Excessive Use of LOLBins Aids in Deployment of Remote Access Trojans
Published on: 2026-01-21
AI-powered OSINT brief from verified open sources. Automated NLP signal extraction with human verification. See our Methodology and Why WorldWideWatchers.
Intelligence Report: Can you use too many LOLBins to drop some RATs
1. BLUF (Bottom Line Up Front)
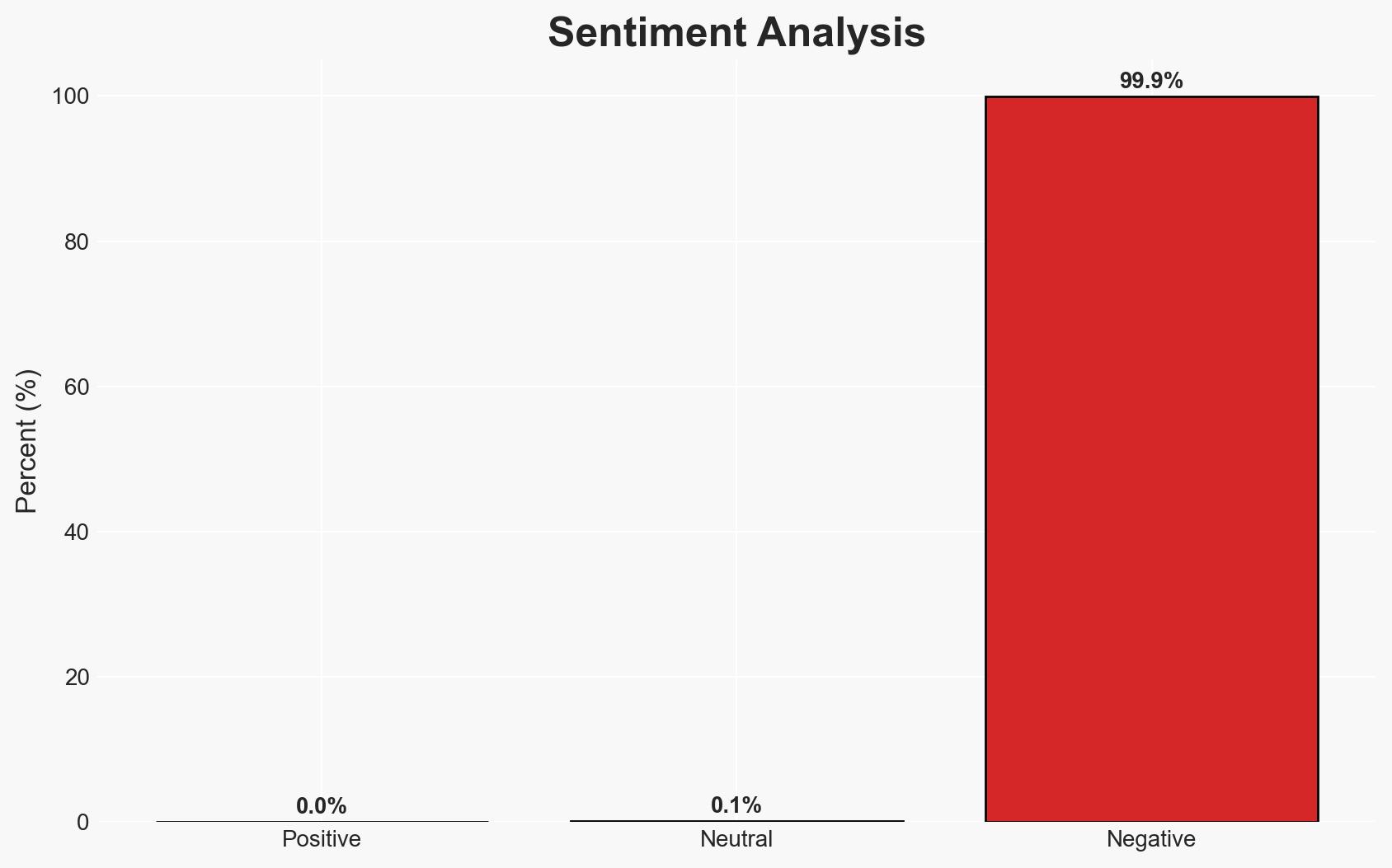
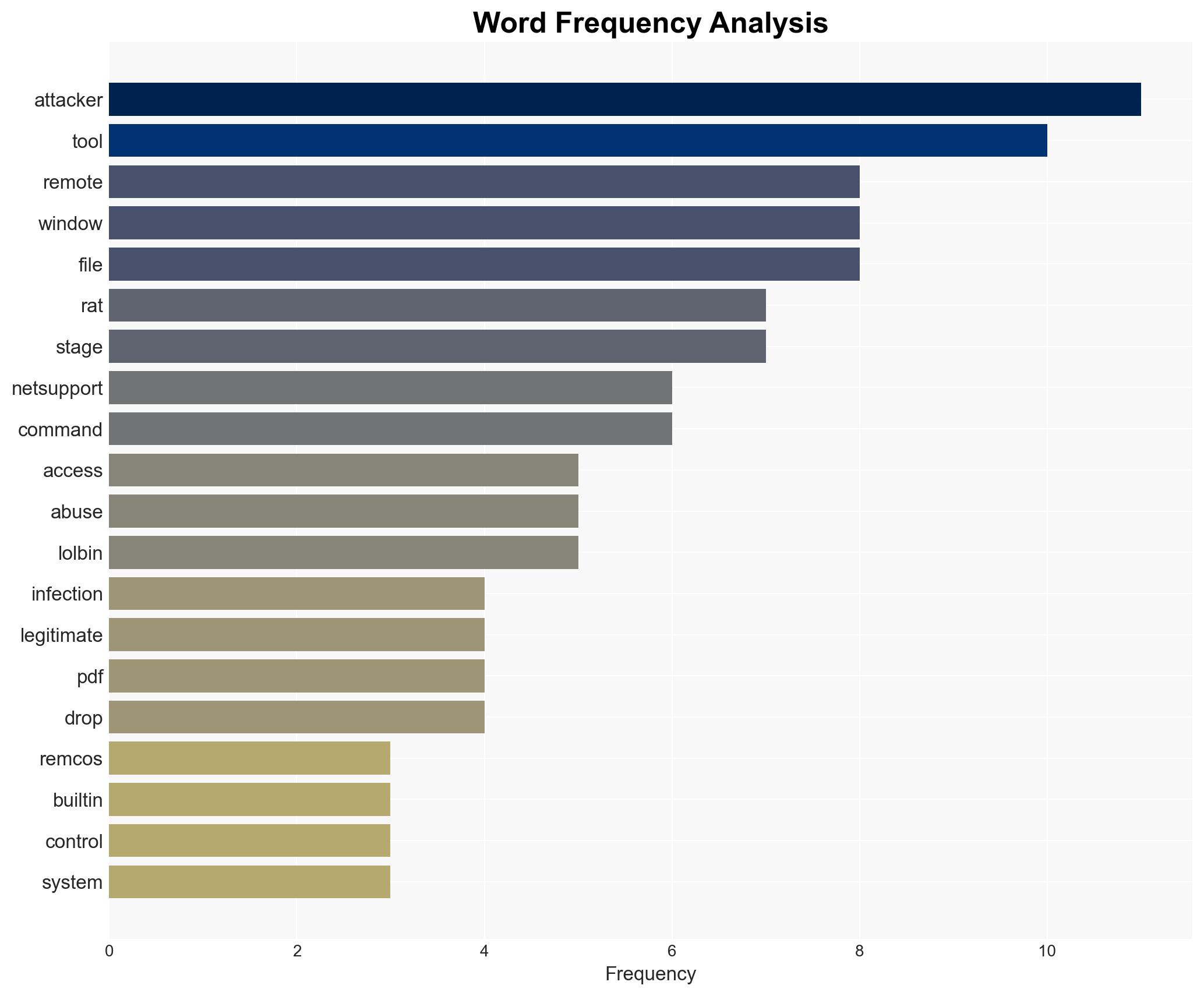
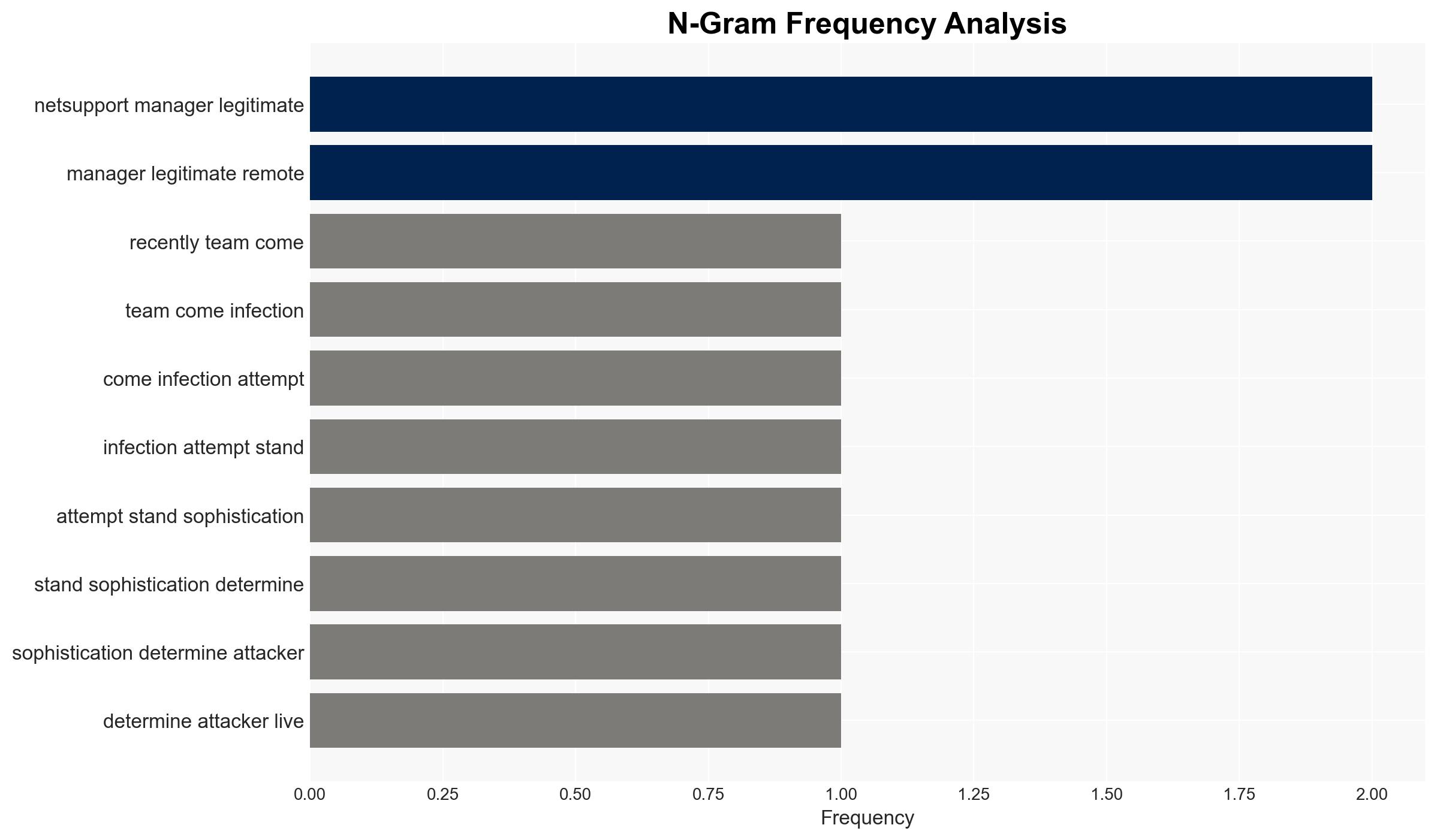
The recent cyber attack leveraged Windows’ built-in utilities, known as LOLBins, to deploy Remcos and NetSupport Manager as Remote Access Trojans (RATs). This method underscores a trend towards using legitimate tools for malicious purposes, complicating detection and response efforts. The primary affected parties include organizations using Windows systems. Overall confidence in this assessment is moderate due to the limited scope of the data.
