Exploiting Process Environment Block to Conceal Malicious Activity in Windows
Published on: 2026-01-09
AI-powered OSINT brief from verified open sources. Automated NLP signal extraction with human verification. See our Methodology and Why WorldWideWatchers.
Intelligence Report: Malicious Process Environment Block Manipulation Fri Jan 9th
1. BLUF (Bottom Line Up Front)
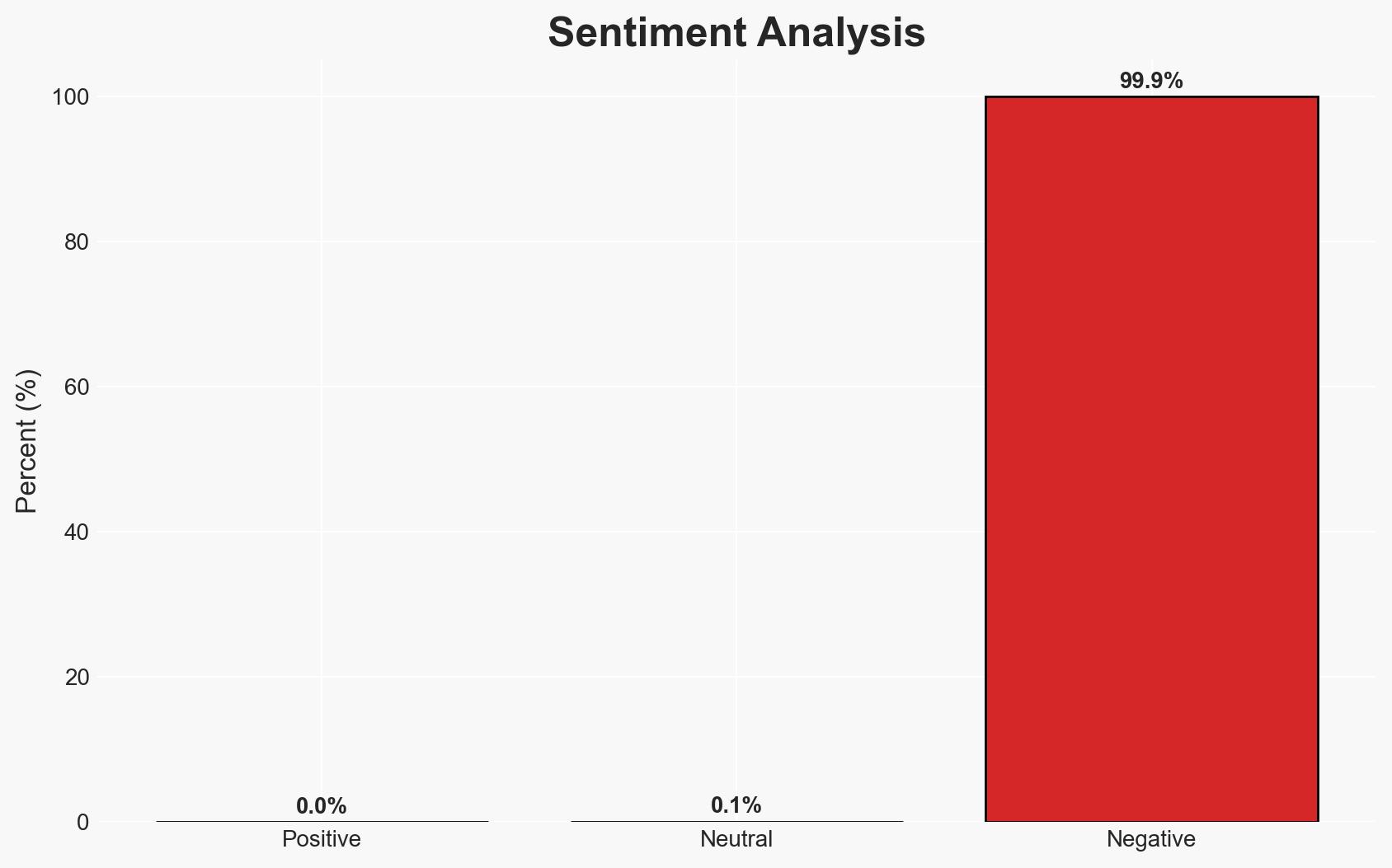
The manipulation of the Process Environment Block (PEB) by malware to hide malicious activities poses a significant threat to cybersecurity, particularly in environments reliant on Windows operating systems. The most likely hypothesis is that threat actors are increasingly utilizing this technique to evade detection by security software. This assessment is made with moderate confidence due to the technical complexity involved and the potential for widespread impact.
