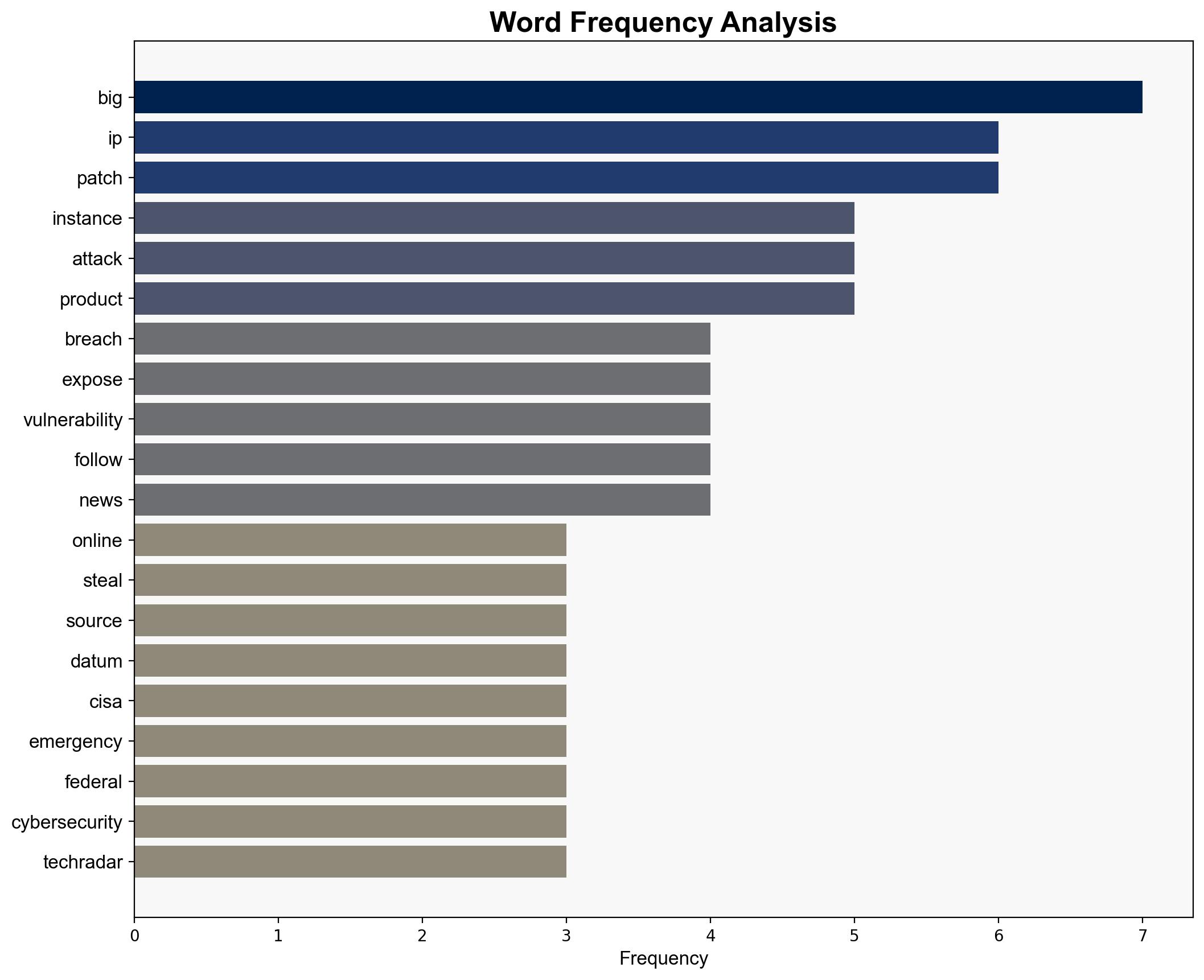
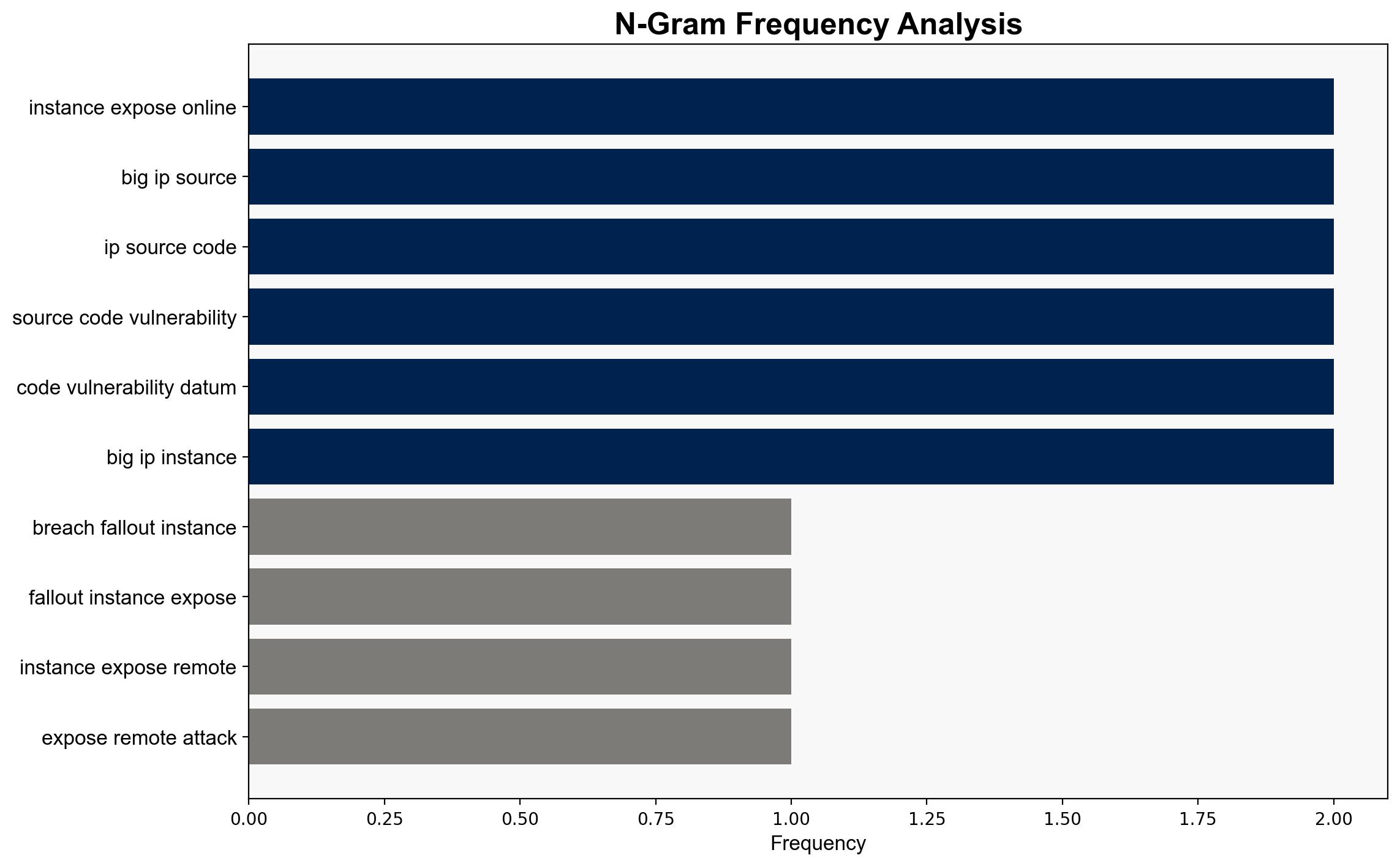
F5 breach fallout – over 266000 instances exposed to remote attacks – TechRadar
Published on: 2025-10-20
Intelligence Report: F5 breach fallout – over 266000 instances exposed to remote attacks – TechRadar
1. BLUF (Bottom Line Up Front)
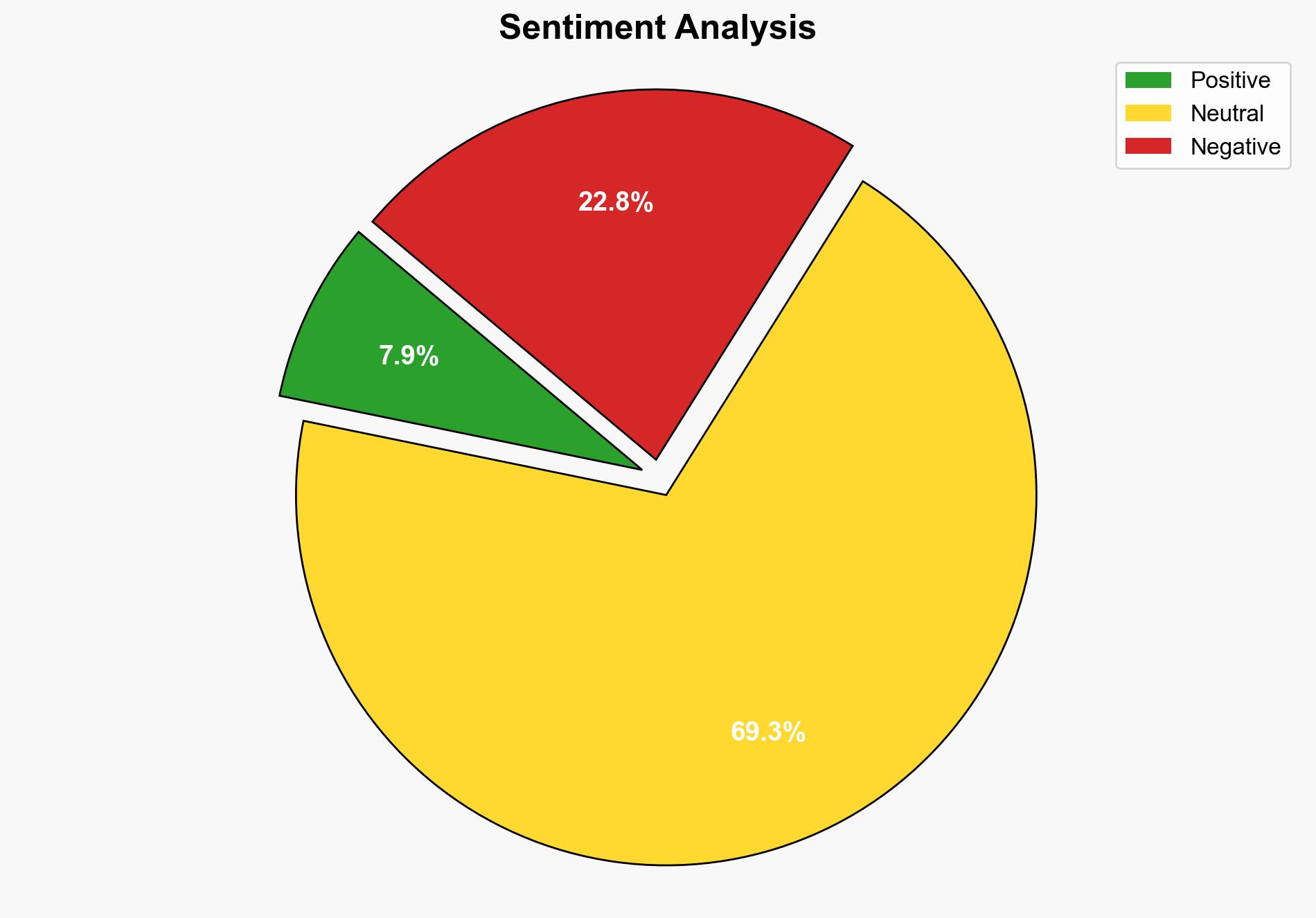
The most supported hypothesis is that the F5 breach represents a significant cybersecurity threat, primarily driven by nation-state actors exploiting vulnerabilities in critical infrastructure. Confidence level is moderate due to the lack of direct evidence of exploitation in the wild. Immediate action is recommended to patch vulnerabilities and enhance monitoring of exposed systems.
2. Competing Hypotheses
1. **Hypothesis A**: Nation-state actors are actively exploiting the F5 vulnerabilities to gain access to sensitive networks, particularly in the United States, Europe, and Asia. This is supported by the involvement of nation-state affiliated cyber threat actors and the strategic importance of the targeted regions.
