Evaluating Australia’s Terrorism Definition Amid Evolving Threats and Recent Incidents
Published on: 2026-02-08
AI-powered OSINT brief from verified open sources. Automated NLP signal extraction with human verification. See our Methodology and Why WorldWideWatchers.
Intelligence Report: Is Australia’s terrorism definition still fit for purpose
1. BLUF (Bottom Line Up Front)
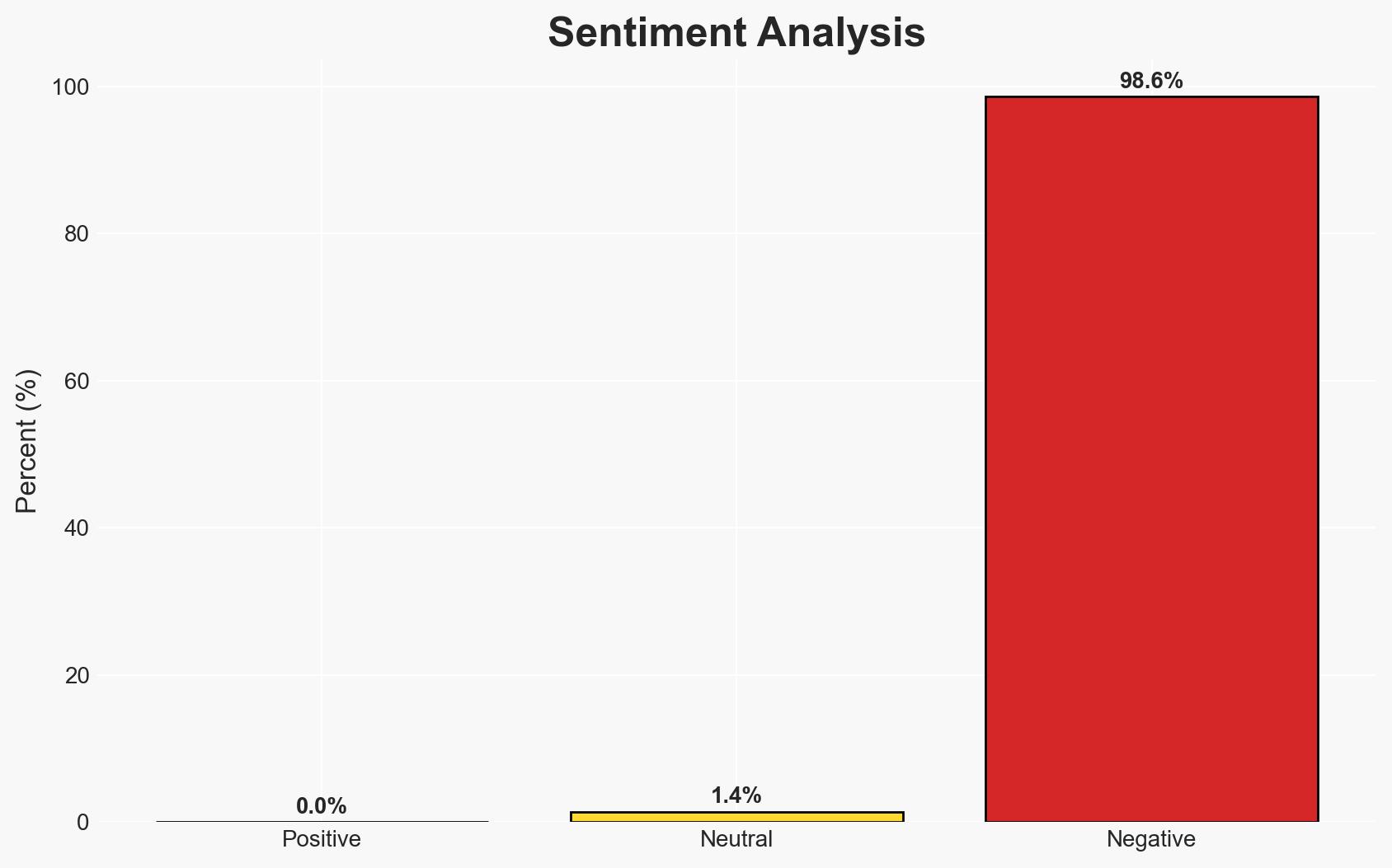
The current legal definition of terrorism in Australia, established in 2002, may not adequately address the evolving threat landscape characterized by diverse actors and motivations. The inquiry by the Independent National Security Legislation Monitor is crucial to assess its relevance. The most likely hypothesis is that the definition requires revision to encompass new forms of extremism and lone-actor threats. Confidence in this assessment is moderate due to evolving threat dynamics and limited data on recent incidents.
