Exposure validation emerges as critical cyber defense component – Help Net Security
Published on: 2025-04-25
Intelligence Report: Exposure Validation Emerges as Critical Cyber Defense Component – Help Net Security
1. BLUF (Bottom Line Up Front)
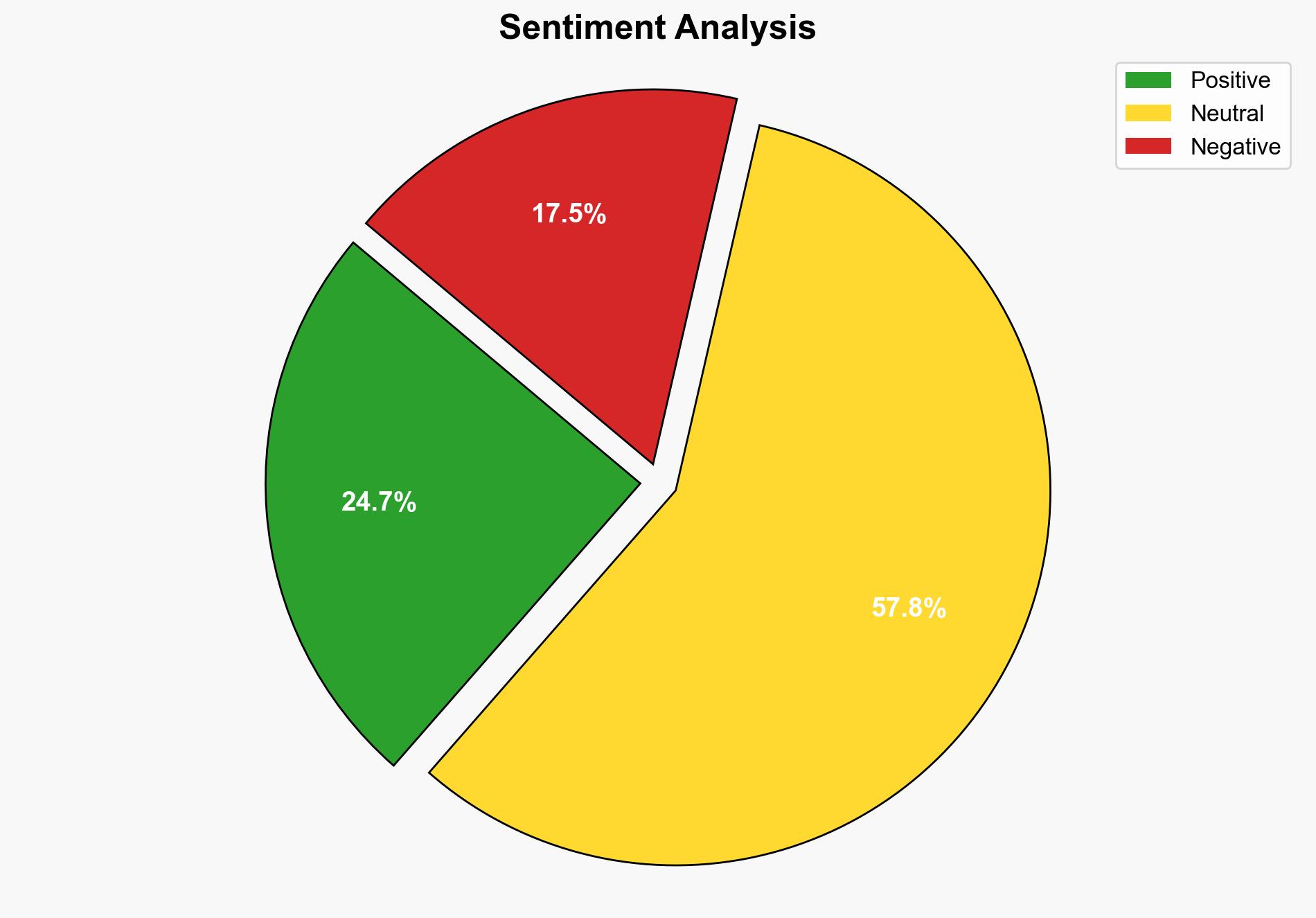
Exposure validation is increasingly recognized as a crucial component of cybersecurity strategies. Organizations are adopting exposure validation to enhance threat detection and improve resilience against sophisticated cyber threats. Automation and AI are pivotal in this shift, enabling continuous testing and monitoring. Key recommendations include prioritizing automated exposure validation processes and integrating AI to optimize threat management.
2. Detailed Analysis
The following structured analytic techniques have been applied to ensure methodological consistency:
Analysis of Competing Hypotheses (ACH)
Exposure validation is assessed against alternative cybersecurity strategies. Evidence supports its effectiveness in reducing breach incidents and improving detection times, making it a preferred approach over traditional methods like manual penetration testing.
SWOT Analysis
Strengths: Enhanced threat detection and resilience. Weaknesses: Resource constraints and gaps in manual testing. Opportunities: Integration of AI and automation. Threats: Increasing sophistication of cyber threats.
Indicators Development
Indicators such as increased automation in threat testing and AI integration are monitored to track the effectiveness of exposure validation in real-time threat management.
3. Implications and Strategic Risks
The shift towards automated exposure validation presents both opportunities and risks. While it enhances threat detection, reliance on technology could introduce vulnerabilities if not properly managed. The evolving threat landscape requires continuous adaptation and resource allocation to maintain effective defenses.
4. Recommendations and Outlook
- Implement automated exposure validation processes to enhance threat detection capabilities.
- Invest in AI technologies to support continuous monitoring and testing.
- Scenario-based projections: Best case: Significant reduction in breach incidents. Worst case: Over-reliance on technology leading to new vulnerabilities. Most likely: Gradual improvement in threat resilience with increased AI integration.
5. Key Individuals and Entities
Avihai Ben-Yossef
6. Thematic Tags
(‘cybersecurity’, ‘national security threats’, ‘automation’, ‘AI integration’)