Exein secures €100 million funding to enhance cybersecurity for IoT devices and expand globally
Published on: 2025-12-18
AI-powered OSINT brief from verified open sources. Automated NLP signal extraction with human verification. See our Methodology and Why WorldWideWatchers.
Intelligence Report: Exein closes 100M round to harden security in internet of things devices
1. BLUF (Bottom Line Up Front)
Exein’s recent €100 million funding round positions it as a significant player in the cybersecurity market for IoT devices, potentially enhancing global cybersecurity resilience. The company’s expansion into critical infrastructure sectors could mitigate risks associated with IoT vulnerabilities. This assessment is made with moderate confidence due to existing information gaps about the company’s operational efficacy and market penetration.
2. Competing Hypotheses
- Hypothesis A: Exein’s funding and expansion will significantly enhance IoT cybersecurity, reducing vulnerabilities and associated risks. Supporting evidence includes the substantial investment and the company’s claims of protecting over a billion devices. However, uncertainties remain regarding the scalability and effectiveness of their solutions in diverse environments.
- Hypothesis B: Despite the funding, Exein’s impact on IoT cybersecurity will be limited due to potential over-reliance on self-reported metrics and challenges in integrating with existing systems. Contradicting evidence includes the lack of independent verification of their claims and potential market competition.
- Assessment: Hypothesis A is currently better supported due to the significant financial backing and strategic partnerships with major manufacturers. Key indicators that could shift this judgment include independent assessments of their technology’s effectiveness and market adoption rates.
3. Key Assumptions and Red Flags
- Assumptions: Exein’s technology is effective across various IoT environments; the reported metrics accurately reflect operational success; market demand for IoT security solutions will continue to grow.
- Information Gaps: Independent evaluations of Exein’s technology performance; detailed market penetration data; competitor analysis in the IoT security sector.
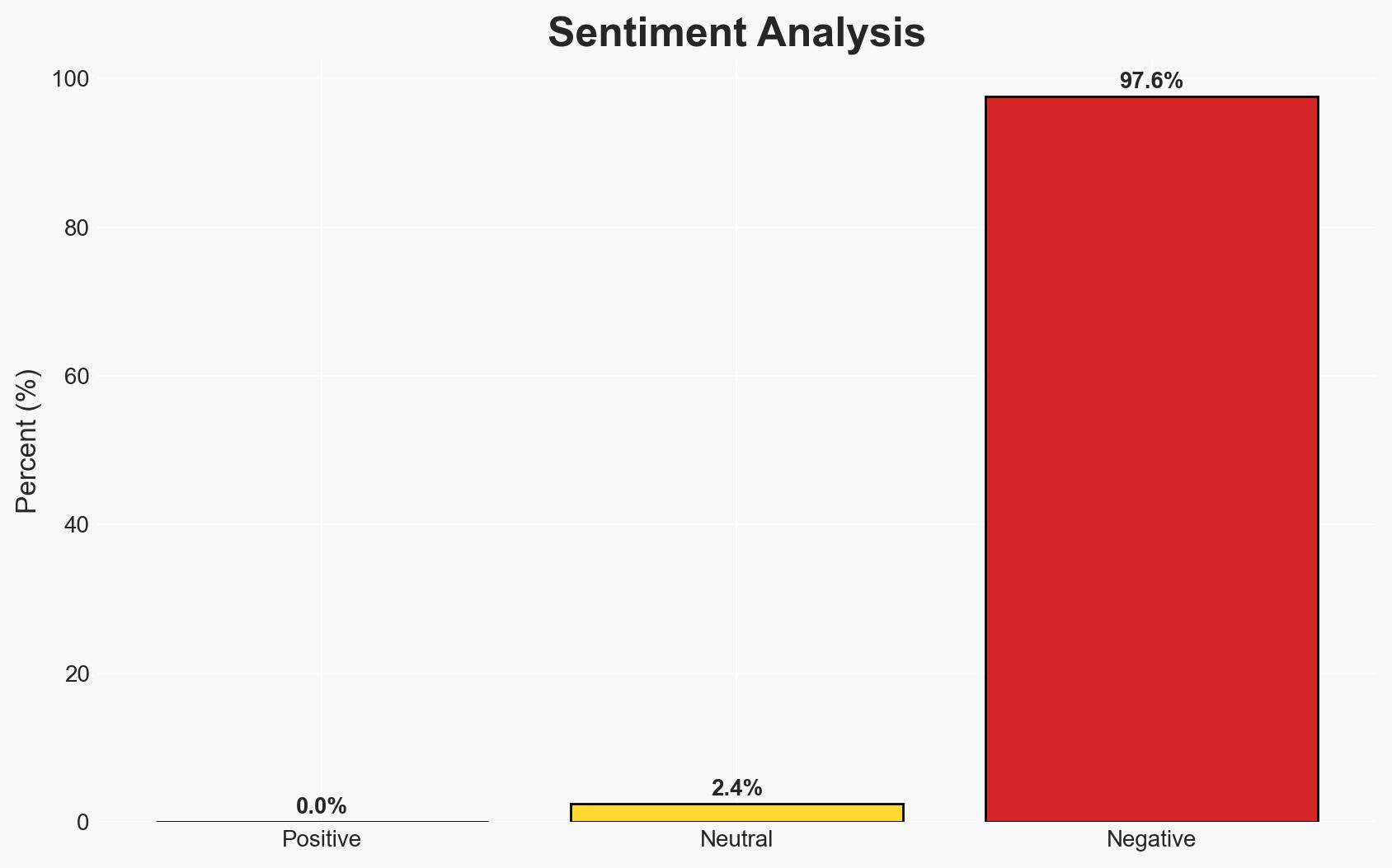
- Bias & Deception Risks: Potential bias in self-reported success metrics; investor-driven optimism may skew public statements; lack of transparency in technology efficacy claims.
4. Implications and Strategic Risks
