EU Urged to Establish Data Security Regulations for Smart Cars, Drawing Insights from China’s Approach
Published on: 2026-02-06
AI-powered OSINT brief from verified open sources. Automated NLP signal extraction with human verification. See our Methodology and Why WorldWideWatchers.
Intelligence Report: EU Needs Smart-Car Data Security Rules And Can Learn From China Group Says
1. BLUF (Bottom Line Up Front)
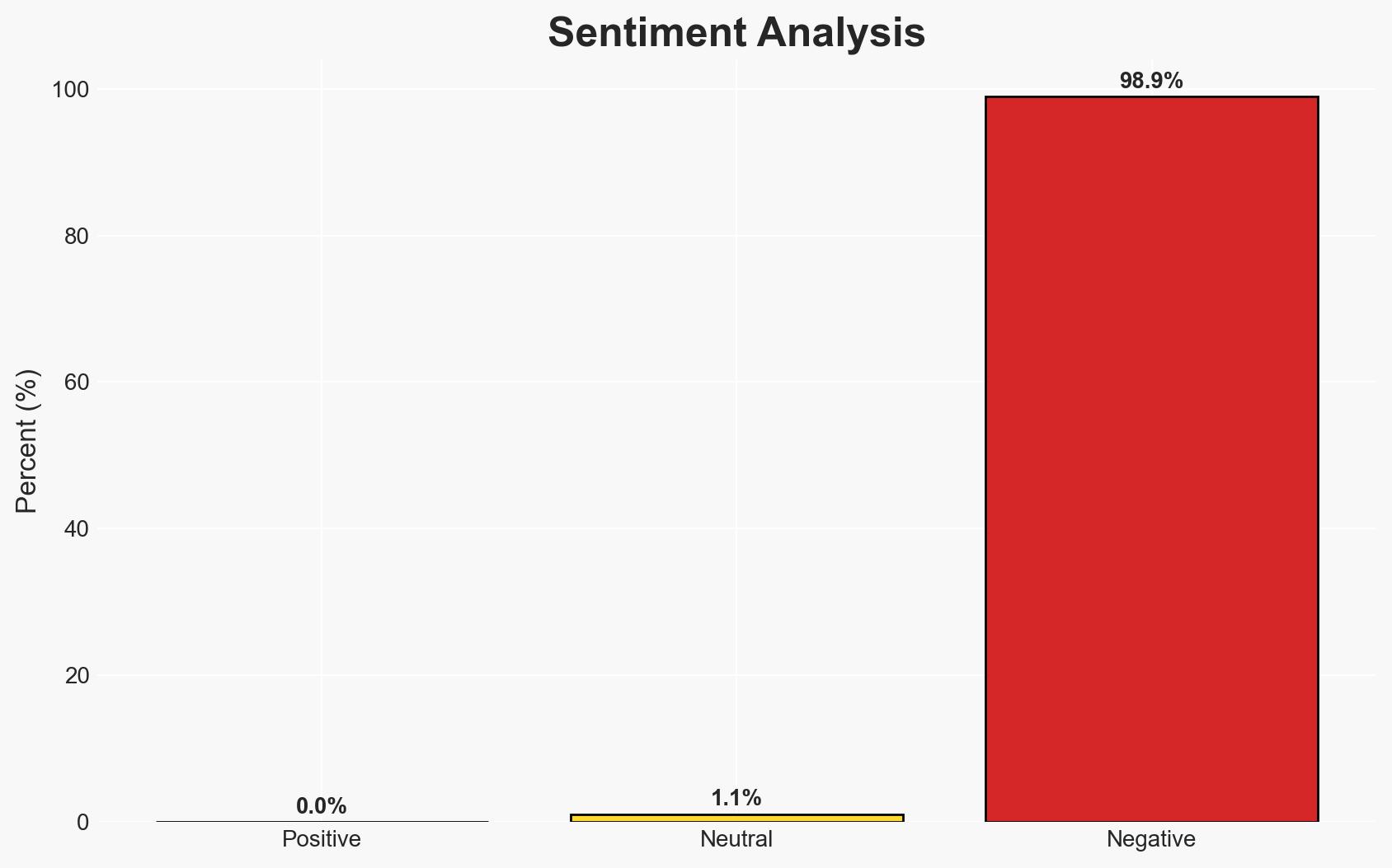
The European Union faces increasing cybersecurity risks from the proliferation of intelligent vehicles, particularly those manufactured in China. The lack of comprehensive EU-wide regulations exacerbates these vulnerabilities. The Center for Eastern Studies suggests that the EU could benefit from adopting regulatory frameworks similar to China’s. This assessment is made with moderate confidence.