2. Competing Hypotheses
- Hypothesis A: Threat actors are using PEB manipulation to conceal malicious processes, thereby evading detection by traditional security measures. This is supported by the technical feasibility of the method and the increasing sophistication of malware.
- Hypothesis B: PEB manipulation is primarily a proof-of-concept or used in limited, targeted attacks rather than widespread deployment. This is supported by the lack of widespread reports of this technique being used in the wild.
- Assessment: Hypothesis A is currently better supported due to the documented capability of malware to manipulate PEBs and the ongoing trend of malware evolution towards more stealthy operations. Indicators that could shift this judgment include reports of widespread exploitation or new detection methods being developed.
3. Key Assumptions and Red Flags
- Assumptions: Malware developers have the technical capability to implement PEB manipulation; security tools are not fully equipped to detect such manipulations; Windows operating systems remain a primary target.
- Information Gaps: The prevalence of PEB manipulation in active malware campaigns; effectiveness of current detection and mitigation strategies.
- Bias & Deception Risks: Confirmation bias in assuming all sophisticated malware employs PEB manipulation; potential for misdirection by threat actors showcasing this technique while using others.
4. Implications and Strategic Risks
The development of PEB manipulation techniques could lead to more sophisticated and stealthy malware campaigns, challenging current cybersecurity defenses and potentially increasing the success rate of cyber-attacks.
- Political / Geopolitical: Increased cyber tensions between nation-states as advanced persistent threats (APTs) may adopt these techniques.
- Security / Counter-Terrorism: Enhanced threat landscape requiring updated security protocols and training for cybersecurity personnel.
- Cyber / Information Space: Potential for significant breaches of sensitive information if PEB manipulation is widely adopted by cybercriminals.
- Economic / Social: Increased costs for businesses to upgrade security measures and potential loss of consumer trust in digital services.
5. Recommendations and Outlook
- Immediate Actions (0–30 days): Enhance monitoring of process creation and modification activities on Windows systems; update security software to detect PEB manipulation attempts.
- Medium-Term Posture (1–12 months): Develop partnerships with cybersecurity firms to share intelligence on emerging threats; invest in research to develop new detection techniques for PEB manipulation.
- Scenario Outlook:
- Best: Effective detection methods are developed, minimizing the impact of PEB manipulation.
- Worst: Widespread adoption of PEB manipulation leads to significant data breaches and economic damage.
- Most-Likely: Incremental adoption of PEB manipulation by sophisticated threat actors, with ongoing challenges in detection and response.
6. Key Individuals and Entities
- Not clearly identifiable from open sources in this snippet.
7. Thematic Tags
cybersecurity, malware, PEB manipulation, Windows OS, threat detection, cyber defense, information security
Structured Analytic Techniques Applied
- Adversarial Threat Simulation: Model and simulate actions of cyber adversaries to anticipate vulnerabilities and improve resilience.
- Indicators Development: Detect and monitor behavioral or technical anomalies across systems for early threat detection.
- Bayesian Scenario Modeling: Forecast futures under uncertainty via probabilistic logic.
Explore more:
Cybersecurity Briefs ·
Daily Summary ·
Support us