliance rates and feedback from businesses; Engage with key stakeholders to address concerns and facilitate smooth implementation.
- Medium-Term Posture (1–12 months): Develop partnerships with cybersecurity experts to enhance capability development; Encourage Member States to invest in cybersecurity skills training.
- Scenario Outlook:
- Best: Full compliance leads to a robust cybersecurity environment, enhancing EU’s global standing.
- Worst: Significant non-compliance and geopolitical tensions undermine the initiative’s effectiveness.
- Most-Likely: Gradual improvement in cybersecurity posture with some implementation challenges.
6. Key Individuals and Entities
- European Commission
- ENISA (European Union Agency for Cybersecurity)
- Europol
- National Computer Security Incident Response Teams (CSIRTs)
- Not clearly identifiable from open sources in this snippet.
7. Thematic Tags
cybersecurity, EU policy, ICT supply chain, telecommunications security, ENISA, compliance, geopolitical tensions
Structured Analytic Techniques Applied
- Adversarial Threat Simulation: Model and simulate actions of cyber adversaries to anticipate vulnerabilities and improve resilience.
- Indicators Development: Detect and monitor behavioral or technical anomalies across systems for early threat detection.
- Bayesian Scenario Modeling: Quantify uncertainty and predict cyberattack pathways using probabilistic inference.
- Network Influence Mapping: Map influence relationships to assess actor impact.
Explore more:
Cybersecurity Briefs ·
Daily Summary ·
Support us