2. Competing Hypotheses
- Hypothesis A: The EU’s current lack of regulations on smart-car data security significantly increases its vulnerability to cyber threats and espionage, particularly from Chinese-made vehicles. Supporting evidence includes the rapid increase in Chinese car sales in Europe and the absence of a unified regulatory framework. Key uncertainties include the extent of data collection and potential misuse.
- Hypothesis B: The perceived threat from Chinese smart cars is overstated, and existing national measures are sufficient to mitigate risks. Supporting evidence includes actions by individual countries like Poland and the US. Contradicting evidence includes the lack of a coordinated EU approach and the growing market share of Chinese vehicles.
- Assessment: Hypothesis A is currently better supported due to the significant increase in Chinese vehicle presence and the absence of comprehensive EU regulations. Indicators that could shift this judgment include new EU regulatory initiatives or evidence of effective national measures.
3. Key Assumptions and Red Flags
- Assumptions: The EU will continue to see an increase in Chinese vehicle imports; Chinese vehicles pose a cybersecurity risk; EU lacks effective regulatory measures.
- Information Gaps: Specific data on the extent of data collection by Chinese vehicles and the current effectiveness of national security measures.
- Bias & Deception Risks: Potential bias from the Center for Eastern Studies due to geopolitical tensions; possible underestimation of existing national measures.
4. Implications and Strategic Risks
The proliferation of Chinese smart cars in the EU could lead to increased cybersecurity vulnerabilities and geopolitical tensions. The lack of a unified regulatory framework may exacerbate these risks.
- Political / Geopolitical: Strained EU-China relations and potential for increased regulatory scrutiny.
- Security / Counter-Terrorism: Heightened risk of espionage and data breaches affecting national security.
- Cyber / Information Space: Increased vulnerability to cyberattacks and data exploitation.
- Economic / Social: Potential impact on the automotive market and consumer trust in smart vehicle technology.
5. Recommendations and Outlook
- Immediate Actions (0–30 days): Conduct a comprehensive risk assessment of smart-car data security; initiate dialogue with stakeholders for regulatory development.
- Medium-Term Posture (1–12 months): Develop and implement EU-wide regulations; enhance cross-border information sharing and cybersecurity capabilities.
- Scenario Outlook:
- Best: EU implements effective regulations, mitigating risks and fostering innovation.
- Worst: Continued regulatory inaction leads to significant data breaches and geopolitical tensions.
- Most-Likely: Incremental regulatory progress with ongoing security challenges.
6. Key Individuals and Entities
- Center for Eastern Studies (OSW)
- European Union policymakers
- Chinese automotive manufacturers
- National security agencies in EU member states
7. Thematic Tags
cybersecurity, EU regulations, smart cars, Chinese automotive industry, data privacy, geopolitical tensions, national security
Structured Analytic Techniques Applied
- Adversarial Threat Simulation: Model and simulate actions of cyber adversaries to anticipate vulnerabilities and improve resilience.
- Indicators Development: Detect and monitor behavioral or technical anomalies across systems for early threat detection.
- Bayesian Scenario Modeling: Quantify uncertainty and predict cyberattack pathways using probabilistic inference.
- Network Influence Mapping: Map influence relationships to assess actor impact.
Explore more:
Cybersecurity Briefs ·
Daily Summary ·
Support us