2. Competing Hypotheses
- Hypothesis A: The attack is part of a broader campaign by a sophisticated actor exploiting LOLBins to evade detection. Supporting evidence includes the strategic use of legitimate tools to obscure malicious activities. However, the lack of sophistication in the attack suggests a less advanced actor.
- Hypothesis B: The attack is an isolated incident by an opportunistic actor experimenting with LOLBins. This is supported by the apparent lack of sophistication and the use of widely known tools like Remcos and NetSupport Manager. Contradicting this is the determined approach and multi-stage execution, which may indicate more strategic intent.
- Assessment: Hypothesis B is currently better supported due to the simplicity of the attack and the use of common tools. Key indicators that could shift this judgment include evidence of coordinated attacks or advanced techniques in future incidents.
3. Key Assumptions and Red Flags
- Assumptions: The attacker has basic to moderate technical skills; the use of LOLBins is primarily for defense evasion; the primary goal is unauthorized access and control.
- Information Gaps: Details on the attacker’s identity, broader campaign context, and specific targets remain unknown.
- Bias & Deception Risks: Potential confirmation bias in interpreting the attack as unsophisticated; possible deception by the attacker to appear less capable than they are.
4. Implications and Strategic Risks
The use of LOLBins for deploying RATs could signal a shift towards more covert cyber operations, complicating detection and response efforts. This development may encourage similar tactics among other threat actors.
- Political / Geopolitical: Increased cyber tensions if linked to state-sponsored actors.
- Security / Counter-Terrorism: Heightened threat landscape due to more actors adopting these techniques.
- Cyber / Information Space: Challenges in cyber defense due to the use of legitimate tools for malicious purposes.
- Economic / Social: Potential economic impact from data breaches and system compromises.
5. Recommendations and Outlook
- Immediate Actions (0–30 days): Enhance monitoring of LOLBins usage, update detection signatures, and conduct awareness training on phishing and social engineering tactics.
- Medium-Term Posture (1–12 months): Develop partnerships for threat intelligence sharing, invest in advanced behavioral analytics, and strengthen incident response capabilities.
- Scenario Outlook:
- Best: Improved detection and mitigation techniques reduce the effectiveness of LOLBin-based attacks.
- Worst: Widespread adoption of these techniques leads to significant data breaches and operational disruptions.
- Most-Likely: Continued sporadic use of LOLBins by various actors, with incremental improvements in detection and response.
6. Key Individuals and Entities
- Not clearly identifiable from open sources in this snippet.
7. Thematic Tags
cybersecurity, LOLBins, remote access trojans, defense evasion, cyber threat intelligence, incident response, phishing
Structured Analytic Techniques Applied
- Adversarial Threat Simulation: Model and simulate actions of cyber adversaries to anticipate vulnerabilities and improve resilience.
- Indicators Development: Detect and monitor behavioral or technical anomalies across systems for early threat detection.
- Bayesian Scenario Modeling: Quantify uncertainty and predict cyberattack pathways using probabilistic inference.
Explore more:
Cybersecurity Briefs ·
Daily Summary ·
Support us