2. **Hypothesis B**: The breach is primarily opportunistic, with cybercriminals exploiting the vulnerabilities for financial gain rather than strategic national objectives. This is supported by the lack of evidence of exploitation in the wild and the general nature of the vulnerabilities.
Using the Analysis of Competing Hypotheses (ACH) 2.0, Hypothesis A is better supported due to the strategic implications and the urgency of the CISA emergency patch directive, indicating a higher perceived threat level.
3. Key Assumptions and Red Flags
– **Assumptions**: It is assumed that all exposed instances are equally vulnerable and that nation-state actors have the capability and intent to exploit these vulnerabilities.
– **Red Flags**: The absence of confirmed exploitation in the wild is a significant red flag, suggesting potential overestimation of the threat.
– **Blind Spots**: Limited information on the specific vulnerabilities and their potential impact on different systems creates uncertainty in assessing the full scope of the threat.
4. Implications and Strategic Risks
The breach could lead to significant disruptions in critical infrastructure, particularly if nation-state actors leverage the vulnerabilities for espionage or sabotage. The economic impact could be substantial, affecting sectors reliant on F5 technologies. Geopolitically, this could escalate tensions between affected countries and suspected nation-state actors.
5. Recommendations and Outlook
- Immediate patching of all vulnerable systems is critical to mitigate the risk of exploitation.
- Enhance monitoring and threat intelligence sharing among affected entities to detect and respond to potential attacks.
- Scenario-based projections:
- **Best Case**: Rapid patching and coordinated response prevent any significant exploitation.
- **Worst Case**: Nation-state actors exploit the vulnerabilities, leading to widespread disruption and geopolitical tensions.
- **Most Likely**: Opportunistic attacks occur, but major exploitation is limited by timely patching and response efforts.
6. Key Individuals and Entities
– Shadowserver Foundation
– Cybersecurity and Infrastructure Security Agency (CISA)
– F5 Networks
7. Thematic Tags
national security threats, cybersecurity, counter-terrorism, regional focus