2. Competing Hypotheses
- Hypothesis A: The current definition of terrorism in Australia is outdated and insufficient to address contemporary threats, which include diverse actors such as neo-Nazis, incels, and lone actors. Supporting evidence includes the complexity of modern threats and the inquiry initiated by the Independent National Security Legislation Monitor. Key uncertainties include the extent of threat evolution and the effectiveness of current counter-terrorism measures.
- Hypothesis B: The existing definition remains adequate, as it broadly encompasses acts intended to intimidate or coerce for political, religious, or ideological purposes. Contradicting evidence includes the persistence of traditional terrorist groups and the exemption for protest actions. However, this hypothesis is weakened by the lack of specificity in addressing new threat actors.
- Assessment: Hypothesis A is currently better supported due to the explicit recognition of new threat actors and the initiation of a formal review process. Indicators that could shift this judgment include evidence of successful counter-terrorism operations under the current definition and comprehensive data on recent threat incidents.
3. Key Assumptions and Red Flags
- Assumptions: The threat landscape has evolved significantly since 2002; lone actors and non-traditional groups pose a substantial risk; the legal framework must adapt to remain effective.
- Information Gaps: Detailed data on recent threat incidents and their alignment with the current definition; effectiveness of existing counter-terrorism measures against new threats.
- Bias & Deception Risks: Potential cognitive bias in favor of maintaining the status quo; source bias from stakeholders with vested interests in the current legal framework.
4. Implications and Strategic Risks
The evolving threat landscape necessitates a reevaluation of legal definitions to ensure effective counter-terrorism strategies. Failure to adapt could lead to increased vulnerability to diverse extremist threats.
- Political / Geopolitical: Potential for legislative changes and political debate over civil liberties versus security needs.
- Security / Counter-Terrorism: Need for enhanced intelligence capabilities to identify and mitigate threats from non-traditional actors.
- Cyber / Information Space: Increased risk of online radicalization and the spread of extremist ideologies through digital platforms.
- Economic / Social: Potential social unrest or division if legal changes are perceived as targeting specific groups unfairly.
5. Recommendations and Outlook
- Immediate Actions (0–30 days): Initiate comprehensive threat assessments; engage with stakeholders to gather diverse perspectives on the current definition.
- Medium-Term Posture (1–12 months): Develop resilience measures and partnerships to address emerging threats; consider legislative amendments based on inquiry findings.
- Scenario Outlook:
- Best: Revised legal framework effectively addresses new threats, enhancing national security.
- Worst: Failure to adapt leads to increased terrorist activity and public fear.
- Most-Likely: Incremental changes to the legal definition improve threat management, but challenges persist.
6. Key Individuals and Entities
- Independent National Security Legislation Monitor
- Australian Federal Police
- Australian Security Intelligence Organisation
- Not clearly identifiable from open sources in this snippet.