The development of Exein’s platform could significantly influence the cybersecurity landscape, particularly for IoT devices, by setting new standards for embedded security solutions.
- Political / Geopolitical: Enhanced IoT security could reduce state-level cyber espionage risks, but may also provoke adversarial states to develop countermeasures.
- Security / Counter-Terrorism: Improved device security could mitigate risks of cyberattacks on critical infrastructure, reducing potential vectors for terrorism.
- Cyber / Information Space: The proliferation of Exein’s technology may drive innovation in cybersecurity, but also increase competition and potential for cyber arms races.
- Economic / Social: Strengthened IoT security could bolster economic stability by protecting critical infrastructure and supply chains, but may also increase costs for device manufacturers.
5. Recommendations and Outlook
- Immediate Actions (0–30 days): Monitor Exein’s integration into critical infrastructure sectors; assess independent evaluations of their technology.
- Medium-Term Posture (1–12 months): Encourage partnerships between Exein and key industry stakeholders; develop resilience measures for potential cybersecurity threats.
- Scenario Outlook:
- Best: Exein’s technology becomes a standard, significantly reducing IoT vulnerabilities.
- Worst: Exein fails to deliver on promises, leading to increased vulnerabilities and investor losses.
- Most-Likely: Exein moderately enhances IoT security, with gradual market adoption and technological improvements.
6. Key Individuals and Entities
- Gianni Cuozzo, Founder and CEO of Exein
- Blue Cloud Ventures, Investor
- HV Capital, Investor
- Intrepid Growth Partners, Investor
- Geodesic, Investor
- J.P. Morgan, Investor
- Kontron, Partner
- MediaTek, Partner
7. Thematic Tags
cybersecurity, internet of things, investment, critical infrastructure, embedded systems, global expansion, technology partnerships
Structured Analytic Techniques Applied
- Adversarial Threat Simulation: Model and simulate actions of cyber adversaries to anticipate vulnerabilities and improve resilience.
- Indicators Development: Detect and monitor behavioral or technical anomalies across systems for early threat detection.
- Bayesian Scenario Modeling: Quantify uncertainty and predict cyberattack pathways using probabilistic inference.
- Network Influence Mapping: Map influence relationships to assess actor impact.
Explore more:
Cybersecurity Briefs ·
Daily Summary ·
Support us