Evil Twin WiFi Attacks Target Travelers, Risking Crypto Security at Airports and Public Hotspots
Published on: 2026-01-19
AI-powered OSINT brief from verified open sources. Automated NLP signal extraction with human verification. See our Methodology and Why WorldWideWatchers.
Intelligence Report: Traveling Evil Twin WiFi networks can steal crypto passwords
1. BLUF (Bottom Line Up Front)
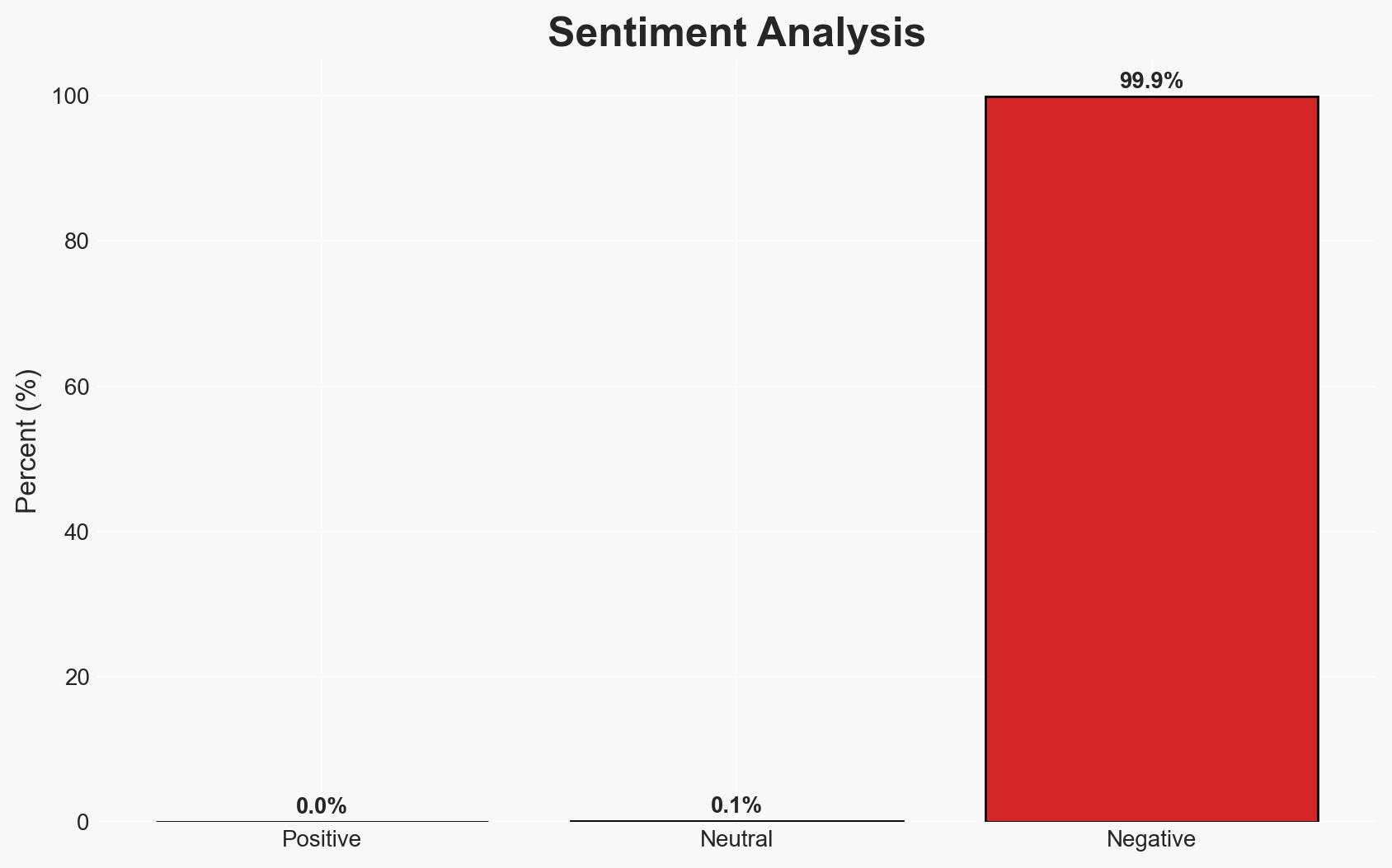
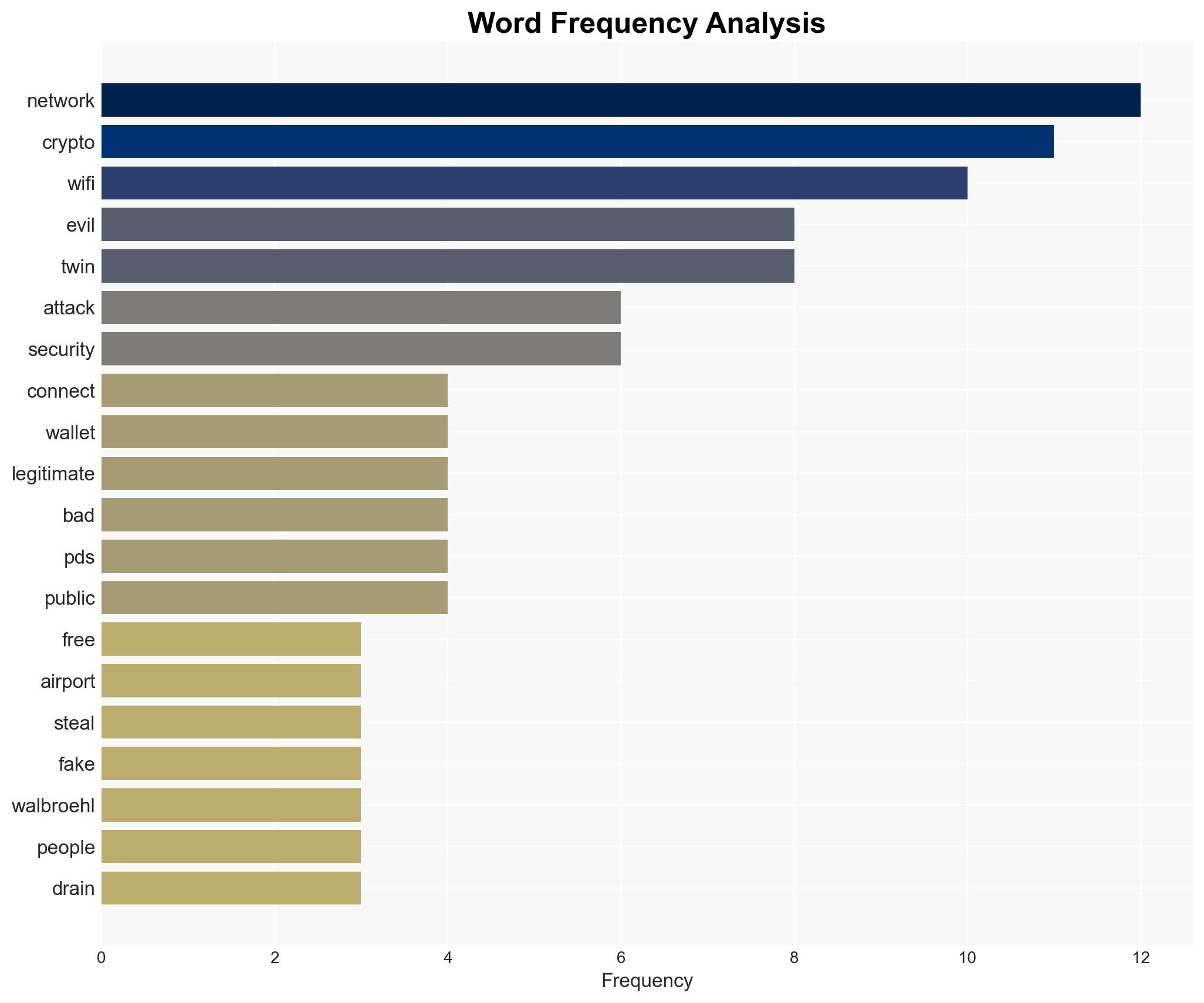
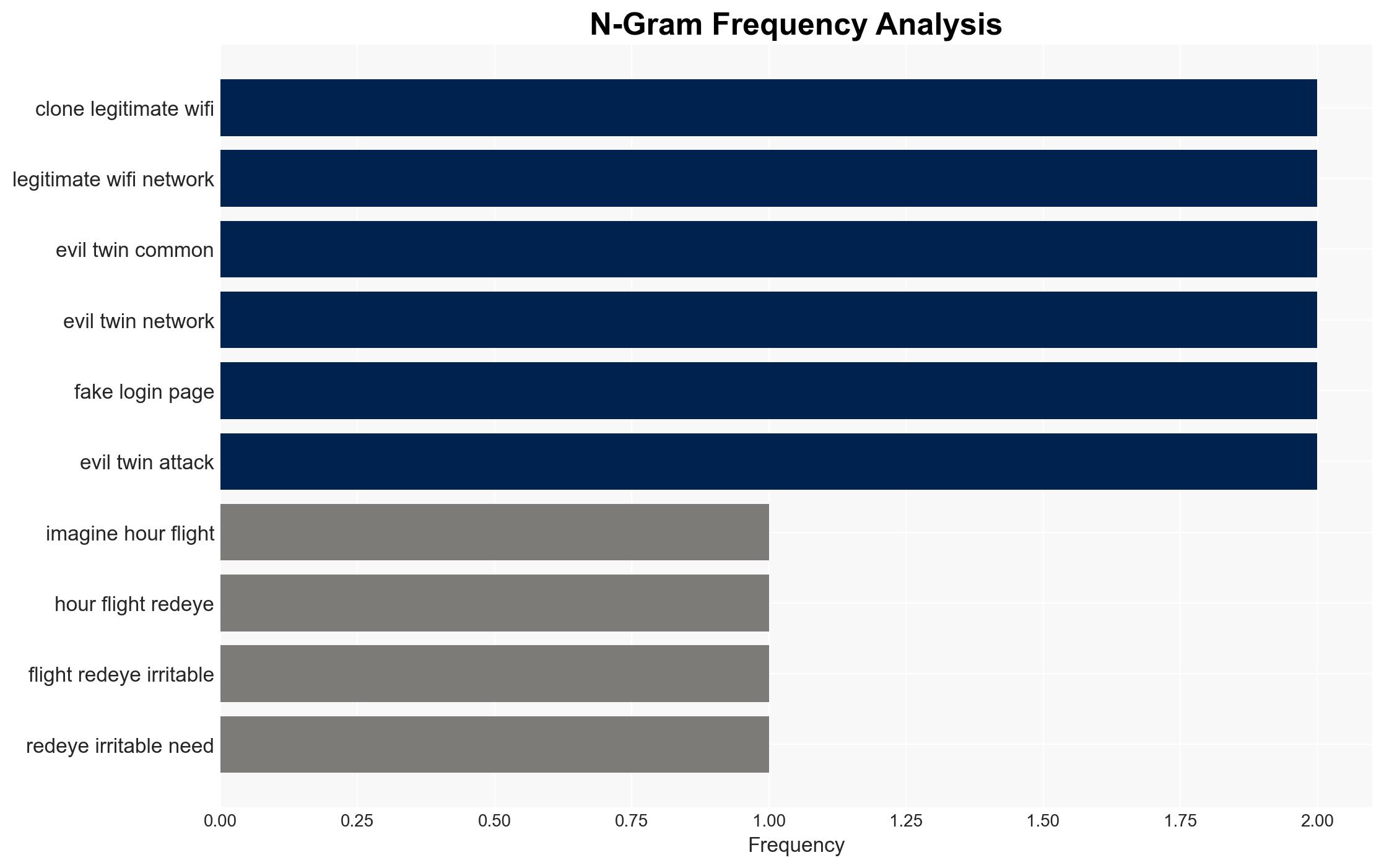
Evil Twin WiFi networks pose a significant threat to cryptocurrency security by exploiting public WiFi environments to steal sensitive information. This attack vector is prevalent in high-traffic areas like airports and cafes, affecting individuals who engage in crypto transactions over unsecured networks. Current assessment supports the hypothesis that these attacks rely heavily on social engineering rather than technical hacking. Overall confidence in this assessment is moderate.