7. Thematic Tags
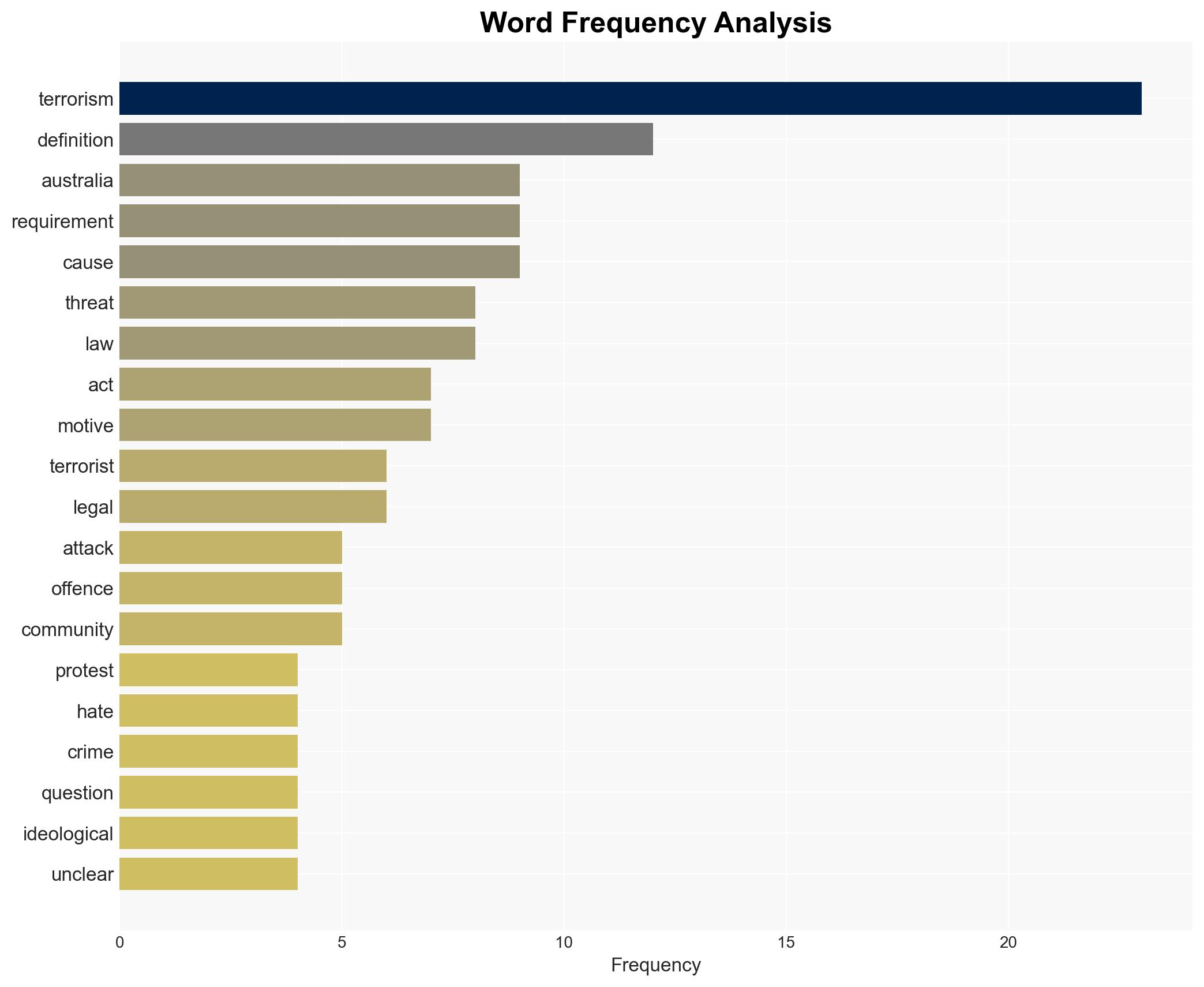
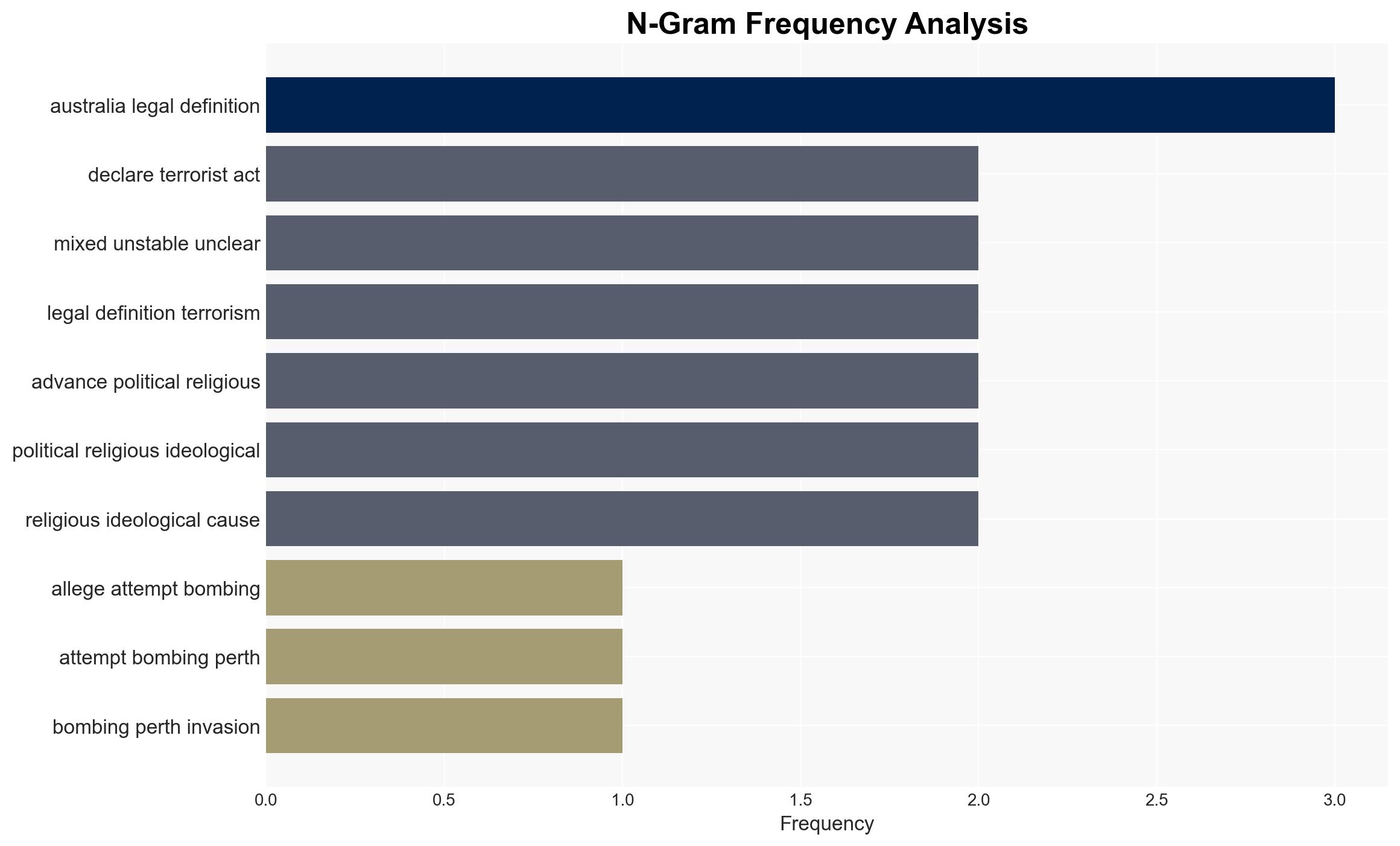
Counter-Terrorism, legal framework, extremism, national security, lone actors, threat assessment, legislative review
Structured Analytic Techniques Applied
- ACH 2.0: Reconstruct likely threat actor intentions via hypothesis testing and structured refutation.
- Indicators Development: Track radicalization signals and propaganda patterns to anticipate operational planning.
- Narrative Pattern Analysis: Deconstruct and track propaganda or influence narratives.
Explore more:
Counter-Terrorism Briefs ·
Daily Summary ·
Support us