Exploit Attempts for Recent Langflow AI Vulnerability CVE-2025-3248 Sat Apr 12th – Sans.edu
Published on: 2025-04-13
Intelligence Report: Exploit Attempts for Recent Langflow AI Vulnerability CVE-2025-3248 Sat Apr 12th – Sans.edu
1. BLUF (Bottom Line Up Front)
A critical vulnerability in Langflow AI, identified as CVE-2025-3248, has been actively exploited following its disclosure. The vulnerability allows unauthorized remote code execution, posing significant risks to systems using Langflow. Immediate action is required to mitigate potential impacts on affected systems, especially those exposed to the internet.
2. Detailed Analysis
The following structured analytic techniques have been applied for this analysis:
General Analysis
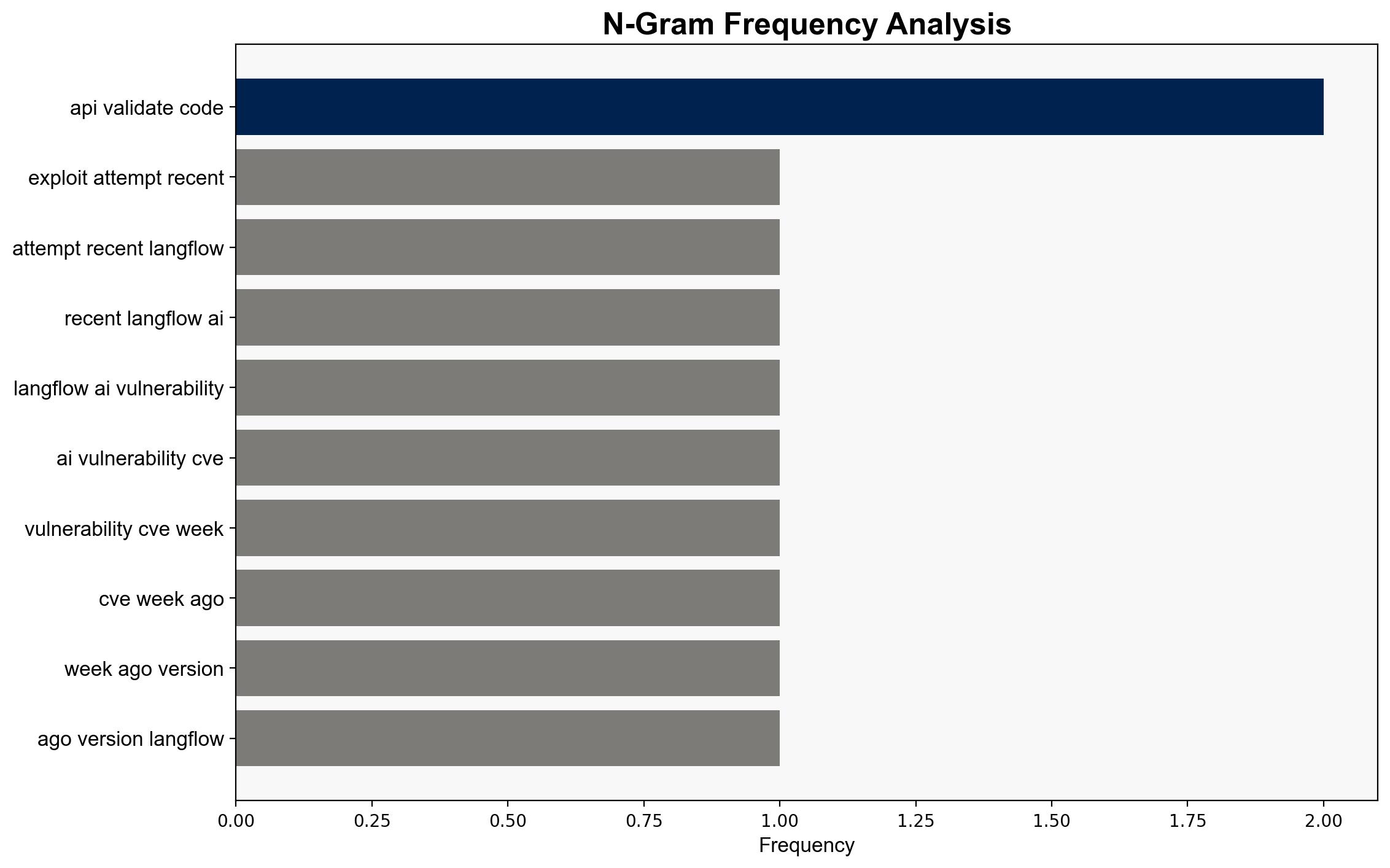
The vulnerability in Langflow AI was inadvertently disclosed in version 1.3.0 release notes. Horizon3’s detailed writeup on April 9th highlighted the ease of exploitation, leading to a surge in exploit attempts. The primary attack vector involves sending malicious payloads to the “/api/v1/validate/code” endpoint to execute arbitrary commands. Initial exploit attempts were detected on April 10th, with a significant increase by April 12th. All observed attempts originated from TOR exit nodes, indicating potential anonymity efforts by attackers.
3. Implications and Strategic Risks
The exploitation of CVE-2025-3248 poses several strategic risks:
- National Security: Compromised systems could be leveraged for further attacks, data exfiltration, or as part of a botnet.
- Regional Stability: Widespread exploitation could disrupt critical infrastructure relying on Langflow AI.
- Economic Interests: Organizations using Langflow may face operational disruptions, financial losses, and reputational damage.
4. Recommendations and Outlook
Recommendations:
- Urgently apply patches or workarounds to secure systems running Langflow AI.
- Enhance monitoring for unusual activity, particularly from TOR exit nodes.
- Consider regulatory measures to mandate disclosure of vulnerabilities and timely patching.
- Invest in technological solutions to detect and prevent unauthorized code execution.
Outlook:
Best-case scenario: Rapid patch deployment and increased awareness lead to a decline in successful exploit attempts.
Worst-case scenario: Delayed response results in widespread exploitation, causing significant disruptions.
Most likely outcome: A moderate level of exploitation persists until comprehensive mitigation measures are implemented.
5. Key Individuals and Entities
The report references Horizon3 as a key entity in identifying and publicizing the vulnerability. Johannes B. Ullrich is mentioned as the author of the source text.