2. Competing Hypotheses
- Hypothesis A: Evil Twin WiFi networks primarily exploit technical vulnerabilities in WiFi encryption to steal cryptocurrency credentials. Evidence contradicts this as experts indicate the attacks rely more on social engineering tactics, such as phishing.
- Hypothesis B: Evil Twin WiFi networks are effective due to social engineering tactics that trick users into revealing sensitive information. This is supported by expert commentary emphasizing phishing and user errors as the main risks.
- Assessment: Hypothesis B is currently better supported, as the evidence indicates that the success of Evil Twin attacks is contingent on social engineering rather than breaking encryption. Indicators that could shift this judgment include new technical vulnerabilities being exploited.
3. Key Assumptions and Red Flags
- Assumptions: Users frequently connect to public WiFi without verifying its legitimacy; attackers have the capability to clone WiFi networks effectively; users are not adequately trained to recognize phishing attempts.
- Information Gaps: Specific data on the frequency and success rate of Evil Twin attacks; detailed profiles of typical victims; technical specifics on how attackers clone networks.
- Bias & Deception Risks: Source bias may exist as cybersecurity firms have an interest in highlighting threats; potential underreporting of incidents due to victim embarrassment or lack of awareness.
4. Implications and Strategic Risks
This development could lead to increased regulatory scrutiny on public WiFi security and heightened awareness campaigns. Over time, the sophistication of attacks may evolve, potentially leading to more complex social engineering tactics.
- Political / Geopolitical: Potential for international cooperation on cybersecurity standards for public WiFi networks.
- Security / Counter-Terrorism: Increased risk of financial crimes linked to terrorism financing if crypto thefts are not mitigated.
- Cyber / Information Space: Growing need for robust cybersecurity measures and public education on digital hygiene.
- Economic / Social: Potential loss of trust in public WiFi networks, impacting tourism and business travel.
5. Recommendations and Outlook
- Immediate Actions (0–30 days): Enhance public awareness campaigns on the risks of public WiFi; encourage the use of VPNs and secure connections.
- Medium-Term Posture (1–12 months): Develop partnerships with tech firms to create more secure public WiFi solutions; implement training programs for recognizing phishing attempts.
- Scenario Outlook: Best: Increased public awareness reduces attack success; Worst: Attack sophistication outpaces security measures; Most-Likely: Continued prevalence of attacks with gradual improvements in user awareness.
6. Key Individuals and Entities
- Steven Walbroehl, co-founder of Halborn
- 23pds, Chief Information Security Officer at SlowMist
- Not clearly identifiable from open sources in this snippet.
7. Thematic Tags
cybersecurity, social engineering, cryptocurrency, public WiFi, phishing, cybercrime, digital hygiene
Structured Analytic Techniques Applied
- Adversarial Threat Simulation: Model and simulate actions of cyber adversaries to anticipate vulnerabilities and improve resilience.
- Indicators Development: Detect and monitor behavioral or technical anomalies across systems for early threat detection.
- Bayesian Scenario Modeling: Quantify uncertainty and predict cyberattack pathways using probabilistic inference.
- Network Influence Mapping: Map influence relationships to assess actor impact.
Explore more:
Cybersecurity Briefs ·
Daily Summary ·
Support us